当前位置:网站首页>[Galaxy Kirin V10] [server] iSCSI deployment
[Galaxy Kirin V10] [server] iSCSI deployment
2022-07-04 10:33:00 【GUI Anjun @kylinos】
step 1:iscsi Introduce
a、backstore, Back end storage
It corresponds to the device that provides actual storage space on the server side ( Note that it is only divided into areas , Unformatted , Storage devices without file systems , Such as unformatted disk sdb1), Need a management name
b、target, Disk group
Is the client's access target , As a framework , By multiple lun form
c、lun, Logical unit
every last lun Need to be associated with a backend storage device , On the client side, it will be regarded as a virtual hard disk
d、 If you put iSCSI As a courier , You can think of back-end storage as a refrigerator , It's something that actually needs express delivery , The disk pack is a wooden box , It's safer to put the refrigerator in a wooden box ,lun It is to associate the refrigerator with the wooden box , So the actual step is to establish backstore Back end storage , Find the fridge first , Then create target Disk group , Create a wooden box , Last lun Put the refrigerator in a wooden box , Connect the two .
step 2:iSCSI Server side (target End ) To configure
1、 Basic interaction , Use targetcli Set up the configuration
# /backstore/block create Back end storage name Actual device path
# /iscsi create Disk group IQN name
# /iscsi/ Disk group name /tpg1/luns create Back end storage path
# /iscsi/ Disk group name /tpg1/scls create The client IQN identification
# /iscsi/ Disk group name /tpg1/portals create IP Address Port number
2、iqn Naming specification
iqn Full name ISCSI Qualified Name
iqn.yyyy-mm. Reverse domain name : Custom logo
Used to identify target Disk group , Also used to identify clients
Name example :
iqn.2016-02.com.example:server0
iqn.2016-02.com.example:desktop0
( Must be iqn start ; Followed by the year and month , The middle is separated by a horizontal bar , Note that the month must be an even number , If it is 2021 year 7 month , You must also write 2021-07, Otherwise, the verification fails ; Then there is the inverted domain name , For example, the domain name is baidu.com, Then it has to be written upside down com.baidu, The verification of the domain name is not very strict , Even if it's written as haha.xixi It doesn't matter ; Finally, the user-defined logo , Write it yourself )
3、 Start deployment
( The firewall configures itself , Turn off or set the area to trusted Or open 3260 port )
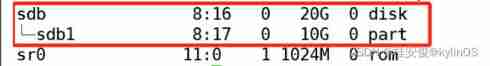
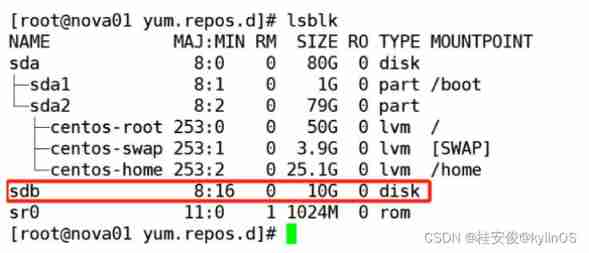
# lsblk // Here is a piece 20GB Free hard disk sdb, Separate out 10G Of sdb1 For network shared storage , Be careful sdb1 Don't format
# yum install targetcli
# targetcli // use targetcli To configure
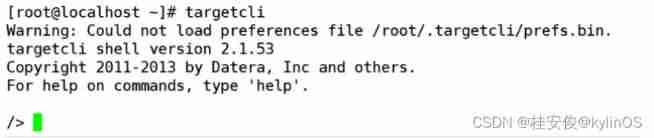
/> ls // Check the initial configuration interface , Support Tab completion

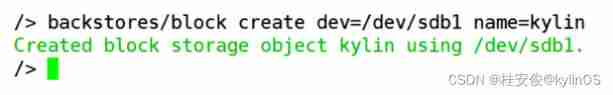
/> backstores/block create dev=/dev/sdb1 name=kylin // Build back-end storage ,block Represents that the storage device type is block device type , Specify storage device sdb1, And named it kylin,name Name customization , It can be understood as creating a refrigerator
 /> ls // View configuration changes , Store on the back end backstores There's one down there block Block device , The name is kylin, The actual equipment used is /dev/sdb1, The following configuration is directly used kylin representative /dev/sdb1 equipment
/> ls // View configuration changes , Store on the back end backstores There's one down there block Block device , The name is kylin, The actual equipment used is /dev/sdb1, The following configuration is directly used kylin representative /dev/sdb1 equipment
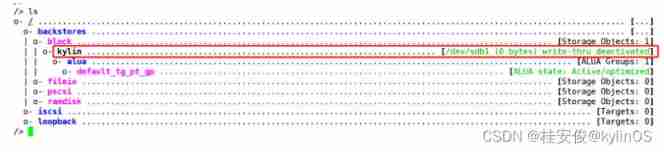
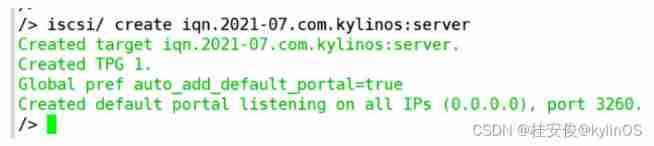
/> iscsi/ create iqn.2021-07.com.kylinos:server // Create disk groups , Note that the name of the disk group must match iqn Naming rules ,iqn See the above description for the naming rules , As shown in the figure below iscsi The default port is 3260, It can be understood as creating a wooden box
/> iscsi/ delete iqn.2021-07.com.kylinos:server //delete Parameters can be deleted for disk groups , This step can be skipped
/> ls // Check the configuration , You can see the new disk group

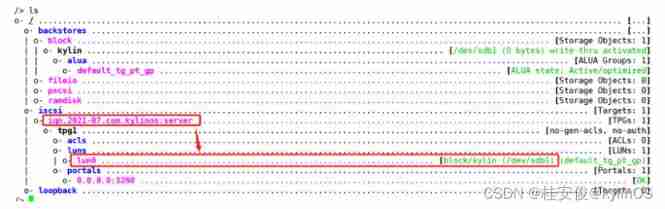
/> iscsi/iqn.2021-07.com.kylinos:server/tpg1/luns create /backstores/block/kylin // Associate disk groups with back-end storage ,tpg1 It's the goal , Followed by luns The way ,kylin Refers to /dev/sdb1, Put the refrigerator into the wooden box , The two are related
/> ls // You can see iqn The next one is luns relation , The device is /dev/sdb1
/> iscsi/iqn.2021-07.com.kylinos:server/tpg1/acls create iqn.2021-07.com.kylinos:client // This step is to establish acl Access control rights , It can be understood as filling in the information of the express recipient , It's called iqn.2021-07.com.kylinos:client People can sign for this express , Note that the name of the recipient must also conform to iqn Naming specification
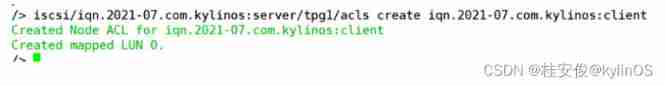 /> ls // You can see acls The client name under access control , Below portals Is the default configuration generated automatically ,0.0.0.0:3260 Represents the default listener for all addresses of this machine 3260 port , The old version needs to be manually configured to listen to which address of the machine 3260 port , With centos For example ,centos7.5 No manual configuration is required by default ,centos7 You need to configure this item manually , The manual configuration method is :/iscsi/ Disk group name /tpg1/portals create IP Address Port number ,IP The address is suggested to be 0.0.0.0, Represents all addresses of this machine , All open to the outside world , No matter which address the client accesses, it can access 3260 Port corresponding service
/> ls // You can see acls The client name under access control , Below portals Is the default configuration generated automatically ,0.0.0.0:3260 Represents the default listener for all addresses of this machine 3260 port , The old version needs to be manually configured to listen to which address of the machine 3260 port , With centos For example ,centos7.5 No manual configuration is required by default ,centos7 You need to configure this item manually , The manual configuration method is :/iscsi/ Disk group name /tpg1/portals create IP Address Port number ,IP The address is suggested to be 0.0.0.0, Represents all addresses of this machine , All open to the outside world , No matter which address the client accesses, it can access 3260 Port corresponding service

/> saveconfig // Save configuration , In fact, it's direct exit Exiting the system will automatically save and exit
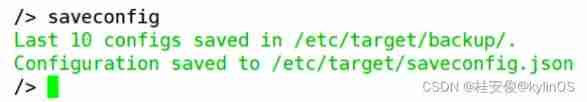
/> exit // sign out targetcli To configure

# systemctl restart target // restart target service
# systemctl enable target // Set power on self start
step 3:iSCSI client (initiator End )
1、 Install the client package
# yum repolist // Refresh yum cache
# yum install iscsi-initiator-utils -y
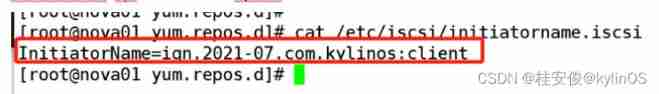
# vim /etc/iscsi/initiatorname.iscsi // Modify the name claimed by the client , It corresponds to the name of the recipient set on the server , The name must be consistent with the client name set by the server
InitiatorName=iqn.2021-07.com.kylinos:client
# systemctl restart iscsid // Restart client service , Refresh iqn name
# iscsiadm --mode discoverydb --type sendtargets --portal 192.168.1.10 --discover // Find out iscsi equipment , Back IP For the server IP, If it fails, please check the firewall configuration , This step can be understood as signing for the wooden box containing the refrigerator , There are also steps to unpack the box
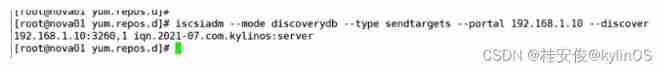
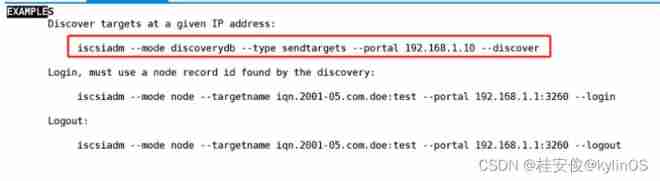
# man iscsiadm // If you can't remember, you can use man Help search EXAMPLES You can get the command template
# systemctl restart iscsi // Be careful iscsi There is no d, Yes d Is refresh iqn Name ,iscsi Is the real client service , Restarting is equivalent to the steps of unpacking ,iscsid It can be seen as iscsi Sub services of
# lsblk // You can see the new disks added by the client sdb,10G, There was no such thing , Server side iscsi Shared , Next, the client can use the change storage normally , Partition 、 Format, etc
# systemctl enable iscsi // Set to boot from , So that the shared storage can be found every time you start up
边栏推荐
- Devop basic command
- Time complexity and space complexity
- Network connection (III) functions and similarities and differences of hubs, switches and routers, routing tables and tables in switches, why do you need address translation and packet filtering?
- The future education examination system cannot answer questions, and there is no response after clicking on the options, and the answers will not be recorded
- [200 opencv routines] 218 Multi line italic text watermark
- 【FAQ】华为帐号服务报错 907135701的常见原因总结和解决方法
- System.currentTimeMillis() 和 System.nanoTime() 哪个更快?别用错了!
- C language structure to realize simple address book
- PHP代码审计3—系统重装漏洞
- Read a piece of text into the vector object, and each word is stored as an element in the vector. Convert each word in the vector object to uppercase letters. Output the converted elements in the vect
猜你喜欢
![[FAQ] summary of common causes and solutions of Huawei account service error 907135701](/img/73/c4ee842475f05e2e67297fcac68779.png)
[FAQ] summary of common causes and solutions of Huawei account service error 907135701
system design
VLAN part of switching technology
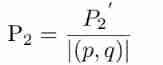
Latex error: missing delimiter (. Inserted) {\xi \left( {p,{p_q}} \right)} \right|}}
如果不知道這4種緩存模式,敢說懂緩存嗎?
How to use diff and patch to update the source code
20 minutes to learn what XML is_ XML learning notes_ What is an XML file_ Basic grammatical rules_ How to parse
Occasional pit compiled by idea
On binary tree (C language)
Error C4996 ‘WSAAsyncSelect‘: Use WSAEventSelect() instead or define _ WINSOCK_ DEPRECATED_ NO_ WARN
随机推荐
Huge number (C language)
DCL statement of MySQL Foundation
Batch distribution of SSH keys and batch execution of ansible
Student achievement management system (C language)
Native div has editing ability
Two way process republication + routing policy
Collection of practical string functions
Latex learning insertion number - list of filled dots, bars, numbers
leetcode1-3
Does any teacher know how to inherit richsourcefunction custom reading Mysql to do increment?
Rhcsa12
Sword finger offer 05 (implemented in C language)
AUTOSAR从入门到精通100讲(106)-域控制器中的SOA
Write a program that uses pointers to set all elements of an int array to 4.18: 0.
Uniapp--- initial use of websocket (long link implementation)
If the uniapp is less than 1000, it will be displayed according to the original number. If the number exceeds 1000, it will be converted into 10w+ 1.3k+ display
RHCE - day one
Recursive method to achieve full permutation (C language)
The most detailed teaching -- realize win10 multi-user remote login to intranet machine at the same time -- win10+frp+rdpwrap+ Alibaba cloud server
Safety reinforcement learning based on linear function approximation safe RL with linear function approximation translation 1