当前位置:网站首页>5000 word analysis: the way of container security attack and defense in actual combat scenarios
5000 word analysis: the way of container security attack and defense in actual combat scenarios
2022-06-26 15:47:00 【Trail safety】
In this critical period of digital transformation , The cloud native technology represented by container relies on its own advantages , Is becoming the core IT infrastructure . Cloud primordial is no longer a minority “ innovator ” The privilege of , Instead, it has become the mainstream choice in the market , Containers 、 Container cloud is becoming the mainstream form of workload .
With this , There are a lot of new technologies in the cloud , It also brings many unknown risk exposures , The objects of security protection have also undergone disruptive changes , Containers are becoming a new drill ground for hackers .
In the age of containers , Security faces the dual challenges of old and new threats . One side , Those traditional and old attacks are still effective , Including exploit 、 Brute force 、 Privilege promotion, etc . On the other hand , New attack postures are emerging one after another , For example, poisoning image 、 Vessel escape 、 colony API Call, etc , It's impossible to defend .
In the past offensive and defensive drills , There have been many cases against containers 、 Cluster attack events . Containers bring new risk exposures , It gives attackers many opportunities to take advantage of .
Why do containers become the key targets of hackers ? The author believes that the core reasons are as follows 6 In terms of :
The safety construction of containers lags behind
Although containers can be implemented more flexibly 、 Lower cost software development and application deployment , However, the corresponding container security construction lags far behind the speed of business development , A lot of “ streaking ” The container becomes the target of the attacker “ The bestselling ”.
The attack value of containers is high
In a container cluster , Just capture a container , It can be moved laterally to other containers , Or escape to node Persistent on nodes , Control the entire node . next step , Attackers can also exploit or invoke API SERVER Control the whole cluster . Cluster is a centralized system , Once lost , The defenders “ Blood strip ” A big reduction is inevitable .
The attack surface of the container is huge
In addition to the attacks introduced by the vulnerability of the application itself , colony 、 The vulnerability of the container itself can not be ignored . For example, an attacker passes through k8s、docker Unauthorized access to long drive in ; The cluster permissions are not configured properly , An attacker can create a high authority container to escape ; utilize Linux kernel cgroups modular (CVE-2022-0492) Escape .
The vulnerability of the container affects a wide range
In the traditional operation mode , The deployed software is updated on the host on which it is running , The container must be updated in the upstream image , And then redeploy . therefore , If there is a problem with the image or the underlying image , Will affect at least one or more clusters .
The protection of containers is very difficult
Container security needs to cover container construction 、 Deploy 、 Run the entire lifecycle , The links and process links involved are very complex . for example , In the build phase , Possible software supply chain attacks , Including basic image pollution 、CI Tool attack 、 Product library vulnerability attack, etc . In the deployment phase, you may also face attacks against cloud native infrastructure platforms , Including open source component orchestration tools . In the runtime phase , It may also face attacks against cloud native applications , Include SQL Inject 、 Loophole 、 Weak password, etc .
It is difficult to trace the source of container attacks
Containers have a short life cycle , Fast dynamic change , exceed 50% The entire life cycle of the container from on-line to off shelf shall not exceed 1 God . How to detect an abnormal intrusion event , Fast security response , Minimizing the loss has become a major security problem .
In the traditional security protection category , The organization's “ Endpoint 、 The Internet 、 The border ”, Each level is relatively clear , But in the cloud native environment, these boundaries disappear .
In recent years , Although the safety construction investment of enterprise organizations has increased significantly , Enterprise organizations have deployed basic firewalls 、 Leakage and 、 Terminal security and other conventional security equipment .
But when the container is under attack , Traditional safety protection means , Can not effectively protect the container . for example , stay IT Architecture , If container is included 、K8S And other new cloud native infrastructure . A simple example , An attacker can easily complete an attack in many ways . A small vulnerability may penetrate the container node , Even the whole cluster .
First step : Attack containers through container applications
Through weblogic Remote code execution vulnerability (CVE-2021-2382), Gained control of a container .
The second step : Attack other containers by collapsing containers
After gaining control of the container , It can be done by nmap And other network detection methods to find accessible container ports .
The third step : Attack the host through the container
if docker、containered Container escape vulnerability exists , This vulnerability can be exploited to gain control of the host .
Step four : Attack the cluster through the container
if K8S There is 8080、6443 Unauthorized access , Can be accessed through the container K8S master api Make malicious calls .
Just imagine , In the face of such an attack , Whether it's a boundary firewall , It is also a terminal security product , Can not complete effective safety protection , Nor can you isolate the container or kill the malicious processes in the container , Moreover, effective traceability analysis cannot be provided , The impact can only be mitigated through offline business , But this does not solve the security problem of containers from the root .
In this context , Ivy League is based on the experience of many years of practical attack and defense drills , Continuously upgrade the iteration scheme , Officially launched the upgraded version 《 Practical solutions for container security V2.0》, Interested readers can scan the code to get the electronic version .

Scan and download 《 Practical solutions for container security V2.0》
The scheme covers several core links , Include Attack risk assessment 、 Risk convergence rectification 、 Attack behavior monitoring 、 Attack event response 、 The traceability analysis report consists of five links , It can realize the active defense effect of the whole life cycle of the container .
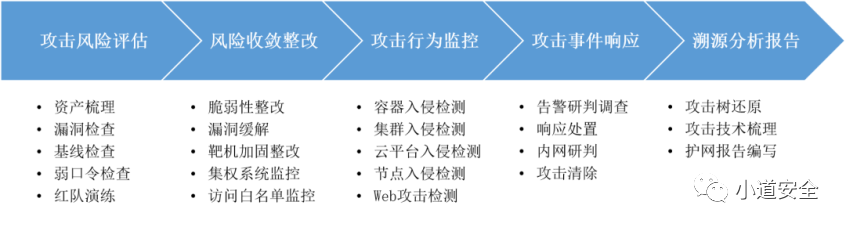
chart 1: Attack and defense drill 5 There are two core links
The first stage : Container attack risk assessment
In the early stage of the attack and defense drill , The most important thing is to make a good attack risk assessment , Including asset sorting 、 Vulnerability check 、 Baseline check 、 Weak password check, etc . The most important thing is to do a good job in sorting out assets .
According to the experience of past attack and defense practice , Many organizations do not have enough control over their own assets , As a result, some assets were not included in effective monitoring , Formed a weak point of protection .
The attack team before launching the attack , We will collect these weak points first , And take this as a springboard to attack the key systems of the enterprise . therefore , Evaluate the assets in advance , Convergence of the exposed attack surface becomes particularly important .
Workload Visualization , Eliminate container asset blind spots
In the cloud native environment , The defender must count the container assets in the early stage of the exercise , In particular, sort out intranet clusters & Non cluster managed system assets , And map assets to people . The most important thing is to have a deep perspective on the core business assets , Especially the target system 、 Centralized system, etc .
With the above detailed asset Kanban , In the event of an intrusion , You can quickly reverse query container business applications , Assist in locating the entry point and impact area of the intrusion . for example , Before an attacker takes advantage of 0day/1day When there's a leak , Defenders can pass application level asset screening , Analyze the scope of the existing business affected by the vulnerability .
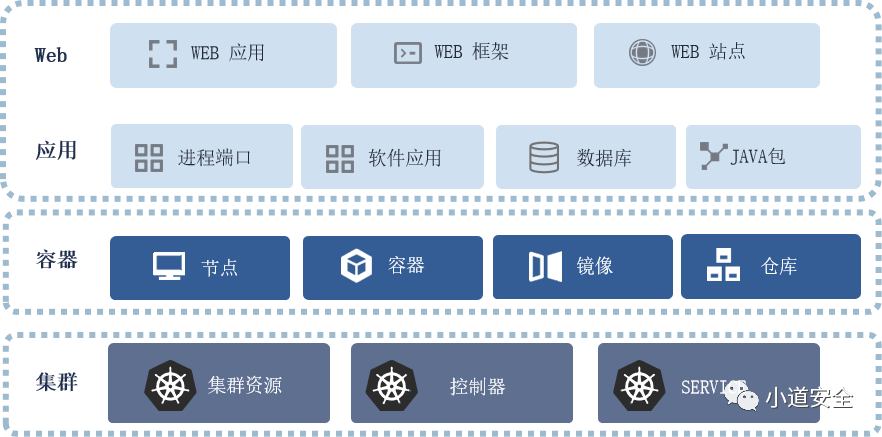
chart 2: Focus on container asset classes
Besides , You also need to sort out the application assets in the container , Discover corner systems and obsolete assets 、 Non compliant assets found , Pave the way for subsequent system reinforcement and emergency response . This process needs to focus on three aspects :
(1) Sort out the boundary between cluster and external system
First , Sort out the external exposure services of the cluster , If host network exposure service is used , Use nodeport Exposure Services . secondly , Sort out the external visits within the cluster , Non compliant external visits are found .
(2) Sort out high power 、 Privileged container
It mainly includes Privileged Privileged container 、 high Capabilities The container of 、 A container that mounts sensitive directories 、Root Container for account numbers 、Host Container for mode operation 、 Shared host namespace The container of 、 Containers for shared host devices 、CPU/ Containers with unlimited memory usage, etc .
(3) Non compliant applications found
It is mainly aimed at ssh、sudo、ftp、vsftp And so on .
Fine-grained sorting of supply chain software components , Do a good job in software management
Through fine-grained inventory of assets , It can also realize the security control of the supply chain . For business organizations , The safety of container product supply chain is also very important . Especially as cloud native application products become more and more diversified , Like a container mirror 、 helm charts They are all common product formats .
One side , It is necessary to ensure the security of the product in the application construction stage ; On the other hand, we need to store WIP ; Establish corresponding compliance checks at the time of distribution and deployment 、 Access control , Security scanning 、 Audit and access 、 Check out mechanism , Ensure the safety of the source of the product .
therefore , Before the attack and defense drill , The asset account of the software supply chain should be kept , Including running applications 、 middleware 、 database 、 Installation package 、 Framework language pack (java、go、ruby、nodejs、python、php) etc. , Find its installation path 、 Version information and configuration .

chart 3: Sinomenine honeycomb can finely comb the software components of the supply chain
The second stage : Container risk convergence reinforcement
In the attack and defense drill , Early preparation includes vulnerability rectification 、 Vulnerability mitigation 、 Target aircraft reinforcement and rectification 、 Centralized system monitoring, etc . We can summarize these technical work into two directions: risk convergence and security reinforcement . For the defender , For cloud native risk convergence reinforcement , You can sort out the system vulnerability & Rectification 、 Micro isolation and reinforcement can realize risk convergence and security reinforcement .
Vessel vulnerability assessment and rectification
Before the attack and defense drill , It is necessary to comprehensively investigate the hidden dangers of intranet security , Find and assist in rectifying the vulnerability of the container environment . There are various ways to fix vulnerabilities that may be exploited by attackers , Strengthen system security configuration , Increase the difficulty of attacker intrusion , Improve the level of security . It converges with the attack surface 、 Bug repair 、 Security policy optimization and other work have formed a complete risk management closed loop .

chart 4: Runtime vulnerability assessment & Rectification
But under the high-intensity attack in the attack and defense drill , Even if we have done a good job of risk convergence and reinforcement in the early stage , There may still be some 0day/1day High risk vulnerability , Cause the situation to be broken .
therefore , Enterprise organizations need security vendors with professional vulnerability researchers and vulnerability emergency response processes , In the 24 Within hours , Provide emergency response plan . Once the intelligence with high-risk loopholes is found during the exercise , Need to follow up as soon as possible . Sinomeni has a very sound emergency response team and a perfect response process , It can well deal with the container safety emergency disposal under the background of actual combat .
 chart 5: Sinomenine vulnerability emergency response and disposal process
chart 5: Sinomenine vulnerability emergency response and disposal process
Micro isolation control of key systems
In actual combat confrontation , It can be predicted that the attacker will launch a high-intensity long-range attack on the exercise target system . Without limiting the attack path , To control the business system 、 The ultimate goal is to obtain important data , Full scale attack . Therefore, the defender needs to micro isolate and control the important systems in the early stage of the exercise , It mainly includes two aspects :
foreign , It is necessary to sort out the boundary between container clusters and external systems , Sort out the services exposed by the cluster and the external access within the cluster , Conduct compliance control .
internal , It is necessary to sort out the important systems in the container ( The cluster system 、 Target system ) Access model in Intranet , Form an access control baseline .

chart 6: Micro isolation control of key systems
The third stage : Container attack behavior monitoring
After the attack and defense drill , The red team followed the attacker's thinking , Initiate high intensity 、 High level cyber attacks . therefore , For the blue team , Monitoring is a crucial step to be able to detect attacks in a timely manner . Ivy honeycomb can provide multi anchor detection capability , Can real-time 、 Accurately perceive intrusion events , Found lost container .

chart 7: Multi anchor monitoring covering the attack link
Container attack event monitoring
Although preventive security technology can deal with known signature based threats , But the blue team still needs network security monitoring to identify more complex threats .
therefore , The defender needs to take advantage of the host deployed in the early stage 、 Container attack monitoring system , Discover attacks in real time , And report according to the attack alarm monitoring process . In addition to being able to detect threats with known characteristics , It can also detect malicious behavior , It can also perform anomaly detection .

chart 8: Ivy honeycomb three-dimensional intrusion monitoring system
(1) Threat detection based on known characteristics
Ivy honeycomb can be used for documents in containers 、 Code 、 Scripts, etc. to detect known features , The virus in the container can be found in real time 、 dig 、webshell And other known threats . With webshell For example , Green rattan thunder fire is based on AI Reasoning found that Webshell Suspicious content in , Its Webshell The detection rate exceeds the highest level in history , the height is 99.99%, And the whole use process does not need long-term training , Plug and play .
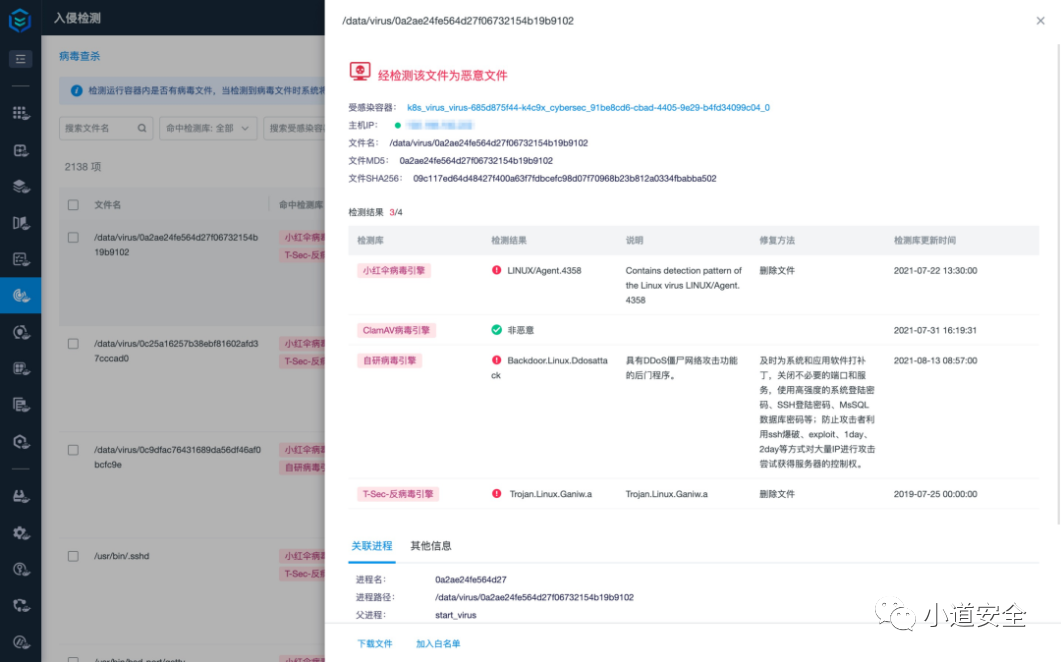
chart 9: Known threat detection
(2) Detection based on malicious behavior
Ivy honeycomb , Based on the definition of malicious behavior patterns , It can detect the hacker attacks of containers and orchestration tools in real time .
First , No file attacks can be detected in the container , Support memory discovery webshell、shellcode And loading dynamic link libraries and other memory codes .
secondly , Container escape behavior can be detected , Support discovery K8S Component vulnerability escape 、 Kernel vulnerability escape 、 Container vulnerability escape 、 Sensitive mount and escape .
Last , Can be detected K8S API A malicious act , Support includes anonymous user login 、secrets obtain 、API server Suspicious operation, etc .
chart 10: Key malicious behavior detection
(3) Detection based on abnormal behavior Ivy honeycomb , Can be applied to processes in the container 、 Network and other behaviors to learn and build models , So as to find abnormal intrusion .
For important container target 、 Cluster system to learn in advance , Form a stable model , Once an exception is found, the process starts 、 Abnormal port listening 、 Abnormal network connection and abnormal file operation will alarm immediately .

chart 11: Unknown threat detection
Handling container attacks
In the detection of ⼊ After the invasion , For collapsible containers, it is necessary to enter ⾏ Fast security response , Minimize the loss . Ivy honeycomb can implement different fine-grained control measures , It can be isolated directly at the container level 、 Pause 、 Kill the container , At the container behavior level, processes can be blocked 、 Isolate files 、 Prohibition IP, No problem workloads are allowed to access or be accessed .
Intrusion rules continue to operate
Ivy vine has collected information about the new invasion posture in the process of attack and defense , It can quickly respond and generate system rules , Enhance the product intrusion detection capability through rule updating .
at present , The latest product features of ivy bee nest , Already has custom Threat Intelligence and detection capabilities . for example , The front-line personnel of the user find the intrusion information disclosed during the attack and defense drill , It is available through the product Custom anchor detection rules and custom Threat Intelligence , Enhance the intrusion detection capability of supplementary products .
The fourth stage : Container attack event response
Once the authenticity of the alarm is determined , The security expert should pass the host 、 Logs on the container and system alarms , Investigate the attack , And generate 《XXX Incident investigation report 》. above all 2 One aspect is : Check the lost area 、 The attack process is restored .
Container attack process restore
Through the analysis and tracing of the attacked assets , Restore attack path and attack technique , Users can not only effectively improve the effect of attack and defense drill , It can also enhance the normalized security defense capability , Convert... Into potential attack , Avoid secondary attacks .

chart 12: The attack process is restored
Troubleshooting of vessel collapse range
Find a confirmed lost host according to the existing information / Container information , Then take the data of the lost host and its interconnection as a clue , Expand intranet traceability in the user system , Confirm whether there is a host penetrated laterally / Containers , And cycle the process , Step by step find out all the lost hosts / Containers , Confirm the impact area of the attack and the specific loss range , Remove the attack team from the intranet .
 chart 13: Scope of investigation
chart 13: Scope of investigation
The fifth stage : Container traceability analysis report
Ivy honeycomb , You can collect container related behavior data , Include API Call behavior log 、 Container process events 、 Container network events 、 Container file Events 、k8s Audit log events, etc , combination ATT&CK Framework model , Use big data tools to analyze security threats , Determine the impact scope and intrusion path of the attack , Actively discover other internal potential threats through threat hunting .
The defender confirmed the investigation after completing the attack 、 After restoring the whole process , Need to sort out a defense report , Explain the authenticity of the attack 、 The coverage of the attack 、 Attacker's attack path and behavior , And submit the report to the Organizer .

chart 14: Form a defensive report
As mentioned earlier , Containers have become an important target for hackers , But at present, there is a great lack of effective security measures . Foreseeable , Future containers 、 Container clustering will become the most important IT infrastructure . No matter in the real network battle , Or in the relevant offensive and defensive exercises , The cloud native infrastructure represented by the container will be a must for both offensive and defensive sides .
If you have any questions about attack and defense drills or container security , Welcome to call 400-188-9287 turn 1, Or scan the QR code directly below , receive 《 Practical solutions for container security V2.0》. You can also click “ Read the original ” Apply for a free trial Sinomenine container safety products ~

Scan and download 《 Practical solutions for container security V2.0》
边栏推荐
- 夏令营来啦!!!冲冲冲
- 买股票通过券商经理的开户二维码开户资金是否安全?想开户炒股
- # 粒子滤波 PF——三维匀速运动CV目标跟踪(粒子滤波VS扩展卡尔曼滤波)
- Learning memory barrier
- 反射修改final
- [file] VFS four structs: file, dentry, inode and super_ What is a block? difference? Relationship-- Editing
- Don't remove custom line breaks on reformat
- [tcapulusdb knowledge base] tcapulusdb doc acceptance - create business introduction
- 「干货」NFT 上中下游产业链全景分析
- 【毕业季·进击的技术er】 什么是微信小程序,带你推开小程序的大门
猜你喜欢

「干货」NFT 上中下游产业链全景分析
![[tcapulusdb knowledge base] tcapulusdb doc acceptance - transaction execution introduction](/img/7c/25a88f46e02cebd2e003b9590b9c13.png)
[tcapulusdb knowledge base] tcapulusdb doc acceptance - transaction execution introduction

PCIe Capabilities List

How to configure and use the new single line lidar

Have you ever had a Kindle with a keyboard?

AbortController的使用

简单科普Ethereum的Transaction Input Data

AbortController的使用
Using restcloud ETL shell component to schedule dataX offline tasks

【毕业季·进击的技术er】 什么是微信小程序,带你推开小程序的大门
随机推荐
Particle filter PF - 3D CV target tracking with uniform motion (particle filter vs extended Kalman filter)
【C语言练习——打印空心上三角及其变形】
反射修改final
Inaccurate data accuracy in ETL process
golang 临时对象池优化
How do I open an account on my mobile phone? Is online account opening safe?
AUTO sharding policy will apply DATA sharding policy as it failed to apply FILE sharding policy
Analyse panoramique de la chaîne industrielle en amont, en aval et en aval de la NFT « Dry goods»
HW安全响应
粒子滤波 PF——在机动目标跟踪中的应用(粒子滤波VS扩展卡尔曼滤波)
[tcapulusdb knowledge base] tcapulusdb doc acceptance - transaction execution introduction
Is it safe to open a stock account through the account opening link of the broker manager? Or is it safe to open an account in a securities company?
Secure JSON protocol
On which platform is it safe to buy shares and open an account? Ask for guidance
Nanopi duo2 connection WiFi
[tcapulusdb knowledge base] Introduction to tcapulusdb general documents
A blog to thoroughly master the theory and practice of particle filter (PF) (matlab version)
【毕业季·进击的技术er】 什么是微信小程序,带你推开小程序的大门
Summary of data interface API used in word search and translation applications
在校生学习生涯总结(2022)

