当前位置:网站首页>Sentinel source code analysis part I sentinel overview
Sentinel source code analysis part I sentinel overview
2022-07-03 19:12:00 【Age people】
List of articles
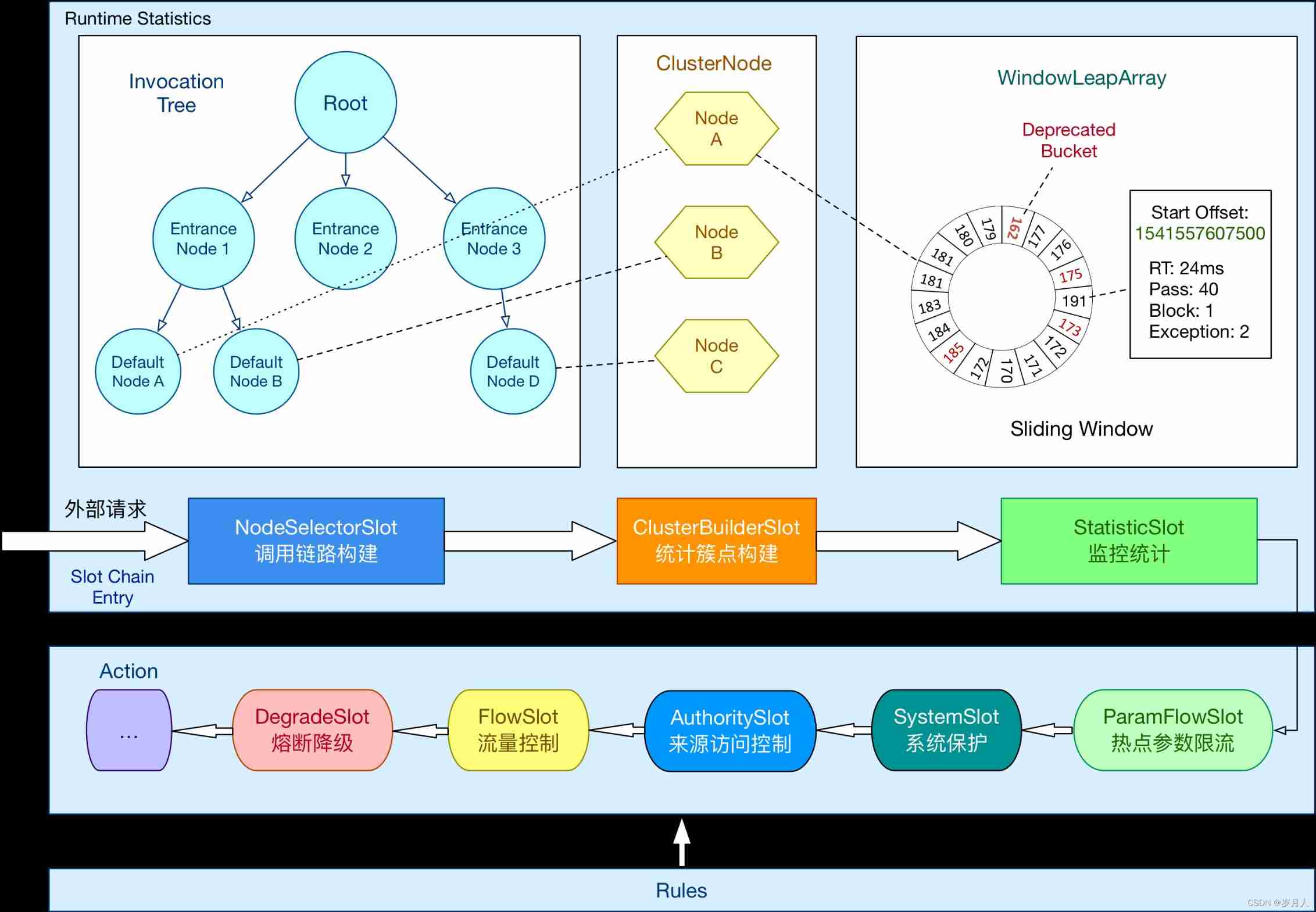
Architecture diagram
The whole source code part is based on the use of the production environment
- 1.1 Sentinel Contains console : Configure current limiting rules [ System rules , Authority, etc ]
- 1.2 The console pushes rules to the data source (zookeeper etc. ) to ground
- 1.3 User process installation sentinel Module monitor zk To configure
- 2.1 Request to enter and hand it over to sentinel-adapter Intercept each module
- 2.2 According to Adapter Analytic contextName structure context
- 2.3 according to contextName structure EntranceNode
- 2.4 Find resources ResourceWrapper Corresponding ProcessorSlotChain
- 2.5 ProcessorSlotChain Handle [ Statistics , Current limiting , Rule verification, etc ]

| Object name | explain |
|---|---|
| EntranceNode | Entry node |
| StatisticNode | Statistics node , It contains two sliding window structures of second level and minute level |
| DefaultNode | Link nodes , It is used to count the data of a resource on the call link , Maintain the tree structure |
| ClusterNode | Cluster link information |
| Entry | every time Adapter Module resource calls will create a Entry, Trestle Structure [ Enter the first ]Entry1->Entry2->Entry3[ Exit first ], Contains the resource name 、curNode( Current statistics node ) When the call of information resources ends, you need entry.exit Restore call stack |
| Context | Call link context , Maintaining the entry node ,Entry link ,curNode |
One context Maintenance request link Entry, Every entry Both contain node, Maintain the tree relationship between resources and the storage of flow limiting information
Schematic diagram of current limiting
- The whole working mechanism of current limiting is handled through the responsibility chain
- Each resource corresponds to a ProcessorSlotChain
- This work chain passes Spi Mechanism discovery , Users can customize the corresponding implementation , And pass @SpiOrder Orchestration priority

context And entry Relationship
- context Represents the current thread context
- Unlike cross process tracing , Here we do not consider cross thread and cross process processing
- Multiple resource calls in the same thread , Will form the entry chain ,context Hold the relevant chain
- context Is the thread dimension . but context The name of is resource ResourceWrapper dimension
context And node Relationship
- According to the resource name, it will build EntranceNode
- context Will hold EntranceNode
node Self relationship tree maintenance
- Call resource throttling multiple times in a thread , be node Form a tree structure
- entry Form a linked list stack [ First in, then out ] structure
See the relationship between the three from the dimension of request and resource
- x Axis indicates request , The thread of each request builds a context, but context Could be the same , Generally, it is the resource name
- Each creation context Will get or build from the cache entranceNode, The same resource name corresponds to the same Node
- node It will build a tree structure , Indicates current statistics node Tree structure current limiting information
That's why ProcessorSlotChain Instantiate by resource dimension , Instead of singleton mode
Because of the statistics Slot Statistics are based on resource dimensions , If singleton is used, the current limit statistics of all resources are in the same node

- Above picture Node The same color means the same object
Expansion point - Official schematic diagram
Expand a little bit node Class diagram

边栏推荐
- High concurrency architecture cache
- Flask generates swagger documents
- Pan for in-depth understanding of the attention mechanism in CV
- Processing of user input parameters in shell script
- 22.2.14 -- station B login with code -for circular list form - 'no attribute' - 'needs to be in path selenium screenshot deviation -crop clipping error -bytesio(), etc
- Scrapy爬虫框架
- [proteus simulation] a simple encrypted electronic password lock designed with 24C04 and 1602LCD
- shell 脚本中关于用户输入参数的处理
- Today I am filled with emotion
- Free hand account sharing in September - [cream Nebula]
猜你喜欢
Flutter网络和数据存储框架搭建 -b1
SQL custom collation
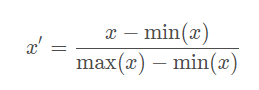
为什么要做特征的归一化/标准化?
Record the errors reported when running fluent in the simulator
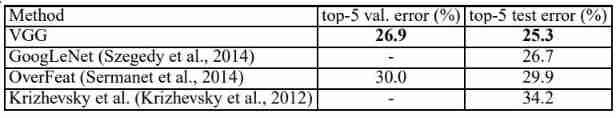
Thesis study - 7 Very Deep Convolutional Networks for Large-Scale Image Recognition (3/3)

Free sharing | linefriends hand account inner page | horizontal grid | not for sale
01. Preparation for automated office (free guidance, only three steps)
![Free hand account sharing in September - [cream Nebula]](/img/4f/fec31778a56886585e35be87885452.jpg)
Free hand account sharing in September - [cream Nebula]
Know what it is, and know why, JS object creation and inheritance [summary and sorting]

Add control at the top of compose lazycolumn
随机推荐
[new year job hopping season] test the technical summary of interviewers' favorite questions (with video tutorials and interview questions)
达梦数据库的物理备份和还原简解
leetcode:11. Container with the most water [double pointer + greed + remove the shortest board]
OSPF - detailed explanation of stub area and full stub area
Pytorch introduction to deep learning practice notes 13- advanced chapter of cyclic neural network - Classification
【学术相关】顶级论文创新点怎么找?中国高校首次获CVPR最佳学生论文奖有感...
Recommend a simple browser tab
How to design a high concurrency system
Zhengda futures news: soaring oil prices may continue to push up global inflation
Why should we do feature normalization / standardization?
[leetcode周赛]第300场——6110. 网格图中递增路径的数目-较难
Valentine's Day - make an exclusive digital collection for your lover
[water quality prediction] water quality prediction based on MATLAB Fuzzy Neural Network [including Matlab source code 1923]
Sqlalchemy - subquery in a where clause - Sqlalchemy - subquery in a where clause
【LeetCode】【SQL】刷题笔记
Latex image rotates with title
变化是永恒的主题
Web Security (VII) specific process of authentication with session cookie scheme
【光学】基于matlab介电常数计算【含Matlab源码 1926期】
[leetcode] [SQL] notes
![Know what it is, and know why, JS object creation and inheritance [summary and sorting]](/img/90/eba7ac9d03d5b1c8dec3343810e30a)