当前位置:网站首页>Security dilemma of NFT liquidity agreement - Analysis of the hacked event of NFT loan agreement xcarnival
Security dilemma of NFT liquidity agreement - Analysis of the hacked event of NFT loan agreement xcarnival
2022-06-28 21:35:00 【SharkTeam】
6 month 24 Japan ,NFT Mortgage loan agreement XCarnival Being attacked by hackers , Hackers profit 3087 ETH, about 380 Thousands of dollars .
This is also NFT There are few serious attacks on liquidity protocols ,SharkTeam The technical analysis of this event was carried out for the first time , And summarizes the means of safety precautions , I hope that the follow-up projects can take warning , Build a security defense line for the blockchain industry .

One 、 Event analysis
The attacker's address :0xb7CBB4d43F1e08327A90B32A8417688C9D0B800a
Through Tornado Extracted 120 ETH Used as start-up funds for attacks :
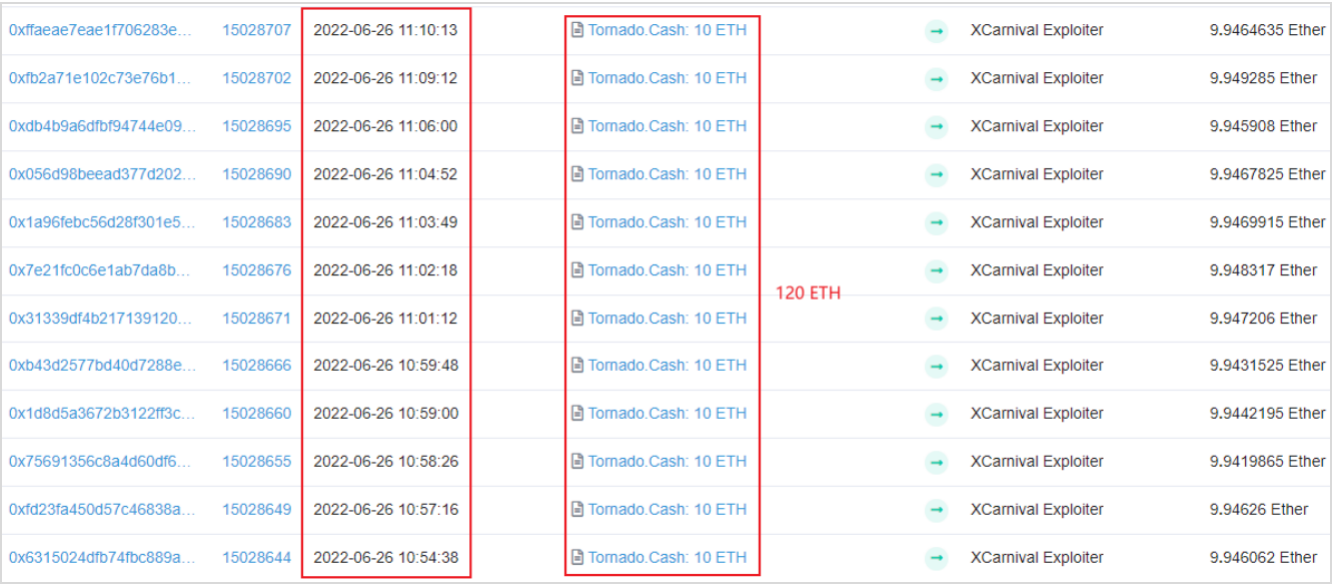
A series of transactions after the attacker's address obtains funds are as follows :

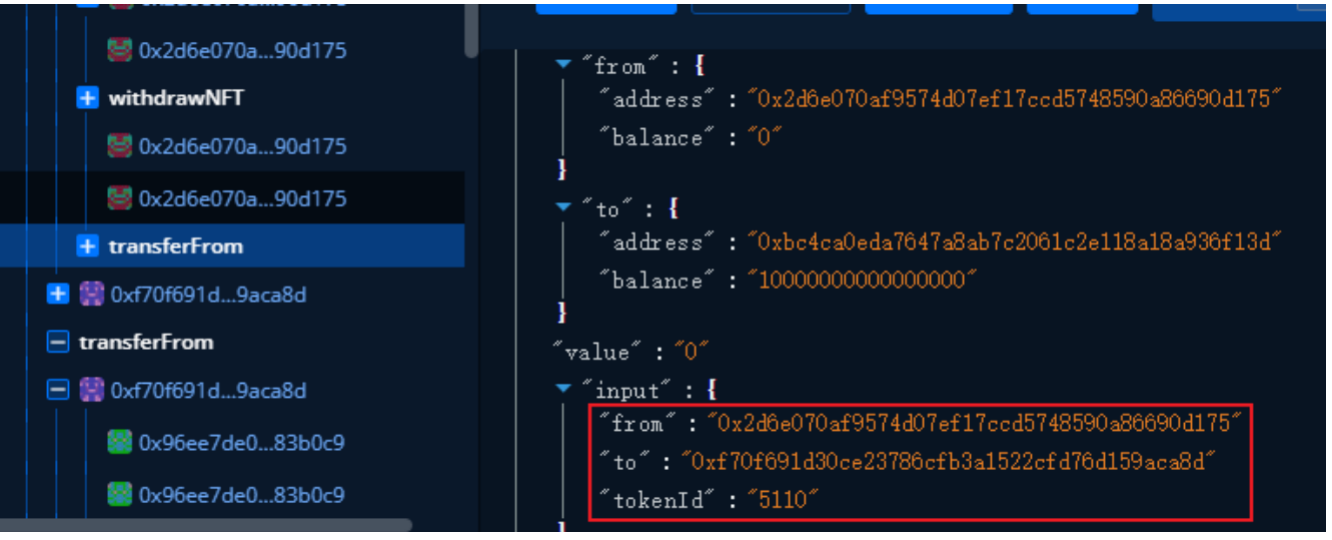
First , Through OpenSea Created a NFT,TokenID=5110

then , The attacker created the attack contract , The address is 0xf70f691d30ce23786cfb3a1522cfd76d159aca8d, Short for 0xf70f

The attacker will create NFT Move to attack contract

After completing the above steps , The attacker launched several attacks , Take the first attack transaction as an example ,
txHash: 0x422e7b0a449deba30bfe922b5c34282efbdbf860205ff04b14fd8129c5b91433
NFT The transfer record is as follows :

In the transaction NFT the 4 Secondary transfer , Each transfer uses a different contract address , And these contract addresses are created in the current transaction , Take the first transfer as an example , The execution process is as follows :
(1) Create a contract 0x2d6e070af9574d07ef17ccd5748590a86690d175, Short for 0x2d6e

And then NFT Transfer to the newly created contract 0x2d6e

(2) Call... Through a proxy contract XNFT Pledge and loan function in the contract pledgeAndBorrow, take NFT Pledge to XNFT In contract , The loan is 0.

XNFT The agency contract address is 0xb14B3b9682990ccC16F52eB04146C3ceAB01169A, Short for 0xb14b
NFT The implementation contract address is 0x39360AC1239a0b98Cb8076d4135d0F72B7fd9909, Short for 0x3936
pledgeAndBorrow Function as follows :
here , On receiving NFT Then the order is directly generated ,orderId=11,tokenId=5110,pledger Namely from, namely 0x2d6e

(3) Call the extraction function withdrawNFT, Pick up the order order=11 Medium NFT(tokenId=5110)
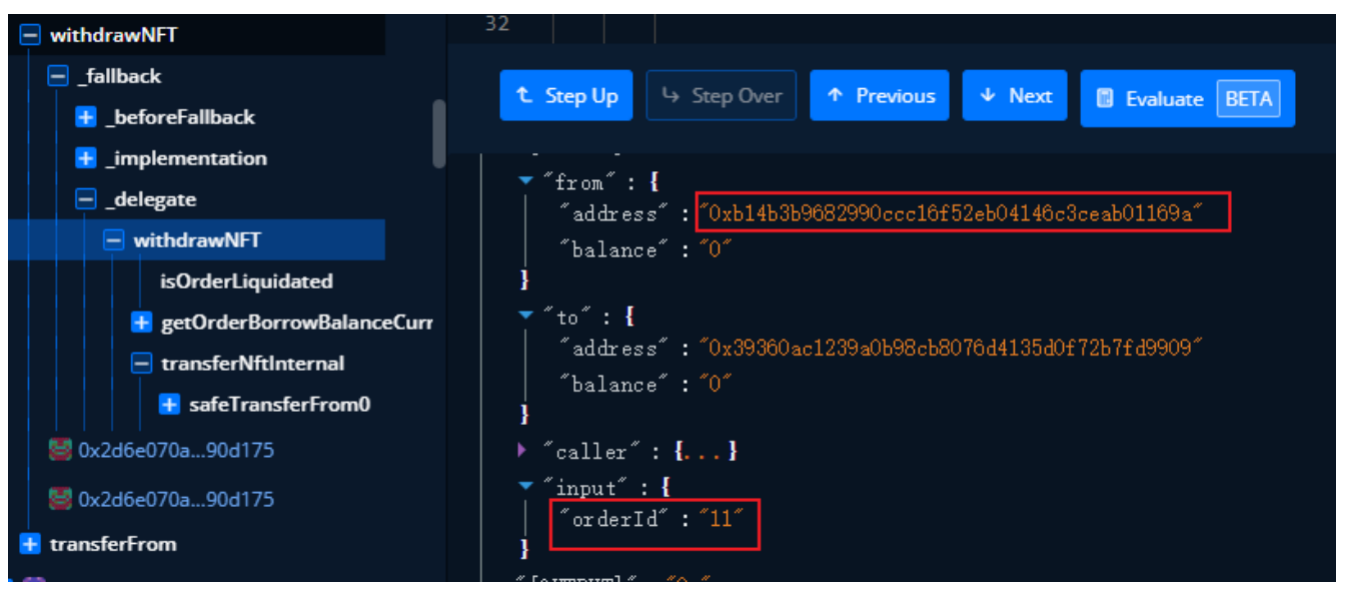
withdrawNFT Function as follows :

This function will 5110 NFT Extracted the address 0x2d6e
(4) take 5110 NFT By contract 0x2d6e Move to attack contract 0xf70f
Go through the above steps , The purpose of this transaction is to create 4 Order per order , Order's orderId Respectively 11,12,13 and 14, And the loan of the order is 0, among NFT Extracted (order.isWithdraw = true).
The attacker repeats the above transaction , Created a lot of orders , Then the attack's start function , attack . Take the first attack transaction as an example ,
txHash: 0xabfcfaf3620bbb2d41a3ffea6e31e93b9b5f61c061b9cfc5a53c74ebe890294d

XToken Agency contract :0xB38707E31C813f832ef71c70731ed80B45b85b2d, Short for 0xb387
XToken Realize the contract :0x5417da20aC8157Dd5c07230Cfc2b226fDCFc5663, Short for 0x5417
There are multiple transactions ETH Transfer record , from 0xb387, The contract created through the attack contract is transferred to the attack contract , Each transfer invokes XToken In the contract borrow function , Take the first transfer as an example , The function call is as follows :

borrow Function as follows :
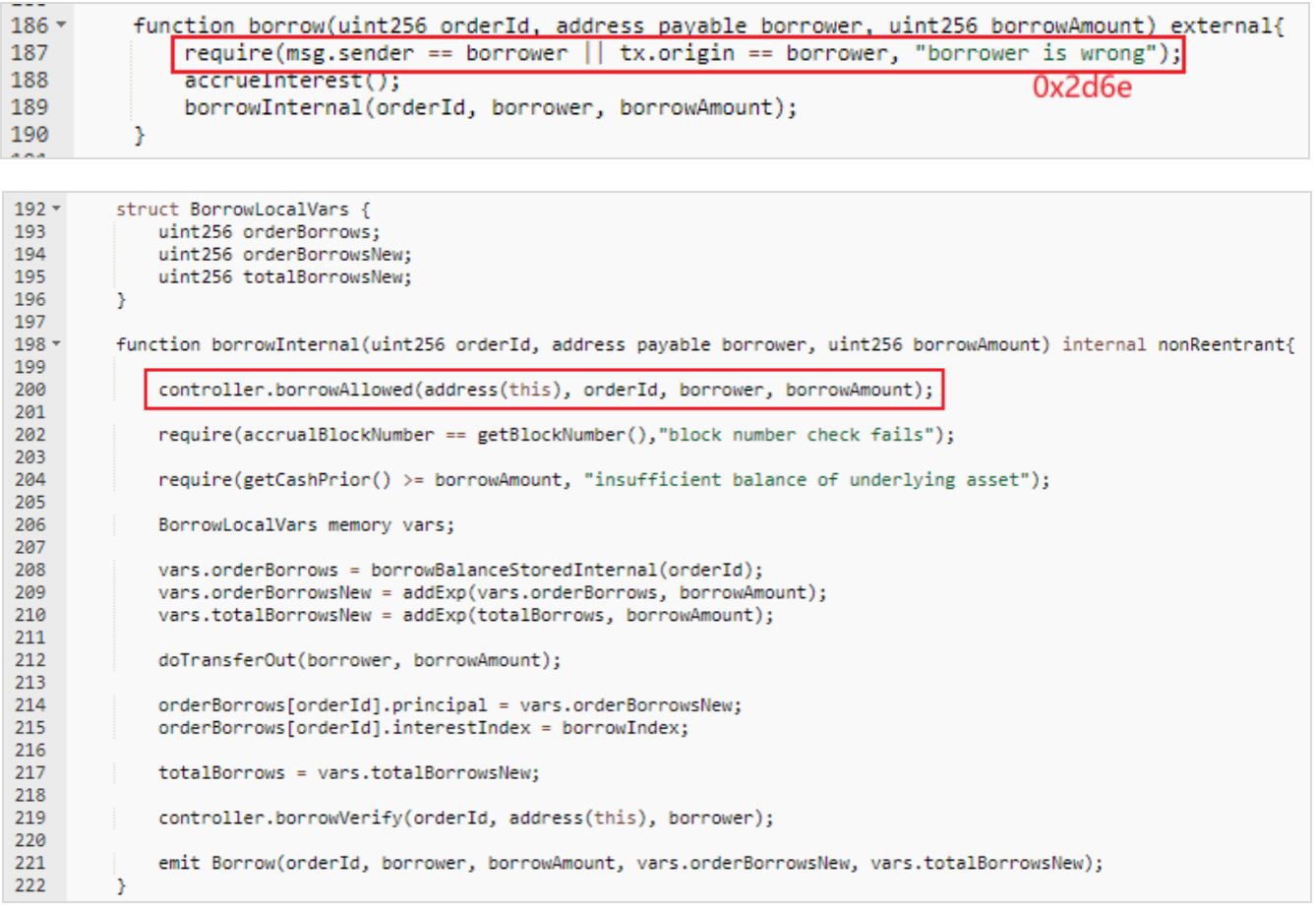
This is going to call controller In the contract borrowAllowed Function to verify , The function call and parameters are as follows :
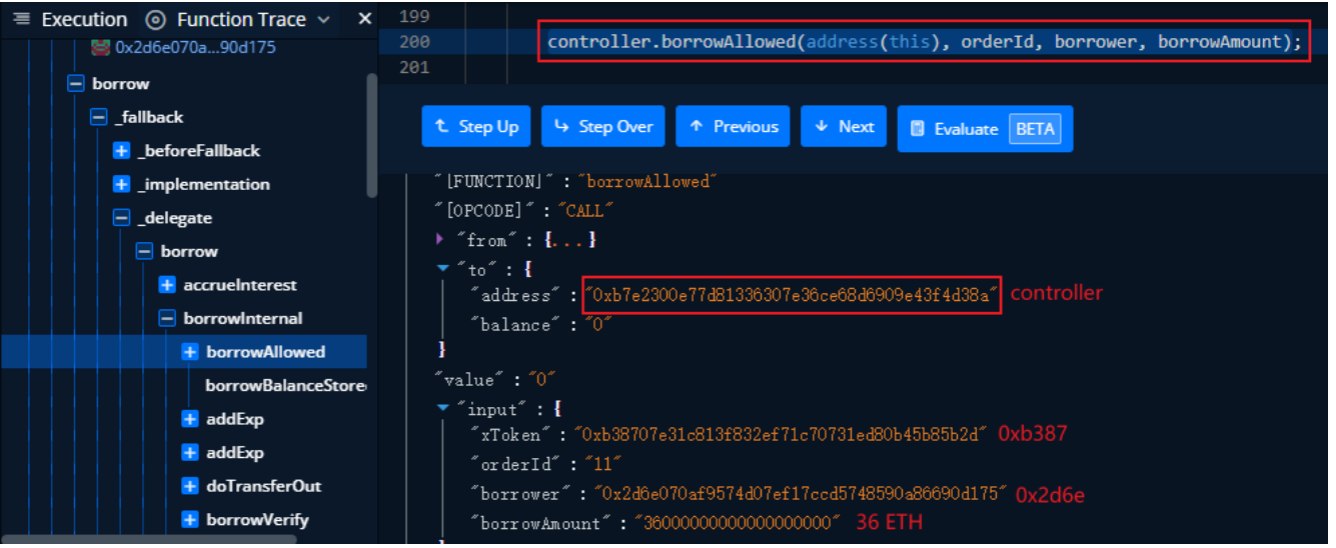
controller contract borrowAllowed Function as follows :

Here to order It's checked , But it only verifies the existence of the order 、 The address is correct and not cleared , There is no verification of the... In order NFT Whether it is extracted , Even though orderId=11 Of your order NFT Has been extracted ,order The verification of can still pass , therefore , The attacker has no actual collateral NFT In the case of 36 ETH.
The attacker exploited the vulnerability , Repeat attack , They successively stole a total of from the contract 3087 ETH, The total value is about 380 Thousands of dollars .
Two 、 Safety suggestion
The root cause of this security incident lies in the logical loopholes in the contract of the project party , The logic is not rigorous when borrowing money , Lack of verification of key logic , That is, whether the collateral has been withdrawn has not been detected .
as everyone knows ,NFT Ecology wants long-term sustainable development , There must be excellent NFT Liquidity program to provide liquidity market . In all kinds of NFT While the collection is constantly released , transaction 、 Loan, etc NFT Liquidity agreements are also the focus of the industry . But because NFT The price prediction machine of 、 Problems such as value endorsement have not been completely solved , So most NFT The volume of liquid projects is still relatively small . under these circumstances , Once a hacker attack occurs , It is often fatal to the project team , It will also greatly affect user confidence .
Therefore, we suggest that the project party design the project 、 The development and testing process should be rigorous , Try to avoid the absence of some core verification logic , Give hackers a chance . in addition , It is recommended to conduct multi-party and multi round audits , Minimize the high-risk loopholes in the contract .
3、 ... and 、 About us
SharkTeam Our vision is to fully protect Web3 The security of the world . The team members are located in Beijing 、 nanjing 、 Silicon valley , It is composed of experienced security professionals and senior researchers from all over the world , Proficient in the underlying theory of blockchain and smart contract , Provide services including smart contract audit 、 On chain analysis 、 Emergency response and other services . We have worked with key players in various fields of the blockchain ecosystem , Such as Huobi Global、OKX、polygon、Polkadot、imToken、ChainIDE And establish a long-term cooperative relationship .
Telegram:https://t.me/sharkteamorg
Twitter:https://twitter.com/sharkteamorg
Reddit:https://www.reddit.com/r/sharkteamorg
More blockchain security consulting and analysis , Click the link below to view
D Check | Chain risk verification https://m.chainaegis.com
边栏推荐
- 图神经网络也能用作CV骨干模型,华为诺亚ViG架构媲美CNN、Transformer
- LeetCode123. 买卖股票的最佳时机III
- Résumé de la stabilité
- Interface test process
- LeetCode117. 填充每个节点的下一个右侧节点指针_II
- 零基础自学SQL课程 | SQL中的日期函数大全
- Is it safe to open an account for stocks on mobile phones in 2022? Who can I ask?
- Apisik helps Middle East social software realize localized deployment
- Application practice | 1billion data second level correlation. Huolala's OLAP System Evolution Based on Apache Doris (with PPT download)
- 【激活函数】
猜你喜欢

Alibaba cloud MSE full link grayscale solution practice based on Apache apisik

Lumiprobe proteorange protein gel dye instructions

QJsonObject的使用示例

How do I download videos? Look at the super simple method!

接口用例设计

Recommend two high-quality Wallpaper software

力扣树的进一步应用

Ehcache configuration data, convenient for self checking

题解 Pie(POJ3122)超详细易懂的二分入门

User network model and QoE
随机推荐
LeetCode117. Populate the next right node pointer for each node_ II
Alist+raidrive gives the computer a complete 8billion GB hard disk drive
Mongodb - replica set and sharding
Apisik helps Middle East social software realize localized deployment
MySQL system error occurred 1067
Interface use case design
Openfire 3.8.2 cluster configuration
LeetCode每日一题——710. 黑名单中的随机数
To be a cross-border e-commerce, you must learn to use PRA software, free your hands and improve efficiency!
LeetCode56. 合并区间
postman简介与安装步骤
LeetCode986. 区间列表的交集
SqlTransaction
LeetCode226. Flip binary tree
PHP uses stack to solve maze problem
Résumé de la stabilité
[book club issue 13] packaging format of video files
Figure neural network can also be used as CV backbone model. Huawei Noah Vig architecture is comparable to CNN and transformer
Interface test process
Alibaba cloud MSE full link grayscale solution practice based on Apache apisik