当前位置:网站首页>Getting started with caspin
Getting started with caspin
2022-07-29 03:37:00 【Nanyidao street】
List of articles
PERM Metamodel
Policy Strategy
constitute
subject(sub Accessed entities )
object( Resources accessed )
action(act Access method )
eft( Strategy results , It is generally empty , If it is empty, it means allow The situation of )(eft There are only two cases ,allow perhaps deny)
The way of writing
[policy_definition]
p = sub,obj,act,( optional eft)
Request Request rules
constitute
- subject(sub Accessed entities )
- object( Resources accessed )
- action(act Access method )
The way of writing :
[request_definition]
r = sub, obj, act
// and policy similar , Just less eft
Matchers Matching rules
effect :Request and Policy Matching rules of
The way of writing :
[matchers]
m = r.sub == p.sub && r.obj == p.obj && r.act == p.act
// Meeting the matching conditions eft Will be returned to effect Expression neutralization effect Expression , Look, what comes back is true still false
Effect influence
Writing rules :
Fixed as the following
| Policy effect | significance | Example |
|---|---|---|
| some(where (p.eft == allow)) | allow-override | ACL, RBAC, etc. |
| !some(where (p.eft == deny)) | deny-override | Deny-override |
| some(where (p.eft == allow)) && !some(where (p.eft == deny)) | allow-and-deny | Allow-and-deny |
| priority(p.eft) || deny | priority | Priority |
| subjectPriority(p.eft) | Role based priority | Topic priority |
role_definition Role domain
g = _,_ Role based
g = _,_,_ Domain based
[role definition]
g = _,_ // first _ On behalf of the user , the second _ Representative role
g = user , role
The user model
stay RBAC In the model , Use g Two related roles , They become universal
Like Guo g relation alice and data2_admin, Can be in policy Of sub Write alice/data2_admin This will pass

Multi tenant model
[role_definition] g = _,_,_
Domain matching rules :g It will receive three parameters
[matchers] m = g(r.sub,p.sub,r.dom)&&r.dom==p.dom&&r.obj==p.obj&&r.act==p.act
[request_definition]
r = sub, dom, obj, act
[policy_definition]
p = sub, dom, obj, act
[role_definition]
g = _, _, _
[policy_effect]
e = some(where (p.eft == allow))
[matchers]
m = g(r.sub, p.sub, r.dom) && r.dom == p.dom && r.obj == p.obj && r.act == p.act
Policy
p, admin, domain1, data1, read
p, admin, domain1, data1, write
p, admin, domain1, data2, read
p, admin, domain2, data2, read
p, admin, domain2, data2, write
g, alice, admin, domain1
g, bob, admin, domain2
Request
alice, domain1, data2, read
Result
true

Instance flow :
According to rules r.sub and r.dom Will look for p.sub, We are Policy According to the
gfind alice,admin,domain1 Medium admin in other words alice and admin It is equivalent. , Then we check policy In the rules , We found that According to the following matching rules data2 = data2 ,read = read2 You can exportp,admin,domain1,data2,read This record , Is there , So back true
Actual operation
Save the configuration rules to the database
go get github.com/casbin/gorm-adapter/v3
func main() {
a, _ := gormadapter.NewAdapter("mysql", "root:[email protected](127.0.0.1:3306)/casbin", true) // Your driver and data source.
e, _ := casbin.NewEnforcer("./model.conf", a)
sub := "alice" // Users who want to access resources
obj := "data1" // Resources to be accessed
act := "read" // Operations performed by users on resources
added, err := e.AddPolicy("alice", "data1", "read")
fmt.Println(added)
fmt.Println(err)
ok, err := e.Enforce(sub, obj, act)
if err != nil {
fmt.Println(" Do you eat oil cake ")
fmt.Printf("%s", err)
return
}
if ok == true {
fmt.Println(" litchi ")
} else {
fmt.Println(" Susan ")
}
}
Yes Policy Addition, deletion and modification of
filterPolicy := e.GetFilteredPolicy(0, "alice")// Inquire about index by 0 in , The name is alice The elements of
fmt.Println(filterPolicy)
//[[alice data1 read] [alice data2 read]]
// litchi
add to RBAC Mapping
policy.csv
[role_definition]
g = _,_
[matchers]
m = g(r.sub,p.sub) && r.obj == p.obj && r.act == p.act
// You need to add... To the matching group g(r.sub, p.sub) The relationship between
main.go
边栏推荐
- RTP send and receive h265
- Practical application cases of digital Twins - smart energy
- 2022-07-28 study notes of group 4 self-cultivation class (every day)
- Understanding of p-type problems, NP problems, NPC problems, and NP hard problems in natural computing
- KNN method predicts pregnancy, KNN principle simple code
- Simple use of eventbus
- C language programming | exchange binary odd and even bits (macro Implementation)
- Ten thousand words detailed Google play online application standard package format AAB
- The latest second edition of comic novels, listening to books, three in one, complete source code / integrated visa free interface / building tutorials / with acquisition interface
- Idea configuration web container and war packaging
猜你喜欢

Mathematical modeling -- analytic hierarchy process model

深入C语言(1)——操作符与表达式

【科技1】

Rongyun real-time community solution

机器学习【Numpy】
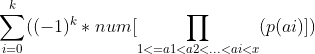
(codeforce547) c-mike and foam
![[technology 1]](/img/eb/63baf1ae3931a156a0a5b377a9b7d1.jpg)
[technology 1]
![MOS tube - rapid recovery application notes (II) [parameters and applications]](/img/54/eb040a51304192def8cfb360c7c213.png)
MOS tube - rapid recovery application notes (II) [parameters and applications]

How to solve the time zone problem in MySQL timestamp

Deep into C language (3) -- input and output stream of C
随机推荐
Learn exkmp again (exkmp template)
Three military product baselines (functional baseline, distribution baseline, product baseline) and the documents contained in the baseline
(nowcoder22529c) diner (inclusion exclusion principle + permutation and combination)
向日葵远程控制为何采用BGP服务器?自动最优路线、跨运营商高速传输
RTP 发送 和接收 h265
RTP send and receive h265
Singleton and invariant modes of concurrent mode
1.6 example: cifar-10 classification
Introduction and comparison of unicast, multicast (target broadcast, multicast), broadcast, flooding, flooding
Leetcode 1331 array sequence number conversion [map] the leetcode path of heroding
Idea configuration web container and war packaging
HDU multi School Game 2 1011 DOS card
Example analysis of while, repeat and loop loops in MySQL process control
暴力递归到动态规划 01 (机器人移动)
今晚7:30 | 连界、将门、百度、碧桂园创投四位大佬眼中的AI世界,是继续高深还是回归商业本质?...
实例搭建Flask服务(简易版)
04 | background login: login method based on account and password (Part 1)
2. 变量及作用域
Matlab learning -- structured programs and user-defined functions
Introduction to static routing and dynamic routing protocols OSPF and rip and static routing configuration commands