当前位置:网站首页>Bits and Information & integer notes
Bits and Information & integer notes
2022-07-07 14:53:00 【weixin_ forty-five million seven hundred and fifty thousand fou】
Basic knowledge of machine operation :
1、 Binary system because :a. Switch circuit characteristics ;b. The operation mode is simple ;c. Anti interference ;d. Matching Boolean algebra , And become the number system used by electronic computers .
Binary system 、 Hexadecimal 、 The conversion between the three decimal systems ( Bottom weight formula 、 Power splicing and so on ), Hexadecimal addition and subtraction operations will be applied to memory address operations .
2、 Bit operation and logic operation :
Note that bit operations expand parameters into bit vectors , Then operate by bit , The result is still a bit vector ; Logical operations only judge whether operands are non 0 Only judge whether it is not 0, by 0 Then it's false , Not 0 It is true . The result is either 0x00( false ), Either for 0x01( really ).
3、 Shift operation :
Shift operation can be realized very conveniently 2 Multiplication and division to the power of ( But this is not the only use of displacement ). Logical left shift and arithmetic left shift are complemented on the right after the shift 0; Logical shift right , Left complement 0,; Logical shift right , On the left is the sign bit ( Nonnegative complement 0, Negative numbers make up 1).
4、 Memory Is a linear combination of bytes , Memory is addressed by bytes , That is, one address corresponds to one byte , The storage of data in memory follows two patterns ( Big end method and small end method ).
Small end method keyword : Small 、 low 、 low ( The small endian method is to put the low order byte on the low order of the data ); Or a pithy formula : high and low ( High data to high address , Low data to low address )
Signed numbers and their relationship with unsigned numbers :
1、 Complement code : The definition of complement is to take the first place as the sign bit and turn it into a negative weight , So as to realize the expression of negative numbers ; In essence , The complement is to set the highest digit to 1 Binary number of “ translation ”2w To negative half axis , A negative number used to express a complementary relationship with it .eg:w=4, 1010 Originally +10, Changing to complement means and +10 stay 24=16 Complementary in scope -6.
2、 The value and range of complement : Use the complement value box , Or use complementary relationships , Or directly use the bottom weight formula that defines the complement , Find the value of complement . By observing the value range of complement, we can find , Different from the original code and inverse code , There is only one complement 0, It is convenient to confirm the calculation results . Also because of being alone 0 The existence of , The range of complement is asymmetric .w Signed number of bits ( Complement code ) The range of phi is zero :-2w-1—2w-1-1.
3、 Ask for a complement Methods : To reverse directly +1;|X| First from the right 1 And its right side remains unchanged , The left side is reversed .( The sign bit is also reversed )
4、 Mutual mapping and transformation :
Signed numbers and unsigned numbers are mapped one by one , The key point of mapping , It is also the only connection point , Is their binary expression . A binary vector , It can be explained as signed number and unsigned number respectively , Between the two numbers explained separately , If it is a non negative number, they are the same ( The complement of a nonnegative number makes itself ), If one of them is negative, the difference between the two is 2w. stay C In language, the two can be forcibly converted to each other .
边栏推荐
- Ascend 910 realizes tensorflow1.15 to realize the Minist handwritten digit recognition of lenet network
- Cvpr2022 | backdoor attack based on frequency injection in medical image analysis
- 6. Electron borderless window and transparent window lock mode setting window icon
- IDA pro逆向工具寻找socket server的IP和port
- 广州开发区让地理标志产品助力乡村振兴
- A laravel background management expansion package you can't miss - Voyager
- 电脑Win7系统桌面图标太大怎么调小
- 暑期安全很重要!应急安全教育走进幼儿园
- PD虚拟机教程:如何在ParallelsDesktop虚拟机中设置可使用的快捷键?
- EMQX 5.0 发布:单集群支持 1 亿 MQTT 连接的开源物联网消息服务器
猜你喜欢
Apache multiple component vulnerability disclosure (cve-2022-32533/cve-2022-33980/cve-2021-37839)

在软件工程领域,搞科研的这十年!
Niuke real problem programming - day13
Niuke real problem programming - Day10

暑期安全很重要!应急安全教育走进幼儿园
Spatiotemporal deformable convolution for compressed video quality enhancement (STDF)
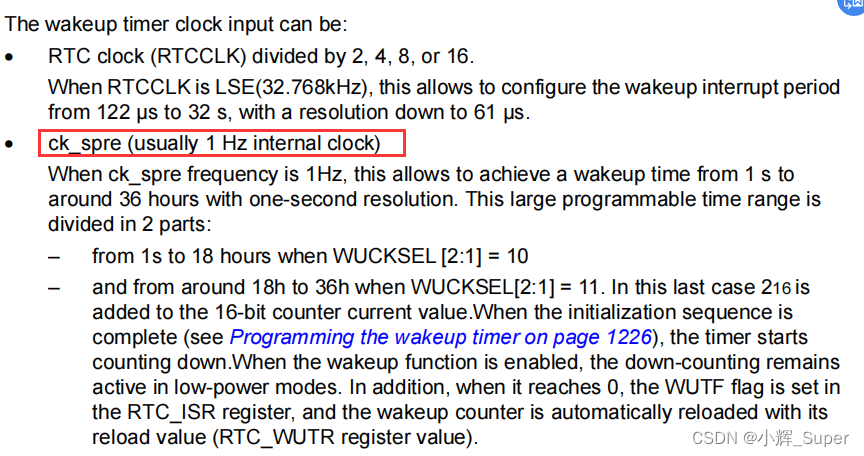
Pandora IOT development board learning (HAL Library) - Experiment 12 RTC real-time clock experiment (learning notes)
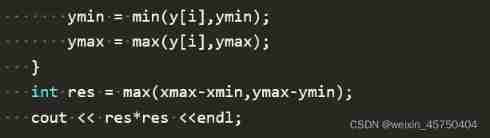
Niuke real problem programming - Day11
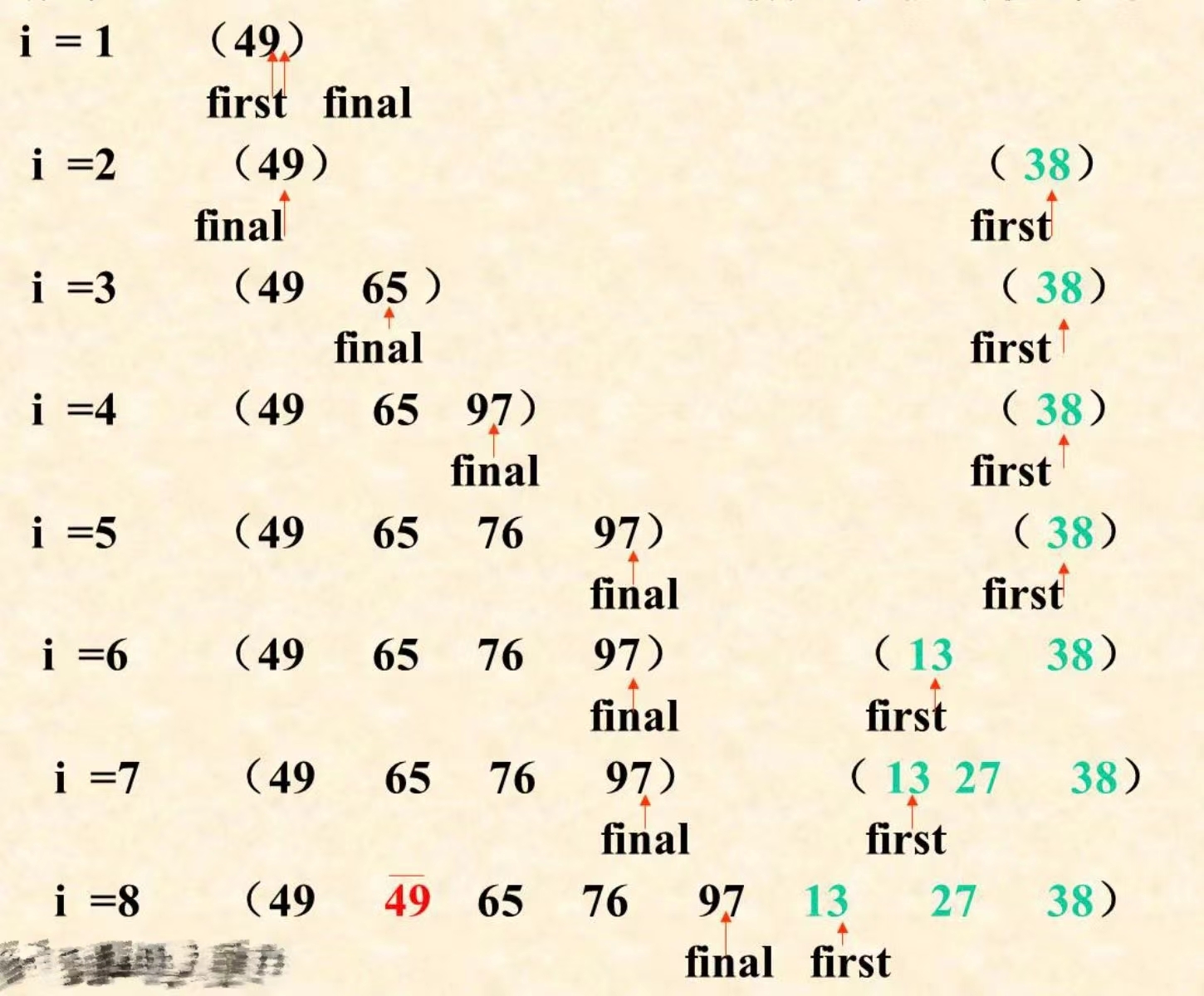
Internal sort - insert sort
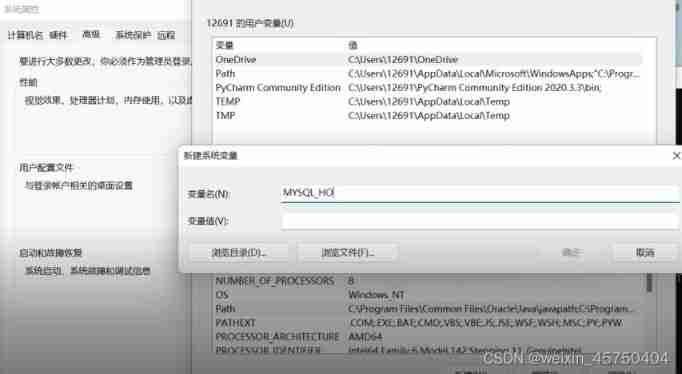
MySQL installation configuration 2021 in Windows Environment
随机推荐
Decrypt the three dimensional design of the game
MicTR01 Tester 振弦采集模块开发套件使用说明
Deformable convolutional dense network for enhancing compressed video quality
Used by Jetson AgX Orin canfd
Cocoscreator resource encryption and decryption
How does the database perform dynamic custom sorting?
一款你不容错过的Laravel后台管理扩展包 —— Voyager
EMQX 5.0 发布:单集群支持 1 亿 MQTT 连接的开源物联网消息服务器
In the field of software engineering, we have been doing scientific research for ten years!
Leetcode one question per day (636. exclusive time of functions)
Niuke real problem programming - day16
PG基础篇--逻辑结构管理(锁机制--表锁)
Attribute keywords ondelete, private, readonly, required
CTFshow,信息搜集:web12
寺岗电子称修改IP简易步骤
Full details of efficientnet model
Data connection mode in low code platform (Part 2)
潘多拉 IOT 开发板学习(HAL 库)—— 实验12 RTC实时时钟实验(学习笔记)
PLC:自动纠正数据集噪声,来洗洗数据集吧 | ICLR 2021 Spotlight
用于增强压缩视频质量的可变形卷积密集网络