当前位置:网站首页>Method of win7 system anti ARP attack
Method of win7 system anti ARP attack
2022-07-28 19:22:00 【wei168hua8888】
Talking about ARP Many users of the virus will not feel strange , Because if you get ARP attack , Computer data will be sent to the designated address , At this time, it will cause great losses to us , So how can it be reversed ARP Attack ? It's very simple , Now I'll teach you Win7 System anti ARP Attack method !
Method / step :
1、 In such as CMD(MS-DOS) box , see ARP Aid of command , Pictured :



2、 Check whether you have suffered... According to the help ARP attack , Pictured :

3、 How to solve ARP attack ?( add to MAC-IP Mapping , This machine IP Corresponding to the local machine MAC), Pictured :


Win7 System anti ARP That's all for the attack method , We only need to do one step , That is to add this machine IP Corresponding MAC Address mapping .
边栏推荐
- 顺序线性表——课上练
- Lookup - lookup of sequential table and ordered table
- Is zero basic software testing training reliable?
- 3、 Uni app fixed or direct to a certain page
- unity CS1513
- Wechat official account custom sharing and updateappmessagesharedata are all successful. Why is it a link that is shared?
- Libgdx learning path 01: libgdx introduction and running tutorial
- Using CPLEX to solve small-scale energy-efficient FJSP
- C and SQL mixed programming, vs need to download what things
- ACM warm-up exercise 3 in 2022 summer vacation (detailed)
猜你喜欢

Self cultivation of Electronic Engineers - when a project is developed
OAI L3 and L2 interface analysis

Parity rearrangement of Bm14 linked list

Web 3.0 development learning path

About ASM redundancy

Tikz draw Gantt chart in FJSP -trans necessary
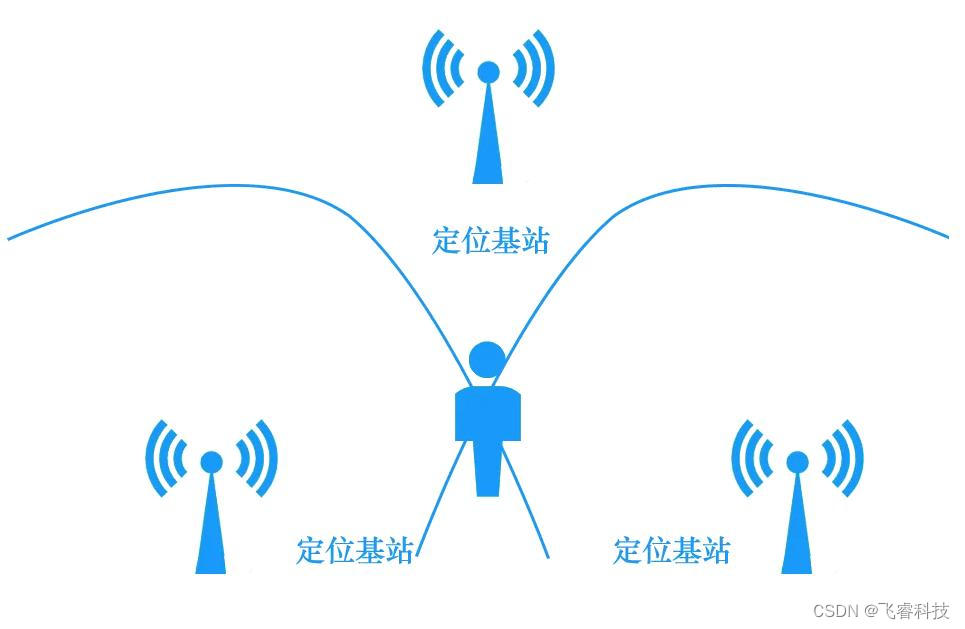
UWB module realizes personnel precise positioning, ultra wideband pulse technology scheme, and real-time centimeter level positioning application

Lookup - lookup of sequential table and ordered table

力扣 1331. 数组序号转换
![[image hiding] digital image information hiding system based on DCT, DWT, LHA, LSB, including various attacks and performance parameters, with matlab code](/img/a4/5c5a90508e2f9c6b4f8e234bdfdc9e.png)
[image hiding] digital image information hiding system based on DCT, DWT, LHA, LSB, including various attacks and performance parameters, with matlab code
随机推荐
三类6种地图可视化软件测评,最好用的工具居然是它
After several twists and turns, how long can the TSDB C-bit of influxdb last?
ICLR21(classification) - 未来经典“ViT” 《AN IMAGE IS WORTH 16X16 WORDS》(含代码分析)
From Bayesian filter to Kalman filter (zero)
When unity customizes the editor, let the subclass inherit the inspector display effect of the parent class
Solve the critical path in FJSP - with Matlab source code
ACM warm-up exercise 3 in 2022 summer vacation (detailed)
uwb模块实现人员精确定位,超宽带脉冲技术方案,实时厘米级定位应用
Using CPLEX to solve small-scale energy-efficient FJSP
Efficiency comparison of JS array splicing push() concat() methods
The difference between --save Dev and --save in NPM
Qt: 一个SIGNAL绑定多个SLOT
UWB module realizes personnel precise positioning, ultra wideband pulse technology scheme, and real-time centimeter level positioning application
1、 My first wechat applet
[filter tracking] target tracking based on EKF, TDOA and frequency difference positioning with matlab code
Can I get employed after two months of software testing training?
unity CS1513
优麒麟系统安装BeyondComare
RFs self study notes (II): theoretical measurement model - without clutter but with detection probability
Pointer learning of C language -- the consolidation of pointer knowledge and the relationship with functions, arrays and structures