当前位置:网站首页>Network security - password cracking
Network security - password cracking
2022-07-03 01:42:00 【One of IT guys】
Reference video :
边栏推荐
- 网络安全-木马
- GDB 在嵌入式中的相关概念
- Tâche 6: regroupement DBSCAN
- LeetCode 987. Vertical order transverse of a binary tree - Binary Tree Series Question 7
- Pytest learning notes (12) -allure feature · @allure Step () and allure attach
- Network security ACL access control list
- C application interface development foundation - form control (3) - file control
- [shutter] animation animation (basic process of shutter animation | create animation controller | create animation | set value listener | set state listener | use animation values in layout | animatio
- Qtablewidget lazy load remaining memory, no card!
- Scheme and practice of cold and hot separation of massive data
猜你喜欢

NCTF 2018 part Title WP (1)
【QT】自定义控件的封装

力扣 204. 计数质数
![[error record] an error is reported in the fluent interface (no mediaquery widget ancestor found. | scaffold widgets require a mediaquery)](/img/fd/d862412db43a641537fd67f7910741.jpg)
[error record] an error is reported in the fluent interface (no mediaquery widget ancestor found. | scaffold widgets require a mediaquery)

Force buckle 204 Count prime
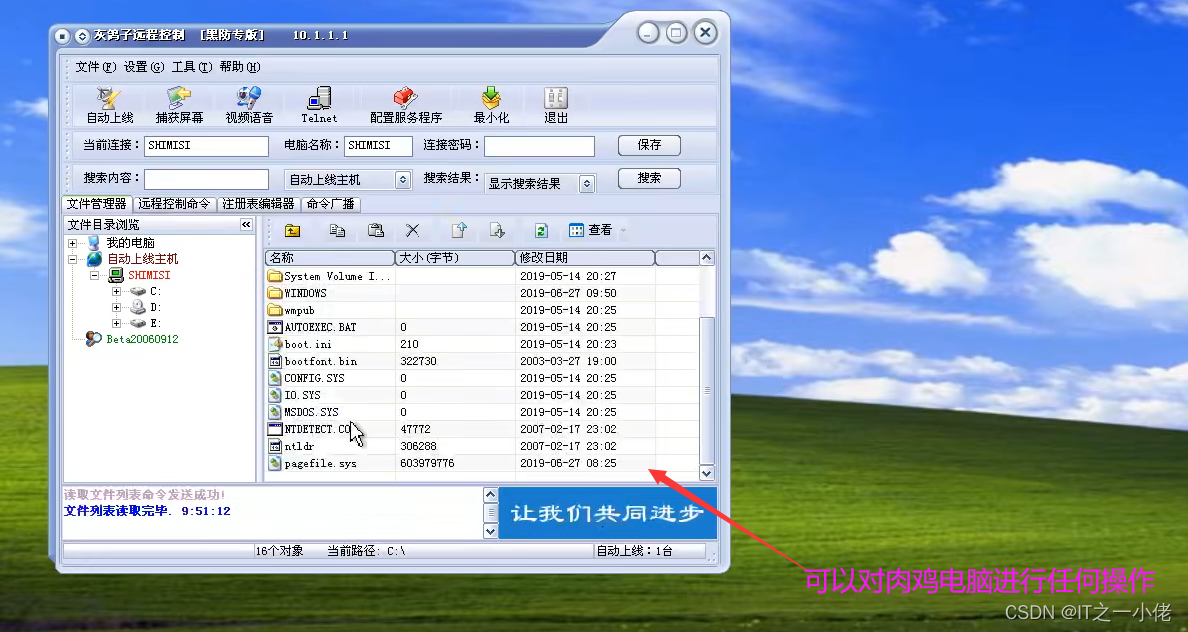
网络安全-漏洞与木马
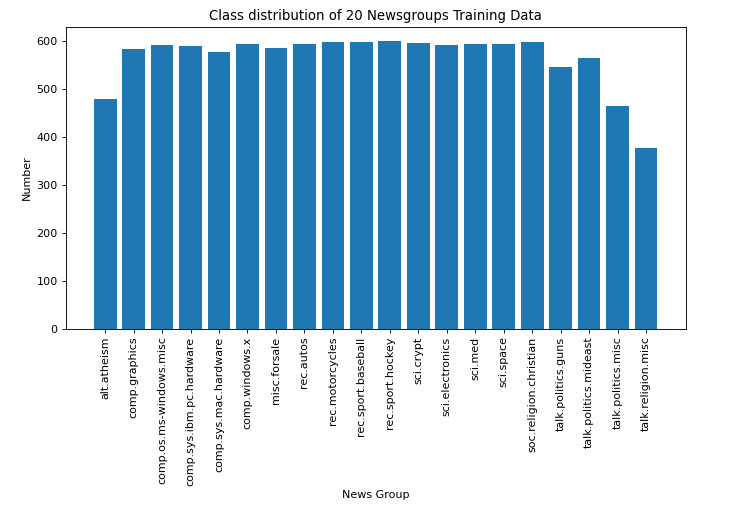
【数据挖掘】任务4:20Newsgroups聚类
Virtual list

leetcode刷题_两数之和 II - 输入有序数组

简易分析fgui依赖关系工具
随机推荐
Main features of transport layer TCP and TCP connection
Smart management of Green Cities: Digital twin underground integrated pipe gallery platform
Dotconnect for PostgreSQL data provider
The meaning of wildcard, patsubst and notdir in makefile
Openresty cache
网络安全-扫描与密码爆破2
One of the C language practical projects is greedy snake
[error record] the shutter component reports an error (no directionality widget found. | richtext widgets require a directionality)
openresty 缓存
Learn the five skills you need to master in cloud computing application development
网络安全-扫描
VIM 9.0 is officially released! The execution speed of the new script can be increased by up to 100 times
Qtablewidget lazy load remaining memory, no card!
Network security - DNS spoofing and phishing websites
Take you ten days to easily complete the go micro service series (I)
[Appendix 6 Application of reflection] Application of reflection: dynamic agent
[技术发展-23]:DSP在未来融合网络中的应用
Mathematical Knowledge: Steps - Nim Games - Game Theory
网络安全-最简单的病毒
[data mining] task 3: decision tree classification