Everyone is responsible for maintaining network security , This article only does technical research , Please do not use it in any business scenario .
background
When we studied polar parity check codes ,validate Parameters are generally issued by the polar test server . However, it was found that the polar verification code of the first flight only interacts with the polar inspection service only once, just pulling fullpage.js file , The inspection service has not been issued validate Parameters . Why are there so many subsequent verification links validate Parameters ?
This has aroused my curiosity , So I decided to find out .
characteristic
(1)fullpage Version is 0.0.0
(2) There is no subsequent interaction with polar experience
(3) When the first flight requests validate, But we can't find it on the Internet validate value
practice
Take Capital Airlines as an example :https://m.jdair.net/h5/views/onlinecheckin/handleCheckin.jsp
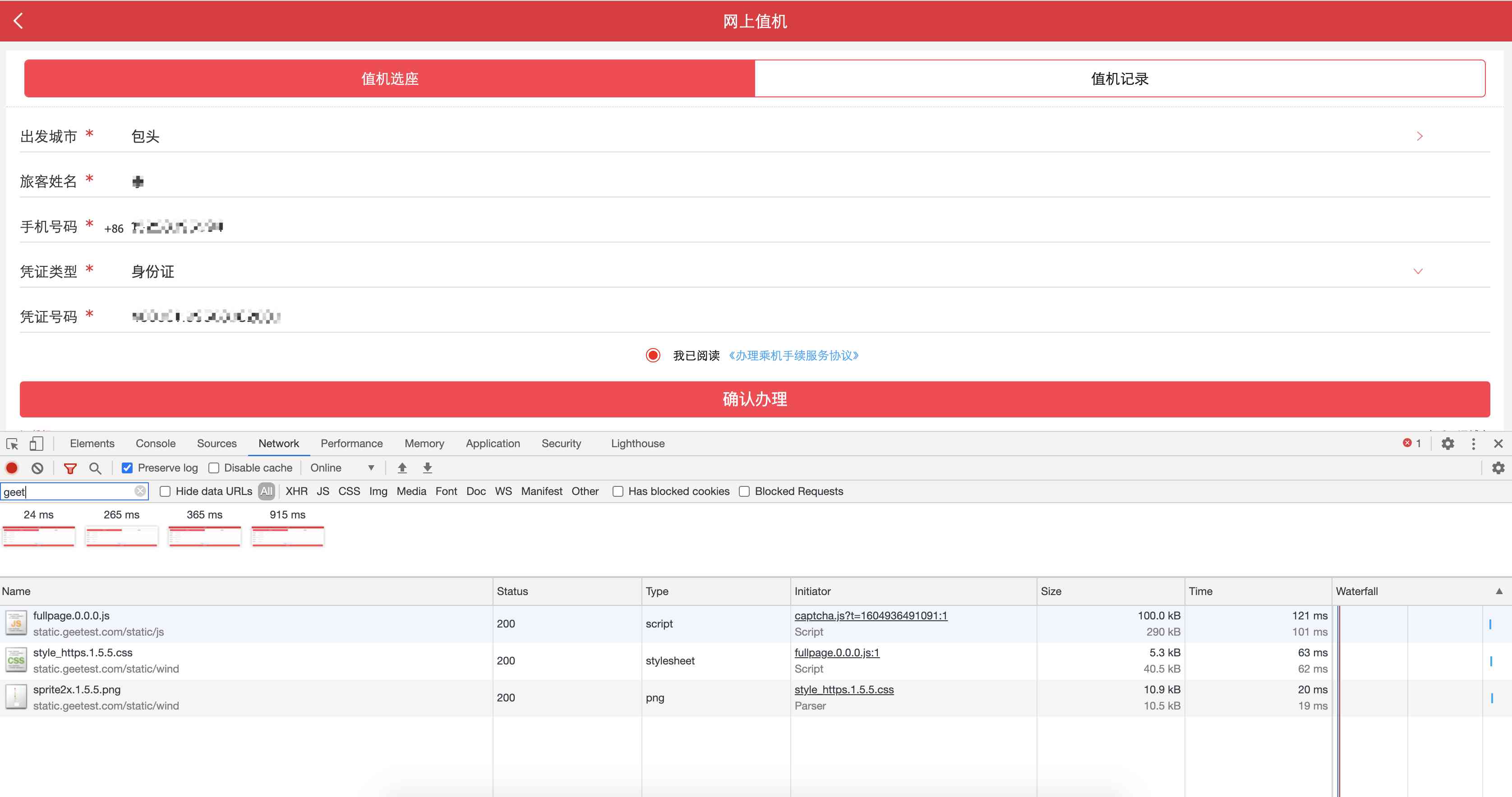
1、 see geetest Relevant request information
The discovery only got fullpage.0.0.0.js, There is no interaction between the subsequent and polar Services . It can be concluded that validate Generate... For the local .
2、 Key code
stay fullpage.0.0.0.js In file , Through static analysis + dynamic analysis , Locate local computing code .
The specific process is : Pass in challenge After function generation validate.
function $_CDm(e) {
function c(e, t) {
return e << t | e >>> 32 - t;
}
function u(e, t) {
var n, r, o, i, a;
return o = 2147483648 & e,
i = 2147483648 & t,
a = (1073741823 & e) + (1073741823 & t),
(n = 1073741824 & e) & (r = 1073741824 & t) ? 2147483648 ^ a ^ o ^ i : n | r ? 1073741824 & a ? 3221225472 ^ a ^ o ^ i : 1073741824 ^ a ^ o ^ i : a ^ o ^ i;
}
function t(e, t, n, r, o, i, a) {
return u(c(e = u(e, u(u(function s(e, t, n) {
var $_DJFy = $_AY.$_Dn
, $_DJED = ['$_DJIw'].concat($_DJFy)
, $_DJGi = $_DJED[1];
$_DJED.shift();
var $_DJHk = $_DJED[0];
return e & t | ~e & n;
}(t, n, r), o), a)), i), t);
}
function n(e, t, n, r, o, i, a) {
return u(c(e = u(e, u(u(function s(e, t, n) {
var $_EAAP = $_AY.$_Dn
, $_DJJG = ['$_EADQ'].concat($_EAAP)
, $_EABQ = $_DJJG[1];
$_DJJG.shift();
var $_EACU = $_DJJG[0];
return e & n | t & ~n;
}(t, n, r), o), a)), i), t);
}
function r(e, t, n, r, o, i, a) {
return u(c(e = u(e, u(u(function s(e, t, n) {
var $_EAFu = $_AY.$_Dn
, $_EAEo = ['$_EAIs'].concat($_EAFu)
, $_EAGH = $_EAEo[1];
$_EAEo.shift();
var $_EAHb = $_EAEo[0];
return e ^ t ^ n;
}(t, n, r), o), a)), i), t);
}
function o(e, t, n, r, o, i, a) {
return u(c(e = u(e, u(u(function s(e, t, n) {
var $_EBAC = $_AY.$_Dn
, $_EAJm = ['$_EBDv'].concat($_EBAC)
, $_EBBJ = $_EAJm[1];
$_EAJm.shift();
var $_EBCI = $_EAJm[0];
return t ^ (e | ~n);
}(t, n, r), o), a)), i), t);
}
function i(e) {
var t, n = $_DFBA(169), r = $_DFAo(169);
for (t = 0; t <= 3; t++)
n += (r = $_DFAo(127) + (e >>> 8 * t & 255)[$_DFAo(209)](16))[$_DFAo(138)](r[$_DFBA(130)] - 2, 2);
return n;
}
var a, s, _, l, h, f, d, p, g, v;
for (a = function m(e) {
var $_EBFg = $_AY.$_Dn
, $_EBEW = ['$_EBIG'].concat($_EBFg)
, $_EBGm = $_EBEW[1];
$_EBEW.shift();
var $_EBHd = $_EBEW[0];
var t, n = e[$_EBFg(130)], r = n + 8, o = 16 * (1 + (r - r % 64) / 64), i = Array(o - 1), a = 0, s = 0;
while (s < n)
a = s % 4 * 8,
i[t = (s - s % 4) / 4] = i[t] | e[$_EBFg(251)](s) << a,
s++;
return a = s % 4 * 8,
i[t = (s - s % 4) / 4] = i[t] | 128 << a,
i[o - 2] = n << 3,
i[o - 1] = n >>> 29,
i;
}(e = function E(e) {
var $_ECAV = $_AY.$_Dn
, $_EBJW = ['$_ECDz'].concat($_ECAV)
, $_ECBc = $_EBJW[1];
$_EBJW.shift();
var $_ECCN = $_EBJW[0];
e = e[$_ECBc(174)](/\r\n/g, $_ECAV(223));
for (var t = $_ECBc(169), n = 0; n < e[$_ECAV(130)]; n++) {
var r = e[$_ECAV(251)](n);
r < 128 ? t += String[$_ECBc(155)](r) : (127 < r && r < 2048 ? t += String[$_ECAV(155)](r >> 6 | 192) : (t += String[$_ECBc(155)](r >> 12 | 224),
t += String[$_ECBc(155)](r >> 6 & 63 | 128)),
t += String[$_ECBc(155)](63 & r | 128));
}
return t;
}(e)),
d = 1732584193,
p = 4023233417,
g = 2562383102,
v = 271733878,
s = 0; s < a[$_DFBA(130)]; s += 16)
p = o(p = o(p = o(p = o(p = r(p = r(p = r(p = r(p = n(p = n(p = n(p = n(p = t(p = t(p = t(p = t(l = p, g = t(h = g, v = t(f = v, d = t(_ = d, p, g, v, a[s + 0], 7, 3614090360), p, g, a[s + 1], 12, 3905402710), d, p, a[s + 2], 17, 606105819), v, d, a[s + 3], 22, 3250441966), g = t(g, v = t(v, d = t(d, p, g, v, a[s + 4], 7, 4118548399), p, g, a[s + 5], 12, 1200080426), d, p, a[s + 6], 17, 2821735955), v, d, a[s + 7], 22, 4249261313), g = t(g, v = t(v, d = t(d, p, g, v, a[s + 8], 7, 1770035416), p, g, a[s + 9], 12, 2336552879), d, p, a[s + 10], 17, 4294925233), v, d, a[s + 11], 22, 2304563134), g = t(g, v = t(v, d = t(d, p, g, v, a[s + 12], 7, 1804603682), p, g, a[s + 13], 12, 4254626195), d, p, a[s + 14], 17, 2792965006), v, d, a[s + 15], 22, 1236535329), g = n(g, v = n(v, d = n(d, p, g, v, a[s + 1], 5, 4129170786), p, g, a[s + 6], 9, 3225465664), d, p, a[s + 11], 14, 643717713), v, d, a[s + 0], 20, 3921069994), g = n(g, v = n(v, d = n(d, p, g, v, a[s + 5], 5, 3593408605), p, g, a[s + 10], 9, 38016083), d, p, a[s + 15], 14, 3634488961), v, d, a[s + 4], 20, 3889429448), g = n(g, v = n(v, d = n(d, p, g, v, a[s + 9], 5, 568446438), p, g, a[s + 14], 9, 3275163606), d, p, a[s + 3], 14, 4107603335), v, d, a[s + 8], 20, 1163531501), g = n(g, v = n(v, d = n(d, p, g, v, a[s + 13], 5, 2850285829), p, g, a[s + 2], 9, 4243563512), d, p, a[s + 7], 14, 1735328473), v, d, a[s + 12], 20, 2368359562), g = r(g, v = r(v, d = r(d, p, g, v, a[s + 5], 4, 4294588738), p, g, a[s + 8], 11, 2272392833), d, p, a[s + 11], 16, 1839030562), v, d, a[s + 14], 23, 4259657740), g = r(g, v = r(v, d = r(d, p, g, v, a[s + 1], 4, 2763975236), p, g, a[s + 4], 11, 1272893353), d, p, a[s + 7], 16, 4139469664), v, d, a[s + 10], 23, 3200236656), g = r(g, v = r(v, d = r(d, p, g, v, a[s + 13], 4, 681279174), p, g, a[s + 0], 11, 3936430074), d, p, a[s + 3], 16, 3572445317), v, d, a[s + 6], 23, 76029189), g = r(g, v = r(v, d = r(d, p, g, v, a[s + 9], 4, 3654602809), p, g, a[s + 12], 11, 3873151461), d, p, a[s + 15], 16, 530742520), v, d, a[s + 2], 23, 3299628645), g = o(g, v = o(v, d = o(d, p, g, v, a[s + 0], 6, 4096336452), p, g, a[s + 7], 10, 1126891415), d, p, a[s + 14], 15, 2878612391), v, d, a[s + 5], 21, 4237533241), g = o(g, v = o(v, d = o(d, p, g, v, a[s + 12], 6, 1700485571), p, g, a[s + 3], 10, 2399980690), d, p, a[s + 10], 15, 4293915773), v, d, a[s + 1], 21, 2240044497), g = o(g, v = o(v, d = o(d, p, g, v, a[s + 8], 6, 1873313359), p, g, a[s + 15], 10, 4264355552), d, p, a[s + 6], 15, 2734768916), v, d, a[s + 13], 21, 1309151649), g = o(g, v = o(v, d = o(d, p, g, v, a[s + 4], 6, 4149444226), p, g, a[s + 11], 10, 3174756917), d, p, a[s + 2], 15, 718787259), v, d, a[s + 9], 21, 3951481745),
d = u(d, _),
p = u(p, l),
g = u(g, h),
v = u(v, f);
return (i(d) + i(p) + i(g) + i(v))[$_DFAo(192)]();
}
3、 Last call result
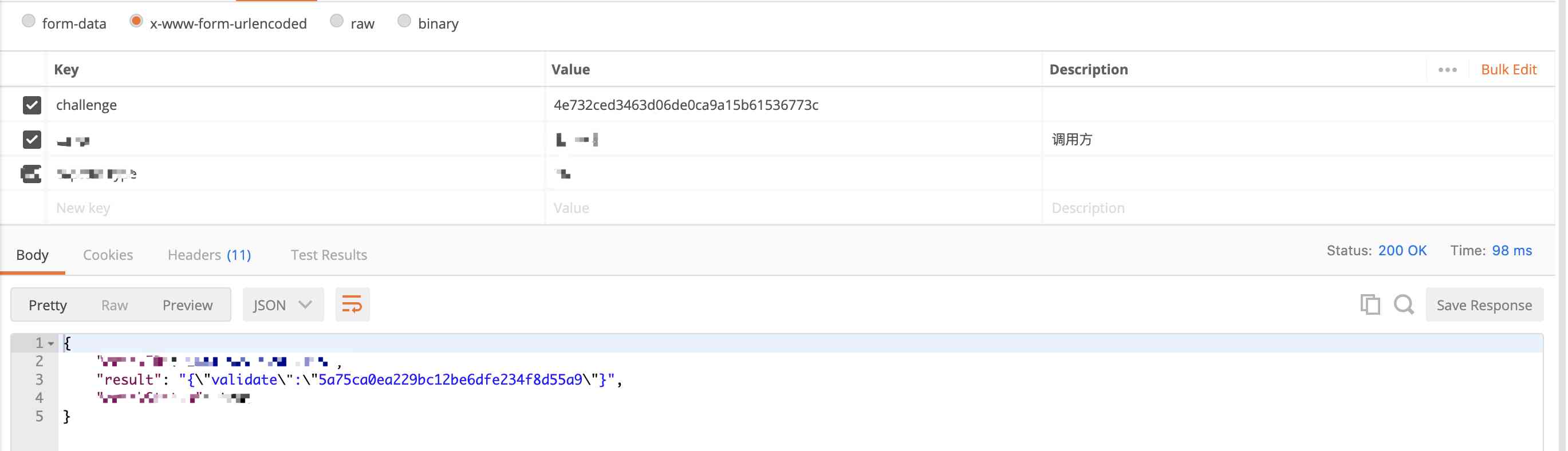
The specific service code is not open source .
Last
I don't understand when it will trigger fullpage.0.0.0.js, Let's take it for a while as a kind of strategy .
In extreme cases , The EPI service cannot respond , Use pass js Confusing the underlying logic , Enable local algorithms for token Computing is also a good way to design .
Last and last , Everyone is responsible for maintaining network security , This article only does technical research , Please do not use it in any business scenario .