当前位置:网站首页>How to prevent governance attacks in DAOs?
How to prevent governance attacks in DAOs?
2022-08-01 21:52:00 【Blockchain Interstellar Society】
Theoretically, DAOs built on the blockchain have high security.However, as a technology that has only been developed for more than ten years, blockchain still has defects in many places, which also makes the blockchain ecology in actual operation not achieve the ideal security.

Similarly, DAOs often face malicious attacks from the Internet.As a decentralized autonomous organization, sometimes, a malicious proposal may bring the DAO to collapse.
There are a large number of real cases of governance attacks against DAOs. For example, in a protocol called Beanstalk, an attacker used a loan to quickly obtain a large number of Beanstalk governance tokens, made a malicious proposal and passed it quickly, stealing $182 million in Beanstalk funds before other members of the protocol responded.
DAO's governance attack has two different ways: light and dark. The above example is a case that happened in a public place.Within a period of time, the accumulation of governance tokens through some anonymous accounts is basically the same as that of normal users. When the time is right, it will show its fangs and launch an attack on DAO.

How to prevent governance attacks in DAOs, the most effective solution is to identify malicious attackers.However, judging from the protocol adopted by the current DAO, the two groups of normal contributors in the DAO and the attackers who want to destroy the DAO for profit are indistinguishable.This has also led to the fact that the higher the autonomy DAO provides to members of the organization, the easier it is for attackers to do evil.However, decentralization is the core idea of DAO, and it is inevitable to provide members with a high degree of autonomy.Therefore, preventing DAO governance attacks requires other means before the technology fails to identify malicious attackers.
After the underlying technology could not be improved to prevent governance attacks, some people proposed a solution to the problem from the governance level. In short, there are three main types:
One, reduce the attack value.When the value of a thing is very low, it is natural that the attacker will not spend a lot of energy and cost to attack it.Although the development of a DAO will naturally lead to an increase in its value, the value of an attack can naturally be reduced by limiting the corresponding governance power when the DAO is initially designed.
Second, increase the cost of voting. Generally speaking, the governance of DAO requires the acquisition of tokens to obtain voting rights. When the cost of acquiring tokens becomes high, attackers are generally reluctant to spend high costs to launch governance attacks on DAO.The DAO community can establish some incentives to reduce the circulation of the token, thereby increasing its value.

Third, increase the attack cost.When the attacker obtains a large number of governance tokens, DAO can also make it difficult for the attacker to launch an attack by increasing the attack cost.For example, common KYC authentication or reputation authentication can make some anonymous attackers have to give up their attacks.In addition, some projects use time locks to prevent the acquired tokens from participating in governance for a period of time. This time lock gives members and the community time to reflect, and can be better dealt with when an attacker launches an attack after releasing the time lock.
边栏推荐
- The difference between groupByKey and reduceBykey
- shell programming conventions and variables
- 基于php影视资讯网站管理系统获取(php毕业设计)
- 使用 Zokrates 在 BSV 上创建您的第一个 zkSNARK 证明
- Appendix A printf, varargs and stdarg a. 2 use varargs. H to realize the variable argument list
- Getting Started Database Days4
- Based on php animation peripheral mall management system (php graduation design)
- Mini Program--Independent Subcontracting & Subcontracting Pre-download
- _ _ determinant of a matrix is higher algebra eigenvalue of the product, the characteristic value of matrix trace is combined
- Upload markdown documents to blog garden
猜你喜欢

Based on php Xiangxi tourism website management system acquisition (php graduation design)
基于php在线音乐网站管理系统获取(php毕业设计)
Raspberry Pi information display small screen, display time, IP address, CPU information, memory information (C language), four-wire i2c communication, 0.96-inch oled screen

shell规范与变量
SAP ABAP OData 服务如何支持删除(Delete)操作试读版

2022 edition of MySQL tutorial, top collection good, take your time

小程序--独立分包&分包预下载
C expert programming
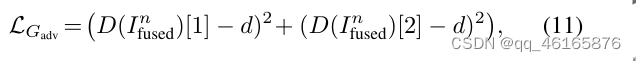
图像融合GANMcC学习笔记

不卷了!入职字节跳动一周就果断跑了。
随机推荐
groupByKey和reduceBykey的区别
AIDL communication
Chapter 12, target recognition of digital image processing
迁移学习——Discriminative Transfer Subspace Learning via Low-Rank and Sparse Representation
一种灵活的智能合约协作方式
感觉自己好傻
【C语言实现】两种计算平均成绩题型,博主精心整理,值得一读
Scala practice questions + answers
找工作必备!如何让面试官对你刮目相看,建议收藏尝试!!
基于php酒店在线预定管理系统获取(php毕业设计)
【Objective-C中的@synthesize】
render-props and higher order components
[@synthesize in Objective-C]
Raspberry Pi information display small screen, display time, IP address, CPU information, memory information (C language), four-wire i2c communication, 0.96-inch oled screen
[ASM] Bytecode Operation MethodWriter
Spark cluster construction
LeetCode952三部曲之一:解题思路和初级解法(137ms,超39%)
数字图像处理 第十二章——目标识别
基于php在线学习平台管理系统获取(php毕业设计)
Spark shuffle调优