当前位置:网站首页>Internet of things security in the era of remote work
Internet of things security in the era of remote work
2022-06-11 10:14:00 【Software test network】
so to speak , One of the biggest impacts of the pandemic on enterprises is the change of work habits , This leads to remote work and Internet of things security . At the peak of lock limits , Telecommuting has become the norm , Even though the office has begun to reopen , This is still the preferred working mode for many employees . for example , According to a recent Pew study , Among the employees who work from home are 76% Expressing their preferences is the main reason why they do this .

Working remotely after a pandemic
As employees and employers have long adapted to telecommuting , It is important that they keep abreast of emerging security issues . When I suddenly switched to remote mode two years ago , Companies and employees are scrambling to ensure that everyone and everything are connected . In confusion , Safety is usually an afterthought , But today companies have the opportunity to eliminate any lingering vulnerabilities and ensure a more secure remote model .
Internet of things security issues
When most workers are working outside the physical location , There are usually sound safety procedures . When employees work remotely , It is not always possible or practical to implement these . Besides ,WFH The model introduces its own security issues , Including weak passwords on personal computers 、 Poor security Wi-Fi Or family Alexa Deliver malware .
that , What can be done to address these vulnerabilities ? Some are right IT Helpful tips for both departments and employees include :
- Carefully review collaboration tools before connecting them to help mitigate security vulnerabilities .
- Do not reuse or share passwords , And understand the impact of this bad practice .
- Deploy technologies that automatically detect and prevent compromised credentials .
- Be aware of remote specific phishing scams , for example Skype、Slack and Zoom, Have become popular phishing bait .
Network security
Network security is another important consideration . Employees may be aware of office security best practices , But it is not uncommon for them to be less vigilant at home . Companies with remote employees must educate them about home network risk , The fact that many household products, including baby monitors or smart TVs, may introduce many security vulnerabilities . Besides , It is always possible for a child or spouse to inadvertently download malware on the home network . For these and other reasons , The organization should encourage employees to establish a separate Wi-Fi account , As far as possible for business purposes only . When employees are not working in the office , Use their VPN Access to any file or system is also important .
Risks of workarounds
Another problem that needs to be paid attention to is the loophole when employees look for workarounds —— This is increasingly common in remote or mixed operating modes . Examples of workarounds include emailing confidential data to a personal account or copying information to for convenience USB. Organizations can respond to this threat in a number of ways , It depends on the way that best suits them . for example , They can communicate with IT cooperation , Add a new resource or file to Intranet, Or start other digital services , Make it easier for employees to work remotely . No matter how the company chooses to address workaround vulnerabilities , It is important that it also monitors this activity and continues to educate employees about threats .
Conclusion
The universality of the connectivity system is one of the reasons why the remote model is so successful . however , Companies cannot invest in these technologies without considering the resulting safety impact . In addition to the above considerations , Companies also need to educate employees about digital best practices , And provide additional guidance to stop potential hackers and protect their business .
As more and more companies use remote models as a standard , Security issues related to connecting various IOT devices and smart products will continue to increase . When this happens , Organizations will have to determine their acceptable tolerance between keeping the business running and minimizing friction , At the same time, the company will not face a lot of security problems . This is a cost-benefit decision that every organization now needs to consider .
边栏推荐
猜你喜欢

What are the functions and applications of Mogg test controller

ZigBee模块通信协议的树形拓扑组网结构
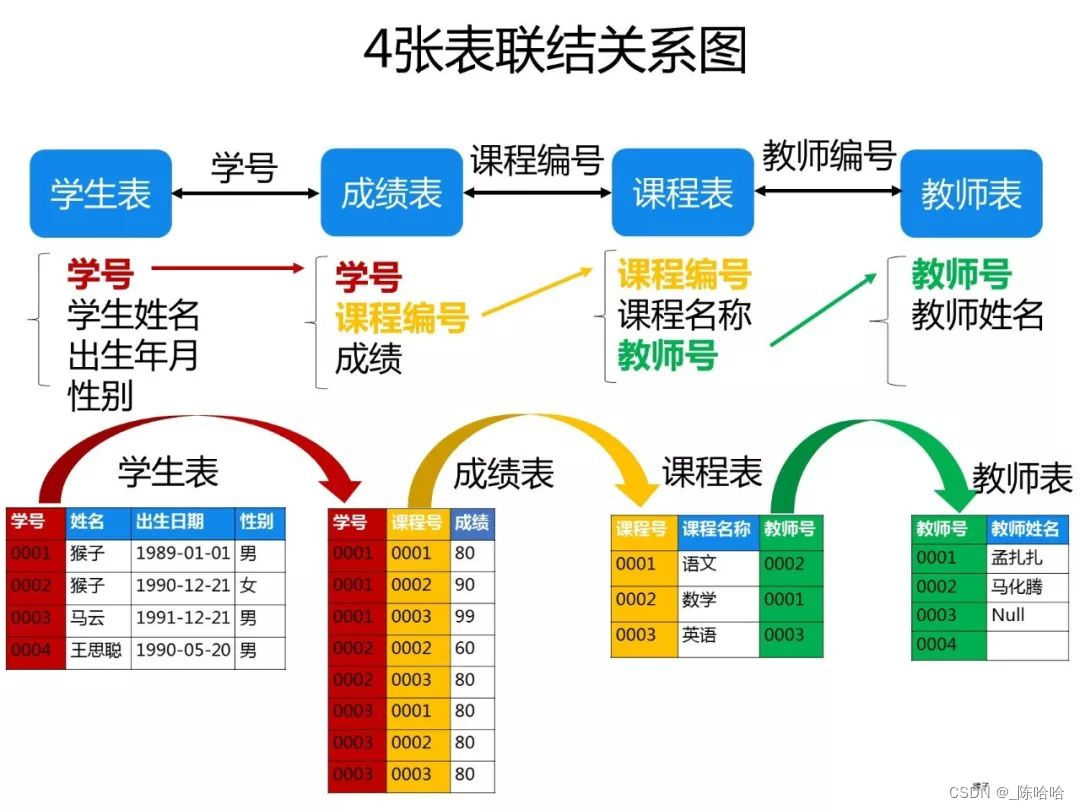
Drink at night, 50 classic SQL questions, really fragrant~

关于马格齿轮泵的应用领域都有哪些?总结一下

Servlet 的初次部署

Correct opening method of RPC | understand go native net/rpc package

图表背后的秘密 | 技术指标讲解:唐奇安通道
Datagrip 2022, datagrip function

ESP8266_ Access to the core suite of Baidu Internet of things and use mqtt protocol for communication

After four years of outsourcing, it was abandoned
随机推荐
[torch]: parallel training and can dynamically set the batch size of the first GPU
Introduction to steamvr
数据库设计及范式讲解
MySQL permission management and backup
Beginning simple blog emlog theme template V3
RSA signature issues
WordPress website backup
What are the application fields of MAG gear pump? To sum up
New feature of ES6 - arrow function
No more! The entry byte beat for a week and ran decisively.
EMG执行器的作用和功能有哪些
With determination to forge ahead, JASMINER continues to deepen its brand strength
BCGControlBar库专业版,完整记录的MFC扩展类
【Objective-C】动态创建控件
Q1's revenue exceeded Wall Street's expectations, and the value of Zhiwen group is waiting to return
启动jar
Use of JMeter (simulating high concurrency)
MySQL 权限管理和备份
基于SSM+Vue+OSS的“依伴汉服”商城设计与开发(含源码+论文+ppt+数据库)
Tree topology networking structure of ZigBee module communication protocol