当前位置:网站首页>Use of unsafe class
Use of unsafe class
2022-07-03 18:03:00 【Spring comes again】
Unsafe The use of the class
Unsafe It can be used to directly access the system memory resources and manage them independently , In the promotion Java Operational efficiency 、 enhance Java The language bottom level operation ability aspect has played the very big role —— It can be said that ,Unsafe Class is Java The back door left in , Provides some low-level operations , Such as direct memory access 、 Thread scheduling, etc .
Unsafe Do not belong to Java standard . The official does not recommend the use of Unsafe, And from JDK 9 Start , Official start Unsafe!
relevant Issue:https://bugs.java.com/bugdatabase/view_bug.do?bug_id=6852936
therefore ,Unsafe Class for project practice , It doesn't mean much . However, at present, there are many easy-to-use class libraries in the industry Unsafe class , for example java.util.concurrent.atomic A bunch of classes in the bag 、Netty、Hadoop、Kafka etc. . So it's good to know .
Different JDK In the version ,Unsafe Classes are also different , for example :
- stay JDK 8 Belong to sun.misc It's a bag ;
- stay JDK 11 Belong to sun.misc Package or jdk.internal.misc Next , among jdk.internal.misc Under the Unsafe Class is more powerful .( Should be from JDK 9 At the beginning , The author did not test it personally )
Quick start
import sun.misc.Unsafe;
import java.lang.reflect.Field;
public class DirectMemoryTest1 {
private static final int _1MB = 1024 * 1024;
public static void main(String[] args) throws IllegalAccessException {
// Get by reflection Unsafe Class and allocate direct memory through it
Field unsafeField = Unsafe.class.getDeclaredFields()[0];
unsafeField.setAccessible(true);
Unsafe unsafe = (Unsafe) unsafeField.get(null);
int i = 0;
while (true) {
unsafe.allocateMemory(_1MB);
System.out.println(++i);
}
}
}
Unsafe The use of the class
See :
- https://www.jb51.net/article/140726.htm
- https://blog.csdn.net/ahilll/article/details/81628215
- https://www.jianshu.com/p/dd2be4d3b88e
JDK 11 How to use Unsafe class
TIPS
- Again , In actual projects , Unless it is necessary , Try not to use Unsafe class , The official does not recommend the use of
- from JDK 10 Start ,Unsafe Some functions of class have been VarHandle replace , Suggest using VarHandle
Create a JDK 11 Project
Create under the project source code path
module-info.java, The contents are as follows :module unsafe { requires jdk.unsupported; }After creation , The code structure is as follows :
|____src | |____main | | |____java | | | |____module-info.java | | | |____com | | | | |____example | | | | | |____demo | | | | | | |____UnsafePlayer.java | | | | | | |____DirectMemoryTest1.javaTest code :
import sun.misc.Unsafe; import java.lang.reflect.Field; public class DirectMemoryTest1 { private static final int _1MB = 1024 * 1024; public static void main(String[] args) throws IllegalAccessException { // Get by reflection Unsafe Class and allocate direct memory through it Field unsafeField = Unsafe.class.getDeclaredFields()[0]; unsafeField.setAccessible(true); Unsafe unsafe = (Unsafe) unsafeField.get(null); int i = 0; while (true) { unsafe.allocateMemory(_1MB); System.out.println(++i); } } }
Reference documents
边栏推荐
- MySQL grouping query
- A. Odd Selection【BruteForce】
- 分布式的任务分发框架-Gearman
- How to draw non overlapping bubble chart in MATLAB
- Website with JS doesn't work in IE9 until the Developer Tools is activated
- Postfix 技巧和故障排除命令
- [untitled]
- Talk about the design and implementation logic of payment process
- 微服务组件Sentinel控制台调用
- Assembly for unloading Loadfrom() loaded assembly - unloading the assembly loaded with assembly LoadFrom()
猜你喜欢

Line by line explanation of yolox source code of anchor free series network (5) -- mosaic data enhancement and mathematical understanding

面试官:值为 nil 为什么不等于 nil ?

Redis core technology and practice - learning notes (VI) how to achieve data consistency between master and slave Libraries

Cloud primordial weekly | CNCF released the 2021 cloud primordial development status report, which was released on istio 1.13

Research on Swift
![[combinatorics] generating function (generating function application scenario | using generating function to solve recursive equation)](/img/e6/9880e708aed42dc82c94aea002020c.jpg)
[combinatorics] generating function (generating function application scenario | using generating function to solve recursive equation)
![AcWing 271. Teacher Yang's photographic arrangement [multidimensional DP]](/img/3d/6d61fefc62063596221f98999a863b.png)
AcWing 271. Teacher Yang's photographic arrangement [multidimensional DP]
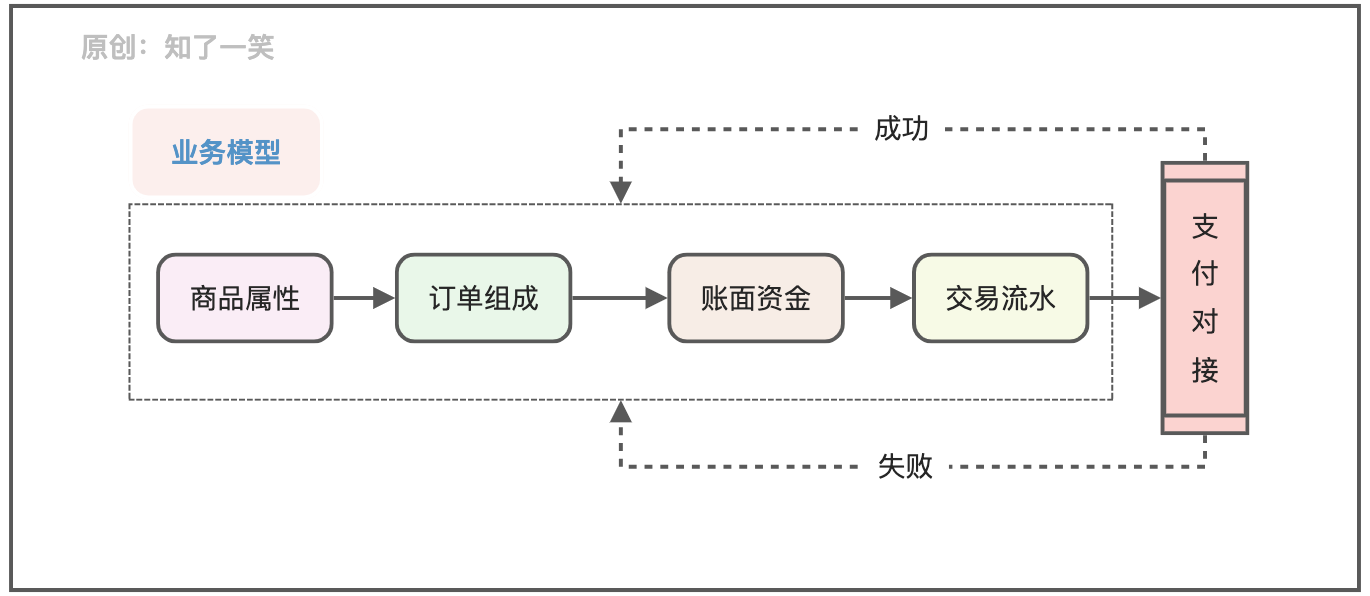
聊聊支付流程的设计与实现逻辑
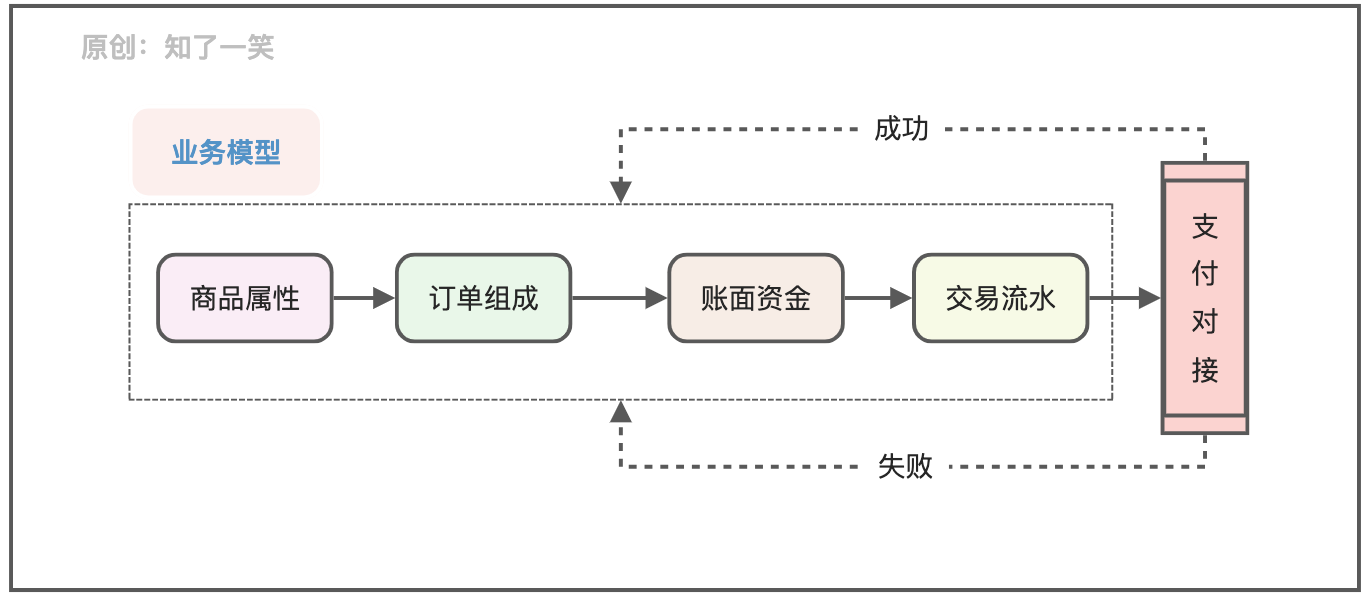
聊聊支付流程的设计与实现逻辑
![[set theory] order relation: summary (partial order relation | partial order set | comparable | strictly less than | covering | hasto | total order relation | quasi order relation | partial order rela](/img/df/a034032e203e7935dafaf8a71cb6c8.jpg)
[set theory] order relation: summary (partial order relation | partial order set | comparable | strictly less than | covering | hasto | total order relation | quasi order relation | partial order rela
随机推荐
How to deploy applications on kubernetes cluster
Should I be laid off at the age of 40? IBM is suspected of age discrimination, calling its old employees "dinosaurs" and planning to dismiss, but the employees can't refute it
Fedora 21 installs lamp host server
Kotlin的协程:上下文
Automata and automatic line of non-standard design
Module 9 operation
Image 24 bit depth to 8 bit depth
(8) HS corner detection
Managing multiple selections with MVVM - managing multiple selections with MVVM
The gbase 8A database does not support the DB2 function value (column_name, 0) cluster syntax
小程序 多tab 多swiper + 每个tab分页
The number of incremental paths in the grid graph [dfs reverse path + memory dfs]
[combinatorics] generating function (generating function application scenario | using generating function to solve recursive equation)
Win32: analyse du fichier dump pour la défaillance du tas
Ssl/bio of OpenSSL_ get_ fd
[enumeration] annoying frogs always step on my rice fields: (who is the most hateful? (POJ hundred practice 2812)
Leetcode Valentine's Day Special - looking for a single dog
聊聊支付流程的設計與實現邏輯
聊聊支付流程的设计与实现逻辑
Cloud primordial weekly | CNCF released the 2021 cloud primordial development status report, which was released on istio 1.13