当前位置:网站首页>Xiaodi notes
Xiaodi notes
2022-07-03 02:35:00 【H0ne】
kitchen knife , Ant sword , Advantages and disadvantages of ice scorpion
kitchen knife : Status not updated , No plug-ins , Single encrypted transmission
Ant sword : Update status , There are plug-ins , Strong expansion , Single encrypted transmission
Ice scorpion : Update status , Unknown plugin , Two way encrypted transmission . Strong expansion , Applicable post penetration .
Idea of vulnerability mining
Fixed point mining keywords :
Controllable variable
Variables accept get post Accept keywords $_GET
Specific functions
Output print
Database operation
Specific keywords :
select,insert,update,sql Execute statement ==sql Inject holes
Search for specific keywords and try to find specific vulnerabilities
Such as : Search for echo,print What you're trying to dig is XSS Loophole
Such as : Search for $_GET $_POST, What I'm trying to dig is security vulnerabilities
Fixed point mining function point :
Such as : I want to mine files to upload , There is an operation address for uploading files in the member center , Packet capture analysis finds specific file code segments in the source code , File upload code analysis and mining ,
expand : Depending on the vulnerability
sql Inject , Database monitoring - Monitor the interaction between the current page and the database (sql Execute statement )
Breakpoint debugging : Visit the corresponding code of the page for breakpoint debugging ( The sequence of the execution process , Call file list, etc ).
Registered users :insert xiaodi union select’
Filter :xiaodi union select’
Access to database :xiaodi union select’
Modify the user :update xiaodi union select’ Conditions = Who is the user name ,xiaodi’ union select update Inject
The principle of secondary injection : Bypass escape injection , Magic quotes 、
Upload files :
# Keyword search :( function , Key word , Global variables, etc )
Upload files $_files move_uploaded_file etc.
# Application function capture :( Any application function point that may have upload )
Front desk member center , There may be upload places such as background news addition
Knowledge point
Elevated privileges :
webshell(
backstage : The function point ( Upload files , Template modification ,SQL perform , The data backup ) Thinking point ( Known procedures , Unknown program )
Loophole : Single point vulnerability ( Upload files , File contains ,RCE perform ,SQL Inject ...) Combined vulnerabilities ( Cooperation in all aspects )
The third party ( compiler , Middleware platform ,PHPadmin
Other permissions ( database (mysql,mssql,oracle...)
( The server FTP RDP SSH…)
Third party interface ( mail , payment , Space quotient …)
Server system
windows( For environment :web Local )
( The way to claim rights : database , Overflow vulnerability , Token stealing , Third party software ,AT&SC&PS, Unsafe service permissions , Service path without quotes ,Unattended installs,AlwayssiinstallElevated)
( For version :windows XP,windows 7/8/10,windows2ks/o8,windows2012/16
Intranet 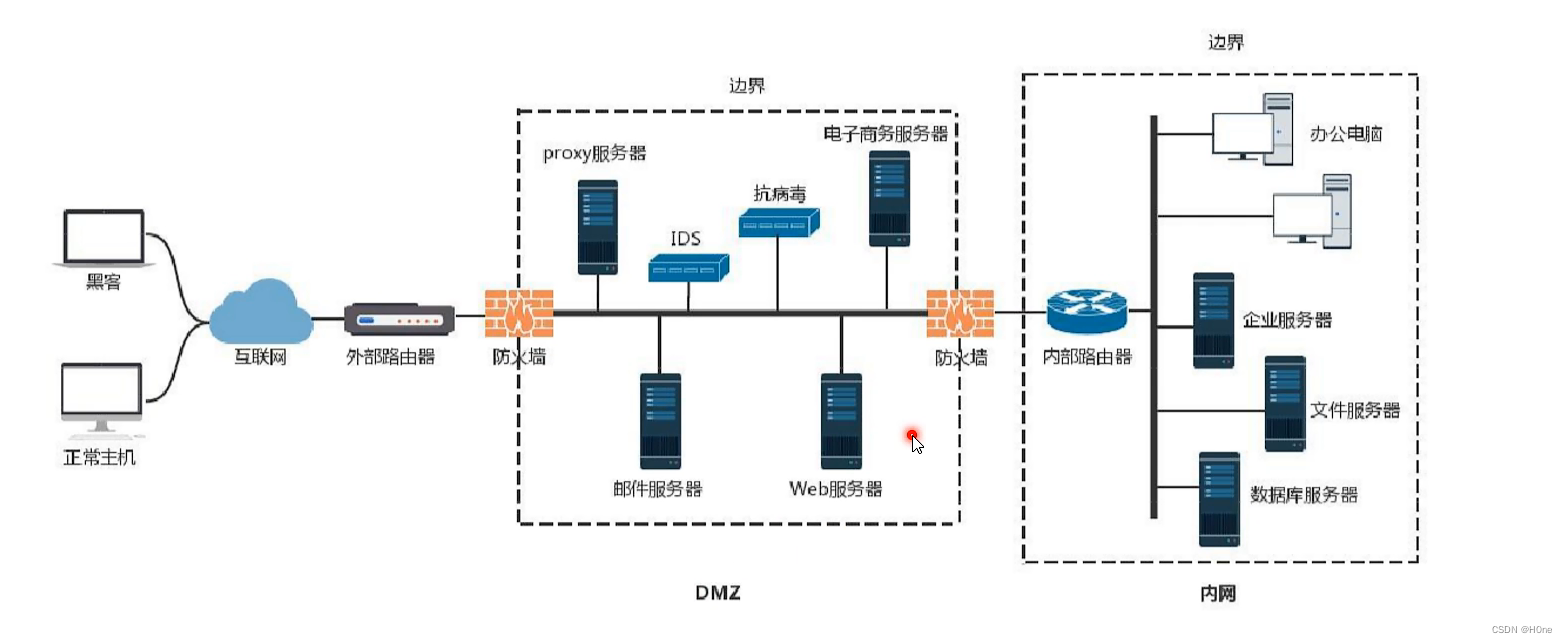
Working group : Family, for example , dormitory Small LAN
Domain environment : There will be a computer to control , School computer room . Belongs to the upgraded version of the working group
Working group :ARP cheating ,DNS end
Domain environment :
DC domain controller : The highest permission of the domain ,
ipconfig /all Determine the domain of existence -dns
net view /admin Determine the domain of existence
net time /domain Determine the primary domain
Emergency response :
Protection phase , analysis phase , Recurrence stage , Repair phase , Proposal stage ,
Purpose : Analyze the attack time , Attack operations , The consequences of the attack , Safe repair, etc. and give reasonable solutions ,
Essential knowledge :
Be familiar with the common web Security attack technology
Be familiar with log activation, storage, viewing, etc
Be familiar with the classification and analysis of data recorded in logs
边栏推荐
- GBase 8c触发器(二)
- awk从入门到入土(0)awk概述
- GBase 8c系统表-pg_class
- Error when installing MySQL in Linux: starting mysql The server quit without updating PID file ([FAILED]al/mysql/data/l.pid
- 【教程】chrome關閉跨域策略cors、samesite,跨域帶上cookie
- Choose it when you decide
- Kotlin middle process understanding and Practice (II)
- easyExcel
- Principle and application of database
- Basic operation of binary tree (C language version)
猜你喜欢

线程安全的单例模式

Return a tree structure data
![[shutter] bottom navigation bar page frame (bottomnavigationbar bottom navigation bar | pageview sliding page | bottom navigation and sliding page associated operation)](/img/6e/67bc187a89fb9125856c78c89f7bfb.gif)
[shutter] bottom navigation bar page frame (bottomnavigationbar bottom navigation bar | pageview sliding page | bottom navigation and sliding page associated operation)
![[translation] the background project has joined the CNCF incubator](/img/0b/e3d2674b1a1cba3ea398cbcb1a018a.png)
[translation] the background project has joined the CNCF incubator

Thread safe singleton mode
Baidu map - surrounding search
Summary of interview project technology stack

Awk from introduction to earth (0) overview of awk
SPI机制
错误Invalid bound statement (not found): com.ruoyi.stock.mapper.StockDetailMapper.xxxx解决
随机推荐
QT qcombobox add qccheckbox (drop-down list box insert check box, including source code + comments)
require. context
GBase 8c系统表-pg_authid
Build a private cloud disk cloudrev
GBase 8c系统表pg_cast
Gbase 8C system table PG_ constraint
[Flutter] dart: class;abstract class;factory;类、抽象类、工厂构造函数
[tutorial] chrome turns off cross domain policies CORS and samesite, and brings cookies across domains
Gbase 8C system table PG_ authid
面试八股文整理版
GBase 8c系统表-pg_amproc
GBase 8c 函数/存储过程参数(二)
sql server 查询指定表的表结构
GBase 8c系统表-pg_attribute
Unrecognized SSL message, plaintext connection?
Gbase 8C trigger (I)
返回一个树形结构数据
leetcode540
awk从入门到入土(0)awk概述
Coroutinecontext in kotlin