当前位置:网站首页>Processing of tree structure data
Processing of tree structure data
2022-07-03 01:49:00 【13 less】
When we do development , Sometimes let's deal with tree data . Today, let's talk about how to deal with tree data .
One . Two structures
(1) The back end returns a tree structure , This can be discussed with the backend .
(2) The back end returns a tiled structure , You need to convert through recursion .
Two . Passed element-ui Look at the tree structure .
Code :
<template>
<div class="">
<el-tree :data="data" :props="defaultProps" @node-click="handleNodeClick"></el-tree>
</div>
</template>
<script>
export default {
data() {
return {
data: [{
label: ' Class A 1',
children: [{
label: ' second level 1-1',
children: [{
label: ' Level three 1-1-1'
}]
}]
}, {
label: ' Class A 2',
children: [{
label: ' second level 2-1',
children: [{
label: ' Level three 2-1-1'
}]
}, {
label: ' second level 2-2',
children: [{
label: ' Level three 2-2-1'
}]
}]
}, {
label: ' Class A 3',
children: [{
label: ' second level 3-1',
children: [{
label: ' Level three 3-1-1'
}]
}, {
label: ' second level 3-2',
children: [{
label: ' Level three 3-2-1'
}]
}]
}],
defaultProps: {
children: 'children',
label: 'label'
}
};
},
methods: {
handleNodeClick(data) {
console.log(data);
}
}
};
</script>
<style scoped></style>
View :
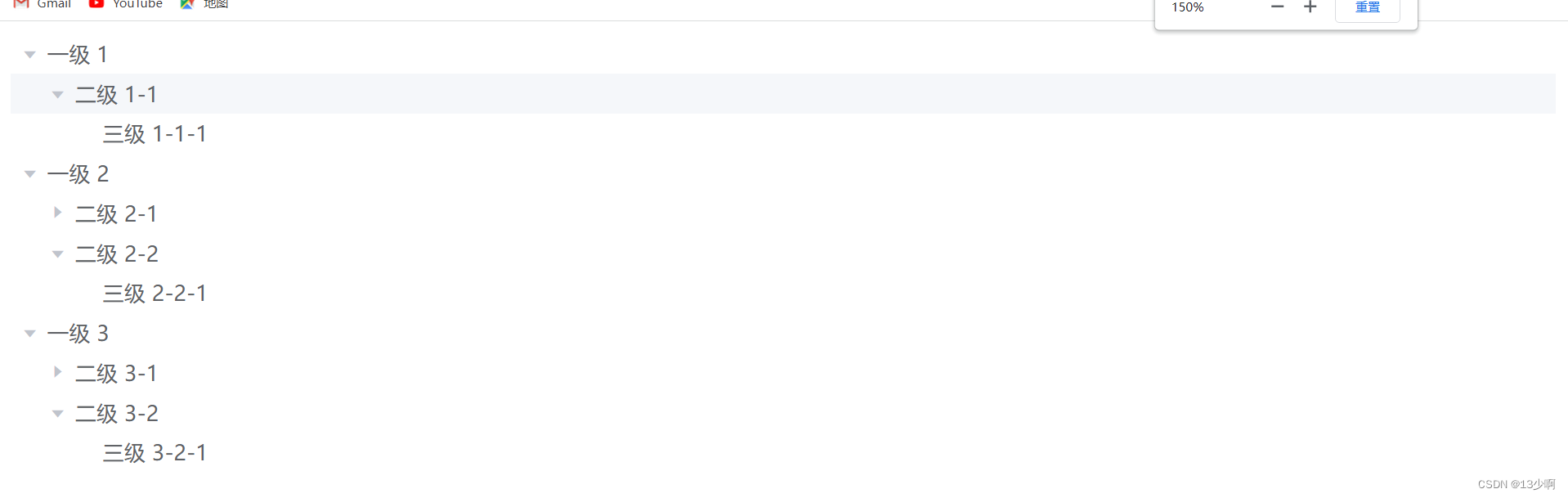
Analysis of the structure :
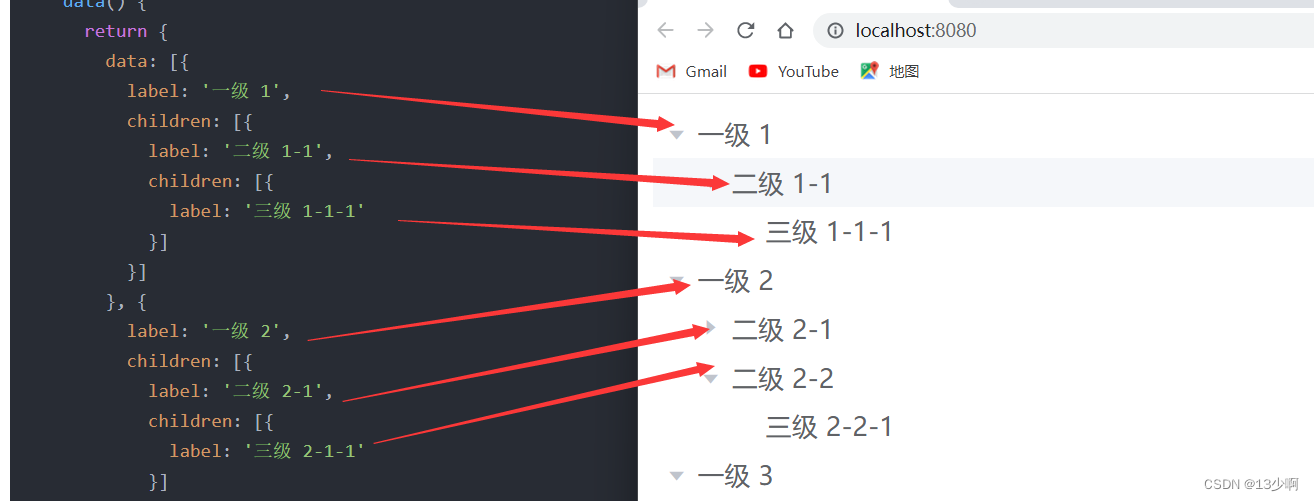
Analyze this structure :
Class A : Nothing there? , only one label ' Class A 1'
second level : stay children Keep writing inside label
Level three : Behind the second level children.
Level Four :......
3、 ... and . The actual development

When adding new interface documents , Transfer to the upper layer id, Can be added .
The same goes for deleting .
边栏推荐
- Network security - scan
- Network security - the simplest virus
- Huakaiyun (Zhiyin) | virtual host: what is a virtual host
- 【Camera专题】手把手撸一份驱动 到 点亮Camera
- Network security - virus
- Caused by: com. fasterxml. jackson. databind. exc.MismatchedInputException: Cannot construct instance o
- [机缘参悟-36]:鬼谷子-飞箝篇 - 面对捧杀与诱饵的防范之道
- Network security - talking about security threats
- 网络安全-扫描与密码爆破2
- What is tone. Diao's story
猜你喜欢
电信客户流失预测挑战赛
QTableWidget懒加载剩内存,不卡!

STM32 - switch of relay control lamp

【數據挖掘】任務6:DBSCAN聚類

Scheme and practice of cold and hot separation of massive data
Smart management of Green Cities: Digital twin underground integrated pipe gallery platform

Tâche 6: regroupement DBSCAN

【数据挖掘】任务6:DBSCAN聚类
![[data mining] task 5: k-means/dbscan clustering: double square](/img/e7/678197e703d1a28b765a0e3afd5580.png)
[data mining] task 5: k-means/dbscan clustering: double square
![[技术发展-23]:DSP在未来融合网络中的应用](/img/2e/f39543a18a8f58b1d341ce72cc4427.png)
[技术发展-23]:DSP在未来融合网络中的应用
随机推荐
Smart management of Green Cities: Digital twin underground integrated pipe gallery platform
串口抓包/截断工具的安装及使用详解
小程序開發的部分功能
【數據挖掘】任務6:DBSCAN聚類
STM32 - GPIO input / output mode
[技术发展-23]:DSP在未来融合网络中的应用
【数据挖掘】任务5:K-means/DBSCAN聚类:双层正方形
Mathematical knowledge: step Nim game game game theory
What is tone. Diao's story
Mathematical Knowledge: Steps - Nim Games - Game Theory
數學知識:臺階-Nim遊戲—博弈論
Types of map key and object key
Uniapp component -uni notice bar notice bar
High resolution network (Part 1): Principle Analysis
[fluent] hero animation (hero animation use process | create hero animation core components | create source page | create destination page | page Jump)
[data mining] task 1: distance calculation
Summary of interval knowledge
STM32 - introduction of external interrupts exti and NVIC
网络安全-扫描与密码爆破2
One of the C language practical projects is greedy snake