当前位置:网站首页>How to determine the authenticity of the website you visit -- certificate system
How to determine the authenticity of the website you visit -- certificate system
2022-07-26 07:50:00 【Earn money to wander】
In order to meet the security requirements of e-commerce and other behaviors in the Internet environment , There needs to be a way to identify . The certificate is to prove the identity of this website
If A Certificates are deployed on the server , Prove that I am Zhang San , and B The server is just a fake Zhang San , But there is no certificate of Zhang San , Then he is not really , Then if you want to communicate with Zhang San, you can only go A The server
Various systems cannot prevent being cheated , But when leaving the factory, various certificates are implanted into the operating system ,IOS、Windows wait
As soon as the operating system leaves the factory, there is a root certificate , The root certificate can be used to verify whether it is a real certificate
X.509 Certificate system
X.509 The certificate is based on the widely accepted international Telecommunication Union (ITU) X.509 Standard digital certificates , This standard defines the public key infrastructure (PKI) The format of the certificate . They are used to manage identity and security in Internet communications and Computer Networks .
Applied to cryptography , Public and private key pairs are used to encrypt and decrypt messages , Ensure the identity of the sender and the security of the message itself . be based on X.509 Of PKI The most common use case is transport layer security (TLS)/ Secure socket layer (SSL), It is HTTPS The basis of the agreement , Safe Web Browse . but X.509 The protocol also applies to application security 、 Digital signatures and code signatures for other key Internet protocols .
On the whole ,X.509 Common applications of certificates include :
- SSL/HTTP and HTTPS For authenticated and encrypted web browsing
- adopt S/MIME Protocol signature and encrypted email
- code signing
- File deployment
- Client side authentication
- E-ID card issued by the government
Every X.509 Certificates contain a public key 、 Digital signature and the identity related to the certificate and its issuing certification authority (CA) Information about
The public key is contained in the certificate , The public key also includes part of the key pair of the private key
A public key or private key pair allows the owner of the private key to digitally sign the document ; Anyone with the corresponding public key can verify these signatures ; Allow third parties to send messages encrypted with public keys , Only the owner of the private key can decrypt
A digital signature is an encoded hash of a document encrypted with a private key ( Fixed length summary ). When X.509 Certificates are publicly trusted CA( for example SSL.com) When signing , Third parties can use this certificate to verify the identity of the entity that provided it .
Not all X.509 Certificate applications require public trust . for example , Companies can issue their own private trusted certificates for internal use .
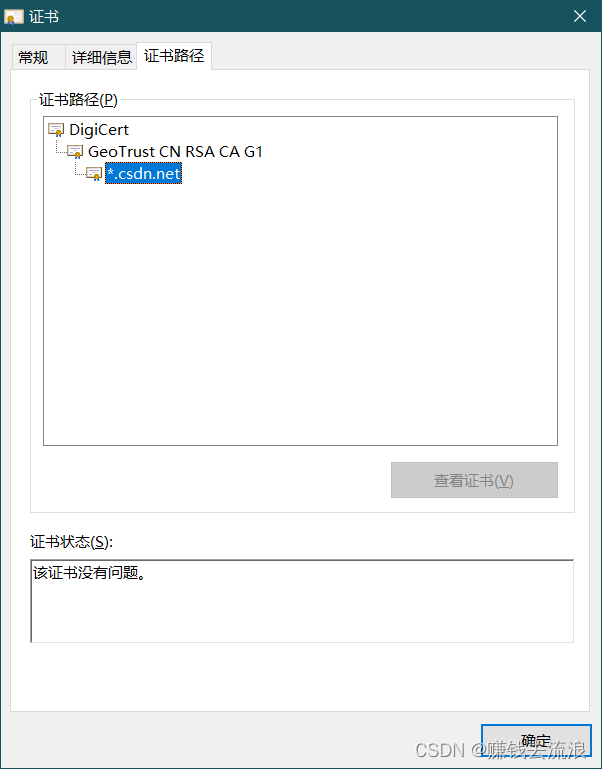
Certificate chain / Trust chain
X.509 Certificates are usually combined into chains for verification
*.csdn.net The certificate is issued by GeoTrust CN RSA CA G10 The intermediate certificate is signed , Up again , from DigiCert Root certificate signature
How to work
X.509 The standard is based on a notation called abstract syntax (ASN.1) Interface description language , It defines data structures that can be serialized and deserialized across platforms . utilize ASN,X.509 The certificate format uses the relevant public and private key pairs to encrypt and decrypt messages .
The key size or bit length of the public key determines the strength of protection . for example ,2048 position RSA The key is usually used for SSL certificate 、 Digital signatures and other digital certificates .
边栏推荐
- Tensorflow learning diary tflearn
- Wrong Addition
- WCF deployed on IIS
- Establishment and use of openstack cloud platform
- LeetCode剑指offer专项(一)整数
- Audio and video learning (10) -- PS streaming
- Use of views
- NLP natural language processing - Introduction to machine learning and natural language processing (3)
- 【uniapp】多种支付方式封装
- PostgreSQL UUID fuzzy search UUID string type conversion SQL error [42883] explicit type casts
猜你喜欢

JWT快速入门

分布式相关面试题总结
JMeter performance test saves the results of each interface request to a file

JMeter性能测试之使用CSV文件参数化

shardingjdbc踩坑记录

What is bloom filter in redis series?

dcn(deep cross network)三部曲

Crawler - > tpimgspider

Practice of online question feedback module (XIV): realize online question answering function

在线问题反馈模块实战(十四):实现在线答疑功能
随机推荐
动态性能视图概述
Network trimming: a data driven neuron pruning approach towards efficient deep architectures paper translation / Notes
Comparison and difference between dependence and Association
【推荐系统经典论文(十)】阿里SDM模型
Lnmp+wordpress to quickly build a personal website
Unity Metaverse(二)、Mixamo & Animator 混合树与动画融合
Quantitative perception training in tensorflow2.x and x86 end evaluation of tflite
How to close the high-level port
Introduction to C language (8)
WCF introductory tutorial II
1. MySQL Architecture [MySQL advanced]
Vscode cannot start the problem solving idea
Selenium: detailed explanation of browser crawler use (I)
Matlab-二/三维图上绘制黑点
API (common class 2)
Master slave database deployment
:app:checkDebugAarMetadata 2 issues were found when checking AAR metadata: 2 issues were found when
程序环境和预处理
Hcip--- BGP comprehensive experiment
Fang Wenshan, Jay Chou's best partner, will officially announce "Hualiu yuancosmos" on July 25