当前位置:网站首页>VI text editor and user rights management, group management and time management
VI text editor and user rights management, group management and time management
2022-07-04 10:35:00 【Zhuge Bo】
vi Text editor
1. install :yum -y install vim*
2. vi/vim Three modes of and the conversion between each mode
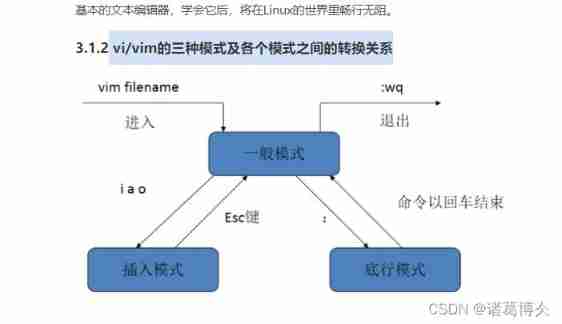
3. Edit commands and shortcuts
Insert command :( General mode goes into insert mode ):
i Insert... In front of the cursor
I Insert... At the current line of the cursor
a Insert... After the cursor
A Insert... At the end of the current line of the cursor
o Insert a new line next to the current line of the cursor
O Insert a new line on the previous line of the cursor's current line
Locate the command ( Write in bottom line mode ):
:set nu According to the line Numbers
:set nonu Cancel the line Numbers
:n To... Of the text n That's ok
gg Go to the first line of the text G To the last line of the text
Replace and cancel commands ( In general mode ):
u undo, Cancel the previous operation ctrl + r redo, Back to undo Before
r Replace character at cursor
R Replace from where the cursor is , Press Esc Key end
The delete command :
x Deletes the character where the cursor is
nx Delete... After the cursor n Characters
dd Deletes the line where the cursor is located .
ndd Delete n That's ok
dG Delete all contents from the cursor line to the end line
D Delete the content from the cursor to the end of the line
:5,7d Deletes the row of the specified range
Common shortcut key :
Shift+ zz Save and exit , And “:wq” The same effect
v Enter character visual mode
V or Shift + v Enter line view mode
Ctrl + v Enter block view mode
ctrl+b: Screen moves back one page
ctrl+f: Move the screen forward one page
Press "$" Symbol moves the cursor to the end of the line
Press "^" Move the cursor to the beginning of the line
yy: Copy cursor line to buffer .
nyy: for example ,「6yy」 Indicates that the copy is from the line where the cursor is located " Count down "6 Line text .
Linuxroot password :aaaqy142
4. User authority management , Group management and time management
1. A file that holds user information :/etc/passwd
2. A file that stores user password information :/etc/shadow
3. The user classification :
The super user :(root,UID=0)
Ordinary users :(UID stay 1000 To 60000)
Dummy user :( UID stay 1 To 999)
4. Add user command useradd
-u Designated user ID(uid)
-g Specify the group name to which you belong (gid) The main group
-G Specify multiple groups , Comma “,” Separate (Groups) Other groups
-c User description (comment) ;
-e Failure time (expire date)
establish :
useradd -u 1888 -g users -G sys,root -c " Description information "uqy142a
(centos 7 Previous version , Pseudo user from 1-999 centos7 Then the pseudo user uses 1-999 Ordinary users of the current version ID Should be 1000 To 60000)
Set the password : passwd uqy142a// Set the password twice
Switching users su su -l uqy142a
5. Modify user command :usermod(user modify)
l Change user name (login)usermod -l a b(b Change it to a)
usermod -l uqy142cc uqy142c
-g add group usermod -g sys tom
usermod -g root uqy142a
-G Add multiple groups usermod -G sys,root tom
usermod -G sys,users uqy142a
–L Lock user account password (Lock) usermod -L uqy142b // lock b user , Even if ordinary users are locked ,root You can still log in
–U Unlock user account (Unlock)
su -l root // Switch to root Unlock
usermod -U uqy142b su -l uqy142a
su -l uqy142b // The password is found to be correct , Switch users
6. Delete user command :userdel
userdel uqy142d // Just delete user information
userdel -r uqy142e When deleting an account, delete the directory (remove
5. Group management
Save user group files :/etc/group
add group :groupadd:
groupadd -g 16666 groupa -g Appoint gid
tail /etc/group // After displaying the file 10 That's ok
Modify the set of :groupmod
groupmod -n groupaa groupa // hold groupa Change the name of groupaa
groups Display the user's group
groups uqy142a
Other group related commands :
chgrp Change the group to which the directory or file belongs ( Reorganize only )
ll |grep aaa // see aaa Subordinate to the group
chgrp groupb aaa change aaa Original group root Change it to groupb
chown Change directories or files Users and groups
ll |grep aaa // see aaa Users and groups
chown uqy142a:groupc aaa // change aaa The user and group of the directory
chown -R uqy142a:groupc aaa // The catalogue of descendants has changed
6.Sudo command
It is generally used in the non-medical field root Under the user , Temporary promotion is not root User's rights .
First step : Must be in /etc/sudoers Non root user
The second step : Carry out orders sudo reboot, Input user1 Password , Restart successful .
su -l uqy142a
sudo shutdown -h now // Tips uqy142a be not in sudoers In file Have no authority to execute
su -l root
vim /etc/sudoers
:100
Copy 100 Change user name
su -l uqy142a
sudo reboot // It's restarted
Any other ordinary user cannot execute commands , You can do that ....
7. time management
Synchronization time
yum -y install ntp ntpdate install ntp ntpdate service
ntpdate cn.pool.ntp.org Manual sync :
边栏推荐
- MPLS: multi protocol label switching
- Occasional pit compiled by idea
- PHP programming language (1) - operators
- uniapp 小于1000 按原数字显示 超过1000 数字换算成10w+ 1.3k+ 显示
- Today's sleep quality record 78 points
- Realsense of d435i, d435, d415, t265_ Matching and installation of viewer environment
- Introduction to tree and binary tree
- RHCE day 3
- Crawl Zhejiang industry and trade news page
- Write a program that uses pointers to set all elements of an int array to 4.18: 0.
猜你喜欢

Latex learning insertion number - list of filled dots, bars, numbers
![[Galaxy Kirin V10] [desktop] printer](/img/ab/066923f1aa1e8dd8dcc572cb60a25d.jpg)
[Galaxy Kirin V10] [desktop] printer
uniapp 小于1000 按原数字显示 超过1000 数字换算成10w+ 1.3k+ 显示
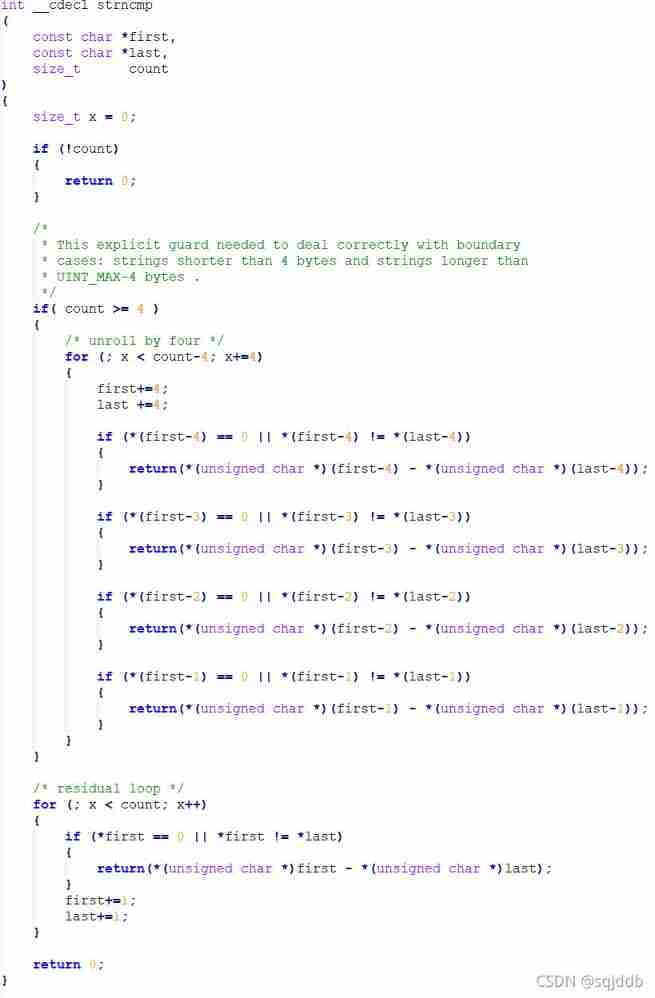
Collection of practical string functions
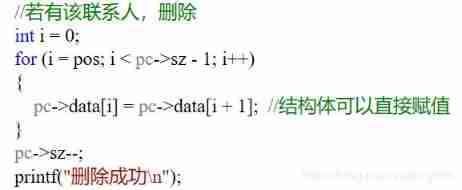
C language structure to realize simple address book

Basic principle of servlet and application of common API methods
![[200 opencv routines] 218 Multi line italic text watermark](/img/3e/537476405f02f0ebd6496067e81af1.png)
[200 opencv routines] 218 Multi line italic text watermark
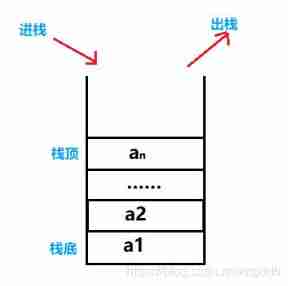
C language - stack
From programmers to large-scale distributed architects, where are you (I)
183 sets of free resume templates to help everyone find a good job
随机推荐
Quick sort (C language)
Latex arranges single column table pictures in double column format articles
Rhcsa12
Error C4996 ‘WSAAsyncSelect‘: Use WSAEventSelect() instead or define _ WINSOCK_ DEPRECATED_ NO_ WARN
uniapp 小于1000 按原数字显示 超过1000 数字换算成10w+ 1.3k+ 显示
Two way process republication + routing policy
20 minutes to learn what XML is_ XML learning notes_ What is an XML file_ Basic grammatical rules_ How to parse
Evolution from monomer architecture to microservice architecture
How do microservices aggregate API documents? This wave of show~
Use C to extract all text in PDF files (support.Net core)
Architecture introduction
Dynamic memory management
Communication layer of csframework
Rhcsa day 9
Development guidance document of CMDB
Dichotomy search (C language)
PHP programming language (1) - operators
/*The rewriter outputs the contents of the IA array. It is required that the type defined by typedef cannot be used in the outer loop*/
[200 opencv routines] 218 Multi line italic text watermark
Leetcode48. Rotate image