当前位置:网站首页>Programmer vs hacker thinking | daily anecdotes
Programmer vs hacker thinking | daily anecdotes
2022-06-25 15:37:00 【CSDN program life】

Poke a little program to see more !
Go to period boring smell
* When programmers are asked if they can repair computers … | Daily anecdotes
* What programmers really think | Daily anecdotes
* Disturbed when the programmer is programming | Daily anecdotes
* When you think you caught all the exceptions … | Daily anecdotes
* Six diagrams explain the life of programmers | Daily anecdotes

Every one you ordered “ Looking at ”, I take it seriously that I like
边栏推荐
- What is the safest app for stock account opening? Tell me what you know
- Lombok common notes
- 双目3D感知(一):双目初步认识
- 客户经理给的开户链接办理股票开户安全吗?我想开个户
- Install Kali extension 1: (kali resolution problem)
- Summary of regularization methods
- iconv_ Open returns error code 22
- Data preprocessing - normalization and standardization
- 剑指 Offer 04. 二维数组中的查找
- Sword finger offer II 091 Paint the house
猜你喜欢

Data feature analysis skills - correlation test

JVM memory region details
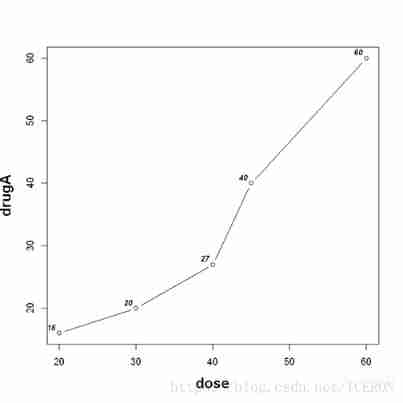
Graphic control and layout basis of R visualization
![[paper notes] contextual transformer networks for visual recognition](/img/e4/45185983e28664564bbf79023ccbf6.jpg)
[paper notes] contextual transformer networks for visual recognition

Afterword of Parl intensive learning 7-day punch in camp

(1) Introduction
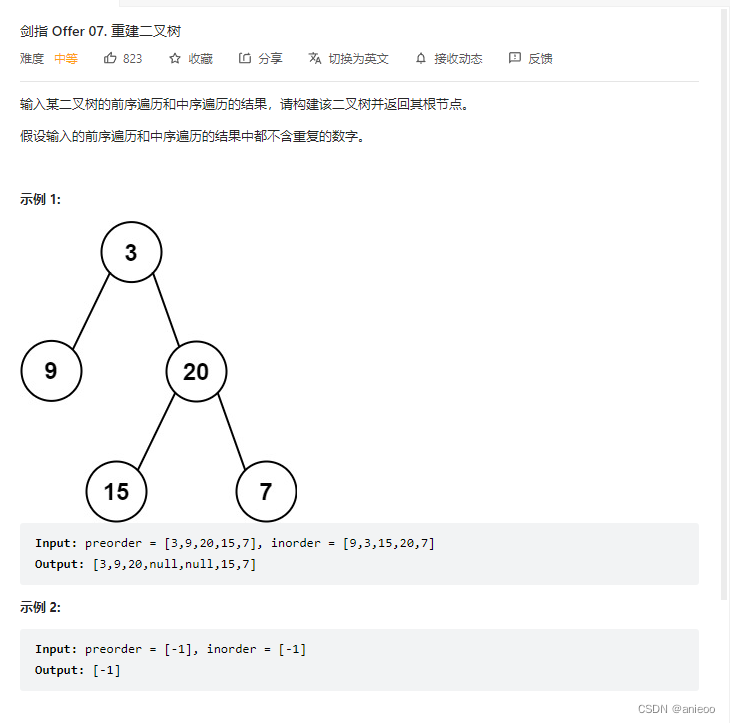
Sword finger offer 07 Rebuild binary tree

Summary of four parameter adjustment methods for machine learning

MySQL field truncation principle and source code analysis
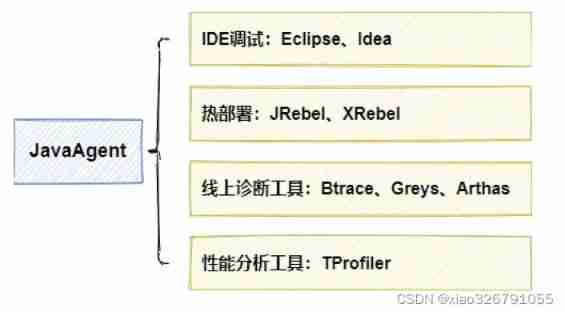
Agent and classloader
随机推荐
[C language] 32 keyword memory skills
Pytorch distributed test pit summary
Solve valueerror: invalid literal for int() with base 10
Sword finger offer 03 Duplicate number in array
Install Kali extension 1: (kali resolution problem)
Kali SSH Remote Login
[paper notes] contextual transformer networks for visual recognition
Reflection - learning notes
Architecture evolution of high-performance servers -- Suggestions
Websocket (WS) cluster solution
[paper notes] rethinking and improving relative position encoding for vision transformer
Lombok common notes
Distributed transaction solution
QT set process startup and self startup
剑指 Offer 05. 替换空格
Differences and solutions of redis cache avalanche, cache penetration and cache breakdown
Principle and implementation of MySQL master-slave replication (docker Implementation)
通过客户经理的开户链接开股票账户安全吗?
Paddlepaddle paper reproduction course biggan learning experience
股票开户用什么app最安全?知道的给说一下吧