当前位置:网站首页>What is devsecops? Definitions, processes, frameworks and best practices for 2022
What is devsecops? Definitions, processes, frameworks and best practices for 2022
2022-07-04 09:58:00 【Doooooooog】
DevSecOps It is a practical and goal oriented method , Used to ensure system security .DevSecOps Is defined as passing with IT Security team 、 Software developers work with the operations team , In standard DevOps The process of establishing key safety principles in the cycle . The following is right 2022 year DevSecOps The Conduit 、 In depth analysis of frameworks and best practices .
Catalog
What is? DevSecOps?
DevSecOps How pipes work ?
understand DevSecOps frame
2022 year 5 Big DevSecOps Best practices
What is? DevSecOps?
DevSecOps It means to pass with IT Security team 、 Software developers work with the operations team , In standard DevOps Establish key safety principles in the cycle .
seeing the name of a thing one thinks of its function ,DevSecOps yes DevOps Continuation of concept . It's based on the fact that , That is, every department in the organization is also responsible for integrating security at every stage of the software development cycle .
It is the common goal of all organizations to release new code to production as quickly as possible . However , In this online security issue 、 In the era of increasingly serious network threats and other security vulnerabilities , Each stage needs to follow a specific security protocol , This is it. DevSecOps Where it comes in handy .
DevSecOps One of its main advantages is that it can minimize the vulnerability of any product , And make it completely ready for end users . Because each process and related workflow are automated through strict safety inspection , Therefore, the safety requirements can be met more accurately . however , Choose the right tools to maintain continuous integration (CI) Security in is crucial . The security team needs to be fully trained to help achieve this goal .
DevSecOps How pipes work ?
Usually ,DevOps Pipelines involve multiple steps .DevSecOps Stand out from traditional methods by ensuring strict safety standards at each stage . Software development lifecycle (SDLC) The main stages of the process include planning 、 code 、 structure 、 test 、 Release and deploy .
plan : In the planning stage , Perform major safety analysis . Engineers develop appropriate testing strategies , Used to determine the way of testing 、 Place and time .
Code : Use various types of Git Controls and tools to protect sensitive information , For example, application programming interface (API) Key and password .
structure : Writing and executing the code used to build the source code is critical . ad locum , Static application security testing (SAST) Technology is widely used to make code error free .
test : In the test phase , Dynamic application security testing (DAST) Tools are mainly used to test products / Applications , Protect user authentication , And identify SQL Injection and API Possible problems in the endpoint .
Release : The release phase refers to the security analysis performed during penetration testing and vulnerability scanning .
Deploy : The deployment phase is to implement appropriate security protocols in production , Prepare for final deployment .
As mentioned earlier , stay DevSecOps A number of safety measures have been implemented at each stage of . The following are the stages of such safety procedures :
The first stage : Threat modeling
Threat modeling summarizes possible attack scenarios , Lists the flow direction of sensitive data , And highlights vulnerabilities and mitigation alternatives . This stage helps to solve safety problems and improve the safety understanding of the team .
The second stage : scanning
The scanning phase evaluates the code to ensure that it is secure and free of security vulnerabilities . Manual and automatic code reviews are included here . In this step , Used SAST and DAST etc. AppSec Tools . Because it is in the early stage of software development life cycle , This phase allows engineers to address most security vulnerabilities and defects .
The third stage : analysis
Analyze all previously obtained data and indicators , To identify any security vulnerabilities at this stage . Then classify the hazards into a list , From the most serious to the least . some SAST Program ( for example Klocwork) This process can be performed automatically .
The fourth stage : Remedy
The remediation phase deals with security vulnerabilities that have been identified and organized in the previous phase . some DevSecOps technology ( for example SAST) You can target the vulnerabilities found 、 Defects and suggestions for repair . This makes it easier to deal with security problems when they occur .
The fifth stage : monitor
In the monitoring phase , Track the vulnerabilities found , Try to reduce or eliminate them , And evaluate the overall security status of the application . It is also good to track and manage the changes between the actual index value and the target index value . In the software development lifecycle , This helps make informed data-driven decisions . The organization should first implement continuous safety in safety unit testing . Security unit test requirements are as important as other unit tests we write .
understand DevSecOps frame
DevOps Help accelerate software delivery , This challenges standard safety practices . Because of this problem ,DevSecOps( or SecDevOps) The term was coined to describe the integration of security procedures into DevOps In the system . understand DevSecOps How to provide the best level of security in different industries is crucial . So , You need to have a clear understanding of building DevSecOps The main functions and solutions required by the framework . Next , We will guide you to understand the top standard functions of application security products , In order to create DevSecOps frame .
3.1 Security scanning
Security scanning is one of the main functions of application security products . It basically has two types —— Agent based and agent-free . Although these two scanning models are very popular , But the agent free scanning model works in a different way . ad locum , Application security services collect projects and related data from security administrators , Then perform security scanning in the agentless scanning architecture .
Security administrators can use Web Dashboards enter project information or write scripts to transfer data to the disclosure of application security services API. Agent free security scanning is based on two main components —— Scan agents and application security services . The main function of the scanning agent is to run a thorough security scan and submit the output to the application security service for further scanning and analysis .
If there is no application security service , The scanning results of the security agent will be useless . for example , about SCA product , The signature of the scanning library can be in the result , The details of the vulnerability are expected . On the other hand , about SAST product , The result contains vulnerable code . therefore , The scan results can only be used with the database of the application security service .
3.2 Get source code
Application security products generally receive source code in two main ways —— Version control system mode and file upload mode . In the process , Relevant security administrators compress the source code and upload it to the application security products as needed . The upload process passes through the published API or Web Management interface for .
The security administrator configures the repository information for the project through the version control system . Some examples are —— Repository unified resource locator 、 Repository access credentials, etc .
The application security service uses a specific set of data to obtain the source code from the version control system . Because obtaining complete source code may be more time-consuming and complex , Therefore, it will retrieve the updated code to ensure better results .
Besides , There are other advantages to using a version control system , For example, incremental scanning 、 More rigorous authentication process 、 Simplified operations related to the project . This is one of the main factors that make obtaining multiple levels of source code unique and effective .
3.3 Project organization
Each project is produced and managed by different teams according to the organizational hierarchy . Users and groups are used to organize tasks in application security products .
Each user is a member of one or more groups , Each group can access one or more projects . Besides , Employees often need to deal with multiple software projects at the same time . Such projects are usually associated with a single Department of the company .
therefore , It is impractical to map directly from the organizational structure . therefore , Each item is assigned to a group , This group includes all users of the project who use application security products .
DevSecOps There are two main parts in the architecture , Especially in high-level architecture . The agent here refers to an easy-to-use script , It extracts and collects the source code and sends it to the relevant engine . This is a CI( Continuous integration ) A key part of the process .
ad locum , Monomer architecture and micro service architecture are two kinds of architectures . For these reasons , The engine of the framework is built using the microservice architecture :
Easier to maintain : The engine supports different security programs ( Such as security scanning 、 Report retrieval and voucher management ). Each feature can be defined as a separate microservice in the architecture , It can be created and maintained independently . If you choose the overall design , Changing or adding a security feature will require changing or adding another element .
Higher reliability and availability : When a security component ( for example , Safety report ) In case of failure , It will not affect other security functions . If you use a single architecture for this framework , Then the failure of a single safety function may lead to the failure of the whole framework .
Easier to expand : Each service can be extended separately , In order to provide more resources when necessary . When using monomer architecture , The entire engine must be extended to meet the resource requirements of a single function .
2022 year 5 Big DevSecOps Best practices
To release DevSecOps The potential of , You must follow the set best practices . ad locum , We have listed DevSecOps Best practices , To ensure a high level of security 、 Reduce risks and improve operational efficiency . The goal should be to ensure a high standard of security .
4.1 Use secure coding technology
Security coding technology is DevSecOps An integral part of , To ensure that the software is fully protected , From any low vulnerability level threat . Unless the code is highly secure , Otherwise, there will be data leakage 、 Risks such as network security attacks and other security threats . It is suggested to invest the time and resources required in the security coding technology , To avoid serious security attacks in the future . Always choose experienced developers and follow the correct coding standards .
4.2 Integrate the right tools
Integrating the right tools is effective implementation DevSecOps One of the foundations of . Most companies use top application security technologies , for example SAST、DAST、 Interactive application security testing (IAST) And source combination analysis (SCA) etc. , To ensure the correct use and optimization of tools .
DevSecOps Some common but popular features of tools are image assurance 、 Intrusion detection 、 Runtime protection and other microservice security functions . With containerization and microservices becoming the foundation of modern application infrastructure , Appropriate DevSecOps Tools integrated into the enterprise SOP in . This is well developed and easy to use API Where it works , Because they help extend and integrate tools across different platforms and application domains .
4.3 Using automation
Manual processes are more error prone , And it is usually inconvenient to expand the scale . Such technologies also increase the risk of misconfiguration , This is the most influential thing facing enterprises 、 One of the most serious security threats .
Need to be in the whole CI/CD Strict safety protocols and measures are applied and verified in the pipeline , Automation is the reason to simplify the whole process . That's why it's DevSecOps One of the most effective best practices . Enterprises must automate as much as possible —— from IDE The code in is written into production IAM role —— Prevent by avoiding misconfiguration 、 Detect and fix problems .
4.4 Using security is code
Security is code, which refers to the coding of security policy 、 Scanning and verification . The main advantage of security as code is that it ensures appropriate security rules . The agreement is implemented uniformly throughout the infrastructure . It also helps speed up the deployment and use of pipeline versioning and Automation .
Security is code , Such as automation and others DevSecOps Best practices , Provides the benefits of enhanced security and helps improve operations . Besides , Once documented , It simplifies iterative and extended security methods .
4.5 Move left safely
Traditionally , Security scanning and evaluation are carried out after software production . therefore , Solving security vulnerabilities is complex 、 Expensive and time sensitive . In order to solve these difficulties , Left shift security emphasizes integrating security into the software development lifecycle as soon as possible (SDLC) in .
Moving left is not just code . It also needs to be in SDLC The planning 、 Priority should be given to safety in the analysis and design stage . Enterprises can find security problems and misconfigurations as soon as possible , Improve product quality and safety , At the same time, reduce the time and effort required to repair vulnerabilities .
边栏推荐
- C # use gdi+ to add text to the picture and make the text adaptive to the rectangular area
- Leetcode (Sword finger offer) - 35 Replication of complex linked list
- libmysqlclient. so. 20: cannot open shared object file: No such file or directory
- H5 audio tag custom style modification and adding playback control events
- AUTOSAR from getting started to mastering 100 lectures (106) - SOA in domain controllers
- Ultimate bug finding method - two points
- Basic data types in golang
- Kotlin:集合使用
- Lauchpad x | MODE
- What are the advantages of automation?
猜你喜欢
Hands on deep learning (38) -- realize RNN from scratch
Hands on deep learning (41) -- Deep recurrent neural network (deep RNN)
Dynamic address book

对于程序员来说,伤害力度最大的话。。。
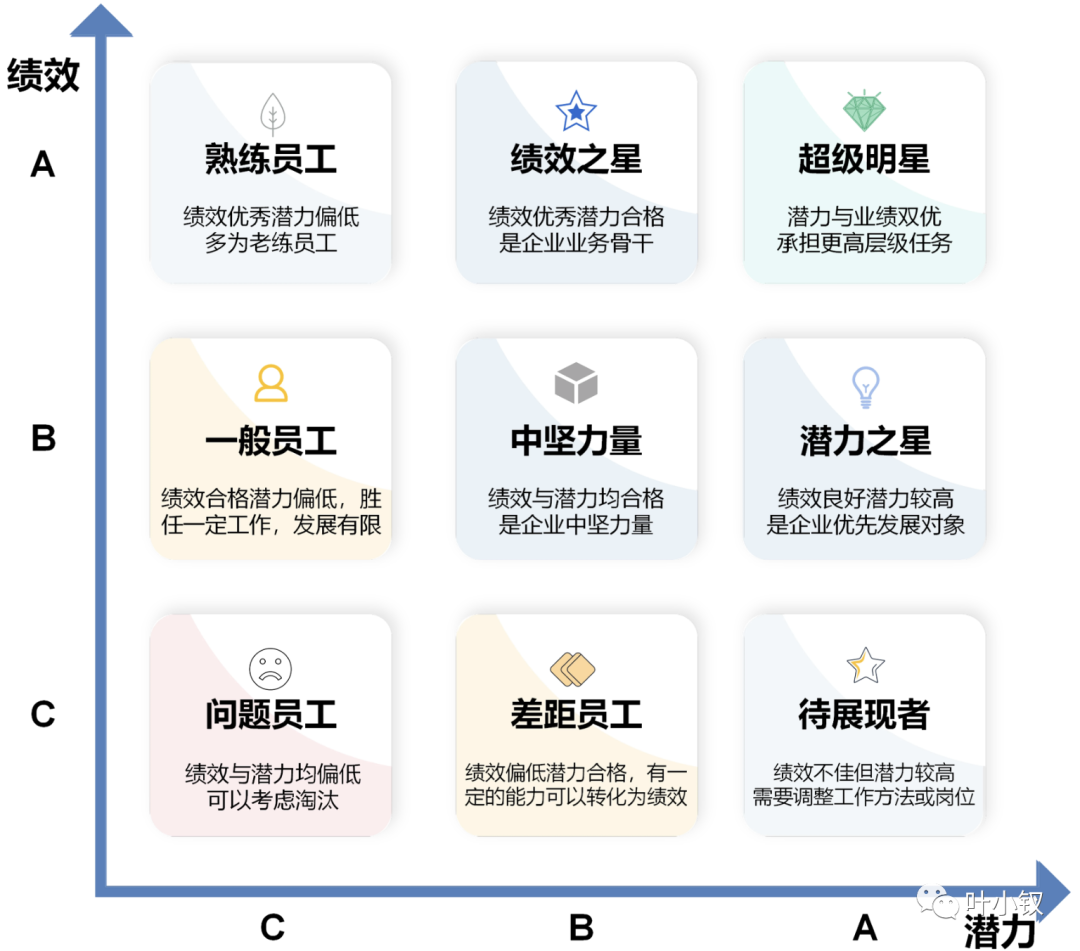
技术管理进阶——如何设计并跟进不同层级同学的绩效
uniapp 小于1000 按原数字显示 超过1000 数字换算成10w+ 1.3k+ 显示
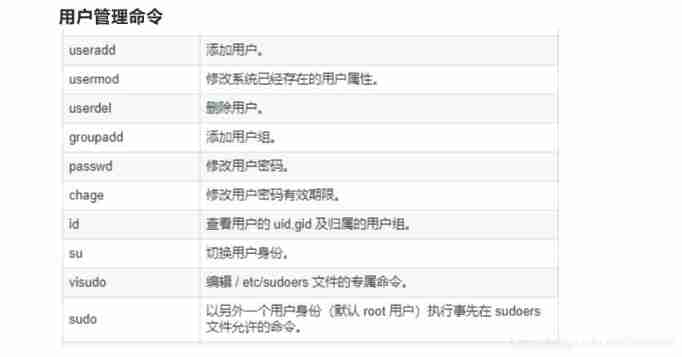
Devop basic command
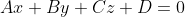
Normal vector point cloud rotation
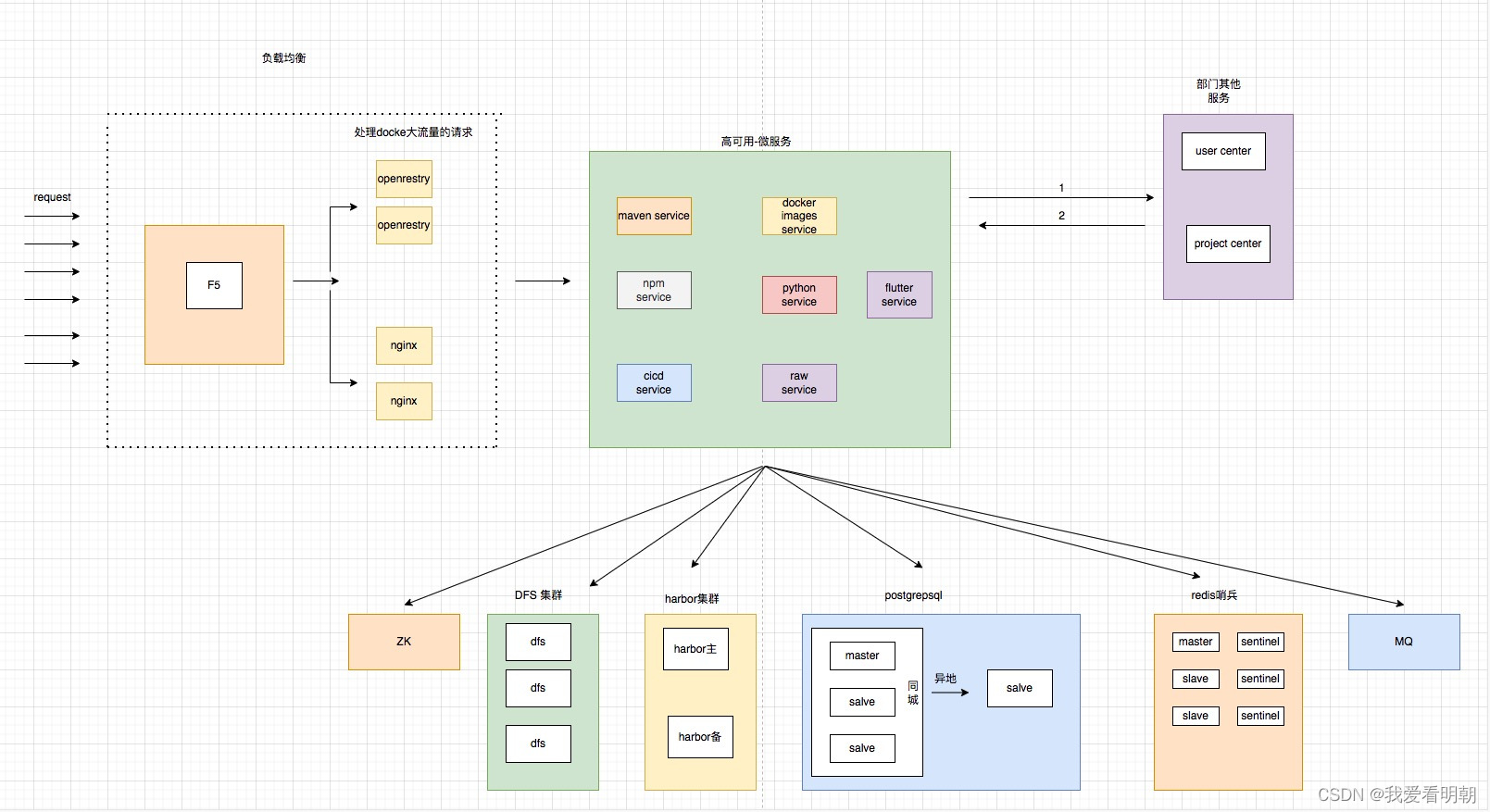
Some summaries of the third anniversary of joining Ping An in China
华为联机对战如何提升玩家匹配成功几率
随机推荐
转载:等比数列的求和公式,及其推导过程
Pcl:: fromrosmsg alarm failed to find match for field 'intensity'
Custom type: structure, enumeration, union
System.currentTimeMillis() 和 System.nanoTime() 哪个更快?别用错了!
Matlab tips (25) competitive neural network and SOM neural network
Hands on deep learning (39) -- gating cycle unit Gru
Exercise 9-4 finding books (20 points)
Histogram equalization
百度研发三面惨遭滑铁卢:面试官一套组合拳让我当场懵逼
Go context basic introduction
Kotlin: collection use
Kubernetes CNI 插件之Fabric
PHP is used to add, modify and delete movie information, which is divided into foreground management and background management. Foreground users can browse information and post messages, and backgroun
Svg image quoted from CodeChina
Explanation of for loop in golang
Launpad | 基礎知識
Golang type comparison
SQL replying to comments
Exercise 9-5 address book sorting (20 points)
智慧路灯杆水库区安全监测应用