当前位置:网站首页>Redis - sentinel mode
Redis - sentinel mode
2022-07-01 00:05:00 【Salted fish_ Turn over】
List of articles
brief introduction
From the original master-slave replication , If the host goes down , You need to manually set a slave to a new master , But this manual configuration requires manual intervention , It takes time and manpower , And it will also cause service unavailability during the time of manual intervention , This is not a good solution for developers .Redis from 2.8 Sentinel mode began to appear .
Sentinel mode can monitor whether the host fails in the background , In case of failure, one of the slave machines will be selected as the host by voting .
Sentinel mode works
1、 By sending commands , Give Way Redis The server returns to monitor its running state , Including the master and slave servers .
2、 When the Sentinels detect master Downtime , Will automatically slave Switch to master, Then the other slave servers are informed through publish subscribe mode , Modify the configuration file , Let them switch hosts .
Sentinel mode principle
Redis The order of the sentry , And it is a special pattern , It will create a completely independent Redis Process of server , One sentry can monitor multiple servers , And there can be multiple sentinels , Each sentinel will send regularly PING Command to the server , And also get the response from the server within a certain period of time , After receiving the response, sentinel mode will determine that your current state is normal . If the host fails to respond to the request it sends within the specified time , Then the Sentry will make a preliminary judgment , The current host is offline , The rest of the Sentinels found that the host did not respond to the data within the specified time , Then the host will be judged once per second , It's really subjective , Then the host will be marked as offline , After the host computer is down , The sentinel will choose one of the suspended hosts as the new host by voting .
Configure sentinel mode
stay Linux Using the editor to write a file , The name of the document is sentinel.conf, Here we need to pay attention to , The name of the configuration file is fixed , Don't Scribble .
Establish different server configurations , Implement one master and two slaves mode , How to configure it can be viewed in my previous articles :https://blog.csdn.net/aaa123_456aaa/article/details/122932495?spm=1001.2014.3001.5502
We can check these services :
The core configuration of the sentry :sentinel monitor myredis 127.0.0.1 6379 1
And the numbers 1 Express : When a sentinel subjectively thinks the host is disconnected , It can be objectively considered that the host is faulty , Then start electing a new host .
# Sentinel service default port
port 26379
# Sentry mode default working directory
dir /tmp
# Property format :sentinel monitor Host name IP port 1 Back number 1 On behalf of the host is hung up ,Slave Vote who will be the new host
sentinel monitor myredis 127.0.0.1 6379 1
edit sentinel.conf
Activate the sentry :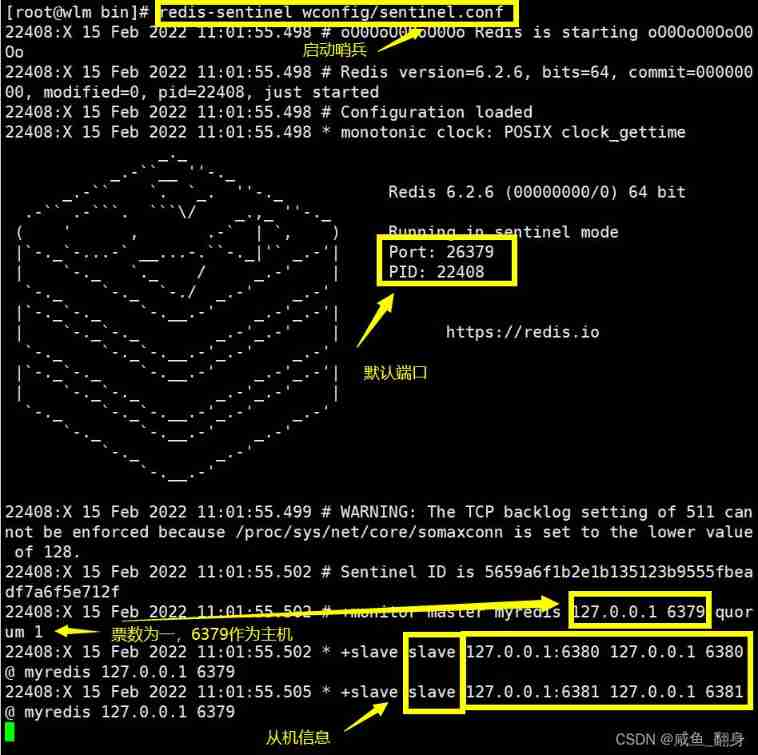
Test sentinel mode
Let's set a value on the host first , Then turn off the host , See if a new host will be created :
Once the host is shut down , We will find that the sentinel side will also change , That is, monitor the host changes :
We see the 6381, It is found that it is still a slave :
So there's no doubt about it , According to the principle of sentinel mode ,6380 Will become a host , So let's see 6380 You can see that it becomes a host :
Be careful :
If the host comes back , Then it will still become 6380 Slave of , This is the time 6380 Is already the boss .
The advantages and disadvantages of sentinel mode
advantage :
1、 The sentry cluster , Based on master-slave replication mode , All the advantages of master-slave replication , It all has .
2、 Master slave can switch , Faults can be transferred , The availability of the system is better .
3、 Sentry mode is an upgrade of master-slave mode , Manual to automatic , More robust
shortcoming :
1、Redis Not good for online expansion , Once the cluster capacity reaches the upper limit , Online expansion is very troublesome
2、 The configuration of sentinel mode is very troublesome , There are many configuration items in it
Full configuration of sentinel mode
Complete sentinel mode configuration file sentinel.conf
# Example sentinel.conf
# sentry sentinel The port on which the instance runs Default 26379
port 26379
# sentry sentinel Working directory of
dir /tmp
# sentry sentinel Monitored redis The master node ip port
# master-name You can name the master node by yourself Only letters A-z、 Numbers 0-9 、 These three characters ".-_" form .
# quorum When these quorum Number sentinel The sentry thought master Primary node lost connection Then at this time It is objectively believed that the primary node is disconnected
# sentinel monitor <master-name> <ip> <redis-port> <quorum>
sentinel monitor mymaster 127.0.0.1 6379 1
# When in Redis In the example, the requirepass foobared Authorization code So all connections Redis The client of the instance must provide the password
# Set up a sentry sentinel Password to connect master and slave Note that the same authentication password must be set for master slave
# sentinel auth-pass <master-name> <password>
sentinel auth-pass mymaster MySUPER--secret-0123passw0rd
# Specify how many milliseconds later The master node didn't answer the sentry sentinel here Sentinels subjectively think that the primary node is offline Default 30 second
# sentinel down-after-milliseconds <master-name> <milliseconds>
sentinel down-after-milliseconds mymaster 30000
# This configuration item specifies what is happening failover How many can there be at most during the primary / standby handover slave Simultaneously on the new master Conduct Sync ,
The smaller the number , complete failover The longer it takes ,
But if the number is bigger , That means the more Much of the slave because replication And is not available .
You can do this by setting this value to zero 1 To make sure there's only one at a time slave In a state where command requests cannot be processed .
# sentinel parallel-syncs <master-name> <numslaves>
sentinel parallel-syncs mymaster 1
# Timeout for failover failover-timeout It can be used in the following ways :
#1. The same sentinel To the same master two failover The time between .
#2. When one slave From a wrong one master Where the synchronized data starts to calculate the time . until slave Corrected to be correct master Where the data is synchronized .
#3. When you want to cancel an ongoing failover The time required .
#4. When doing failover when , Configure all slaves Point to the new master Maximum time required . however , Even after this timeout ,slaves It will still be correctly configured to point master, But it won't parallel-syncs Here comes the configured rule
# Default three minutes
# sentinel failover-timeout <master-name> <milliseconds>
sentinel failover-timeout mymaster 180000
# SCRIPTS EXECUTION
# Configure the scripts that need to be executed when an event occurs , The administrator can be notified by script , For example, when the system is not running normally, send an email to inform the relevant personnel .
# There are the following rules for the result of the script :
# If the script returns 1, Then the script will be executed again later , The number of repetitions currently defaults to 10
# If the script returns 2, Or 2 A higher return value , The script will not repeat .
# If the script is terminated during execution due to receiving a system interrupt , Then the same return value is 1 The same behavior when .
# The maximum execution time of a script is 60s, If I exceed that time , The script will be a SIGKILL Signal termination , And then re execute .
# Notification scripts : When sentinel When any warning level event occurs ( for instance redis Subjective failure and objective failure of examples, etc ), Will call this script ,
# At this point the script should be sent by email ,SMS Wait for the way to inform the system administrator about the abnormal operation of the system . When the script is called , Two parameters will be passed to the script ,
# One is the type of event ,
# One is the description of the event .
# If sentinel.conf The script path is configured in the configuration file , Then you have to make sure that the script exists in this path , And it's executable , otherwise sentinel Failed to start normally successfully .
# Notification script
# sentinel notification-script <master-name> <script-path>
sentinel notification-script mymaster /var/redis/notify.sh
# The client reconfigures the master node parameter script
# When one master because failover And when it changes , This script will be called , Notify related clients about master Information that the address has changed .
# The following parameters will be passed to the script when the script is called :
# <master-name> <role> <state> <from-ip> <from-port> <to-ip> <to-port>
# at present <state> Always “failover”,
# <role> yes “leader” perhaps “observer” One of them .
# Parameters from-ip, from-port, to-ip, to-port It's for the old master And the new master( I.e. old slave) communication
# This script should be generic , Can be called many times , It's not targeted .
# sentinel client-reconfig-script <master-name> <script-path>
sentinel client-reconfig-script mymaster /var/redis/reconfig.sh
边栏推荐
- Ditto set global paste only text shortcuts
- LVM snapshot: preparation of backup based on LVM snapshot
- Achieve secure data sharing among multiple parties and solve the problem of asymmetric information in Inclusive Finance
- Don't worry about whether you can be a coder if you don't learn English well. Learn it first
- shell 同时执行多任务下载视频
- Kubernetes ---- pod configuration container start command
- Inventory the six second level capabilities of Huawei cloud gaussdb (for redis)
- Bridge emqx cloud data to AWS IOT through the public network
- Software engineering best practices - project requirements analysis
- Which is better, server rental or hosting services in the United States?
猜你喜欢
![Cesiumjs 2022 ^ source code interpretation [6] - new architecture of modelempirical](/img/ce/519778cd731f814ad111d1e37abd10.png)
Cesiumjs 2022 ^ source code interpretation [6] - new architecture of modelempirical

Solution to the conflict between unique index and logical deletion

1. crawler's beautifulsoup parsing library & online parsing image verification code

Quick start of wechat applet -- project introduction

Wordpress blog uses volcano engine veimagex for static resource CDN acceleration (free)

HP notebook disable touchpad after mouse is inserted

Inventory the six second level capabilities of Huawei cloud gaussdb (for redis)

Solve arm_ release_ ver of this libmali is ‘g2p0-01eac0‘,rk_ so_ Ver is' 4 ', libgl1 mesa dev will not be installed, and there are unsatisfied dependencies
![[NLP] [textcnn] text classification](/img/bb/c8fd9f1ed458a88a17b8d5c70d9ce2.png)
[NLP] [textcnn] text classification

让企业数字化砸锅和IT主管背锅的软件供应链安全风险指北
随机推荐
In depth understanding of jetpack compose kernel: slottable system
HP notebook disable touchpad after mouse is inserted
在指南针上买基金安全吗?
CentOS 6.3 x64 PHP 5.2.6 扩展安装OpenSSL出错的解决方法
Prospects of world digitalization and machine intelligence in the next decade
Code de conduite pour la vente de fonds et la gestion de l'information
Arthas debugging problem determination Toolkit
Red hat will apply container load server on project atomic
Operation record of reinitialization instance of Dameng database
Fund clients and sales agencies
[designmode] factory pattern
Inventory the six second level capabilities of Huawei cloud gaussdb (for redis)
How do it outsourcing resident personnel position their pain points?
C /platform:anycpu32bitpererrored can only be used with /t:exe, /t:winexe and /t:appcontainerexe
Understand target detection in one article: r-cnn, fast r-cnn, fast r-cnn, Yolo, SSD "suggestions collection"
Solutions to errors in installing OpenSSL for CentOS 6.3 x64 PHP 5.2.6 extensions
Ditto set global paste only text shortcuts
基金銷售行為規範及信息管理
Repetition is the mother of skill
未来十年世界数字化与机器智能展望