当前位置:网站首页>Basic knowledge of network security
Basic knowledge of network security
2022-07-03 09:01:00 【qfliweimin】
One 、 Preface
When it comes to network security , Generally, people regard it as a branch of information security , Information security is a broader concept : Prevent knowledge 、 The facts 、 Unauthorized use of data or capabilities 、 misuse 、 Tamper with or refuse to use the measures taken .
To put it bluntly , Information security is to protect sensitive and important information from illegal access , And used to enter — Step by step to do illegal things . Network security is embodied in the information security problem in the environment where multiple computers realize independent interconnection , The main performance is : Autonomous computer security 、 Internet security ( Interconnected devices 、 communication link 、 Network software 、 Network protocol ) And the security of various network applications and services .

Here are some typical network security issues , You can sort it out :
1.IP Security : The main attack methods are passive network eavesdropping , Aggressive IP cheating ( Message forgery 、 Tampering ) And routing attacks ( Man-in-the-middle attack );
2.DNS Security : You should be familiar with , modify DNS Mapping table , Misleading user traffic ;
3.DoS attack : Denial of service attack initiated by a single attack source , It mainly occupies network resources , Force the target to collapse , What is more popular now is DDoS, Distributed denial attack initiated by multiple attack sources ;
Three basic attributes of network security :
Confidentiality
integrity
Usability
In fact, auditability can also be added .
Confidentiality is also called confidentiality , It mainly refers to the outflow of control information , That is to ensure that information and information are not obtained and used by unauthorized persons , The main preventive measure is password technology ;
Integrity refers to the reliability of information , That is, information will not be forged 、 Tampering , The main preventive measures are verification and Certification Technology , Is to ensure that the system can be used normally .

Network security measures are generally based on the network TCP/IP perhaps OSI The model is classified to all levels , For example, the data link layer is responsible for establishing point-to-point communication , The network layer is responsible for routing , The transport layer is responsible for establishing end-to-end communication channels .
The earliest security problems occurred on computer platforms , Later, it gradually entered the network level , In computer security, the subject mainly controls the access rights of the object , The network contains more complex security issues . Now the development of network application is in full swing , E-government 、 Electronic Commerce 、 Electronic financial management has developed rapidly , These all pose challenges for dealing with security threats .
The application of cryptography in the field of network security is mainly confidentiality and identity authentication , Symmetric cryptosystems such as DES, Asymmetric cryptosystems such as RSA, The general way is RSA Protect DES secret key ,DES Responsible for the actual transmission of information , The reason lies in DES Make it fast ,RSA Occupy more computing resources than .
Two 、 risk analysis
The main task of risk analysis is to identify the assets that need to be protected and the potential threats they are subjected to . The first step is to identify assets , Including physical resources ( The workstation 、 Servers and various devices )、 Knowledge resources ( database 、 Financial information, etc ) And time and credit resources . The second step is to analyze potential attack sources , Such as internal employees , External enemies, etc ; The third step is to specify a compromise security policy for the above analysis , Because security measures are often inversely proportional to system performance . Risk is defined as vulnerability threat , Vulnerability refers to the way an attacker can attack . Threat refers to the specific behavior of realizing the attack , For risk , Lack of both — must not .

Security policies can be divided into many types , such as :
Information strategy : Such as identifying sensitive information 、 Information classification 、 Sensitive information marking / Storage / transmission / The destruction ;
System and network security policy : User identification and identity authentication 、 Access control 、 Audit 、 network connections 、 Encryption, etc ;
Computer user policy : Computer ownership 、 Information ownership 、 Computer license, etc ;
Internet Use policy : Mail policy ( Distinguish and filter internal mail from external mail ); User management program : New employee procedures 、 Employee procedures for job transfer 、 Procedures for leaving employees ;
System management program : Software update 、 Vulnerability scanning 、 Policy check 、 Login check 、 Routine monitoring, etc ;
Accident corresponding procedures : Respond to 、 to grant authorization 、 file 、 Program testing ;
Configuration Manager : Initial state of the system 、 Change control procedures
3、 ... and 、 Network information security services
Network information security services can be divided into :
confidential **
complete **
You can use **
Auditable **
confidential ** It mainly uses cryptography technology to encrypt files , Integrity mainly uses verification code /Hash technology , You can use ** Mainly for disaster recovery .
Identity authentication in the network environment , Of course, it depends on cryptography , A technology that can use passwords , The other is based on the identification of physical forms , Such as ID card . In fact, it is safer to implement multi factor identity authentication , Use more than one way . Digital signature can be used to ensure the integrity of information , such as RSA It can be used for digital signature :
if A towards B Send a message m Then use your own secret key first ( Private key ) Yes m encryption , And then use B The second encryption of public key , Send a B after ,B Decrypt it with your private key first , Reuse A Decrypt the public key of .
Kerberos The symmetric cryptographic algorithm is used to realize the authentication service through the trusted third-party key distribution center , It has become the de facto standard of industry .
Four 、 Security architecture
Design a security system , Attention should be paid to the following key issues : Subject and object 、 Trusted computing basis (TCB)、 Security boundary 、 Benchmark monitor and security kernel 、 Security domain 、 Minimum privilege 、 Resource isolation and layering 、 Data concealment and abstraction . In fact, these contents are the principles of operating system security design .
The network system mainly relies on OSI model , Provides 5 Class security services :
To identify , Identity authentication of peer entities 、 Original identification of data ;
Access control ;
Data confidentiality ;
Data integrity ;
Resist denial , Note here that neither the sender nor the receiver can deny ;
OSI Security mechanism of security architecture :
Specific security mechanisms : Encryption mechanism 、 Digital signature mechanism 、 Access control mechanism 、 Data integrity mechanism 、 Authentication exchange mechanism 、 Communication service filling mechanism 、 Routing control mechanism and notarization mechanism .
Universal security mechanism : Trusted functionality 、 Safety signs 、 Event detection 、 Safety audit and tracking 、 Security recovery .
5、 ... and 、 Extended data
1、 What can be done to ensure the safety of surfing the Internet before surfing the Internet ?
First , You need to install a personal firewall , Take advantage of privacy control features , You can choose which information needs to be kept confidential , Instead of accidentally sending these information to unsafe websites . such , It can also prevent the website server from tracking your email address and other personal information without your awareness .
secondly , Please install patches and updates of the system and other software in time . Basically, the earlier you update , The less risk . The data of firewall should also be updated in time .
2、 How to prevent hacker attacks ?
First , Use personal firewall anti-virus program to prevent hacker attacks and check hacker programs (— A software that connects to an external server and transmits your information ). Personal firewall can protect your computer and personal data from hackers , Prevent applications from automatically connecting to and sending information to websites .
secondly , When file and print sharing is not required , Turn off these functions . File and print sharing is sometimes a very useful feature , But this feature will also expose your computer to hackers looking for security vulnerabilities . Once you enter your computer , Hackers can steal your personal information .
3、 How to prevent computer poisoning ?
First , Don't open email attachments from strangers or files sent by instant messaging software . These files may contain a Trojan horse program , This program enables hackers to access your documents , Even control your peripherals , You should also install an anti-virus program to protect you from viruses 、 Trojan horse program and worm infringement .
4、 How to ensure information security when browsing the web ?
Browse anonymously , When you log in to the website, you will have a kind of phenomenon called cookie( Temporary files , You can save the traces of browsing the web ) Information storage , Many websites use cookie Track your activities on the Internet .
You can choose to turn off computer reception in the parameter options when using the browser cookie The option to .( open E browser , Click on “ Tools ”—“Internet Options ”, In the open options , choice “ privacy ”, keep “Cookies” The check box is not selected , Click button " determine ")
5、 How to ensure your information security when shopping online ?
When shopping online , Make sure you're using a secure connection . You can determine whether a connection is safe by checking whether the lock icon on the corner of the browser window is closed . Read the privacy policy of the website before making any transaction or sending information . Because some websites will sell your personal information to third parties . Don't disclose personal information and passwords to anyone while online .
6、 ... and 、 Q & A on basic knowledge of network security
ask ∶ What is network security ?
answer : Network security refers to the hardware of the network system 、 The data in the software and its system is protected , Not damaged by accidental or malicious reasons 、 change 、 Let the cat out of the , The system can operate continuously, reliably and normally , Network services are not interrupted .
ask : What is a computer virus ﹖
answer : Computer virus (Computer Virus ) It refers to the destruction of computer functions or data inserted by the programmer in the computer program , A set of computer instructions or program codes that affect the use of a computer and can be copied by itself .
ask : What is a Trojan ?
answer : Trojan horse is a kind of remote control software with malicious nature . Trojans are generally divided into client ( client ) And the server side ( server ). The client is the console of various commands used locally , The server side is to run for others , Only computers that have run on the server side can be fully controlled . Trojans don't infect files like viruses .
ask ∶ What is a firewall ﹖ How does it ensure network security ?
answer : Use a firewall (Firewall ) Is a way to ensure network security . Firewalls are set up on different networks ( Such as trusted intranet and untrusted public network ) Or a combination of components between network security domains . It is the only entry and exit of information between different network or network security domains , Be able to control according to the safety policy of the enterprise ( allow 、 Refuse 、 monitoring ) Information flow in and out of the network , And it has strong anti attack ability . It's about providing information security services , Infrastructure for network and information security .
ask : What is the back door ﹖ Why there is a back door ?
answer : back door ( Back Door ) It refers to a method of gaining access to a program or system by bypassing security controls . In the software development phase , Programmers often create backdoors in software so that they can fix bugs in their programs . If the back door is known to others , Or not deleted before releasing the software , Then it becomes a security risk .
ask ∶ What is intrusion detection ﹖
answer ∶ Intrusion detection is a reasonable supplement to firewall , Help systems deal with cyber attacks , Expand the security management ability of system administrator ( Including security audit 、 monitor 、 Attack recognition and response ), Improve the integrity of the information security infrastructure . It collects information from several key points in a computer network system , And analyze the information , Check the network for security policy violations and signs of attack .
ask : What is packet monitoring ﹖ What does it do ?
answer : Packet monitoring can be considered as the equivalent of a wiretap in a computer network . When someone is in “ monitor ” When the network , They are actually reading and interpreting packets that are transmitted over the network . If you need to send an email or request to download a web page on the Internet through a computer , All of these operations allow data to pass through many computers between you and the data destination . The computers that pass through these messages can see the data you send , And the packet monitoring tool allows someone to intercept the data and view it .
ask ∶ What is? NIDS ?
answer :NIDS yes Network Intrusion Detection System Abbreviation , Network intrusion detection system , It is mainly used to detect Hacker or Cracker Intrusion through the network .NIDS There are two ways to run , One is to run on the target host to monitor its own communication information , The other is to run on a single machine to monitor the communication information of all network devices , such as Hub、 Router .
ask ∶ What do you mean SYN package ?
answer :TCP The first package connected , A very small packet .SYN Attacks include a large number of such packages , Because these packages seem to come from sites that don't actually exist , So it can't be processed effectively .
ask : What is encryption ?
answer : Encryption technology is the most commonly used means of security , Use technology to turn important data into garbled code ( encryption ) delivery , After arriving at the destination, restore by the same or different means ( Decrypt ).
Encryption consists of two elements :
Algorithm
secret key
The algorithm is to combine common information or understandable information with a series of numbers ( secret key ) combination , The steps to produce incomprehensible ciphertext , A key is an algorithm used to encode and decrypt data . In security , The information communication security of the network can be guaranteed through appropriate key encryption technology and management mechanism .
ask : What is a worm ﹖
answer ∶ worm-type virus ( Worm) From the first virus that spreads on the network .1988 year ,22 Robert, a 19-year-old graduate student at Cornell University · Maurice ( Robert Morris ) A special attack was sent over the network UNIX System defects 、 be known as “ worm ”( Worm ) The virus of . Worms cause 6000 A system is down , The estimated loss is 200 Wan to 6000 Thousands of dollars . Because of the birth of this worm , A computer emergency response team has also been set up on the Internet (CERT ). Now the worm family has grown to thousands of species , And most of these ten million kinds of worms are created by hackers .
ask ∶ What is an operating system virus ﹖ What harm does it do ?
answer : This virus will use its own program to join the operating system or replace part of the operating system to work , It has strong destructive power , It will lead to the paralysis of the whole system . And because of infection with the operating system , This virus runs , It will replace the legal program module of the operating system with its own program fragments . According to the characteristics of the virus itself and the status and role of the legal program module in the replaced operating system , And the way in which viruses replace operating systems , Destroy the operating system . meanwhile , This virus is also very infectious to the files in the system .
ask : What does Morris worm mean ﹖ What are its characteristics ?
answer ∶ Its author is Cornell University — Grade graduate student lot · Maurice . This program only 99 That's ok , Take advantage of Unix Shortcomings in the system , use Finger Command to check the list of online users , Then crack the user password , use Mail System Replication 、 Propagate its own source program , Recompile the generated code .
The original design purpose of network worm is when the network is idle , The program is in the computer room “ Wander ” Without any damage . When a machine is overloaded , The program can be downloaded from idle computers “ Borrow resources ” And achieve the load balance of the network . Morris worm is not “ Borrow resources ”, It is “ Exhaust all resources ”.
ask : What is? DDoS ? What consequences will it lead to ?
answer :DDoS Distributed denial of service attack . It uses the same method as a normal denial of service attack , But there are multiple sources of attack .
Usually attackers use downloaded tools to penetrate unprotected hosts , After obtaining the appropriate access rights of the host , An attacker installs a service or process of software in the host ( Hereinafter referred to as agent ). These agents stay asleep , Until they get instructions from their master , Launch a denial of service attack on the specified target . With the widespread spread and use of hacker tools with strong harmfulness , Distributed denial of service attacks can launch thousands of attacks on a target at the same time . The power of a single denial of service attack may have no impact on sites with wide bandwidth , And thousands of attacks distributed around the world will have fatal consequences .
ask ∶ LAN internal ARP What does an attack mean ?
answer :ARP The basic function of the protocol is through the target device IP Address , Query the... Of the target device MAC Address , In order to ensure the communication .
be based on ARP This working feature of the protocol , Hackers constantly send fraudulent messages to each other's computers ARP Data packets , The packet contains the same... As the current device Mac Address , Make the other party respond to the message , Due to simple address repetition error, normal network communication can not be carried out .
In general , suffer ARP There are two phenomena in the attacking computer ∶
Keep popping up “ Native XXX Segment hardware address and XXX Segment address conflict ” The dialog . The computer can't access the Internet normally , There are symptoms of network disruption . Because this attack is using ARP Request message for “ cheating ” Of , So the firewall will mistake it as a normal request packet , No interception . So ordinary firewalls are hard to resist this kind of attack .
ask ∶ What is cheating attack ? What kind of attacks does it have ?
answer ∶ The technology of network cheat mainly has :HONEYPOT And distributed HONEYPOT、 Deceiving space technology, etc .
The main ways are :
IP cheating 、 ARP cheating 、 DNS cheating 、 Web cheating 、 Email spoofing 、 Source routing spoofing ( By specifying the route , Legally communicate with other hosts or send fake messages as a fake identity , Cause the attacked host to behave incorrectly )、 Address spoofing ( Including forged source address and forged intermediate site ) etc. .
边栏推荐
- Using variables in sed command
- 剑指 Offer II 029. 排序的循环链表
- Allocation exception Servlet
- Drawing maze EasyX library with recursive backtracking method
- Dom4j traverses and updates XML
- [concurrent programming] concurrent security
- Es8 async and await learning notes
- Final review of Database Principles
- 22-06-28 西安 redis(02) 持久化机制、入门使用、事务控制、主从复制机制
- Alibaba canal actual combat
猜你喜欢
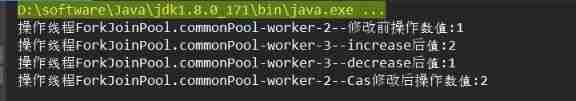
Concurrent programming (VI) ABA problems and solutions under CAS
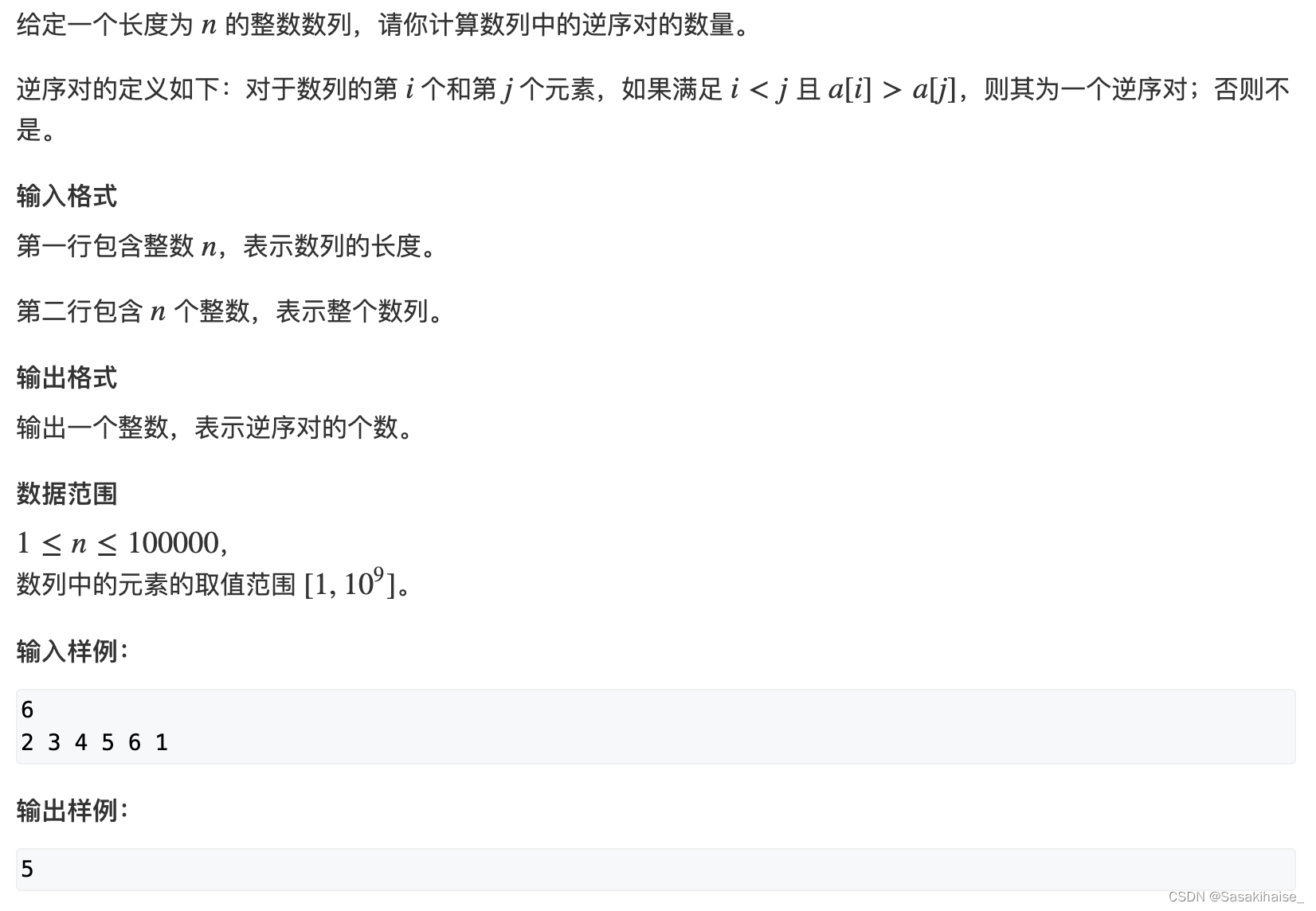
AcWing 788. 逆序对的数量
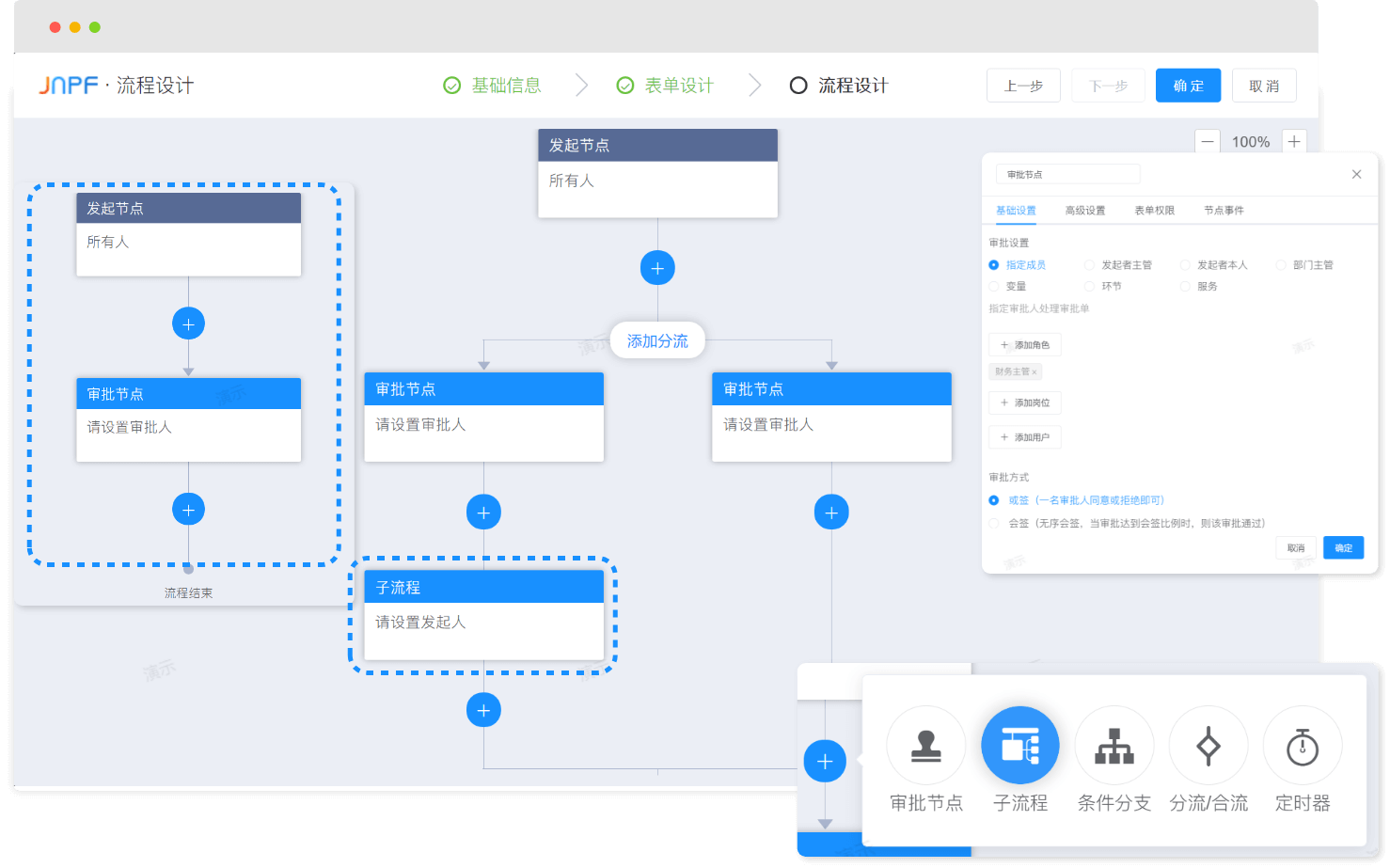
推荐一个 yyds 的低代码开源项目

Tree DP acwing 285 A dance without a boss

Alibaba canaladmin deployment and canal cluster Ha Construction
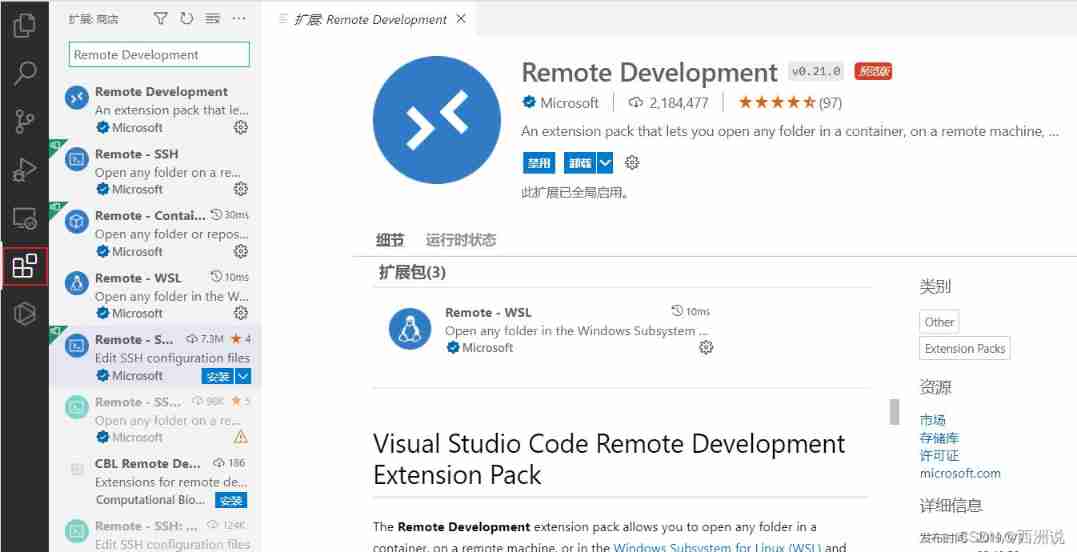
Vscode connect to remote server

LeetCode 513. 找树左下角的值

Drawing maze EasyX library with recursive backtracking method

LeetCode 515. 在每个树行中找最大值

Deep parsing (picture and text) JVM garbage collector (II)
随机推荐
Alibaba canal actual combat
[rust notes] 08 enumeration and mode
低代码起势,这款信息管理系统开发神器,你值得拥有!
我们有个共同的名字,XX工
Deeply understand the underlying data structure of MySQL index
Noip 2002 popularity group selection number
即时通讯IM,是时代进步的逆流?看看JNPF怎么说
How to deal with the core task delay caused by insufficient data warehouse resources
[concurrent programming] concurrent security
22-05-26 西安 面试题(01)准备
[rust notes] 11 practical features
LeetCode 535. TinyURL 的加密与解密
Alibaba canaladmin deployment and canal cluster Ha Construction
[rust note] 10 operator overloading
LeetCode 438. 找到字符串中所有字母异位词
Life cycle of Servlet
How to use Jupiter notebook
AcWing 786. 第k个数
传统企业数字化转型需要经过哪几个阶段?
LeetCode 1089. 复写零