当前位置:网站首页>Hash table, generic
Hash table, generic
2022-07-03 07:10:00 【L gold p】
1 Set
1.1 HashSet Use


2、 Hash table
2.1 summary
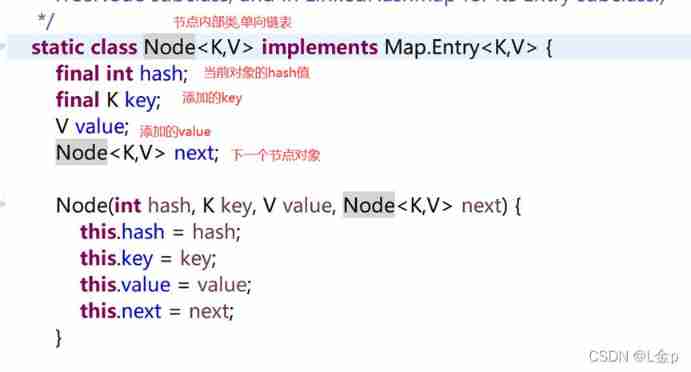
* Hash table structure It can be understood as The first node of the Federation is saved in the array , For preservation k and v Key operation
*
*hash Algorithm : Is a secure encryption mechanism , You can convert variable length data into fixed length data , And there is no guarantee of its uniqueness , Also known as hash conflict
*
* Again Java The middle finger is hashCode Method
*
* Generate multiple times for an object hash value , The value must be the same , Multiple objects can also generate the same hash value , It's called hash conflict
*
*k Do not repeat ,v Can be repeated
*
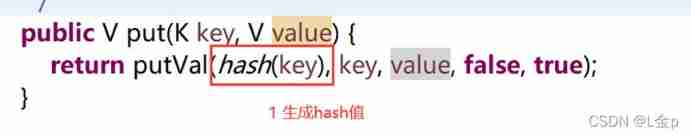
* Add process :
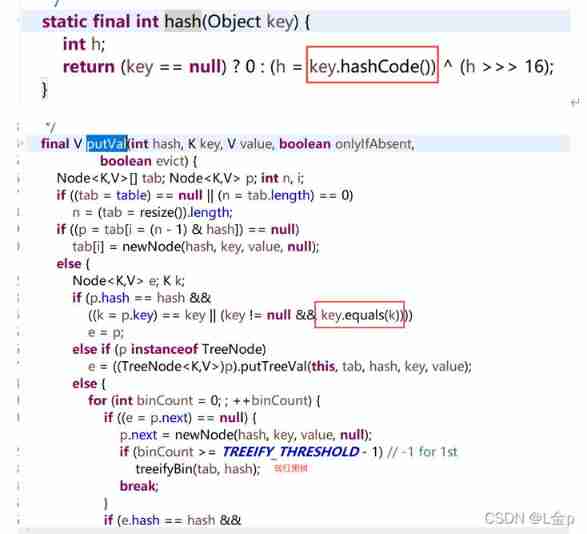
* 1 According to the... To be added key, Call his hashCode Method , Generate hash value
* 2 Through a certain algorithm , according to hash Value generates the subscript of the array
* 3 Judge whether the subscript is , Is there any data , If there is no data, save the key value pair mapping relationship to the array
* 4 If the subscript is in , There's data , Call key Of equals Method , Compare with all the corresponding data . If it's not equal , Then add it to the tail of the linked list
* 5 If the corresponding linked list , adopt equals When comparing methods , Found the same data , that key Not adding , however value Value will replace the original value value
* Through the addition process, we know , Will automatically call the hashCode and equals. So when saving custom types , Attention should be paid to method overrides
* Again 1.8 There is a new change in , In order to improve the query efficiency , The optimization of red black tree and capacity expansion is introduced
* Because the efficiency and performance of linked list re query are poor So if the number of linked lists in each array is greater than or equal to 7, The linked list will be converted into a red black tree
* The default initialization capacity of the array is 16
*
stay Java There is no concept of hash table , Wrap the hash table into HashMap and HashTable
2.2 HsahSet

When we use HashSet When , In fact, it is equal to using again HashMap
When adding data , Even though it's called HashSet Of add Method , But the essence is to call map Of put Method
Ps : stay map in ,put Is an add operation
and map in What needs to be saved is k and v The mapping relationship , So in set There is a variable in that holds value Value
So let's go on set When adding , It's just the operation map Medium key,value We no longer care about
3 Map
3.1 summary
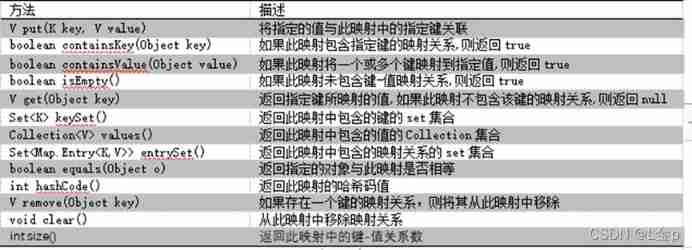
map Is chaotic , And save to yes k-v The mapping relationship between key value pairs of , among K Can't repeat ,V repeatable
HsahMap: At the bottom is a hash table
TreeMap : At the bottom are red and black trees It must be sorted according to certain rules
The mapping relationship : such as goods And the number of purchases Or statistics
3.2 Inheritance system

3.3 Usage method
3.4 HashMap
// establish map
HashMap map = new HashMap();
// add to K-V
map.put("A", "one");
map.put("B", "two");
map.put("C", "three");
map.put(65,100);
map.put('A', "2222");
// key repeat , Don't add ,value Replace
map.put("A", "2222");
// Support K and V all null, But it doesn't make sense
map.put(null,null);
// Number
System.out.println(map.size());
// get : according to K obtain V Value
System.out.println(map.get("A"));
// To determine whether or not to include a key
System.out.println(map.containsKey(65));
// To determine whether or not to include a value
System.out.println(map.containsValue("one"));
// according to key Delete The mapping relationship , Return the corresponding value value
map.remove(65);
// Get all value, And put it in the collection to return
Collection values = map.values();
for (Object object : values) {
System.out.println(object);
}
System.out.println("======");
// keySet : Get all key, Package to set Object and return
Set keys = map.keySet();
for (Object object : keys) {
System.out.println(object +":"+map.get(object));
}
// hold map Convert to set
// Entry Class , Save the K and V Two variables , hold map Medium k and v Convert to entry Class
// So we just need to save entry object , It's like saving k and v
Set set = map.entrySet();
for (Object object : set) {
// C=three
System.out.println(object);
// Convert to entry type
Entry entry = (Entry) object;
// obtain k and v
System.out.println(entry.getKey()+" : "+entry.getValue());
}
3.5 TreeMap
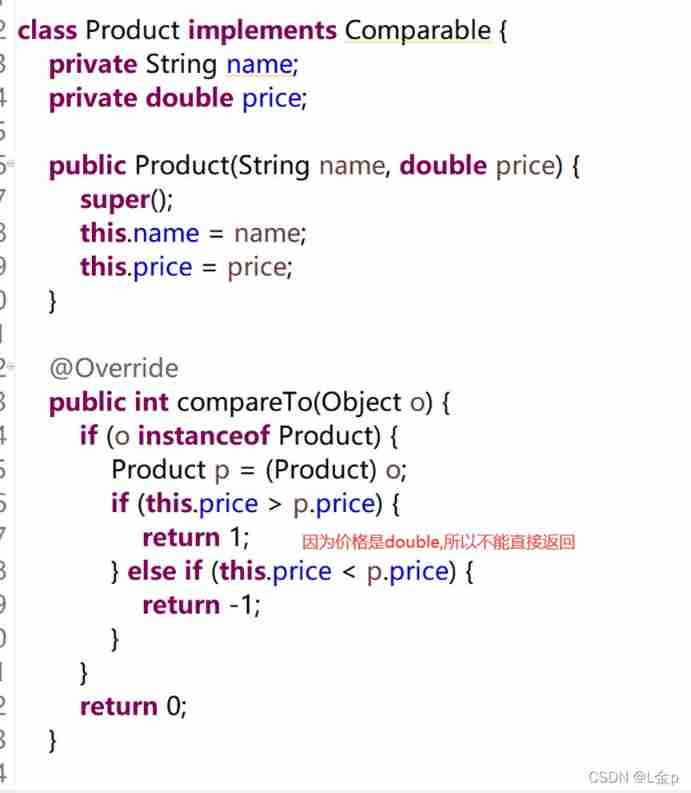

4 Generic
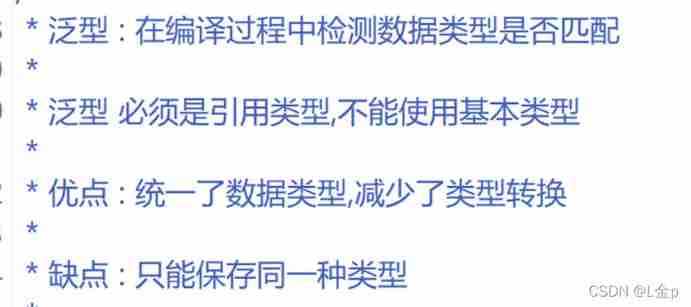
4.1 summary
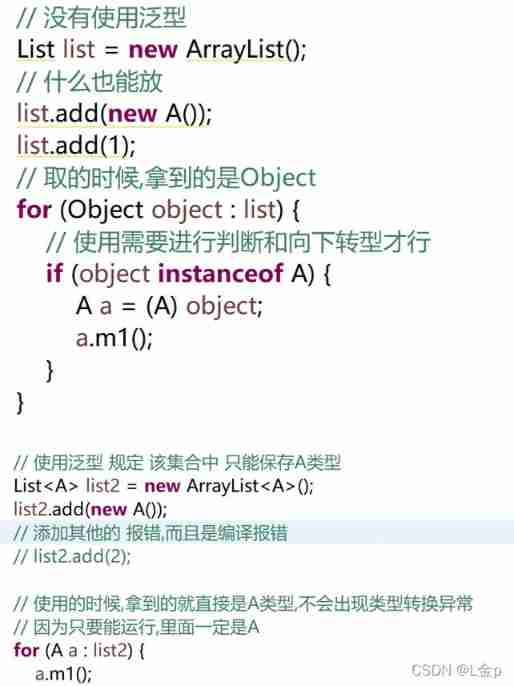
4.2 Usage mode
4..3 Be careful
Generic types cannot write basic types Only reference types can be written
If you want to save basic types , You need to write the corresponding packing class type

4.4 Custom generics


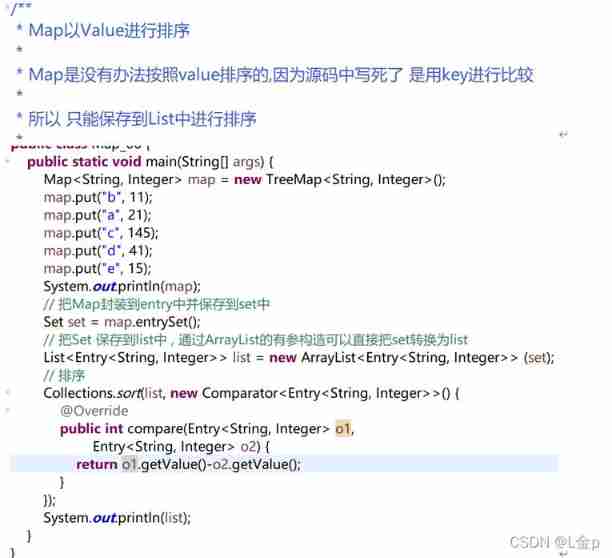
5、 Example
边栏推荐
- 【最詳細】最新最全Redis面試大全(50道)
- IC_ EDA_ All virtual machine (rich Edition): questasim, vivado, VCs, Verdi, DC, Pt, spyglass, icc2, synthesize, innovative, ic617, mmsim, process library
- [set theory] equivalence classes (concept of equivalence classes | examples of equivalence classes | properties of equivalence classes | quotient sets | examples of quotient sets)*
- Software testing assignment - day 3
- File links cannot be opened or downloaded in Google browser
- Common APIs
- The essence of interview
- 20220319
- Interface learning
- Advanced APL (realize group chat room)
猜你喜欢
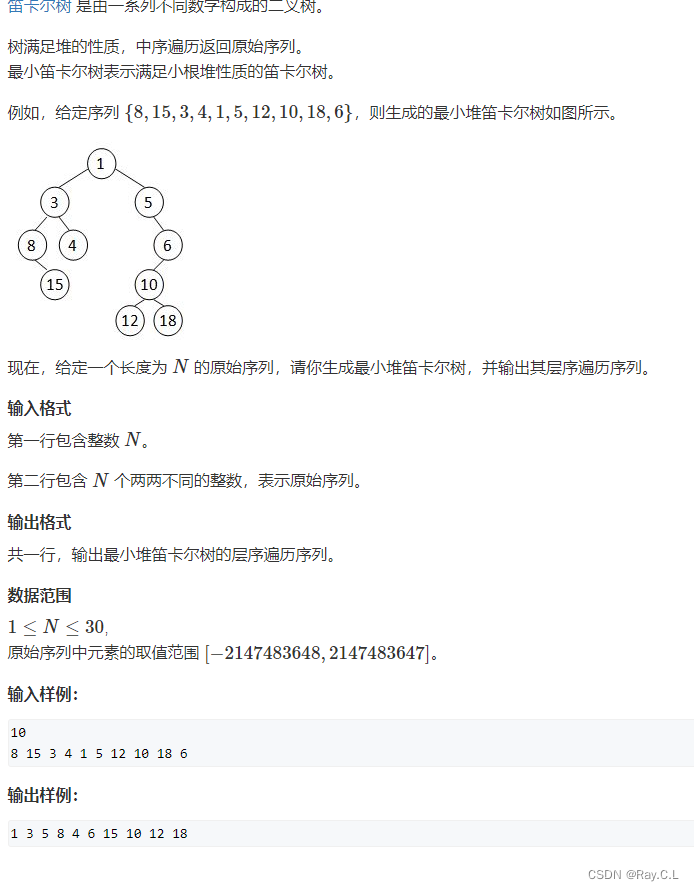
4279. Cartesian tree

How to specify the execution order for multiple global exception handling classes
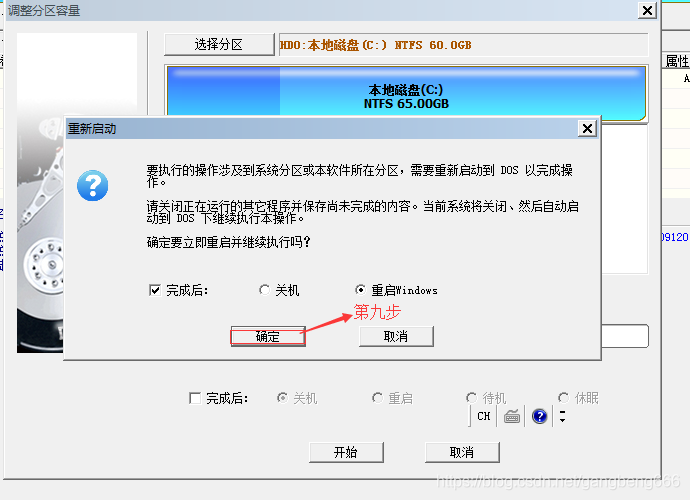
VMware virtual machine C disk expansion

Distributed transactions
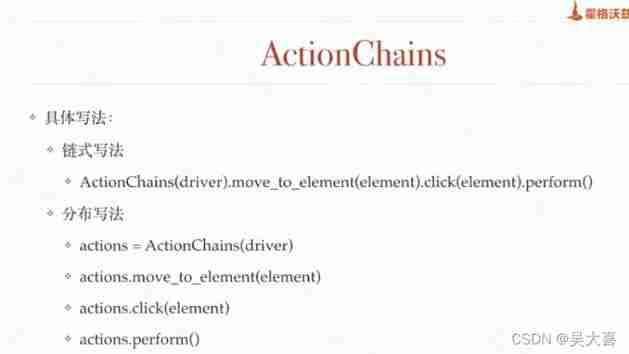
Selenium key knowledge explanation
![[Fiddler problem] solve the problem about Fiddler's packet capturing. After the mobile network is configured with an agent, it cannot access the Internet](/img/9d/42dfef67246740f0dba0c6d8f1b625.jpg)
[Fiddler problem] solve the problem about Fiddler's packet capturing. After the mobile network is configured with an agent, it cannot access the Internet

In depth analysis of reentrantlock fair lock and unfair lock source code implementation
Pits encountered in the use of El checkbox group
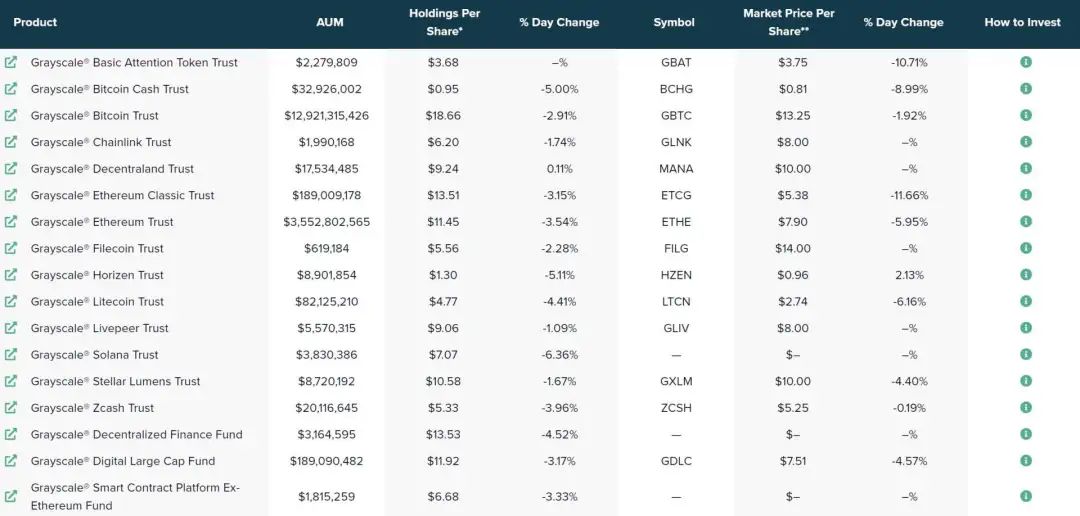
熊市里的大机构压力倍增,灰度、Tether、微策略等巨鲸会不会成为'巨雷'?

多个全局异常处理类,怎么规定执行顺序
随机推荐
What are the characteristics and functions of the scientific thinking mode of mechanical view and system view
Tool class static method calls @autowired injected service
File links cannot be opened or downloaded in Google browser
Shim and Polyfill in [concept collection]
[LeetCode]404. Sum of left leaves
Use the jvisualvm tool ----- tocmat to start JMX monitoring
20220319
Selenium key knowledge explanation
Search engine Bing Bing advanced search skills
Software testing learning - the next day
Laravel Web Framework
Winter vacation work of software engineering practice
La loi des 10 000 heures ne fait pas de vous un maître de programmation, mais au moins un bon point de départ
Error c2017: illegal escape sequence
How can the server set up multiple interfaces and install IIS? Tiantian gives you the answer!
In depth analysis of reentrantlock fair lock and unfair lock source code implementation
Win 10 find the port and close the port
3311. Longest arithmetic
Final, override, polymorphism, abstraction, interface
Advanced API (multithreading 02)