当前位置:网站首页>Deep learning notes (constantly updating...)
Deep learning notes (constantly updating...)
2022-07-03 01:57:00 【North Village South】
Data preprocessing One-Hot - You know (zhihu.com)
A person without touching each other , In a special way , Have a series of questions and answers with each other . If for a long time , He can't judge whether the other party is a person or a computer based on these questions , Then it can be considered that the computer is intelligent .
—— Alan · Turing (Alan Turing)
《Computing Machinery and Intelligence 》
Knowledge system
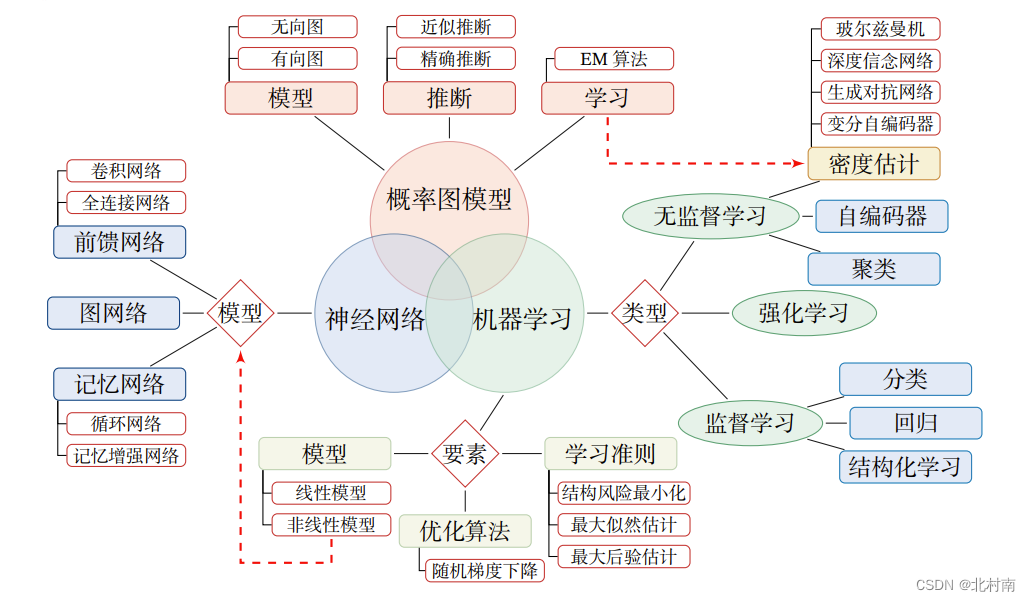
Why does deep learning mainly use neural networks ?
The main reason is that the neural network model can use error back propagation BP Algorithm , So we can better solve the problem of contribution distribution
What neural networks need to learn : The weight parameter of the connection between each neuron
Why use activation functions : If you don't use the activation function , Then the output of each layer is the linear function of the input of the previous layer , Then eventually, the whole network is linear , That is, the most primitive perceptron (Perceptron), Its presentation ability is poor
Neuron
Neural networks are composed of Neuron Composed of , The structure of each neuron is as follows

Activation function
among f Is the activation function , common Activation function as follows
Sigmoid function

ReLu function

Swish function

Network structure
There are three common network structures , Feedforward networks FNN Similar to a directed acyclic graph , Information can only spread in one direction , It's simpler . Memory network MN Similar to a directed cyclic graph , Information can be transmitted in one direction or two directions , More complicated . Figure network GN It is the generalization of feedforward network and memory network , Each square is one or a group of neurons

Reference material
《 Neural networks and deep learning 》-- Professor Qiu Xipeng
《 Hands-on deep learning 》Pytorch Open source -- Li Mu
《2022 Deep learning and machine learning 》-- Wu enda
边栏推荐
- Internal connection query and external connection
- [data mining] task 2: mimic-iii data processing of medical database
- Network security - scan
- Network security ACL access control list
- 云原生题目整理(待更新)
- 疫情当头,作为Leader如何进行团队的管理?| 社区征文
- Sweet talk generator, regular greeting email machine... Open source programmers pay too much for this Valentine's day
- Network security - the simplest virus
- [leetcode] 797 and 1189 (basis of graph theory)
- [Yu Yue education] Jiujiang University material analysis and testing technology reference
猜你喜欢

Everything文件搜索工具
Virtual list
![[shutter] hero animation (hero realizes radial animation | hero component createrecttween setting)](/img/e7/915404743d6639ac359bb4e7f7fbb7.jpg)
[shutter] hero animation (hero realizes radial animation | hero component createrecttween setting)
Take you ten days to easily complete the go micro service series (II)

深度学习笔记(持续更新中。。。)
Wechat applet Development Tool Post net:: Err Proxy Connexion Problèmes d'agent défectueux

Visualisation de l'ensemble de données au format yolov5 (fichier labelme json)

Everything file search tool

【数据挖掘】任务3:决策树分类

可視化yolov5格式數據集(labelme json文件)
随机推荐
File class (add / delete)
小程序開發的部分功能
Return the only different value (de duplication)
[North Asia data recovery] data recovery case of raid crash caused by hard disk disconnection during data synchronization of hot spare disk of RAID5 disk array
网络安全-破解系统密码
[shutter] animation animation (animatedbuilder animation use process | create animation controller | create animation | create components for animation | associate animation with components | animatio
Learn BeanShell before you dare to say you know JMeter
Storage basic operation
技术大佬准备就绪,话题C位由你决定
[Appendix 6 Application of reflection] Application of reflection: dynamic agent
Network security - vulnerabilities and Trojans
微信小程序開發工具 POST net::ERR_PROXY_CONNECTION_FAILED 代理問題
Cloud native topic sorting (to be updated)
How is the mask effect achieved in the LPL ban/pick selection stage?
网络安全-扫描
A 30-year-old software tester, who has been unemployed for 4 months, is confused and doesn't know what to do?
File class (check)
Prohibited package name
Query product cases - page rendering data
[data mining] task 3: decision tree classification