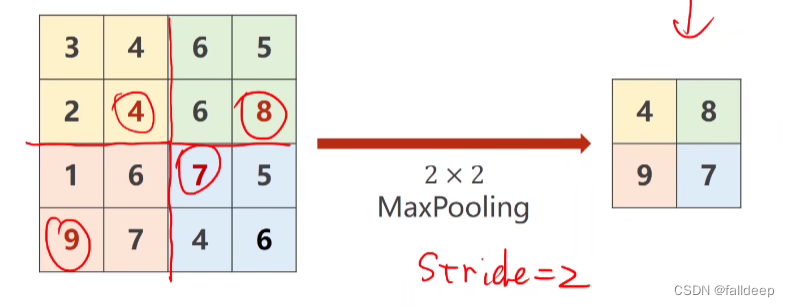
当前位置:网站首页>Hash these knowledge you should also know
Hash these knowledge you should also know
2022-08-05 07:11:00 【code and thinking】
What is Hash
Hash is translated as hash in Chinese, and it is also called "hash". It is a general term for a class of functions.The input of any length (also known as pre-map, pre-image) is transformed into a fixed-length output through a hashing algorithm, and the output is the hash value.This transformation is a compressed map, that is, the space of the hash value is usually much smaller than the space of the input, and different inputs may hash to the same output, so it is impossible to determine the unique input value from the hash value.
Simply put, it is a function that compresses a message of any length into a message digest of a fixed length.
The role of Hash
hash is a function of compressing a message of any length into a message digest of a certain length.Equivalent to the fingerprint of a file.
Because the file is unlimited, the number of bits that can be represented by the mapped string is limited.Therefore, there may be different keys corresponding to the same Hash value.That's the possibility of a collision.
Hash storage data
The essence of the hash table is actually an array, and the key-value pair Entry is usually stored in the hash table.
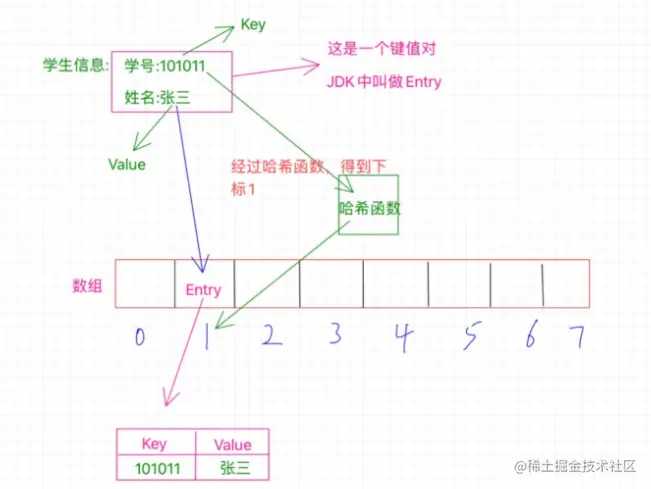
The student number here is a key, and the hash table uses the hash function to calculate a value based on the key value. This value is the subscript value, which is used to determine where in the hash table the entry should be stored.
Hash collision solution
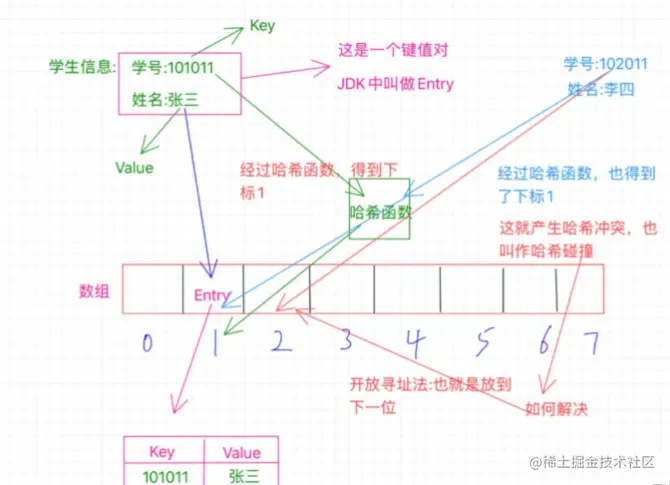
The solution to hash collision is open addressing method and zipper method.
Open addressing means that if the current array position 1 is occupied, it will be placed in the next position 2. If 2 is also occupied, it will continue to search until an empty position is found.
The zipper method uses a linked list. At this time, position 1 does not only store the Entry. At this time, the Entry also saves an additional next pointer, pointing to another position outside the array, and arranges Li Si in theHere, the next pointer in Zhang San's Entry points to Li Si's location, which is the stored memory address of this location.If there is still a conflict, put the conflicting Entry in a new position, and then Li Si's Entry points to it, thus forming a linked list.
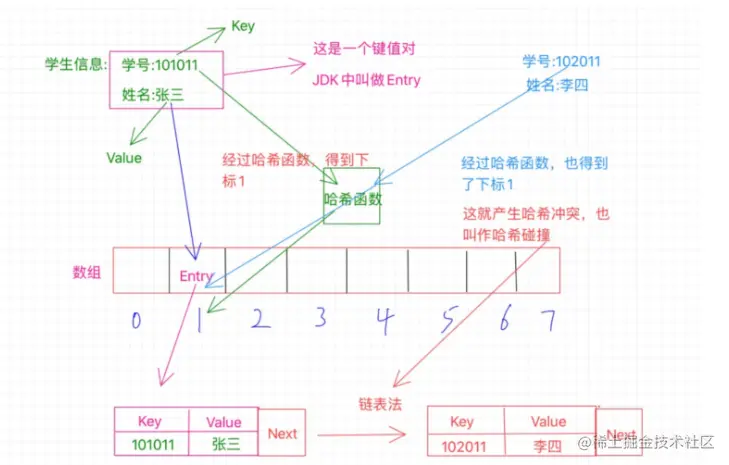
Open addressing and zipping both try to find the next empty location to store the conflicting value.
Practical uses of Hash
Unique verification
- In java, it is used to judge whether the variables are equal and put into hashCode(), and together generate an integer that will not collide as much as possible
Data integrity verification:
- After downloading a file from the Internet, you can confirm whether the downloaded file is damaged by comparing the Hash value (such as MD5, SHA1) of the file.If the Hash value of the downloaded file is consistent with the Hash value given by the file provider, it proves that the downloaded file is intact
Quick Find:
- HashMap
Privacy Protection:
- When important data must be exposed, someone can choose to expose its Hash value (such as MD5) to ensure the security of the original data.For example, when logging in to a website, you can only save the hash value of the user's password. In each login verification, you only need to compare the hash value of the entered password with the hash value saved in the database. The website does not need to knowUser's password.In this way, when the website data is stolen, the user will not endanger the security of other websites because of the theft of their own password.
Author: Arrom
Link: https://juejin.cn/post/7127862424887099406
Source: Rare Earth Nuggets
边栏推荐
- 在STM32中使用printf函数
- Takeda Fiscal 2022 First Quarter Results Strong; On Track to Achieve Full-Year Management Guidance
- 软件测试必问面试题(附答案和解析)
- Hong Kong International Jewellery Show and Hong Kong International Diamond, Gem and Pearl Show kick off
- Promise (3) async/await
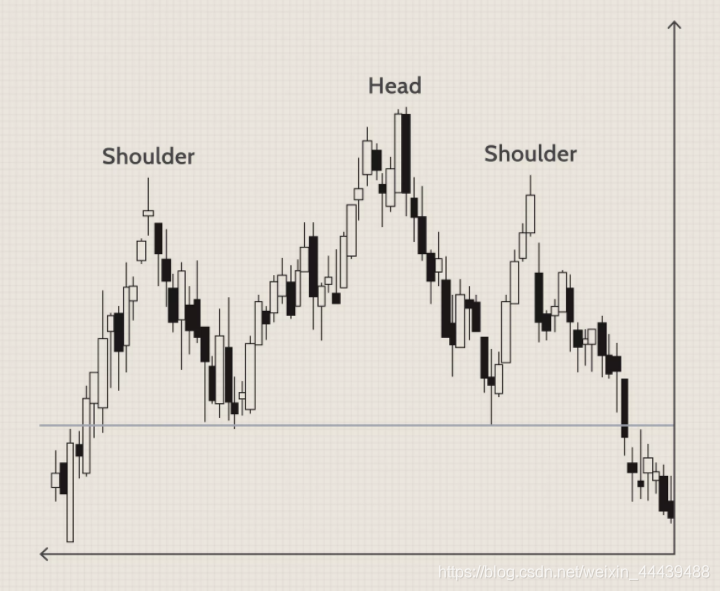
- 技术分析模式(十)头肩图案
- MySQL:连接查询 | 内连接,外连接
- Source code analysis of Nacos configuration service (full)
- Kioxia and Aerospike Collaborate to Improve Database Application Performance
- PCI Pharma Services宣布斥资数百万美元扩建英国制造设施,以满足市场对支持肿瘤治疗的全球高效药制造服务日益增长的需求
猜你喜欢
随机推荐
DevExpress中针对指定列进行百分比转换
性能提升400倍丨外汇掉期估值计算优化案例
MySQL:连接查询 | 内连接,外连接
typescript67-索引查询类型
17-VMware Horizon 2203 虚拟桌面-Win10 手动桌面池浮动(十七)
浮点数基础知识
Shiny04---DT和进度条在shiny中的应用
(JLK105D)中山爆款LED恒流电源芯片方案
【Dynamic type detection Objective-C】
typescript60-泛型工具类型(readonly)
IO进程线程->进程间的通信->day7
2022最强版应届生软件测试面试攻略
一天学会从抓包到接口测试,通过智慧物业项目深度解析
技术分析模式(十)头肩图案
Mysql master-slave delay reasons and solutions
专用机终端安装软件后报IP冲突
It turns out that Maya Arnold can also render high-quality works!Awesome Tips
怎么样避免线上内存泄漏
[instancetype type Objective-C]
(四)旋转物体检测数据roLabelImg转DOTA格式