当前位置:网站首页>Can JDBC based on openjdk connect to MySQL?
Can JDBC based on openjdk connect to MySQL?
2022-07-01 00:35:00 【hncscwc】
be familiar with ranger We should know ,ranger The server stores the policy information of service authentication in mysql in .
In the use of oracle jdk In the process of , There has been no problem ,ranger Can correctly from mysql Read and store data . However, when switching to openjdk after , There is ranger Startup cannot connect to mysql The phenomenon of , The following error messages can be seen from the log :
SQLException: SQL state: 08S01 com.mysql.cj.jdbc.exceptions.CommunicationsException: Communications link failure Through some source code analysis and online search of similar error information , The final positioning is :openjdk 1.8.0_291 Start , It is disabled by default tls1.0 and 1.1 edition , Lead to jdbc And mysql The connection to could not be established correctly , To report a mistake :

detailed release Poke it here :https://www.java.com/en/download/helprelease_changes.html
contrast oracle jdk Version of ,jdbc Connecting There is no manual designation useSSL=false When , The connection is still established using tls The way , And by default 1.1 Version .

Use openjdk after , Because disabled tls1.1, Unable to send correctly client hello, Therefore, the connection cannot be established .
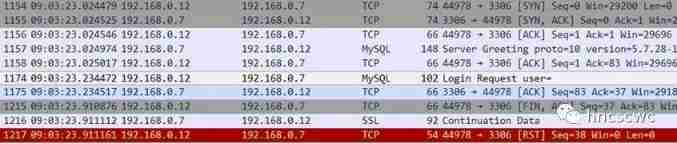
The solution is simple :
One way is to jdbc Specifies not to use ssl, That is, add parameters useSSL=false, This is a common solution .
But one thing , Because the connection interaction process is not encrypted , Safety cannot be guaranteed ( Usually mysql All on the intranet , Interact with platform services , The network environment itself is relatively safe , Therefore, there is not much risk without encryption )
Another way is to jdbc The use of tls1.2 Version establishes a connection with mysql Interact . That is, add parameters enabledTLSProtocols=TLSV1.2.
and mysql By default, it also supports tls1.0/1.1/1.2, So there will be no problem .
Appoint tls1.2 after , The packet capture for establishing connection interaction is shown in the following figure :

To sum up , An error log for connection exceptions , Most of the solutions that can be found on the Internet are the first , In fact, manually specify the use of tls1.2 It's OK, too , The conclusion of this article is to check the leak and fill the vacancy .
Okay , That's all for this article , Originality is not easy. , give the thumbs-up , Looking at , Sharing is the best support , thank you ~
in addition , Two menus are arranged under the official account

One is the addition of classified historical articles , The current is hdfs、yarn、ranger、rabbitmq series , More articles will follow ; Another is the addition of personal wechat , There are some mistakes in the article , What is lacking , You can add me to wechat communication , Of course, it is not limited to the problem of the article , Other technical issues can also be exchanged .

This article is from WeChat official account. - hncscwc(gh_383bc7486c1a).
If there is any infringement , Please contact the [email protected] Delete .
Participation of this paper “OSC Source creation plan ”, You are welcome to join us , share .
边栏推荐
- Docsify building a personal minimalist knowledge warehouse
- 剑指 Offer 19. 正则表达式匹配
- Ditto set global paste only text shortcuts
- The programmer's girlfriend gave me a fatigue driving test
- 【日常记录】——对BigDecimal除法运算时遇到的Bug
- LVM snapshot: backup based on LVM snapshot
- Mysql database query optimization
- What does it mean to open an account online? Is it safe to open an account online?
- On the application of cluster analysis in work
- Yboj mesh sequence [Lagrange interpolation]
猜你喜欢

Redis - cache penetration, cache breakdown, cache avalanche

2022-2028 global rampant travel industry research and trend analysis report

Deployment of mini version message queue based on redis6.0

The programmer's girlfriend gave me a fatigue driving test

Bridge emqx cloud data to AWS IOT through the public network

IFLYTEK active competition summary! (12)

Vulnerability discovery - App application vulnerability probe type utilization and repair
![[untitled]](/img/96/7f26614bbdcce71006e38ee34ab216.jpg)
[untitled]

2022-2028 global ultra high purity electrolytic iron powder industry research and trend analysis report

Why should VR panoramic shooting join us? Leverage resources to achieve win-win results
随机推荐
LVM snapshot: backup based on LVM snapshot
[untitled]
Don't worry about whether you can be a coder if you don't learn English well. Learn it first
第53章 从业务逻辑实现角度整体性理解程序
Combining online and offline, VR panorama is a good way to transform furniture online!
NE555波形发生器手把手教程之NE555内部结构(一)
left join左连接匹配数据为NULL时显示指定值
2022-2028 global single travel industry research and trend analysis report
Error 2059 when Navicat connects to MySQL
What is the fastest way to import data from HDFS to Clickhouse? Spark is imported through JDBC or HDFS
How to close an open DNS resolver
Unit test concept and purpose
SSM integration process (integration configuration, function module development, interface test)
What should I do without 50W bride price
Wordpress blog uses volcano engine veimagex for static resource CDN acceleration (free)
New trend of embedded software development: Devops
Redis - sentinel mode
Redis - how to understand publishing and subscribing
[DaVinci developer topic] -37- detail IRV: introduction to inter runnable variable + configuration
20220216 misc buuctf backdoor killing (d shield scanning) - clues in the packet (Base64 to image)