当前位置:网站首页>Didi off the shelf! Data security is national security
Didi off the shelf! Data security is national security
2022-07-03 15:04:00 【Huazhang it】
7 month 4 Japan ,“ Drops travel ” because App There is a serious problem of illegal collection and use of personal information , According to the national Internet Information Office 《 Network security law of the people's Republic of China 》 phase Off the shelf according to relevant regulations .
The announcement shows : To prevent National data security risks , Safeguarding national security , Protecting the public interest , basis 《 National Security Law of the people's Republic of China 》《 Network security law of the people's Republic of China 》, Cybersecurity review office according to 《 Network security review method 》, Yes “ Drops travel ” Implement network security review . In order to cooperate with the network security review work , Prevent risk expansion , During the review “ Drops travel ” Stop new user registration .

website :http://www.cac.gov.cn/2021-07/02/c_1626811521011934.htm
As report goes , This is a For the first time in China 《 National Security Law of the people's Republic of China 》 The case of .
7 month 5 Japan , The Network Security Review Office issued another announcement , Announce that it will be right “ Full of luck ”、“ Van gang ”、“BOSS Direct employment ” Start Network Security Review , without doubt , Didi is just a representative , The era of national attention to data security is finally about to begin .
6 month 10 Japan , The 29th meeting of the Standing Committee of the 13th National People's Congress voted to adopt the following 《 Data security law 》 Including many bills and two decisions .《 Data security law 》 The introduction of , To raise data security to the level of national security .
In the era of financial technology and digitalization , Data has become an important asset of a company , Even related to the survival of a company . The industry calls data assets “ crown jewels ”. Make a not necessarily appropriate analogy , Compare big data to nuclear fission , If we use this reaction properly , That will enable it to bring great energy to economic development , But if the control is improper , It will cause a huge crisis . Data security can be compared with big data “ nuclear power plant ” Provide key capabilities for controlled nuclear fission .
01
Threats and challenges faced by data assets
According to the Chinese Academy of information and communication in 2018 Published in 《 Big data security white paper 》, In the context of cloud computing and big data , Around the production of data 、 collection 、 Handle 、 Sharing and other aspects of the data life cycle , Internal leaks and external attacks 、 Management and technology 、 New technology risks and stock technology risks are intertwined , Data security threats can come from the big data platform itself 、 Data security 、 Three aspects of privacy protection .
The challenges of platform security are mainly manifested in the following aspects :
Hadoop And other open source tools lack overall security planning , Its own security mechanism has limitations .
Because big data platform services have multiple sources of data 、 diversification 、 Highly mobile , Traditional security mechanisms are difficult to meet the needs .
The large-scale distributed storage and computing mode of big data platform has doubled the difficulty of security configuration .
For the new network attack means facing big data platform ( Such as APT etc. ), There are obvious deficiencies in traditional safety monitoring technology .
Data threats and challenges are mainly manifested in the following aspects :
The number of data leakage events continues to grow , The harm caused is becoming more and more serious .
Due to the lack of monitoring means , The lack of integrity guarantee in data collection has become a new risk point that affects decision-making analysis .
The problem of confidentiality protection in data processing across traditional organizational boundaries is gradually emerging .
Due to the complexity of data flow path , It becomes extremely difficult to trace the source afterwards .
The challenges of personal privacy are mainly manifested in the following aspects :
Because the traditional privacy protection technology can come from many sources 、 Anonymous data can be restored by association analysis and deep mining of multiple types of data sets , So privacy protection may fail .
Traditional privacy protection technology ( Such as de identification 、 Anonymization Technology ) Non relational databases that are difficult to adapt to big data . In the field of financial technology , Because there are a large amount of personal sensitive information and transaction information in the system , Therefore, the supervision of network security and consumer data security are facing major challenges .
02
Data asset valuation
Want to protect data , The value of data assets should be judged accordingly . The industry has carried out relevant practices in recent years , It is found that there are three factors that affect the value of data assets ( See the picture 1): Data asset quality value 、 Application value of data assets and risk . The quality value of data assets is from the perspective of data consumers , Consider the authenticity of data assets 、 integrity 、 accuracy 、 Data cost 、 Security ; The application value of data assets considers scarcity 、 timeliness 、 Multidimensional 、 Scenario economy ; Risk mainly refers to legal restrictions and moral constraints , This has an impact on the value of data assets from quantitative change to qualitative change . The more restrictive regulations on data transactions , The higher the compliance and security costs of both parties to the transaction . Be able to formulate data security solutions that can effectively solve compliance security and efficiency problems , Can provide more value .
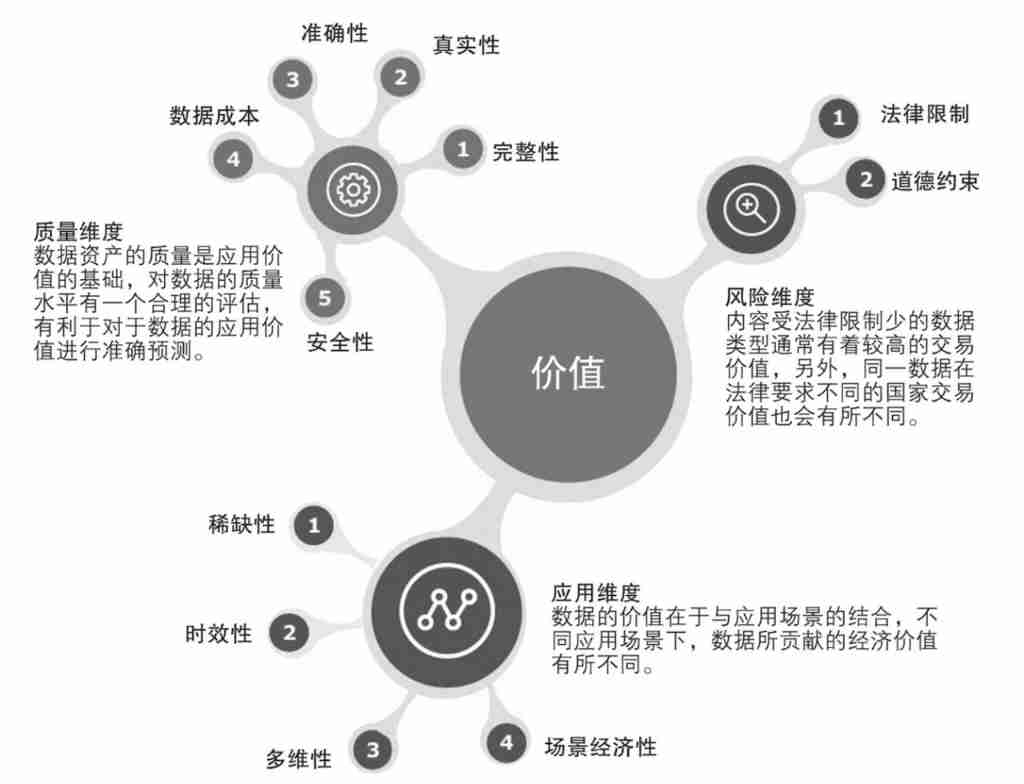
![]()
chart 1 Factors that affect the value of data assets
In terms of data asset evaluation , According to the practice of the industry in recent years , It can be found through the cost method 、 Income approach 、 Quantitative evaluation of data assets by market method . When evaluating data assets with cost method , It will be based on the cost of forming data assets . Although the cost and value of intangible assets are not strongly related and the cost is not necessarily complete , However, it is reasonable to use the cost method to evaluate the value of some data assets , For example, when trading and profitability are uncertain but trading is needed , The cost method can be used . When using the income method to evaluate data assets , Data assets, as operating assets, directly or indirectly generate income , The way to realize its value includes data analysis 、 data mining 、 Application development, etc . The income method is more authentic 、 It accurately reflects the value of data asset capitalization , It is easier to be accepted by all parties to the transaction . In market law , The profit-making form of data assets usually includes customer relationship management 、 Customer segmentation 、 Customer portrait 、 Personalized precision marketing 、 Improve the return on investment 、 Internal risk management . Income method and market method can be applied to the evaluation of data assets with good trading and profitability . When the three evaluation methods are applied to the value evaluation of data assets , Each has its own advantages and limitations , At present, there is no mature data asset value evaluation method .
03
How to understand data security
Data security is different from the traditional defense against network attacks , Under the framework of big data management , Focus on protecting data , hold “ Establish data security policies and standards , Legal compliance collection 、 Application data , Protect customer privacy according to law , Divide the data security level , Specify access and replication permissions , Monitor behaviors such as access and replication , Improve data security technology , Regularly audit data security ” As the main content of data security management . There is a complementary relationship between data security management and data governance , We can pass the goal 、 object 、 idea 、 technology 、 Initiating Department 、 Output content 、 Asset management and other dimensions are important to data security 、 Network security 、 Compare data governance ( See table 1).
surface 1 Data security 、 Network security 、 Data governance comparison table

![]()
04
Data security management reference framework
At present, the industry has two main ideas to solve data security management :
From the perspective of data security governance , First, clarify who is ultimately responsible for data security , Then under this responsibility framework, through data discovery 、 Data classification , Make it clear that DLP( Data leakage prevention ) As the leading technical management measures and audit measures . Under the centralized traditional technical framework dominated by financial institutions , This model is effective . However , Just as the effectiveness of Newton's classical physics is no longer so effective on a broader scale , In microenterprises 、 consumption credit 、 Medical insurance 、 Automobile insurance and other fields , transboundary 、 Multi data source computing across entities has become the main computing scenario .
In terms of regulations , It will also face strict requirements for privacy protection and personal data security in relevant laws and regulations such as network security and personal information protection , Traditional based on DLP Our solutions cannot meet new challenges . At this time , Some leading fintech companies have started in the verification and testing stage and even in the production stage , Use new data security solutions such as federated learning to deal with . The two are not mutually exclusive , It's complementary , What they have in common is “ Data centric ”, The difference is that data security governance is to look at data security from the perspective of an organization , New data security solutions such as federated learning are from the perspective of a cross-border business ecosystem .
Different scales 、 Institutions at different stages of development can flexibly use the above ideas to solve practical problems according to their actual situation .
Next , Let's talk about the reference framework related to data security .
Gartner It has also made great achievements in the field of data security , It has successively put forward reference frameworks such as data security governance and data centric security architecture , The data security governance architecture is said to be Gartner Analysts Marc Antoine Meunier stay “Gartner 2017 Safety and Risk Management Summit ” On behalf of Gartner released ,Marc Compare it to “ Eye of the storm ”, To describe Data security governance framework (DSGF) Important position and role in the field of data security .
DSGF The core architecture of is shown in the figure 2 Shown . Many people think that data security is just a technical problem , However, I want to classify data 、DLP、 It is impossible for tools such as digital rights management or digital encryption to completely solve the problem of data security . Data security is a complex problem , If not the data itself 、 Have a deep understanding of the context in which data is created and used and how it maps to the established governance framework , You can't understand what data security is , Not to mention data protection .
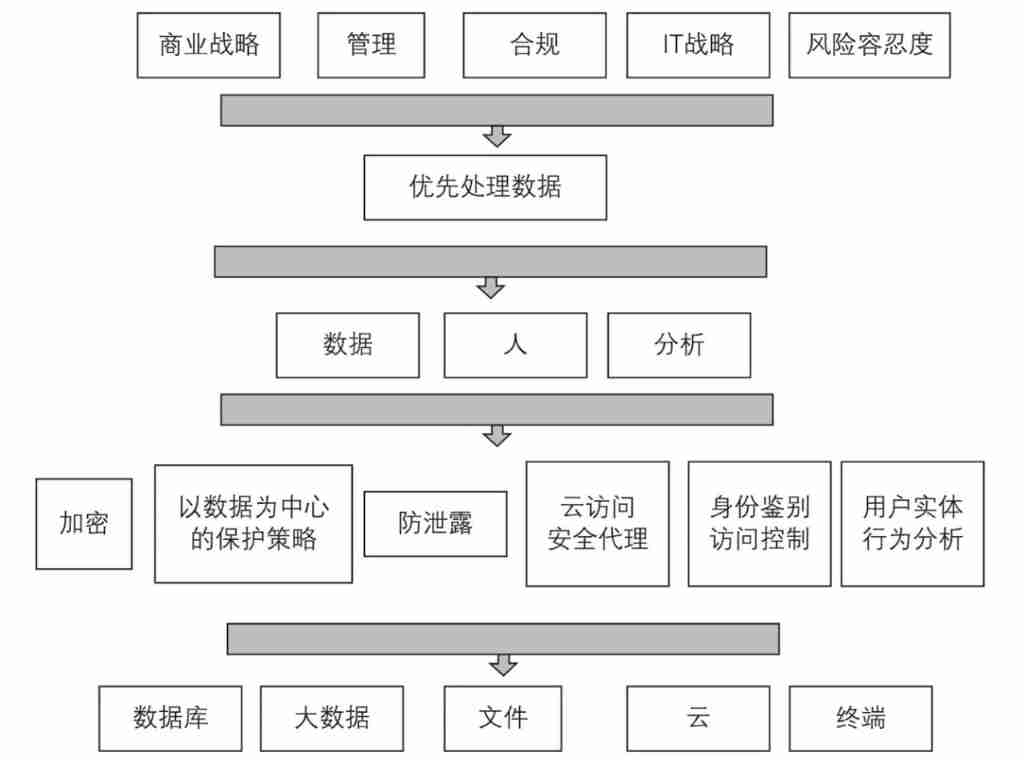
![]()
chart 2 DSGF Core architecture
DSGF It can help enterprises solve data security problems .DSGF Provides a data centric blueprint , These include : Identify and classify enterprise related structured and unstructured data sets , Define data security policies , Choose the technology to implement risk mitigation .
stay DSGF During landing , The high-level risk leader of the enterprise is the main person in charge , Its main responsibilities are as follows : One is Must determine the organization's response to data security events 、 Business strategy and risk tolerance of the regulatory environment , And identify and classify data assets according to business risks ; Two is Further consider and clarify the priority of enterprise technology investment , In order to realize the DSGF Derived goals ; The third is Need to make full use of data , Provide data-driven intelligence for management ; Fourth, data security must include other aspects besides traditional data security technology .
The other aspects mentioned above include the following .
Key technical aspects : Identity and access management (IAM) The program should help understand the user context and track the key components of data access , Especially in response to compromised credentials .IAM It provides a structured way for managers to access systems and data 、 A coherent approach . and UEBA The solution adopts a method based on behavior analysis to build users and entities ( host 、 Applications 、 Network traffic and database ) Standard configuration files and behavior standards . Activities that do not meet these standards will be considered suspicious , Thus, malicious insiders and external attackers can be found .
Intention : In terms of data protection , Enterprises must be able to try to reveal the intentions of users and attackers , To better identify and distinguish which are legitimate data security events , What are the cases of negligence or abuse .
priority : By adopting automation and intelligent advice , Use DSGF Priority should be given to using a continuous adaptive risk and trust assessment system to select appropriate security policy rules and functions , To ensure that the risks of key businesses can be reduced .
Fully cooperate with data governance : stay DSGF In the process of implementation , Ensure that the data security scheme is consistent with the enterprise data governance scheme , Especially the evaluation policy and data classification of data control .
Development and identification of key sensitive data sets : Develop the ability to identify sensitive or critical data sets , And audit the whole enterprise environment . Clear rules for coordination across multiple tools , Because a single tool or control can rarely solve the data security risk problem of all enterprises .
Continuous improvement : Regularly conduct gap analysis in enterprise data security procedures , In response to changing business objectives and dynamic threats .
This article is excerpted from 《 Read a book through financial technology security 》, Issued under the authority of the publisher .
边栏推荐
- [graphics] adaptive shadow map
- [ue4] material and shader permutation
- [opengl] advanced chapter of texture - principle of flowmap
- Detailed explanation of four modes of distributed transaction (Seata)
- TPS61170QDRVRQ1
- [transform] [NLP] first proposed transformer. The 2017 paper "attention is all you need" by Google brain team
- Global and Chinese market of Bus HVAC systems 2022-2028: Research Report on technology, participants, trends, market size and share
- 链表有环,快慢指针走3步可以吗
- 5.2-5.3
- Yolov5 series (I) -- network visualization tool netron
猜你喜欢
Vs+qt multithreading implementation -- run and movetothread
![[attention mechanism] [first vit] Detr, end to end object detection with transformers the main components of the network are CNN and transformer](/img/9b/6ca8375ef8689a80d437665909ae30.png)
[attention mechanism] [first vit] Detr, end to end object detection with transformers the main components of the network are CNN and transformer
![[engine development] in depth GPU and rendering optimization (basic)](/img/71/abf09941eb06cd91784df50891fe29.jpg)
[engine development] in depth GPU and rendering optimization (basic)
Implement Gobang with C language
5.4-5.5

Besides lying flat, what else can a 27 year old do in life?

Pytorch深度学习和目标检测实战笔记

4-20-4-23 concurrent server, TCP state transition;

Open under vs2019 UI file QT designer flash back problem
![[transformer] Introduction - the original author of Harvard NLP presented the annotated transformer in the form of line by line implementation in early 2018](/img/2b/b23aeab584f89be6678c0fe059d4b6.png)
[transformer] Introduction - the original author of Harvard NLP presented the annotated transformer in the form of line by line implementation in early 2018
随机推荐
什么是one-hot encoding?Pytorch中,将label变成one hot编码的两种方式
Tencent internship interview sorting
cpu飙升排查方法
[graphics] hair simulation in tressfx
[transform] [NLP] first proposed transformer. The 2017 paper "attention is all you need" by Google brain team
远程服务器后台挂起 nohup
[engine development] in depth GPU and rendering optimization (basic)
Yolov5进阶之七目标追踪最新环境搭建(二)
Awvs batch operation script
Global and Chinese market of air cargo logistics 2022-2028: Research Report on technology, participants, trends, market size and share
406. 根据身高重建队列
[ue4] HISM large scale vegetation rendering solution
C language dup2 function
TPS61170QDRVRQ1
Tensor 省略号(三个点)切片
. Net six design principles personal vernacular understanding, please correct if there is any error
Zzuli:1059 highest score
QT program font becomes larger on computers with different resolutions, overflowing controls
Global and Chinese markets for flexible chips 2022-2028: Research Report on technology, participants, trends, market size and share
Global and Chinese markets for transparent OLED displays 2022-2028: Research Report on technology, participants, trends, market size and share

