当前位置:网站首页>Sword finger offer 31 Stack push in and pop-up sequence
Sword finger offer 31 Stack push in and pop-up sequence
2022-07-04 10:16:00 【JoesonChan】
subject
Enter two sequences of integers , The first sequence represents the push order of the stack , Determine whether the second sequence is the pop-up order for the stack . Suppose that all the Numbers pushed are not equal . for example , Sequence {1,2,3,4,5} Is the stack pressing sequence of a stack , Sequence {4,5,3,2,1} Is a popup sequence corresponding to the stack sequence , but {4,3,5,1,2} It cannot be a popup sequence of the push sequence .、
Example 1:
Input :pushed = [1,2,3,4,5], popped = [4,5,3,2,1]
Output :true
explain : We can do it in the following order :
push(1), push(2), push(3), push(4), pop() -> 4,
push(5), pop() -> 5, pop() -> 3, pop() -> 2, pop() -> 1
Example 2:
Input :pushed = [1,2,3,4,5], popped = [4,3,5,1,2]
Output :false
explain :1 Can't be in 2 Pop up before .
Tips :
0 <= pushed.length == popped.length <= 1000
0 <= pushed[i], popped[i] < 1000
pushed yes popped Permutation .
public static boolean isStackArray(int[] nums1, int[] nums2) {
if (nums1.length != nums2.length) {
return false;
}
int index1 = nums1.length - 1;
LinkedList<Integer> stack = new LinkedList<>();
for (int index2 = 0; index2 < nums2.length; index2++) {
stack.push(nums2[index2]);
while (!stack.isEmpty() && nums1[index1] == stack.peek()) {
index1--;
stack.pop();
}
}
return stack.isEmpty();
}
边栏推荐
- Use C to extract all text in PDF files (support.Net core)
- Golang Modules
- uniapp 小于1000 按原数字显示 超过1000 数字换算成10w+ 1.3k+ 显示
- MySQL develops small mall management system
- 查看CSDN个人资源下载明细
- JDBC and MySQL database
- Hands on deep learning (43) -- machine translation and its data construction
- Some summaries of the third anniversary of joining Ping An in China
- [200 opencv routines] 218 Multi line italic text watermark
- Golang defer
猜你喜欢
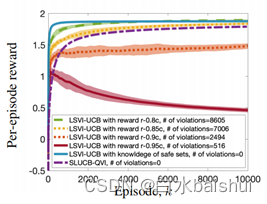
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 2
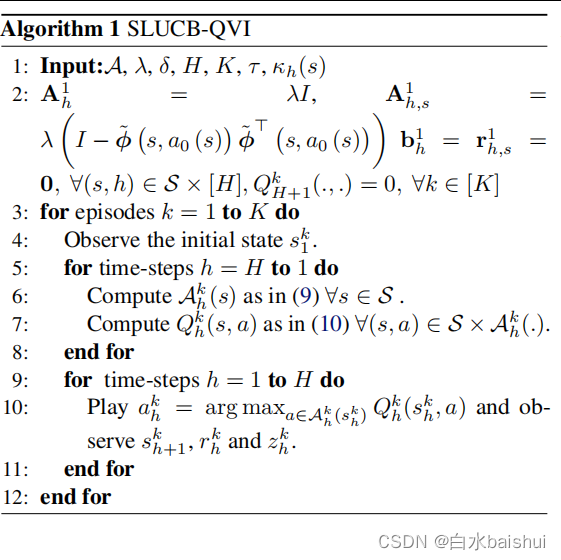
基于线性函数近似的安全强化学习 Safe RL with Linear Function Approximation 翻译 1
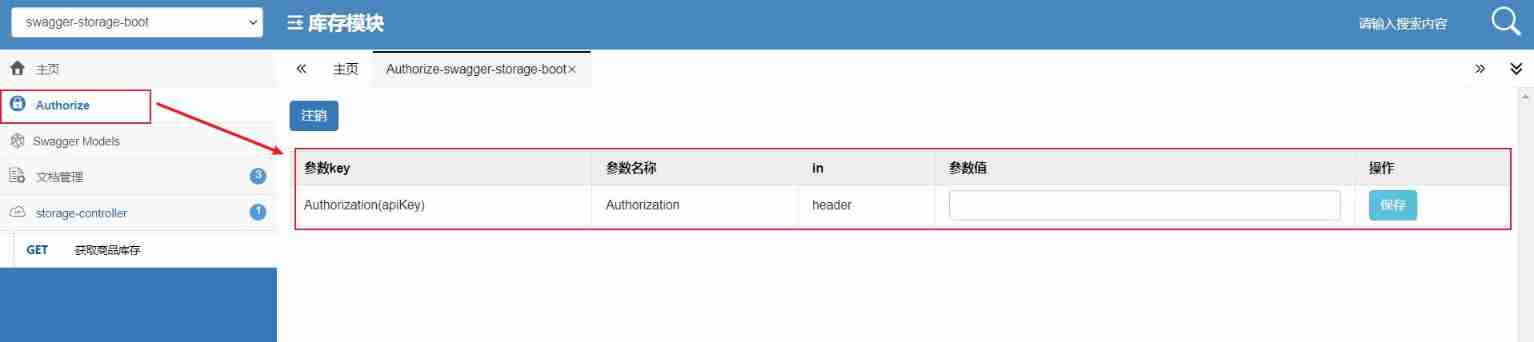
How do microservices aggregate API documents? This wave of show~

5g/4g wireless networking scheme for brand chain stores

Hands on deep learning (33) -- style transfer
Web端自动化测试失败原因汇总

Hands on deep learning (40) -- short and long term memory network (LSTM)

For programmers, if it hurts the most...
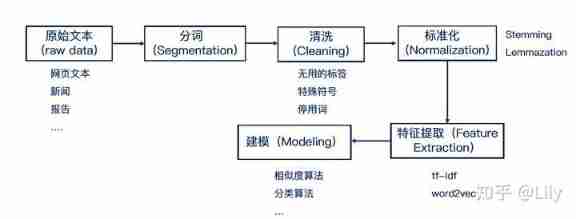
Hands on deep learning (35) -- text preprocessing (NLP)
Hands on deep learning (39) -- gating cycle unit Gru
随机推荐
Hands on deep learning (35) -- text preprocessing (NLP)
Exercise 9-5 address book sorting (20 points)
Hands on deep learning (43) -- machine translation and its data construction
用数据告诉你高考最难的省份是哪里!
按键精灵打怪学习-识别所在地图、跑图、进入帮派识别NPC
[FAQ] summary of common causes and solutions of Huawei account service error 907135701
Hands on deep learning (46) -- attention mechanism
Deep learning 500 questions
Vanishing numbers
Advanced technology management - how to design and follow up the performance of students at different levels
Normal vector point cloud rotation
libmysqlclient. so. 20: cannot open shared object file: No such file or directory
Whether a person is reliable or not, closed loop is very important
PHP code audit 3 - system reload vulnerability
Hands on deep learning (42) -- bi-directional recurrent neural network (BI RNN)
品牌连锁店5G/4G无线组网方案
Legion is a network penetration tool
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 2
六月份阶段性大总结之Doris/Clickhouse/Hudi一网打尽
Go context basic introduction
