当前位置:网站首页>面试官:JVM如何分配和回收堆外内存
面试官:JVM如何分配和回收堆外内存
2022-07-03 16:04:00 【InfoQ】
JVM内存模型
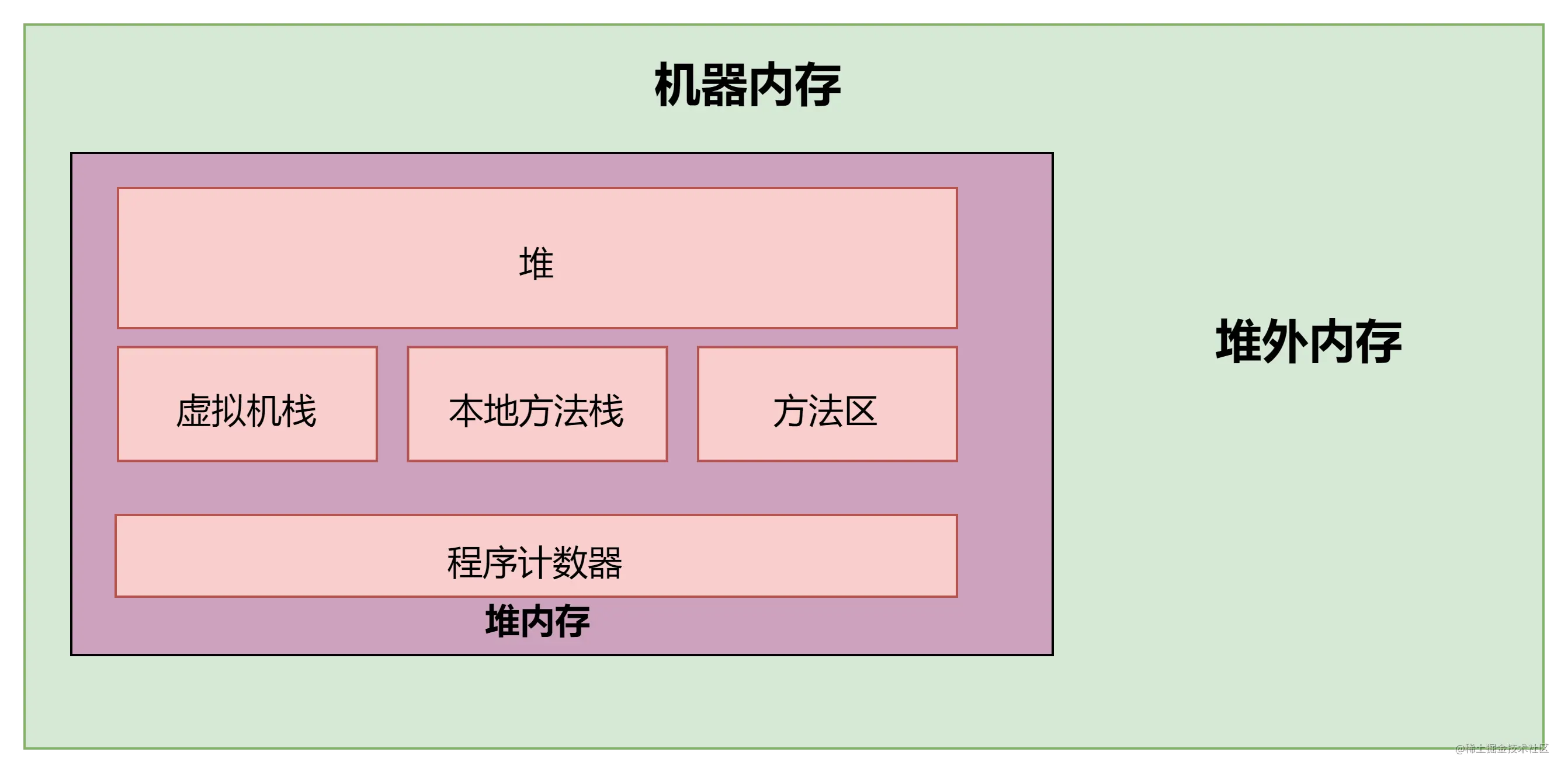
如何分配堆外内存
第一种方式:ByteBuffer#allocateDirect
//分配10M的内存
ByteBuffer byteBuffer = ByteBuffer.allocateDirect(10 * 1024 * 1024);第二种方式:Unsafe#allocateMemory
public class Test {
private static Unsafe unsafe = null;
public static void main(String[] args) throws NoSuchFieldException, IllegalAccessException {
//分配10M的内存
Field getUnsafe = Unsafe.class.getDeclaredField("theUnsafe");
getUnsafe.setAccessible(true);
unsafe = (Unsafe)getUnsafe.get(null);
//分配完内存返回内存的地址
long address = unsafe.allocateMemory(10 * 1024 * 1024);
}
}如何回收堆外内存
第一种方式:Unsafe#freeMemory
public class Test {
private static Unsafe unsafe = null;
public static void main(String[] args) throws NoSuchFieldException, IllegalAccessException {
//分配10M的内存
Field getUnsafe = Unsafe.class.getDeclaredField("theUnsafe");
getUnsafe.setAccessible(true);
unsafe = (Unsafe)getUnsafe.get(null);
//分配完内存返回内存的地址
long address = unsafe.allocateMemory(10 * 1024 * 1024);
//回收分配的堆外内存
unsafe.freeMemory(address);
}
}第二种方式:JVM回收堆外内存

- JVM执行Full GC时会将DirectByteBuffer进行回收,回收之后Clearner就不存在引用关系
- 再下一次发生GC时会将Cleaner对象放入ReferenceQueue中,同时将Cleaner从链表中移除
- 最后调用unsafe#freeMemory清除堆外内存
注意点
注意点1:
注意点2:
边栏推荐
- Initial test of scikit learn Library
- Use percent sign in CString
- How to thicken the brush in the graphical interface
- Embedded development: seven reasons to avoid open source software
- Introduction series of software reverse cracking (1) - common configurations and function windows of xdbg32/64
- How can technology managers quickly improve leadership?
- Reading notes of "micro service design" (Part 2)
- Redis在Windows以及Linux系统下的安装
- Detailed explanation of string function and string function with unlimited length
- 一些事情的反思
猜你喜欢
The difference between calling by value and simulating calling by reference

使用AUR下载并安装常用程序

Brush questions -- sword finger offer
Stm32f103c8t6 firmware library lighting
Srs4.0+obs studio+vlc3 (environment construction and basic use demonstration)

CString的GetBuffer和ReleaseBuffer使用说明

2022年Q2加密市场投融资报告:GameFi成为投资关键词
Introduction series of software reverse cracking (1) - common configurations and function windows of xdbg32/64

近视:摘镜or配镜?这些问题必须先了解清楚

QT use qzxing to generate QR code
随机推荐
App移动端测试【4】apk的操纵
《微服务设计》读书笔记(上)
Mb10m-asemi rectifier bridge mb10m
Go language self-study series | if else statement in golang
Win32 create window and button (lightweight)
Go语言自学系列 | golang中的if else语句
找映射关系
[combinatorics] combinatorial identities (review of eight combinatorial identities | product of combinatorial identities 1 | proof | use scenario | general method for finding combinatorial numbers)
Using optimistic lock and pessimistic lock in MySQL to realize distributed lock
Distributed task scheduling XXL job
[system safety] 43 PowerShell malicious code detection series (5) automatic extraction of ten thousand words from abstract syntax tree
The accept attribute of the El upload upload component restricts the file type (detailed explanation of the case)
A Fei's expectation
Under VC, Unicode and ANSI are converted to each other, cstringw and std:: string are converted to each other
阿飞的期望
Create gradle project
请做好3年内随时失业的准备?
Is it safe to open an account with tongdaxin?
[web security] - [SQL injection] - error detection injection
Detailed pointer advanced 1