当前位置:网站首页>Detailed analysis of micro service component sentinel (hystrix)
Detailed analysis of micro service component sentinel (hystrix)
2022-07-03 02:11:00 【kjshuan】
1 Microservice component Sentinel (Hystrix)
1、 Problems encountered in Distributed Systems


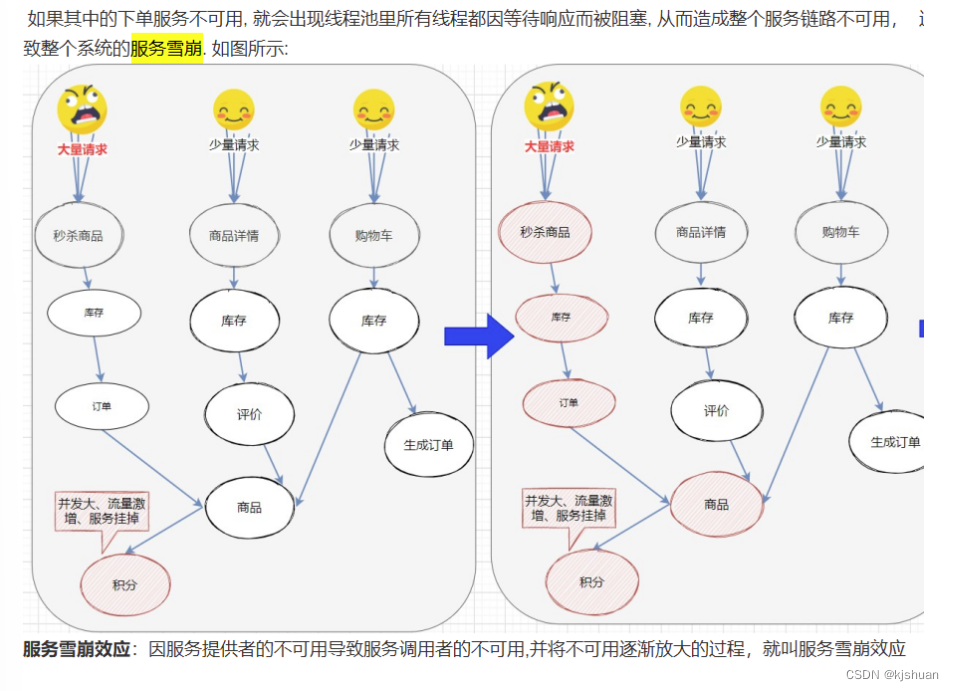

What is a cache avalanche 、 breakdown 、 through ?
How to solve them
redis Cache avalanche Refers to the time from the large amount of data in the cache to the expiration time , And the amount of query data is huge , All requests access the database directly , Causes database pressure to be too big even down machine . Caused by the simultaneous expiration of a large amount of data , For this reason , It can be solved by setting the expiration time evenly , That is, let the expiration time be relatively discrete . If a larger fixed value is used + A smaller random value ,5 Hours +0 To 1800 Second sauce purple . Redis Failure and downtime may also lead to cache failure . This requires construction Redis High availability cluster . Cache penetration : It means to query a certain nonexistent data , Because the cache is not hit when it needs to be queried from the database , If no data is found, it will not be written to the cache , This will cause this nonexistent data to be queried in the database every time it is requested , And bring pressure to the database . If it's an illegal request , We are API entrance , Check the parameters , Filter illegal values . If the query database is empty , We can set a null value for the cache , Or default . But if there's a request to come in , Need to update cache , To ensure cache consistency , meanwhile , Finally, set an appropriate expiration time for the cache .( It's commonly used in business , Simple and effective ) Use bloom filter to quickly determine whether the data exists . When a query request comes , First, judge whether the value exists through the bloom filter , Only when it exists can we continue to look into it . Principle of bloon filter : It has an initial value of 0 Bitmap array and N It's a hash function . One to one key Conduct N individual hash Algorithm acquisition N It's worth , Put this in the bit array N After hashing, set to 1, Then, when checking, if the specific positions are 1, So the bloom filter decides what to do key There is . Cache breakdown It means hot spots key When it expires at a certain point in time , And just at this point in time Key There are a lot of concurrent requests coming , So a lot of requests come to db. It looks a bit like , In fact, the difference between them is , Caching refers to excessive database pressure or even down machine , Cache breakdown is just a large number of concurrent requests to DB Database level . It can be said that breakdown is a subset of the cache . Some articles think that the two are different , The difference is that the breakdown is targeted at a hot spot key cache , There are a lot of them key. 1. Use the mutex scheme . When the cache fails , Not immediately to load db data , Instead, first use some atomic operation commands with a successful return , Such as (Redis Of setnx) To operate , When it's successful , Reload db Database data and set cache . Otherwise, try to get the cache again . 2. “ Never expire ”, No expiration time is set , But when hot data is about to expire , Asynchronous thread to update and set expiration time .

Solution Common fault tolerance mechanisms :
Timeout mechanism
Without any treatment , The unavailability of the service provider will cause the consumer request thread to force a wait , And cause system resource depletion . Add a timeout mechanism , Once timeout , Just release the resources . Due to the faster release of resources , To some extent, it can restrain the problem of resource depletion .
Service restriction

Isolation
principle : The user's request will no longer directly access the service , Instead, the service is accessed through idle threads in the thread pool , If the thread pool is full , Will be downgraded Handle , The user's request will not be blocked , You can see at least one execution result ( For example, return friendly prompts ), Instead of endless waiting or watching To the system crash .
Signal isolation : Signal isolation can also be used to limit concurrent access , To prevent obstruction from spreading , The biggest difference from thread isolation is that the thread executing dependent code is still the request thread ( The thread needs to apply through signals , If the client is trusted and can return quickly , You can use signal isolation instead of thread isolation , Reduce overhead . The size of semaphore can be adjusted dynamically , Thread pool size cannot .
Service failure
Temporarily shut down when the remote service is unstable or the network jitters , Just call service . Everyone must know the circuit breaker in the real world , The circuit breaker monitors the condition of the circuit in real time , If the circuit current is found to be abnormal , Will trip , So as to prevent the circuit Burned down . The circuit breaker in the software world can be understood this way : Real time monitoring application , If it is found that the number of failures within a certain period of time / The failure rate reaches a certain threshold , Just “ trip ”, Open circuit Device open —— here , Request direct return , Instead of calling the original logic . After tripping for a period of time ( for example 10 second ), The circuit breaker will enter the semi open state state , This is a transient state , At this point, a request is allowed to call the logic of the call , If it works , The circuit breaker is closed , Application normal call ; If the call is still not success , The circuit breaker continues to return to the open state , Try to enter the half open state again after a period of time —— adopt ” trip “, Apps can protect themselves , And avoid wasting money Source ; And through the half open design , Applicable “ Self repair “. therefore , Same thing , When there is a large amount of overtime for dependent services , There's no point in having new requests to visit , Will only fearlessly consume existing resources . such as We set the timeout to 1s, If there are a large number of requests in a short period of time 1s No response from inside , It means that the service is abnormal , There is no need to Let other requests access this dependency , At this time, circuit breakers should be used to avoid waste of resources .

service degradation
Service fuse , There must be service degradation . So called demotion , It's when a service melts , The service will no longer be called , At this point the client can prepare a local one itself fallback( Back off ) Callback , Returns a default value . for example :( Spare interface / cache /mock data ) . To do so , Although the level of service has declined , But somehow it can be used , Better than just hanging up , Of course, it also depends on the appropriate business scenario .
2 Alibaba sentinel
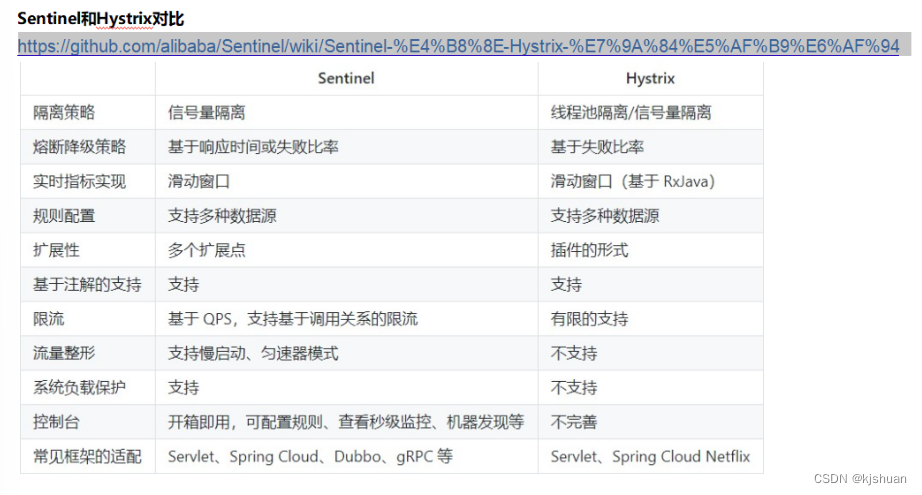
Sentinel** Quick start **
The first step is to import pom rely on
<dependency> <groupId>com.alibaba.csp</groupId> <artifactId>sentinel-core</artifactId> <version>1.8.1</version> </dependency>
The second step is configuration yml
server: port: 12004 spring: application: name: nacossentinel
Step 3 configuration controller
@RestController
@RequestMapping("/sent-serv")
public class InitCtrl {
private static final String RESOURCE_NAME_FIND="find";
@RequestMapping("/find")
public String find(){
try {
// Set a resource here ( Traffic ) Managed listeners ( Whatever the name is )
// People words : Just add a monitor
Entry entry = SphU.entry(RESOURCE_NAME_FIND);
return "hello , world";
} catch (BlockException e) {
return " I'm restricted ....";
}catch (Exception e){
return " My service is going to be degraded ....";
}
}
// When the controller object is created First create the trigger rule of the resource management listener
// People words : Trigger the monitor
@PostConstruct
private static void init(){
ArrayList<FlowRule> rules = new ArrayList<>();
FlowRule rule = new FlowRule();
// Fill in the managed resources
rule.setResource(RESOURCE_NAME_FIND);
// Set traffic rules
rule.setGrade(RuleConstant.FLOW_GRADE_QPS);
// Limit the number of accesses per second
rule.setCount(1);
rules.add(rule);
// Store the rule set in the rule manager
FlowRuleManager.loadRules(rules);
}
}Step 4 start test
http://localhost:12004/sent-serv/find
bean Life cycle of
Instantiation initialization service The destruction
Import pom
spring-core spring-context spring-beans
Write a service class
public class MyService{
priavate String name;
}
To configure spring.xml
<beans>
<bean id="ms" class="com.kgc.MyService" init-method="init"></bean>
</beans>sentinel Achieve two ( Configuration aspect Unusually low intrusive )
The first step is to import pom rely on
<dependency> <groupId>com.alibaba.csp</groupId> <artifactId>sentinel-annotation-aspectj</artifactId> <version>1.8.1</version> </dependency>
The second step is configuration config class Configure aspect support
@Configuration
public class SentinelConfiguration {
@Bean
public SentinelResourceAspect sentinelResourceAspect(){
return new SentinelResourceAspect();
}
}Step 3 configuration controller
@RestController
@RequestMapping("/sent-serv")
public class InitCtrl {
private static final String RESOURCE_NAME_FIND="find";
// @RequestMapping("/find")
// public String find(){
//
// try {
// // Set a resource here ( Traffic ) Managed listeners ( Whatever the name is )
// // People words : Just add a monitor
// Entry entry = SphU.entry(RESOURCE_NAME_FIND);
// return "hello , world";
// } catch (BlockException e) {
// return " I'm restricted ....";
// }catch (Exception e){
// return " My service is going to be degraded ....";
// }
// }
@RequestMapping("/find")
@SentinelResource(value = "find",blockHandler = "bkHandler")
public String find(){
return "Hello World!";
}
// Exception handling method
public String bkHandler(BlockException e){
return " I'm restricted again o(╥﹏╥)o";
}
// When the controller object is created First create the trigger rule of the resource management listener
// People words : Trigger the monitor
@PostConstruct
private static void init(){
ArrayList<FlowRule> rules = new ArrayList<>();
FlowRule rule = new FlowRule();
// Fill in the managed resources
rule.setResource(RESOURCE_NAME_FIND);
// Set traffic rules
rule.setGrade(RuleConstant.FLOW_GRADE_QPS);
// Limit the number of accesses per second
rule.setCount(2);
rules.add(rule);
// Store the rule set in the rule manager
FlowRuleManager.loadRules(rules);
}
}Step 4 test
project
边栏推荐
- Iptables layer 4 forwarding
- Everything file search tool
- easyExcel
- Internal connection query and external connection
- 微服务组件Sentinel (Hystrix)详细分析
- Missing library while loading shared libraries: libisl so. 15: cannot open shared object file: No such file
- 【Camera专题】手把手撸一份驱动 到 点亮Camera
- What are the key points often asked in the redis interview
- Where is the future of test engineers? Confused to see
- [Yu Yue education] reference materials of love psychology of China University of mining and technology
猜你喜欢

Distributed transaction solution
Certaines fonctionnalités du développement d'applets

MySQL学习03

stm32F407-------DMA
![[leetcode] 797 and 1189 (basis of graph theory)](/img/2a/9c0a904151a17c2d23dea9ad04dbfe.jpg)
[leetcode] 797 and 1189 (basis of graph theory)

How to deal with cache hot key in redis

RestCloud ETL 跨库数据聚合运算
使用Go语言实现try{}catch{}finally

ByteDance data Lake integration practice based on Hudi
Detailed introduction to the deployment and usage of the Nacos registry
随机推荐
通达OA 首页门户工作台
Redis:Redis的简单使用
小程序開發的部分功能
A 30-year-old software tester, who has been unemployed for 4 months, is confused and doesn't know what to do?
Caused by: com. fasterxml. jackson. databind. exc.MismatchedInputException: Cannot construct instance o
Where is the future of test engineers? Confused to see
[leetcode] 797 and 1189 (basis of graph theory)
【Camera专题】Camera dtsi 完全解析
Use go language to realize try{}catch{}finally
Bottleneck period must see: how can testers who have worked for 3-5 years avoid detours and break through smoothly
2022 spring "golden three silver four" job hopping prerequisites: Software Test interview questions (with answers)
stm32F407-------ADC
MySQL学习03
[shutter] top navigation bar implementation (scaffold | defaulttabcontroller | tabbar | tab | tabbarview)
CFdiv2-Fixed Point Guessing-(区间答案二分)
Coroutinecontext in kotlin
Network security - scan
Network security - phishing
机器学习笔记(持续更新中。。。)
[shutter] shutter debugging (debugging control related functions | breakpoint management | code operation control)