当前位置:网站首页>Go deep into the details of deconstruction and assignment of several data types in JS
Go deep into the details of deconstruction and assignment of several data types in JS
2022-07-04 15:26:00 【InfoQ】
Deconstruct assignment
- deconstruction: Can be separated from the values in an array or object
- assignment: Assign values to variables based on the deconstructed data
var a = 1;
var b = 2;
let [a,b] = [1,2] // Equivalent to the above
An array of deconstruction
Nested deconstruction
let [a,[b],c] = [1,[1,2],3]
console.log(a,b,c) // 1 1 3
The extension operator deconstructs
...let [a,...b] = [1,2,3,4]
console.log(a,b)
// a = 1 b = [2,3,4]
Incomplete deconstruction
let [, , a] = [1,2,3]
console.log(a) // 3
Unsuccessful deconstruction
let [a] = 1
console.log(a) // TypeError: 1 is not iterable
blet [a,b] = [1]
console.log(a,b) // 1 undefined
About
interator
1 is not iterableinteratorinteratorundefinednullNaNinteratorinteratorinteratorDeconstruction assignment with default values
let [a,b=2] = [1]
console.log(a,b) // 1 2
let [c = 1] = [undefined]
console.log(c) // 1
About
undefined
The problem of
NaNnulllet [c = 1] = [NaN]
console.log(c) // NaN
let [c = 1] = [null]
console.log(c) // null
===NaNnullundefinedObject to deconstruct
Different from array deconstruction
let {name} = {name:" Pig ruffian bully "}
console.log(name) // Pig ruffian bully
Variable name does not match property name
:let {name:difname} = {name:" Pig ruffian bully "}
console.log(difname) // Pig ruffian bully
nameDeconstruction assignment of multi-level nested objects
let people = {
name:" Pig ruffian bully ",
like:{
community:"juejin",
code:"js"
}
}
let {name,like:{code}} = people
console.log(name,code) // Pig ruffian bully js
codelikelikecodePattern problem
likelike is not definedString deconstruction
let str = " Pig ruffian bully "
let {1:first} = str
console.log(first) // Ruffian
let str = " Pig ruffian bully "
let [a] = str
console.log(a) // The pig
let str = " Pig ruffian bully "
let {length} = str
console.log(length) // 4
Numeric and Boolean deconstruction
let { toFixed:a} = 123
console.log(a) // toFixed() { [native code] }
toFixedUse prototype chain to judge
toFixedconsole.log(a === Number.prototype.toFixed) // true
Deconstruction of function parameters
function add([x,y]) {
return x+y
}
add([1,2]) // 3
let arr = [[1,2],[2,3]]
arr.map((item) => item[0]+item[1])
let arr = [[1,2],[2,3]]
arr.map(([a,b]) => a+b)
Deconstructive ambiguity
===reference
- ES6 Introduction to standards, Third Edition
边栏推荐
- PXE network
- 【读书会第十三期】 音频文件的封装格式和编码格式
- 基于MAX31865的温度控制系统
- Introduction of text mining tools [easy to understand]
- go-zero微服务实战系列(九、极致优化秒杀性能)
- Unity脚本常用API Day03
- Unity update process_ Principle of unity synergy
- Live broadcast preview | PostgreSQL kernel Interpretation Series II: PostgreSQL architecture
- 宽度与对齐
- MySQL~MySQL给已有的数据表添加自增ID
猜你喜欢

音视频技术开发周刊 | 252

Helix Swarm中文包发布,Perforce进一步提升中国用户体验

MySQL学习笔记——数据类型(2)

Live broadcast preview | PostgreSQL kernel Interpretation Series II: PostgreSQL architecture
MySQL组合索引(多列索引)使用与优化案例详解

夜天之书 #53 Apache 开源社群的“石头汤”
![[local differential privacy and random response code implementation] differential privacy code implementation series (13)](/img/fe/f6a13dcf31ac67633ee5a59d95149d.jpg)
[local differential privacy and random response code implementation] differential privacy code implementation series (13)
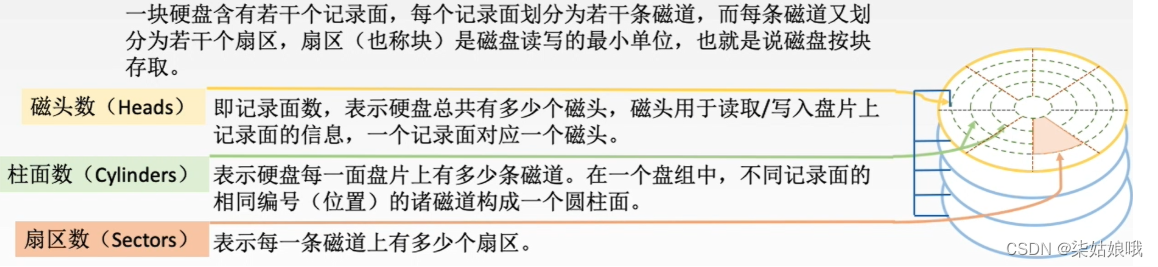
03 storage system
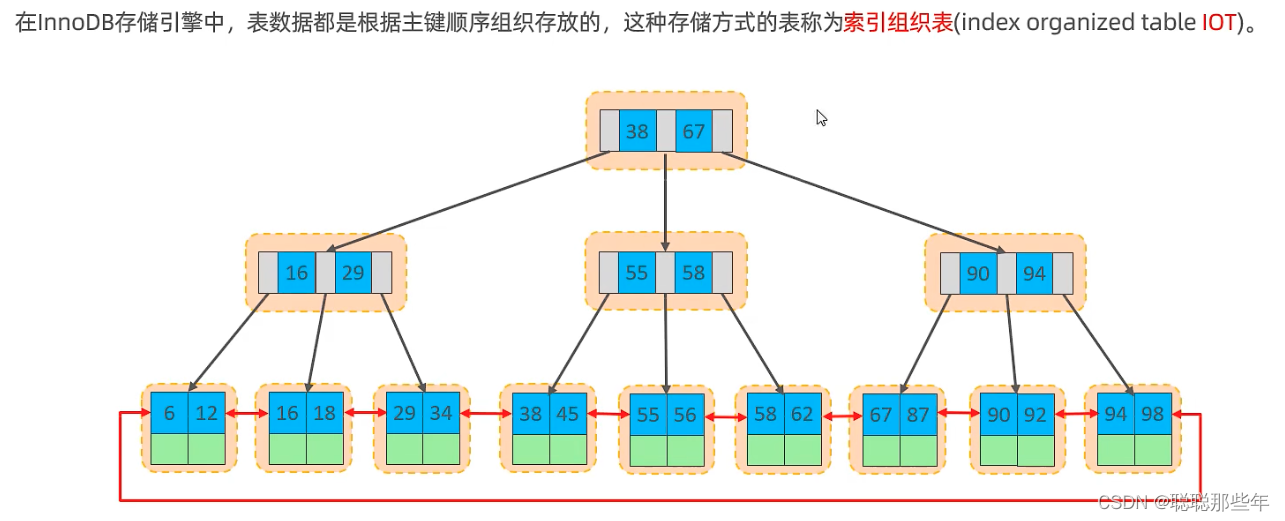
MYSQL索引优化
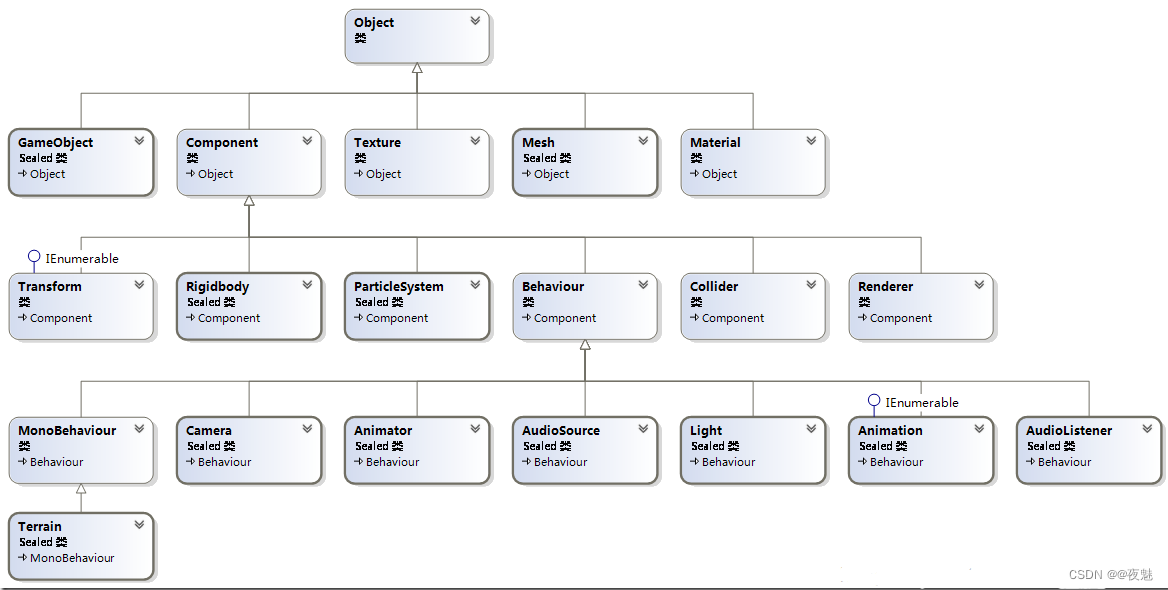
Common API day03 of unity script
随机推荐
Common API day03 of unity script
左右对齐!
Redis publish and subscribe
力扣刷题01(反转链表+滑动窗口+LRU缓存机制)
Width accuracy
Optimization method of deep learning neural network
%S format character
Lombok使用引发的血案
每周招聘|高级DBA年薪49+,机会越多,成功越近!
這幾年爆火的智能物聯網(AIoT),到底前景如何?
Summer Review, we must avoid stepping on these holes!
. Net applications consider x64 generation
浮点数如何与0进行比较?
Ffprobe common commands
Align left and right!
Introduction to modern control theory + understanding
Force button brush question 01 (reverse linked list + sliding window +lru cache mechanism)
Data Lake Governance: advantages, challenges and entry
PXE网络
大神详解开源 BUFF 增益攻略丨直播