当前位置:网站首页>DASCTF2022.07赋能赛密码wp
DASCTF2022.07赋能赛密码wp
2022-07-27 07:03:00 【mxx307】
DASCTF2022.07赋能赛 WriteUp
CRYPTO
babysign
已知 r , s , n o n c e , m s g , o r d e r r,s,nonce,msg,order r,s,nonce,msg,order, k = n o n c e k = nonce k=nonce, s = k − 1 ∗ ( m s g + r ∗ s e c r e t ) % o r d e r s = k^{-1} * (msg + r*secret)\% order s=k−1∗(msg+r∗secret)%order
其中 o r d e r order order为固定值
import hashlib
import ecdsa
from Crypto.Util.number import *
r = int('7b35712a50d463ac5acf7af1675b4b63ba0da23b6452023afddd58d4891ef6e5', 16)
s = int('a452fc44cc36fa6964d1b4f47392ff0a91350cfd58f11a4645c084d56e387e5c', 16)
nonce = 57872441580840888721108499129165088876046881204464784483281653404168342111855
msg = b'welcome to ecdsa'
msg = int(hashlib.sha256(msg).hexdigest(), 16)
gen = ecdsa.NIST256p.generator
order = gen.order()
secret = (s * nonce - msg) * inverse(r, order) % order
print(b'DASCTF{' + long_to_bytes(secret) + b'}')
# b'DASCTF{11b7311d4f0137074a7256d3eb82f368}'
easyNTRU
n = 10 n=10 n=10很小直接爆破 m m m
from Crypto.Hash import SHA3_256
from Crypto.Cipher import AES
c = b'\xb9W\x8c\x8b\x0cG\xde\x7fl\xf7\x03\xbb9m\x0c\xc4L\xfe\xe9Q\xad\xfd\xda!\x1a\[email protected]}U\x9ay4\x8a\xe3y\xdf\xd5BV\xa7\x06\xf9\x08\x96="f\xc1\x1b\xd7\xdb\xc1j\x82F\x0b\x16\x06\xbcJMB\xc8\x80'
R.<x> = ZZ[]
import itertools
t = [1, 0, -1]
for i in itertools.product(t,repeat=10):
m = list(i)
m = R(m)
sha3 = SHA3_256.new()
sha3 = sha3.update(bytes(str(m).encode('utf-8')))
key = sha3.digest()
cypher = AES.new(key, AES.MODE_ECB)
m = cypher.decrypt(c)
if b'DASCTF' in m:
print(m)
# b'DASCTF{b437acf4-aaf8-4f8f-ad84-5b1824f5af9c}\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14\x14'
NTRURSA
先多项式RSA分解求 h i n t hint hint( h h h),然后 N T R U NTRU NTRU求 g 1 g1 g1,最后爆破 r a n d rand rand求 g g g,之后就是普通的 r s a rsa rsa。脚本网上都有,拿来用就行。
from Crypto.Util.number import *
p= 64621
P = PolynomialRing(Zmod(p), name = 'x')
x = P.gen()
e = 0x10001
n = 25081*x^175 + 8744*x^174 + 9823*x^173 + 9037*x^172 + 6343*x^171 + 42205*x^170 + 28573*x^169 + 55714*x^168 + 17287*x^167 + 11229*x^166 + 42630*x^165 + 64363*x^164 + 50759*x^163 + 3368*x^162 + 20900*x^161 + 55947*x^160 + 7082*x^159 + 23171*x^158 + 48510*x^157 + 20013*x^156 + 16798*x^155 + 60438*x^154 + 58779*x^153 + 9289*x^152 + 10623*x^151 + 1085*x^150 + 23473*x^149 + 13795*x^148 + 2071*x^147 + 31515*x^146 + 42832*x^145 + 38152*x^144 + 37559*x^143 + 47653*x^142 + 37371*x^141 + 39128*x^140 + 48750*x^139 + 16638*x^138 + 60320*x^137 + 56224*x^136 + 41870*x^135 + 63961*x^134 + 47574*x^133 + 63954*x^132 + 9668*x^131 + 62360*x^130 + 15244*x^129 + 20599*x^128 + 28704*x^127 + 26857*x^126 + 34885*x^125 + 33107*x^124 + 17693*x^123 + 52753*x^122 + 60744*x^121 + 21305*x^120 + 63785*x^119 + 54400*x^118 + 17812*x^117 + 64549*x^116 + 20035*x^115 + 37567*x^114 + 38607*x^113 + 32783*x^112 + 24385*x^111 + 5387*x^110 + 5134*x^109 + 45893*x^108 + 58307*x^107 + 33821*x^106 + 54902*x^105 + 14236*x^104 + 58044*x^103 + 41257*x^102 + 46881*x^101 + 42834*x^100 + 1693*x^99 + 46058*x^98 + 15636*x^97 + 27111*x^96 + 3158*x^95 + 41012*x^94 + 26028*x^93 + 3576*x^92 + 37958*x^91 + 33273*x^90 + 60228*x^89 + 41229*x^88 + 11232*x^87 + 12635*x^86 + 17942*x^85 + 4*x^84 + 25397*x^83 + 63526*x^82 + 54872*x^81 + 40318*x^80 + 37498*x^79 + 52182*x^78 + 48817*x^77 + 10763*x^76 + 46542*x^75 + 36060*x^74 + 49972*x^73 + 63603*x^72 + 46506*x^71 + 44788*x^70 + 44905*x^69 + 46112*x^68 + 5297*x^67 + 26440*x^66 + 28470*x^65 + 15525*x^64 + 11566*x^63 + 15781*x^62 + 36098*x^61 + 44402*x^60 + 55331*x^59 + 61583*x^58 + 16406*x^57 + 59089*x^56 + 53161*x^55 + 43695*x^54 + 49580*x^53 + 62685*x^52 + 31447*x^51 + 26755*x^50 + 14810*x^49 + 3281*x^48 + 27371*x^47 + 53392*x^46 + 2648*x^45 + 10095*x^44 + 25977*x^43 + 22912*x^42 + 41278*x^41 + 33236*x^40 + 57792*x^39 + 7169*x^38 + 29250*x^37 + 16906*x^36 + 4436*x^35 + 2729*x^34 + 29736*x^33 + 19383*x^32 + 11921*x^31 + 26075*x^30 + 54616*x^29 + 739*x^28 + 38509*x^27 + 19118*x^26 + 20062*x^25 + 21280*x^24 + 12594*x^23 + 14974*x^22 + 27795*x^21 + 54107*x^20 + 1890*x^19 + 13410*x^18 + 5381*x^17 + 19500*x^16 + 47481*x^15 + 58488*x^14 + 26433*x^13 + 37803*x^12 + 60232*x^11 + 34772*x^10 + 1505*x^9 + 63760*x^8 + 20890*x^7 + 41533*x^6 + 16130*x^5 + 29769*x^4 + 49142*x^3 + 64184*x^2 + 55443*x + 45925
c = 19921*x^174 + 49192*x^173 + 18894*x^172 + 61121*x^171 + 50271*x^170 + 11860*x^169 + 53128*x^168 + 38658*x^167 + 14191*x^166 + 9671*x^165 + 40879*x^164 + 15187*x^163 + 33523*x^162 + 62270*x^161 + 64211*x^160 + 54518*x^159 + 50446*x^158 + 2597*x^157 + 32216*x^156 + 10500*x^155 + 63276*x^154 + 27916*x^153 + 55316*x^152 + 30898*x^151 + 43706*x^150 + 5734*x^149 + 35616*x^148 + 14288*x^147 + 18282*x^146 + 22788*x^145 + 48188*x^144 + 34176*x^143 + 55952*x^142 + 9578*x^141 + 9177*x^140 + 22083*x^139 + 14586*x^138 + 9748*x^137 + 21118*x^136 + 155*x^135 + 64224*x^134 + 18193*x^133 + 33732*x^132 + 38135*x^131 + 51992*x^130 + 8203*x^129 + 8538*x^128 + 55203*x^127 + 5003*x^126 + 2009*x^125 + 45023*x^124 + 12311*x^123 + 21428*x^122 + 24110*x^121 + 43537*x^120 + 21885*x^119 + 50212*x^118 + 40445*x^117 + 17768*x^116 + 46616*x^115 + 4771*x^114 + 20903*x^113 + 47764*x^112 + 13056*x^111 + 50837*x^110 + 22313*x^109 + 39698*x^108 + 60377*x^107 + 59357*x^106 + 24051*x^105 + 5888*x^104 + 29414*x^103 + 31726*x^102 + 4906*x^101 + 23968*x^100 + 52360*x^99 + 58063*x^98 + 706*x^97 + 31420*x^96 + 62468*x^95 + 18557*x^94 + 1498*x^93 + 17590*x^92 + 62990*x^91 + 27200*x^90 + 7052*x^89 + 39117*x^88 + 46944*x^87 + 45535*x^86 + 28092*x^85 + 1981*x^84 + 4377*x^83 + 34419*x^82 + 33754*x^81 + 2640*x^80 + 44427*x^79 + 32179*x^78 + 57721*x^77 + 9444*x^76 + 49374*x^75 + 21288*x^74 + 44098*x^73 + 57744*x^72 + 63457*x^71 + 43300*x^70 + 1508*x^69 + 13775*x^68 + 23197*x^67 + 43070*x^66 + 20751*x^65 + 47479*x^64 + 18496*x^63 + 53392*x^62 + 10387*x^61 + 2317*x^60 + 57492*x^59 + 25441*x^58 + 52532*x^57 + 27150*x^56 + 33788*x^55 + 43371*x^54 + 30972*x^53 + 39583*x^52 + 36407*x^51 + 35564*x^50 + 44564*x^49 + 1505*x^48 + 47519*x^47 + 38695*x^46 + 43107*x^45 + 1676*x^44 + 42057*x^43 + 49879*x^42 + 29083*x^41 + 42241*x^40 + 8853*x^39 + 33546*x^38 + 48954*x^37 + 30352*x^36 + 62020*x^35 + 39864*x^34 + 9519*x^33 + 24828*x^32 + 34696*x^31 + 2387*x^30 + 27413*x^29 + 55829*x^28 + 40217*x^27 + 30205*x^26 + 42328*x^25 + 6210*x^24 + 52442*x^23 + 58495*x^22 + 2014*x^21 + 26452*x^20 + 33547*x^19 + 19840*x^18 + 5995*x^17 + 16850*x^16 + 37855*x^15 + 7221*x^14 + 32200*x^13 + 8121*x^12 + 23767*x^11 + 46563*x^10 + 51673*x^9 + 19372*x^8 + 4157*x^7 + 48421*x^6 + 41096*x^5 + 45735*x^4 + 53022*x^3 + 35475*x^2 + 47521*x + 27544
#分解N
q1, q2 = n.factor()
q1, q2 = q1[0], q2[0]
#求φ,注意求法,
phi = (p**q1.degree() - 1) * (p**q2.degree() - 1)
assert gcd(e, phi) == 1
d = inverse_mod(e, phi)
m = pow(c,d,n)
h = ''
for i in range(77):
h+=str(m[i])
h = int(h)
p = 106472061241112922861460644342336453303928202010237284715354717630502168520267
c = 20920247107738496784071050239422540936224577122721266141057957551603705972966457203177812404896852110975768315464852962210648535130235298413611598658659777108920014929632531307409885868941842921815735008981335582297975794108016151210394446009890312043259167806981442425505200141283138318269058818777636637375101005540308736021976559495266332357714
v1 = vector(ZZ, [1, h])
v2 = vector(ZZ, [0, p])
m = matrix([v1,v2]);
f, g1 = m.LLL()[0]
g1 = 228679177303871981036829786447405151037
n = 31398174203566229210665534094126601315683074641013205440476552584312112883638278390105806127975406224783128340041129316782549009811196493319665336016690985557862367551545487842904828051293613836275987595871004601968935866634955528775536847402581734910742403788941725304146192149165731194199024154454952157531068881114411265538547462017207361362857
for i in range(2^20):
q = g1 ^^ i
if n % q == 0:
p = n // q
phi = (p-1) * (q-1)
d = inverse(0x10001,phi)
print(long_to_bytes(int(pow(c,d,n))))
# b'DASCTF{P01yn0m141RS4_W17h_NTRU}'
LWE?(复现)
LWE? GGH?用Babai的算法好像通吃?(198×200的矩阵LLL要一点点的时间)
b = x ∗ A + b ∗ Y + z ∗ C + e b = x*A+b*Y+z*C+e b=x∗A+b∗Y+z∗C+e可以看成 b = s e c r e t ∗ D + e b = secret*D+e b=secret∗D+e,即将 x , y , z ; A , B , C x,y,z;A,B,C x,y,z;A,B,C拼起来,酱紫看起来就像GGH的形式了;但转化一下行和列又能有 b ′ = D ′ ∗ s e c r e t + e b' = D'*secret+e b′=D′∗secret+e,酱紫看来又好像是LWE了。道理我不懂,脚本我会用
反正Babai算法和Nguyen’s Attack算法都可解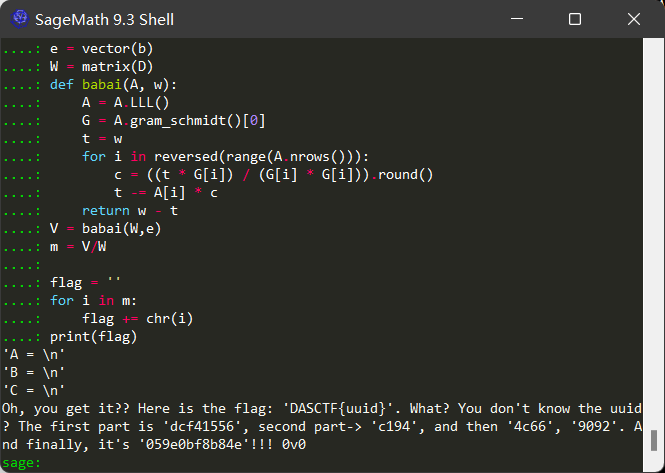
DASCTF{dcf41556-c194-4c66-9092-059e0bf8b84e}
# 跑个半小时?
from sage.modules.free_module_integer import IntegerLattice
m = 66
n = 200
p = 3
q = 2 ^ 20
f = open('out', 'r')
A = []
B = []
C = []
f.readline()
for j in range(m):
x = f.readline().replace(' ', ' ').replace(' ', ' ').replace(' ', ' ').replace('\n', '').replace(' ', ',')
if x[1] == ',':
x = x[0] + x[2:]
x = eval(x)
A.append(x)
f.readline()
for j in range(m):
x = f.readline().replace(' ', ' ').replace(' ', ' ').replace(' ', ' ').replace('\n', '').replace(' ', ',')
if x[1] == ',':
x = x[0] + x[2:]
x = eval(x)
B.append(x)
f.readline()
for j in range(m):
x = f.readline().replace(' ', ' ').replace(' ', ' ').replace(' ', ' ').replace('\n', '').replace(' ', ',')
if x[1] == ',':
x = x[0] + x[2:]
x = eval(x)
C.append(x)
f.close()
b = (
-19786291, -713104590, 79700973, 23261288, 203038164, 430352288, 147848301, 633183638, 188651439, 243206160, -654830271,
335642059, -100511588, 180023362, 130607831, 227597861, 188424473, 175518170, -246987997, 180879649, 421934976,
-227575274, -628937118, 5466646, -254939474, -438417079, 150434624, 327054986, 163561829, 816959939, -265298657,
82651050, 176899880, 174020455, -419656325, -101606182, 300413909, 237169571, -589213744, 121803611, -38080334,
-255712509, -133782964, 106220001, 195767251, -397096116, -583305587, -182462561, -271478737, -32014717, 114385188,
437506115, -1165732, 179349265, -77761751, -233976783, 410153356, 476453640, 91892631, -242168750, 506769243,
-384438362, 131852532, 586202810, 376719791, 578215353, 874304742, 163584566, 434260863, 98013671, 213627784, 59622886,
-84912852, 156744856, 169652328, 178143615, 400046730, 408163110, -357990863, -269552089, -199410809, 187503858,
-853206157, 134901027, 313984185, -162544217, -69722073, 43817388, -47389463, 210346729, -46516961, 72002967, 327714191,
45052266, 1010509210, 110937225, 448179404, 341448936, 446550865, 221914340, -804918424, -12007071, 151215468,
440279795, -73408566, -112121988, 40294376, 283179449, -193812410, -30061804, 20326854, 65412625, -260020045,
-570090340, 1546454, 548030557, 618148316, 290333796, 665474379, 301709165, -104726821, -503111899, 480689642,
-331192606, -518345784, -314602459, 25354403, 410995568, 179675848, -207010027, 400838662, 125916880, 501112567,
578261227, 24802586, 493171331, 383306766, -390093502, -389822626, -303615722, 20813851, -399678371, -566907567,
-432647113, -280465568, 1002042393, -510901339, 316603766, -139701243, 211217523, 108545545, -12948109, -569199543,
37065919, -150542603, 417851006, -470173530, -628557669, -128339015, -427978763, 381402990, 205835334, -30976552,
-357466556, -104985580, -115366372, 296031071, -8036087, 79340491, 650365147, 295521125, 885900267, 133049758,
217970062, 237420894, 358760095, -2684469, 475711698, 316770575, -25024622, -193442003, 200260606, 89183826, 567491985,
726371428, 222116554, 87397506, -29529094, 125968479, -50793004, 218035181, -210376687, 1025673749, -262390458,
467412984, -71097225, 259125517, -337232810, 143359550, 27115363)
D = matrix(ZZ, 66*3, 200)
for i in range(66):
for j in range(200):
D[i,j] = A[i][j]
for i in range(66):
for j in range(200):
D[i+66,j] = B[i][j]
for i in range(66):
for j in range(200):
D[i+66*2,j] = C[i][j]
e = vector(b)
W = matrix(D)
def babai(A, w):
A = A.LLL()
G = A.gram_schmidt()[0]
t = w
for i in reversed(range(A.nrows())):
c = ((t * G[i]) / (G[i] * G[i])).round()
t -= A[i] * c
return w - t
V = babai(W,e)
m = V/W
flag = ''
for i in m:
flag += chr(i)
print(flag)
不过用下面这种好像要快亿点(大概1分半)
小注意:
- solve_left()方法好像要一个方方正正的矩阵所以改成了198×198的矩阵
- 利用Nguyen’s Attack算法,不过这里的delta变成了1,加密代码中的errorV由 − 1 , 0 , 1 -1,0,1 −1,0,1组成,与GGH加密中的误差向量取3或-3相对比,delta自然变成了1。
- 原GGH加密中的误差向量取3或-3,这里取的-1,0,1,m解出来存在误差,四舍五入一下就好了
- 参考:GYCTF 2020 - GGH
# 数据导入省略
c = vector(ZZ, b)[:198]
# B = matrix(ZZ, D)
B = matrix(ZZ, 198, 198)
for i in range(198):
B[i] = D[i][:198]
n = 198
delta = 1
s = vector(ZZ, [delta]*n)
B6 = B.change_ring(Zmod(2*delta))
left = (c + s).change_ring(Zmod(2*delta))
m6 = (B6.solve_left(left)).change_ring(ZZ)
new_c = (c - m6*B) * 2 / (2*delta)
# embedded technique
new_B = (B*2).stack(new_c).augment(vector(ZZ, [0]*n + [1]))
new_B = new_B.change_ring(ZZ)
new_B_BKZ = new_B.BKZ()
shortest_vector = new_B_BKZ[0]
mbar = (B*2).solve_left(new_c - shortest_vector[:-1])
m = mbar * (2*delta) + m6
flag = ''
for i in m:
flag += chr(round(i))
print(flag)
貌似LWE>GGH,能解LWE的脚本也能解GGH?
边栏推荐
- flink中维表Join几种常见方式总结
- (2022牛客多校三)J-Journey(dijkstra)
- Demonstrate the use of foreign keys with Oracle
- Cadence(十一)丝印调整和后续事项
- sql语句批量更新 时间减去1天
- (2022 Hangdian multi school III) 1009.package delivery (greedy)
- Bash: create a function that returns a Boolean value
- Plato Farm有望通过Elephant Swap,进一步向外拓展生态
- Using loops to process data in tables in kettle
- C language programming | program compilation and preprocessing
猜你喜欢
SQLite common function integration

冰冰学习笔记:类与对象(中)

ClickHouse 笔记1 | 简介、特点 | 基于CentOS7系统的安装与使用 | 常用数据类型 | MergeTree 表引擎 | SQL操作

Okaleido ecological core equity Oka, all in fusion mining mode

(2022 Niuke multi school III) a-ancestor (LCA)

Docker install MySQL 8.0.28

什么是真正的 HTAP ?(二)挑战篇

Use reflection to dynamically modify annotation attributes of @excel

VLAN trunk experiment

Actual combat of flutter - Request encapsulation (I)
随机推荐
glGetUniformLocation,glUniform4f
The error of QT connecting SQLite database and its modification
帮忙发一份招聘,base全国,有兴趣的可以过来看看
Single arm routing (explanation + experiment)
Prior Attention Enhanced Convolutional Neural Network Based Automatic Segmentation of Organs at Risk
Quickly update the information in a field in kettle
Closed hash and open hash resolve hash conflicts
Okaleido ecological core equity Oka, all in fusion mining mode
How to get DDL information of an object
The DrawImage method calls the solution of not displaying pictures for the first time
Demonstrate the use of foreign keys with Oracle
2022-07-25 Gu Yujia's study notes
TCP/IP协议分析(TCP/IP三次握手&四次挥手+OSI&TCP/IP模型)
ARP broadcasting practice cases
flink去重(一)flink、flink-sql中常见的去重方案总结
Using loops to process data in tables in kettle
(2022牛客多校三)J-Journey(dijkstra)
冰冰学习笔记:类与对象(中)
Use Popen to execute a command and get the return result
单片机多级菜单