当前位置:网站首页>Daily book CSO advanced road first exposed
Daily book CSO advanced road first exposed
2022-07-02 21:47:00 【Editorial Department of new programmer】

2014 year 2 month 27 Japan , The central network security and Informatization Leading Group was established . In the name of this group , “ Network security ” Be placed in “ Promotion of information technology ” In front of , It marks that the development of Chinese organizations has entered a new era , It is clear to ensure development with safety 、 The new concept of promoting safety through development .
In this new stage , Different from the previous poor entrepreneurial period , Chinese enterprises have made radical development in business , It needs to be guaranteed by system and process , Drive safely , Like Alibaba's goal , To be “ business 101 year ” The enterprise . This is not only reflected in the operating profits to support development , More importantly, we should not die suddenly in the face of crisis and risk .
therefore , future CSO Your role in the company is indispensable .《CSO Advanced road : From safety engineer to chief safety officer 》 emerge as the times require , Try to solve the following four problems :

First of all , What kind of chief security officer does the enterprise need in the future ?
second , How to understand and deal with the crisis faced by enterprises ?
Third , Under safety requirements , How to build a comprehensive security system in the organization ?
Fourth , How to face the challenge of unknown risks to enterprise management ?
The editors recommend
(1) Years of experience of many senior experts , It focuses on describing the system capabilities and overall perspective of network security practitioners , It has been highly praised by industry experts .
(2) The content covers event handling 、 Crisis response 、 Attack and defense 、 Investigation and traceability 、 Mocha ITOM 、 Internal control of enterprises 、 Corporate governance 、 effective communication 、 Safe ecology and other multi-dimensional career secrets .
How to read this book
This book is divided into four parts , The first chapter introduces the connotation of network security and informatization , Let readers deeply understand the impact of information technology on people's production and lifestyle 、 The Internet has transformed the fundamental aspects of the world and society , Understand the relationship between safety and enterprise development in the new pattern and environment , And the career path and skill map of the chief safety officer .
The second part mainly expounds CSO First level skill . For a new chief safety officer , It is more efficient to deal with internal safety incidents and accidents . This article introduces the standard management method of network security incident disposal 、 Setting of classification and classification mechanism of security events 、 Handling and review of safety events , At the same time, it expounds the mechanism design of enterprise crisis response 、 Business continuity management and disaster recovery plan 、 Practical cases of emergency and crisis management , From Internet enterprises to financial businesses , From denial of service attacks to privacy breaches , Use examples to deepen readers' understanding of crisis response mechanism .
The third part is for the chief security officer in the advanced stage , It focuses on the security capability guarantee map throughout the enterprise business life cycle , The content involves the design and implementation of risk management and internal control mechanism , Help organizations identify potential threats and weaknesses , How can the chief safety officer obtain the support of enterprise operators and allocate resources reasonably and effectively , And take the network security capability system as the core , The method and process of building a comprehensive protection mechanism .
The fourth chapter introduces the high-level ability to become the chief security officer . Different from the previous chapters of this book , This article focuses on how the chief security officer prepares for handling unknown security risks , Because high-level security managers are always facing unconventional network security problems . This article mainly involves the classification and description of unknown risks , Clarify the source and objective of the risk , And the principles of resource acquisition and allocation to deal with unknown risks ; At the same time, the establishment of early warning mechanism is discussed — Getting the information of unknown risks at the first time requires a complete set of processes and methods , We also need to expand the counteraction and deterrence capabilities of network security , Finally, the network security risks can be controlled and prevented .
Author's brief introduction
Zhang Wei
Cyber security veterans ,(ISC)² The first 9 The Asia Pacific Information Security Leadership achievement plan (ISLA) Winner of information security expert Contribution Award , Fudan University MBA Guest lecturer , The largest network security practitioner community of Party A in China, enterprise network security expert alliance ( Everyone said ) One of the sponsors , Committed to leading the country to surpass 2000 Several sub cloud member enterprises have explored the road of network security construction and guarantee in line with China's national conditions .
Zhangyaojiang
One of the earliest development team members of China's Shenzhou series manned spacecraft , The earliest introduction and transformation in China ISO27001 And other international standards , Anyan consulting and the founder of anyin new media .
Zhao Rui
Person in charge of network security and compliance of a multinational enterprise , Zhuziyun, President of Shanghai Branch , The United Nations ITU-T DevOps Experts in the core compilation of international standards ,CCSF Excellent chief safety officer .
Xu Zhengwei
Financial security experts , Once served in a department of the people's Liberation Army 、 Cisco R & D Center 、 Alibaba Group Security Department , Participate in the emergency response work of dealing with too many cyber attacks on the national key guarantee infrastructure , Racing enthusiasts , Self drive across the Sichuan Tibet line twice ,BMW Second place in the amateur car race .
Chen Xinwei
China Merchants Bank Zhaoyin yunchuang information security compliance principal , near 20 Years of network security experience , Dug a hole 、 Entrepreneurship 、 Protect the net 、 Manage people , hold 20 More than invention patents and utility model patents .
He Zhuo
Head of security management of Chinatelecom wing payment , An evaluation expert of the Security Evaluation Center for new Internet technologies and new businesses of the China Academy of information and communications , The current (ISC)² Director of Shanghai Branch , Zhuziyun, director of Shanghai Branch .
Zhang Yuan
Head of network security of Geely Automobile Group , Technical experts in the automotive industry , One of the earliest TISAX Standards research and practitioners , Zhuziyun, director of Hangzhou Branch .
The system capability and overall perspective of network security practitioners
Covers incident handling 、 Crisis response 、 Attack and defense 、 Investigation and traceability 、 Mocha ITOM 、 Internal control of enterprises 、 Corporate governance 、 effective communication 、 Safe ecology and other multi-dimensional career secrets .
- 11 A kind of crisis response practice
- 6 Build a comprehensive security system
- 3 Recruit to prevent unknown sudden risks
Four features of this book :
- Comprehensive knowledge , Improve network security from the system capability and overall perspective of others
- Author senior , From finance 、 telecom 、 Internet 、 Senior authors from many industries, such as automobile, have made great efforts
- In depth content , Comprehensively sorted out the advanced path of milling from technicians to industry leaders
- Pay attention to practical operation ,11 A kind of crisis response practice ,6 Build a comprehensive security system ,3 Recruit to prevent unknown sudden Phoenix risks
边栏推荐
- The web version of xshell supports FTP connection and SFTP connection
- [shutter] statefulwidget component (image component | textfield component)
- Market trend report, technical dynamic innovation and market forecast of China's low gloss instrument
- Etcd Raft 协议
- Basic knowledge of tree and binary tree (detailed illustration)
- [shutter] shutter page Jump (route | navigator | page close)
- China plastic bottle and container market trend report, technological innovation and market forecast
- MySQL learning record (2)
- Go web programming practice (2) -- process control statement
- China microporous membrane filtration market trend report, technological innovation and market forecast
猜你喜欢

如何防止你的 jar 被反编译?
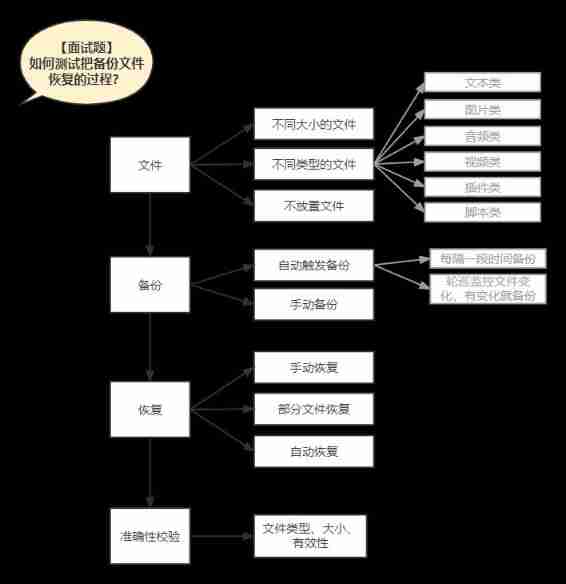
How to test the process of restoring backup files?

Redis distributed lock failure, I can't help but want to burst

Interpretation of CVPR paper | generation of high fidelity fashion models with weak supervision
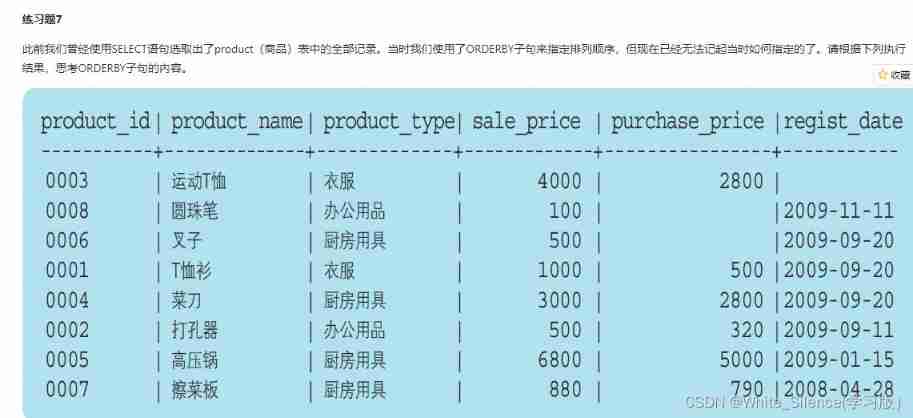
MySQL learning record (5)
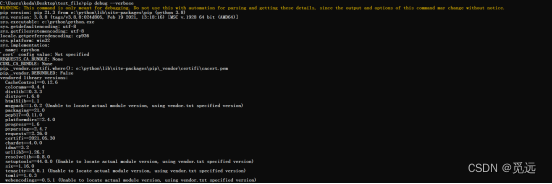
Pip install whl file Error: Error: … Ce n'est pas une roue supportée sur cette plateforme
![[shutter] shutter layout component (wrap component | expanded component)](/img/a7/824a990235fc5ce67841ebdcf001fb.jpg)
[shutter] shutter layout component (wrap component | expanded component)
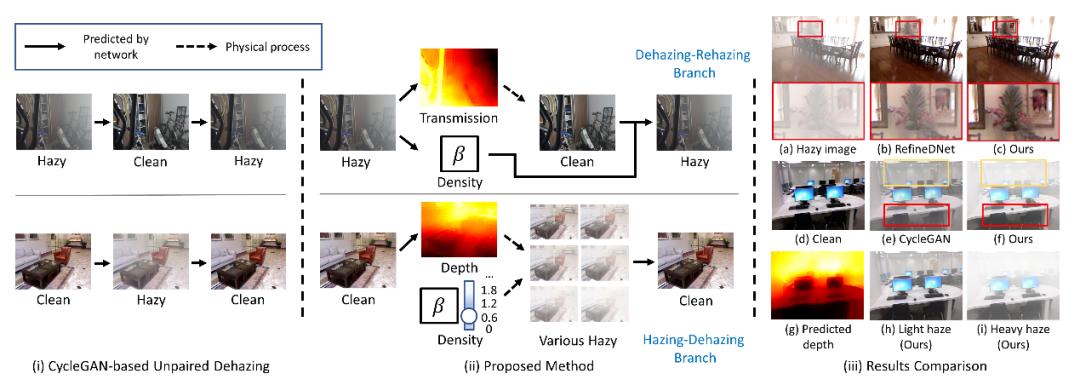
D4:非成对图像去雾,基于密度与深度分解的自增强方法(CVPR 2022)
How is LinkedList added?

One week dynamics of dragon lizard community | 2.07-2.13
随机推荐
pip安装whl文件报错:ERROR: ... is not a supported wheel on this platform
Market trend report, technical dynamic innovation and market forecast of China's low gloss instrument
GEE:(二)对影像进行重采样
Research Report on market supply and demand and strategy of microplate instrument industry in China
Research Report on plastic antioxidant industry - market status analysis and development prospect forecast
MySQL learning record (3)
读博士吧,研究奶牛的那种!鲁汶大学 Livestock Technology 组博士招生,牛奶质量监测...
Off chip ADC commissioning record
Gee: (II) resampling the image
Accounting regulations and professional ethics [16]
Get weekday / day of week for datetime column of dataframe - get weekday / day of week for datetime column of dataframe
Browser - clean up the cache of JS in the page
【剑指 Offer 】56 - II. 数组中数字出现的次数 II
LandingSite eBand B1冒烟测试用例
Analysis of enterprise financial statements [2]
Interpretation of CVPR paper | generation of high fidelity fashion models with weak supervision
Research Report on micro gripper industry - market status analysis and development prospect prediction
Construction and maintenance of business websites [7]
*C语言期末课程设计*——通讯录管理系统(完整项目+源代码+详细注释)
The web version of xshell supports FTP connection and SFTP connection [detailed tutorial] continued from the previous article