当前位置:网站首页>Learning serialization and deserialization from unserialize3
Learning serialization and deserialization from unserialize3
2022-06-22 09:37:00 【Xia ~ Chen】

Today, I have just finished this topic to learn about serialization and deserialization
One 、 What is serialization and deserialization ?
First, let's think about the advantages of serialization ? Why serialization ?php What's good about serialization ?
First of all, we can know that this method must be for the convenience of data transmission , You can understand , Doing so is equivalent to storing an instantiated object on the computer disk for a long time , Whenever you call it, you can restore it to its original state . This is actually done to solve this problem : Because when PHP The file destroys the object after execution , Then if you need to call this object again next , That must be inconvenient , And you can't keep this object waiting for you , This way is to PHP Serialize it ( After serialization, the object has been converted into a string that can be transferred ), Deserialize when you need to use it ( The string is deserialized and converted to an object ), In this way PHP You can also call this object after the execution .
Serialization means converting an object into a string that can be transferred
Deserialization is to convert a string that can be transferred into an object
Let's take this problem as a simple example
First of all PHP Serialization converts an object to a string
<?php
class ctf
{
var $a = '123';
}
$class1 = new ctf; // Here is to create a new object
$class2 = serialize($class1); // Encapsulate this object in a string , Is to serialize it
print_r($class2);
?>Put it in PHP To get :
O:3:"ctf":1:{s:1:"a";s:3:"123";}Let's explain the meaning of the above code :
O:3:"ctf":1:{s:1:"a";s:3:"123";}
O Namely object The meaning of the object
3 The function names representing the objects are 3 A space
ctf It's the object name
1 There is also a variable in the object
s Representation string
Inside the curly braces 1 Represents the placeholder of the variable name
This is followed by the value of the variable name
3 Represents the placeholder of the variable value
Next, let's look at deserialization
<?php
class ctf
{
var $a = '123';
}
$class1 = new ctf;
$class2 = serialize($class1);
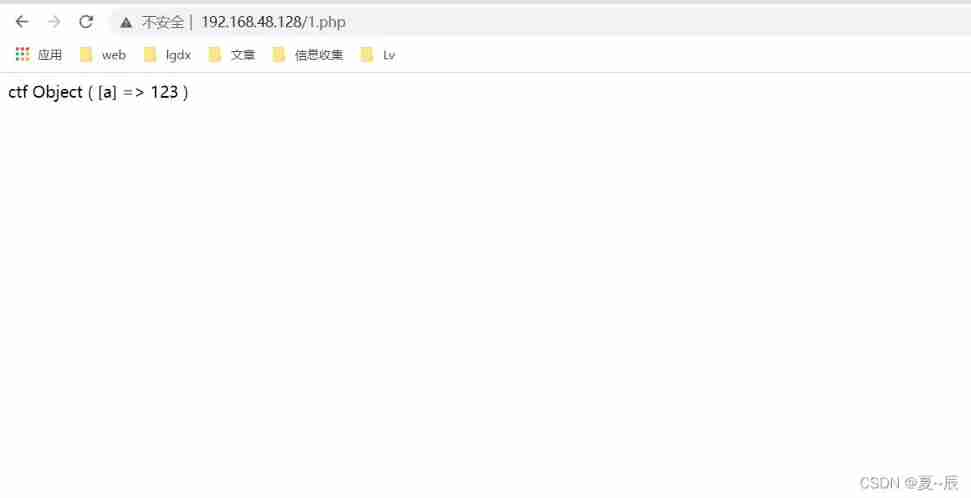
$class3=unserialize($class2);
print_r($class3);
?>This is the deserialization output
Two 、 So when will serialization and deserialization be used
Here are some magic functions , Usually we don't need to call... Manually , The general magic function is based on __ At the beginning , When you encounter these magic functions again, think about whether you can take advantage of serialization and deserialization vulnerabilities :
__constuct() When creating an object is called automatically
__destuct() amount to c++ The destructor in will eventually destroy the object , So when the object is destroyed Called
__toString() But when an object is used as a string, it is called
__sleep() Use... Before the object is serialized
__wakeup() Will be called immediately after serialization // Our problem is to use this to make use of serialization
Come back to this problem
class xctf{
public $flag = '111';
public function __wakeup(){
exit('bad requests');
}
?code=
Let's talk about it here serialize and unserialize
serialize() Function to check if there is a magic method in the class __sleep() I didn't expect that the function mentioned above was called before serialization, so it is necessary to check whether there is this magic function before serialization . If there is , This method will be called first , Then do the serialization operation , This feature can be used to clean up objects .
unserialize() Function to check if there is a magic method in the class __wakeup(), If there is , Will be called first __wakeup Method , Prepare resources needed for objects in advance
Here is _wakeup, It is obviously a deserialization vulnerability
Let's take a look at _wakeup Execution Vulnerability , After a string or object is serialized , If the attribute value is modified , that _wakeup Function will not be executed , So we can use this to bypass
Let's try to execute the code :( Need to make a little change )
<?php
class xctf
{
public $flag = '111';
}
$test1=new xctf;
$test2=serialize($test1);
print($test2);
?>Then get :
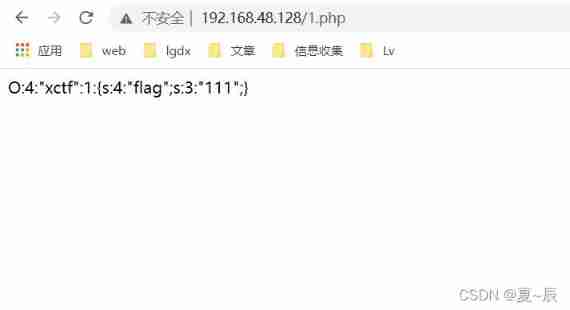
O:4:"xctf":1:{s:4:"flag";s:3:"111";}We will change the value attribute of this serialized string
O:4:"xctf":3:{s:4:"flag";s:3:"111";}
This is because after we change the property value of the function , Title Code deserialization failed and _wakeup The function fails
Then pass the reference to the topic :

Succeed in getting flag
cyberpeace{d523d340982d31b2e2eccc8f63462ff1}I suggest that you can set up a local environment to try to execute the serialization and deserialization code , I believe you will have a deeper understanding of this problem
Attached below is an article by a big man
CTF-WEB:PHP Deserialization - Black lacquer WhiteMoon - Blog Garden
边栏推荐
- Error in PHP installation of Pagoda: libcares so. 2: cannot open shared object file: No such file or directory
- Brush questions in C language | judge whether a certain year is only a leap year (12)
- Centos7安装PostgreSQL12
- FileZilla server prompts 550 could not open file for reading when downloading files (illustration)
- try/finally --return那些事
- Summary and future prospect of transfer learning | community essay solicitation
- Solutions to prompt non standard import in go language
- [ZOJ] P3228 Searching the String
- 钟珊珊:被爆锤后的工程师会起飞|OneFlow U
- Machine learning | nltk_ Data download error |nltk's stopwords corpus download error solution
猜你喜欢

锁-ReentrantLock

How C processes use non static methods

SQL编程task02作业-基础查询与排序

Langchao state-owned assets cloud: state-owned assets as a guide to help state-owned enterprises use data to enrich their wisdom in the cloud

支付-订单案例构建
![[学习笔记] 回滚莫队](/img/19/d374dd172b9609a3f57de50791b19e.png)
[学习笔记] 回滚莫队

Opencv daily function histogram correlation (3)

编译basalt时出现的报错

模糊查询和聚合函数

Debian10 LVM逻辑卷
随机推荐
day500:键盘行
循环队列超详细实现,小白秒懂
PAT甲级 - 1015 Reversible Primes (进制转换&素数判断)
Lifecycle of Servlet
Module usage of pytorch: linear model (incomplete)
Unicode字符/静态非静态的访问
[node] scaffolding server to complete token verification
C language brush question | temperature conversion (11)
如何将数据库中的值经过Servlet传到jsp页面通过EL表达式中显示出来?
==经典面试题
Debian10 创建用户、用户组、切换用户
Try/finally --return those things
Classic & Cases
[node] theory + practice enables you to win sessions and cookies
[Luogu] P1083 [NOIP2012 提高组] 借教室(差分)
Error in PHP installation of Pagoda: libcares so. 2: cannot open shared object file: No such file or directory
Value (address) transmission, see the name clearly, don't fall into the ditch
[hdu] P1466 计算直线的交点数
Process status summary
container_ of