当前位置:网站首页>access control
access control
2022-07-27 20:29:00 【Leisurely summer】
“ jurisdiction ” The word "security" appears frequently in the field of security .“ jurisdiction ” It's actually a kind of “ Ability ”. Reasonable allocation of authority , It has always been the core issue in security design . but “ jurisdiction ” The Chinese meaning of the word is too broad , Therefore, in this section “ Access control ” Instead of . In the field of Internet security , In especial Web In the field of security ,“ Access control ” All the problems can be attributed to “ Access control ” The problem of , This description is also more accurate .
stay Linux In the file system , Divide permissions into “ read ”、“ Write ”、“ perform ” Three abilities . Users may have “ read ” Authority , But there is no “ Write ” Authority .
stay Web Application , According to the different visiting objects , Common access control can be divided into “ be based on URL Access control ” and “ Data based access control ”.
Generally speaking ,“ be based on URL Access control ” Is the most common . To achieve a simple “ be based on URL Access control ”, Based on Java Of Web Application , You can add a filter Realization .
// Get access function
String url = request.getRequestPath();
// Verify authority
User user = request.getSession.get("user");
// Verify whether the user has access to the target url
boolean permit = PrivilegeManager.permit(user,url);
if(permit){
chain.doFilter(request,response);
}else{
// Unauthorized prompt
}1、 Vertical permissions ( Function permissions )
be based on URL Vulnerability and protection of access control .
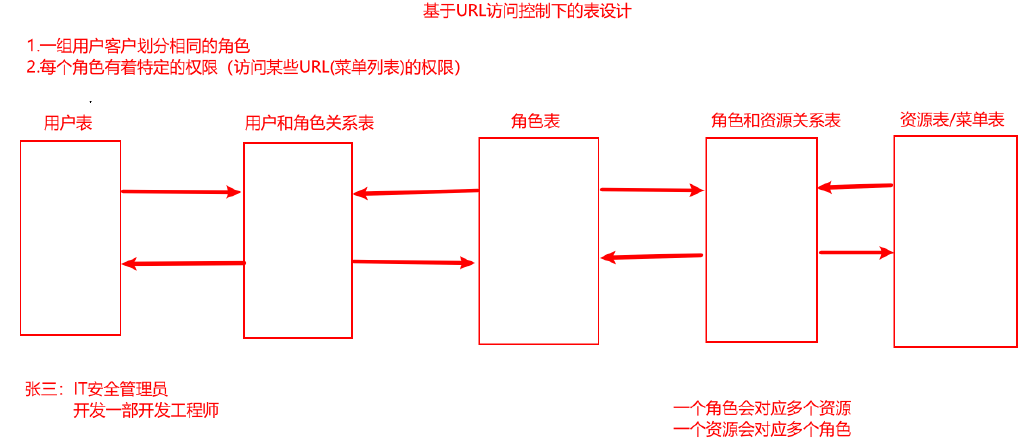
Access control is actually to establish the corresponding relationship between users and permissions , Now a widely used method , Namely “ Role-based access control (Role-Based Access Control)”, abbreviation RBAC, The final manifestation is what a user can access URL.

RBAC Different roles will be defined in the system in advance , Different roles have different permissions , A role is actually a collection of permissions . All users of the system will be assigned different roles , A user may have multiple roles , There are high and low points between the characters ( Authority level ). When the system validates permissions , Just verify the user's role , Then you can authorize according to the permissions the role has .
for example : In a forum , Yes admin、 Ordinary users 、 Anonymous users have three roles ,admin Have deleted 、 edit 、 The authority of the top post , Ordinary users have the right to comment and browse Posts , Anonymous users can only browse Posts . So far Shiro,Spring Security Based on RBAC The mature framework of the model deals with the problem of functional authority management and authentication .
Vertical permission is also called function permission
Examples of vulnerabilities in vertical permissions :
Web The application does not do permission control on the server , Just hide some of the pages in the front menu display . here , Malicious users can guess other management pages URL, You can access or control data or pages owned by other roles , To achieve the purpose of ultra vires operation , It may make ordinary users have administrator rights .
Vertical privilege vulnerability refers to Web The application does not do permission control , Or just do permission control on the menu , As long as other users guess the malicious page URL, You can access or control data or pages owned by other roles , To achieve the purpose of authority promotion .
Solution :
For any URL, Every time a user visits , Whether the user has access to this URL Authority . It is recommended to use a mature authority solution framework , such as Spring Security.
2、 Horizontal authority ( Data access )
Data based access control
Users Zhang San and Li Si in the same department have Access clue management Authority , But Zhang San can only operate Zhang San's Clues , Li Si can only manipulate Li Si's Clues
user A And the user B May belong to the same role RoleX, But users A And the user B Each has some private data , Under normal circumstances , Users can only access their own private data , for example : You have the function of deleting emails ( Operating authority ), But you can only delete your own email , Don't delete others' emails by mistake ( Data access ). But in RBAC Under the model , The system only validates users A Belong to role or not RoleX, Instead of judging users A Access only to users B The data of DataB, At this time, unauthorized access may occur .
This kind of problem , be called 『 Horizontal authority management issues 』, It can also be called 『 Data based access control 』: Compared with vertical permission management , Horizontal permission problems occur in the same role , The system only verifies the role that can access the data , There is no subdivision of subsets of data , Therefore, there is a lack of correspondence between users and data levels . For data access control , It is closely combined with business , At present, there is no unified data level permission management framework , Generally, specific problems should be solved .
Data permission is to control the visible range of access data , The form of expression is : When a user has operation permission , It does not mean that you have permission to view or manage all data . Generally, row permissions and column permissions
- Line authority : Restrict user access to certain rows , for example : Only to someone 、 Access the data of a department ; It can also be limited according to the range of data , for example : Restrict users' access to data according to the size of the contract
- Column permissions : Restrict user access to certain columns , for example : A summary of some content can be consulted , But the details are only VIP Users can check
Vulnerability cases of horizontal permissions :
Web The application accepts the user's request , When modifying a piece of data , Without judging whether the current user can access this record ( Judge who the data belongs to ), As a result, malicious users can modify data that does not belong to them . for example : /api/v1/blog?blogId=xxx [DELETE] This is to delete blog content url, When the user changes blogId when , If the backend does not verify whether the owner of the blog is the current user , You can delete other people's blog content .
Solution :
According to the user's ID Do a good job in data level permission control , For example CRUD Operation for session authentication , And verify the authority of the object record verification data accessed by the user , Prevent modification ID The way of ultra vires to view others' private information ( By business scenario ).
Access control is closely related to business requirements , It is not a simple safety problem . Therefore, when solving such problems or designing permission control schemes , Pay attention to business opinions . Last , No matter which access control method you choose , When designing the scheme, it should meet “ The principle of minimum authority ”, This is the golden rule of privilege management .
边栏推荐
- Data warehouse construction - DWD floor
- Redis queue, RDB learning
- Clickhouse 实现 MaterializedPostgreSQL
- Unity2d dynamic cartoon script (animation demonstration II for the chapter of Tiger Bridge)
- greedy
- 2019年中国智能机市场:华为拿下近4成份额,稳坐国内第一
- Redis Hash 结构命令
- MediaTek releases Helio g80, a mid-range game phone chip
- Pytorch multiplication and broadcasting mechanism
- 最新获得淘宝app商品详情原数据 的API
猜你喜欢

Anfulai embedded weekly report no. 275: 2022.07.18--2022.07.24

学习Blender必备的12款动画插件,来了解一下
2022年,软件测试还能学吗?别学了,软件测试岗位饱和了...

Mlx90640 infrared thermal imager temperature sensor module development notes (VII)

PC Museum (3) MITs Altair 8800

Illustration leetcode - 592. Fraction addition and subtraction (difficulty: medium)

办公自动化解决方案——DocuWare Cloud 将应用程序和流程迁移到云端的完整的解决方案

Pyqt5 rapid development and practice 4.3 qlabel and 4.4 text box controls

antdv: Each record in table should have a unique `key` prop,or set `rowKey` to an unique primary key

JS实现视频录制-以Cesium为例
随机推荐
盘点下互联网大厂的实习薪资:有了它,你也可以进厂
C # network application programming, experiment 2: IP address translation and domain name resolution exercises
Pytorch multiplication and broadcasting mechanism
Under the epidemic, I left my job for a year, and my income increased 10 times
Membership card head assembly usage document
C语言--数组
In 2019, the global semiconductor market revenue was $418.3 billion, a year-on-year decrease of 11.9%
Two years after its release, the price increased by $100, and the reverse growth of meta Quest 2
ECU software and hardware architecture
JS array method foreach and map comparison
图解LeetCode——剑指 Offer II 115. 重建序列(难度:中等)
速卖通:按关键字搜索商品 API
Mongodb learning notes: bson structure analysis
Huawei's mobile phone shipments exceed Apple's, ranking second in the world, but it faces a large amount of inventory that needs to be cleaned up
十年测试老鸟聊聊移动端兼容性测试
JS jump to the page and refresh (jump to this page)
Standing on the shoulders of giants to learn, jd.com's popular architect growth manual was launched
[C # network application programming] Experiment 3: process management exercise
LED high precision scale scheme specification
MongoDB 学习笔记: BSON 结构分析