当前位置:网站首页>Sunflower teaches you how to prevent denial of service attacks?
Sunflower teaches you how to prevent denial of service attacks?
2022-07-27 06:46:00 【Business information collection】
With the development of network technology and network application , Network vulnerabilities are becoming more and more important . Denial of service is easy to implement 、 It's hard to guard against 、 It is difficult to track and become one of the most difficult network problems , It has brought great harm to the network society . meanwhile , Denial of service will also be one of the important means of information war in the future .
But if there are certain vulnerabilities in denial of service , Under attack , Then it will cause unpredictable losses to the enterprise , How to prevent denial of service attacks , Become the key . Next, sunflower comes to popularize what is denial of service attack ? How to prevent it !

Denial of service (DoS):DoS yes Denial of Service For short , Denial of service , Any interference with the service , Making its availability reduced or lost is called denial of service . The simple understanding is , The normal service request required by the user cannot be processed by the system . For example, a computer system crashes or its bandwidth is exhausted or its hard disk is filled , As a result, it cannot provide normal services , It constitutes a denial of service .
Denial of service attacks : cause DoS Is known as DoS attack , Its purpose is to make the computer or network unable to provide normal services .
On the Internet , Sunflower told you that denial of service attacks can be roughly divided into three categories : Take advantage of defects in software implementation ; Exploit loopholes in the Protocol ; Use resources to suppress . And in blockchain , Denial of service attacks disrupt 、 suspend 、 Freeze the execution of normal contracts , Even the logic of the contract itself cannot work properly .

So what should we do in the face of denial of Service Vulnerability attacks ? Sunflowers to help you !
1、 It is recommended to make some configuration adjustments on the router of this network segment , These adjustments include limitations Syn Traffic and number of half open packets .
2、 To prevent SYN Data segment attack , We should set the corresponding kernel parameters for the system , Make the system force the timeout Syn Request connection packet reset , At the same time, by shortening the timeout constant and lengthening the waiting queue, the system can quickly deal with invalid Syn Request packet .
3、 Do the necessary work in front of the router TCP Intercept , Make only complete TCP The data packets of three handshakes can enter the network segment , This can effectively protect the servers in this network segment from such attacks .
4、 For information flooding attacks , We should turn off services that may generate infinite sequences to prevent such attacks . For example, we can reject all on the server side ICMP package , Or on the router of this network segment ICMP Packets are limited in bandwidth , Control it within a certain range .
I don't know after reading the above , Do you know how to prevent denial of service attacks ? It doesn't matter if you don't understand , Then take a look at sunflowers ! Sunflower will answer your questions .
边栏推荐
- Socket programming II: using Select
- 反射器中getattr,hasattr,delattr,setattr的使用
- Constraints and design of database
- 关于在Gazebo中给无人机添加相机(摄像头)之后,无人机无法起飞
- Ftx.us launched stock and ETF trading services to make trading more transparent
- Basic knowledge of English: modifying sentence elements - Part 1
- 关于testng相关标签的使用
- 面试常问的问题总结【呕心沥血熬了一个晚上总结的】
- DNS fault analysis optimization
- Shell -- operation of variables
猜你喜欢

To improve the baby's allergy, take yiminshu. Azg and aibeca love la Beijia work together to protect the growth of Chinese babies
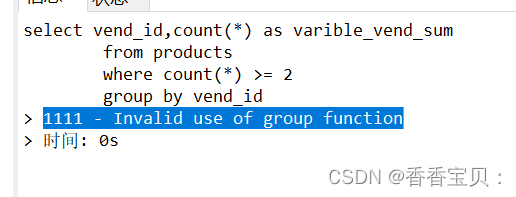
According to SQL, you must know and learn SQL (MySQL)

Seven sorting details
![Summary of frequently asked questions in the interview [summarized after painstaking work all night]](/img/70/90543c23326305590242716b989643.png)
Summary of frequently asked questions in the interview [summarized after painstaking work all night]

iptables防火墙
Pruning - quantification - turn to onnx Chinese series tutorials

Use of getattr, hasattr, delattr and setattr in reflectors

FTX Foundation funded 15million to help covid-19 clinical trials, which will affect global public health

logging日志的封装

win10 添加虚拟网卡,配置op路由
随机推荐
Raid explanation and configuration
According to SQL, you must know and learn SQL (MySQL)
ESXI虚拟机启动,模块“MonitorLoop”打开电源失败
磁盘管理与文件系统
PSI|CSI和ROC|AUC和KS -备忘录
Decorator functions and the use of class decorators
项目实训经历1
1. Install redis in CentOS 7
项目实训经历2
shell--变量的运算
Redis fast learning
PXE efficient batch network installation
win10 添加虚拟网卡,配置op路由
shell--条件语句(if语句、case语句)
Redis快速学习
shell--自定义变量与赋值
DNS domain name resolution service
Open source WebGIS related knowledge
Shell script backup MySQL database
rsync远程同步