当前位置:网站首页>The fuse: OAuth 2.0 four authorized login methods must read
The fuse: OAuth 2.0 four authorized login methods must read
2022-08-05 10:17:00 【InfoQ】
- About authorized login includes three terminals, resource owner (user), resource server (website storing user resources), pageThird-party website.
- OAuth is a layer used to separate users and third-party websites. After the user agrees, the resource server can issue tokens to the third-party websites, and the firstThe third-party website can access the information of the resource server corresponding to the user through this token.
Four ways of OAuth2.0 authorization
Premise: No matter which way, the third-party website needs to register with the resource server in advanceIdentity, get the corresponding appid and secret, in order to prevent the token from being used indiscriminately.authorization-code
- First, the third-party website carries the appid, secrect and redirect_url to the resource server to get the QR code for login
- Pass the confirmation notification to the resource server after the user scans the code
- The resource server returns according to the redirect_url in the first stepauthorization-codeand the login success status
- After the third party obtains the authorization-code, it will bring its own previously registered appid, secrect and authorization-code to the resource server to obtain the token
- Then the third-party website can go to the resource server to obtain the user information according to the token, and then it can wake up the follow-up operation.
Hidden (implicit)
- The third-party website carries the appid, secrect and redirect_url to the resource server to obtain the login QR code
- After the user scans the code, the confirmation notification is sent to the resource server
- The resource server follows the firstThe redirect_url of the step returnstokenand the successful login status
- and then the third-party website according to the tokenGo to the resource server to get the user information and you can do the follow-up operations
password
- ported by the third-party websiteUsername and password go to the resource server to get the token
- Then the third-party website can go to the resource server to obtain the user information according to the token, and then follow-up operations can be done
client credentials (client credentials)
- Get the token from the resource server by carrying the appid and secrect on the command line
- Then the command line goes to the resource server to obtain user information according to the token, and then the follow-up operations can be done
Summary
边栏推荐
- 第五章:activiti流程分流判断,判断走不同的任务节点
- 19. Server-side session technology Session
- three物体围绕一周呈球形排列
- Pytorch Deep Learning Quick Start Tutorial -- Mound Tutorial Notes (3)
- 第三章 : redis数据结构种类
- egg框架使用(二)
- What is the function of the regular expression replaceAll() method?
- uniapp 连接ibeacon
- Wei Dongshan Digital Photo Frame Project Learning (6) Transplantation of tslib
- IDEA performs the Test operation, resulting in duplicate data when data is inserted
猜你喜欢

Advanced usage of C language
JS逆向入门学习之回收商网,手机号码简易加密解析

How can project cost control help project success?
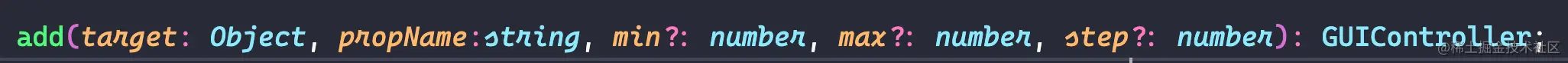
three.js调试工具dat.gui使用

电竞、便捷、高效、安全,盘点OriginOS功能的关键词
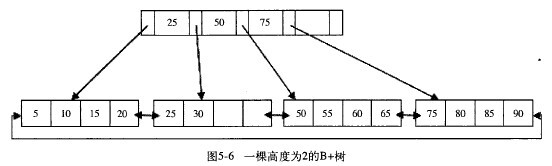
MySQL advanced (twenty-seven) database index principle

Oracle临时表空间作用
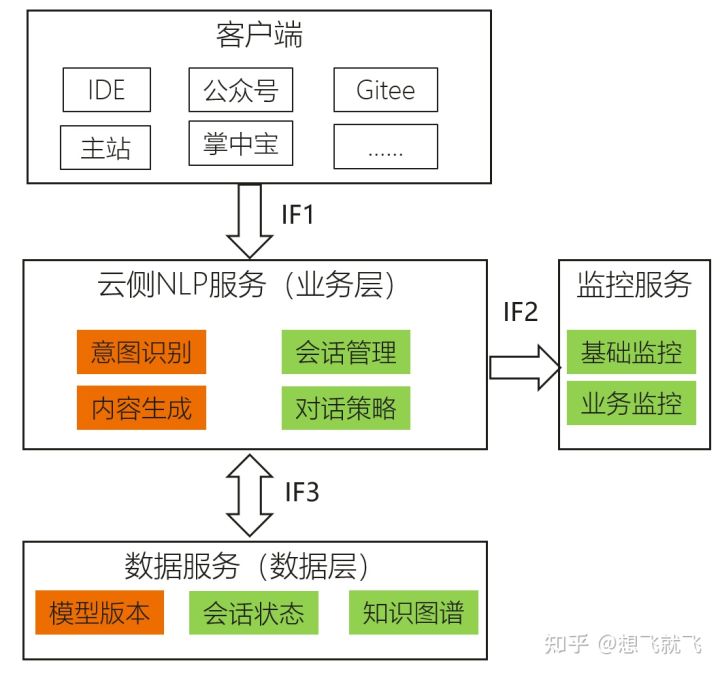
【MindSpore易点通机器人-01】你也许见过很多知识问答机器人,但这个有点不一样
Bias lock/light lock/heavy lock lock is healthier. How is locking and unlocking accomplished?

What is SPL?
随机推荐
首次去中心化抢劫?近2亿美元损失:跨链桥Nomad 被攻击事件分析
【MindSpore Easy-Diantong Robot-01】You may have seen many knowledge quiz robots, but this one is a bit different
JS逆向入门学习之回收商网,手机号码简易加密解析
PHP operation mangoDb
Open Source Summer | How OpenHarmony Query Device Type (eTS)
How can project cost control help project success?
入门 Polkadot 平行链开发,看这一篇就够了
Analysis and practice of antjian webshell dynamic encrypted connection
FPGA: Use of the development environment Vivado
第四章:activiti流程中,变量的传递和获取流程变量 ,设置和获取多个流程变量,设置和获取局部流程变量「建议收藏」
Egg framework usage (1)
Wei Dongshan Digital Photo Frame Project Learning (6) Transplantation of tslib
产品太多了,如何实现一次登录多产品互通?
【温度预警程序de开发】事件驱动模型实例运用
Introduction to SD NAND Flash!
ffmpeg drawtext 添加文本水印
First Decentralized Heist?Loss of nearly 200 million US dollars: analysis of the attack on the cross-chain bridge Nomad
还在找网盘资源吗?快点收藏如下几个值得收藏的网盘资源搜索神器吧!
three.js debugging tool dat.gui use
数据中台建设(十):数据安全管理