当前位置:网站首页>Leetcode 183 Customers who never order (2022.07.02)
Leetcode 183 Customers who never order (2022.07.02)
2022-07-03 02:01:00 【ChaoYue_ miku】
Create table If Not Exists Customers (id int, name varchar(255))
Create table If Not Exists Orders (id int, customerId int)
Truncate table Customers
insert into Customers (id, name) values ('1', 'Joe')
insert into Customers (id, name) values ('2', 'Henry')
insert into Customers (id, name) values ('3', 'Sam')
insert into Customers (id, name) values ('4', 'Max')
Truncate table Orders
insert into Orders (id, customerId) values ('1', '3')
insert into Orders (id, customerId) values ('2', '1')
A website contains two tables ,Customers Table and Orders surface . Write a SQL Inquire about , Find all customers who never order anything .
Customers surface :
±—±------+
| Id | Name |
±—±------+
| 1 | Joe |
| 2 | Henry |
| 3 | Sam |
| 4 | Max |
±—±------+
Orders surface :
±—±-----------+
| Id | CustomerId |
±—±-----------+
| 1 | 3 |
| 2 | 1 |
±—±-----------+
For example, given the above table , Your query should return :
±----------+
| Customers |
±----------+
| Henry |
| Max |
±----------+
source : Power button (LeetCode)
link :https://leetcode.cn/problems/customers-who-never-order
Method 1 :NOT IN Words and expressions
MySQL Submission :
select customers.name as 'Customers'
from customers
where customers.id not in
(
select customerid from orders
);
边栏推荐
- Certaines fonctionnalités du développement d'applets
- How can retail enterprises open the second growth curve under the full link digital transformation
- 网络安全-扫描与密码爆破2
- Network security - phishing
- Analysis, use and extension of open source API gateway apisex
- Basic operation of view
- Function definition and call, this, strict mode, higher-order function, closure, recursion
- 网络安全-NAT网络地址转换
- [shutter] shutter debugging (debugging fallback function | debug method of viewing variables in debugging | console information)
- [camera topic] how to save OTP data in user-defined nodes
猜你喜欢
Smart management of Green Cities: Digital twin underground integrated pipe gallery platform
小程序开发的部分功能

可视化yolov5格式数据集(labelme json文件)
网络安全-漏洞与木马
Bottleneck period must see: how can testers who have worked for 3-5 years avoid detours and break through smoothly

Deep learning notes (constantly updating...)
![[data mining] task 2: mimic-iii data processing of medical database](/img/ad/4e7b253d60b29351e3ef252ee5230f.png)
[data mining] task 2: mimic-iii data processing of medical database
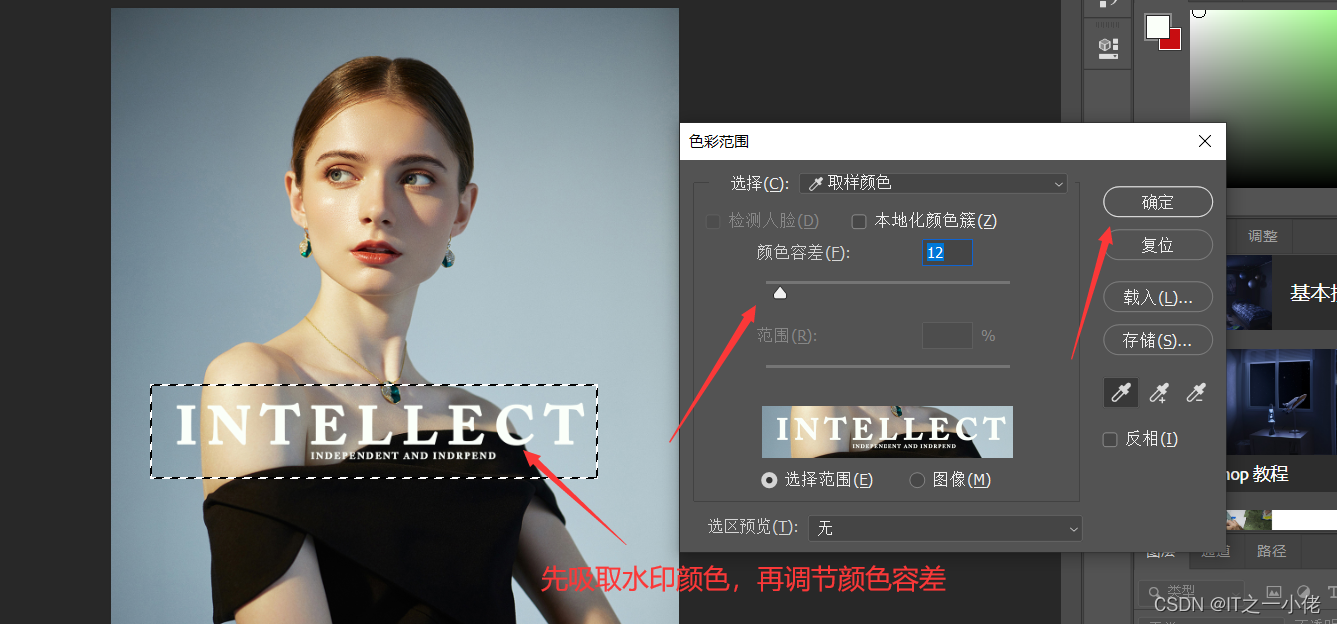
PS remove watermark details

Depth (penetration) selector:: v-deep/deep/ and > > >

Machine learning notes (constantly updating...)
随机推荐
Leetcode(540)——有序数组中的单一元素
[data mining] task 1: distance calculation
苏世民:25条工作和生活原则
Custom components, using NPM packages, global data sharing, subcontracting
502 (bad gateway) causes and Solutions
深度(穿透)选择器 ::v-deep/deep/及 > > >
[error record] navigator operation requested with a context that does not include a naviga
网络安全-病毒
PS remove watermark details
Analysis, use and extension of open source API gateway apisex
Network security - scan
Socket编程
Huakaiyun | virtual host: IP, subnet mask, gateway, default gateway
函数的定义和调用、this、严格模式、高阶函数、闭包、递归
Answers to ten questions about automated testing software testers must see
Network security ACL access control list
自定义组件、使用npm包、全局数据共享、分包
How to deal with cache hot key in redis
His experience in choosing a startup company or a big Internet company may give you some inspiration
【Camera专题】HAL层-addChannel和startChannel简析