当前位置:网站首页>Centos7 operating system security hardening series (2)
Centos7 operating system security hardening series (2)
2020-11-09 22:42:00 【yuanfan2012】
Click on the above "walkingcloud" Focus on , And select " Star standard " official account

1、 Password repeat limit
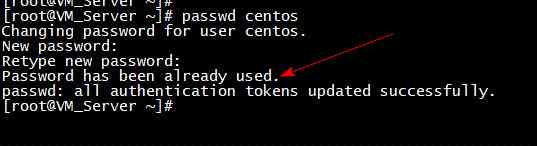
Rule description : Re enable an old password , Make sure that the password has been changed several times since it was last used . This policy enables administrators to enhance security by ensuring that old passwords are not continuously reused
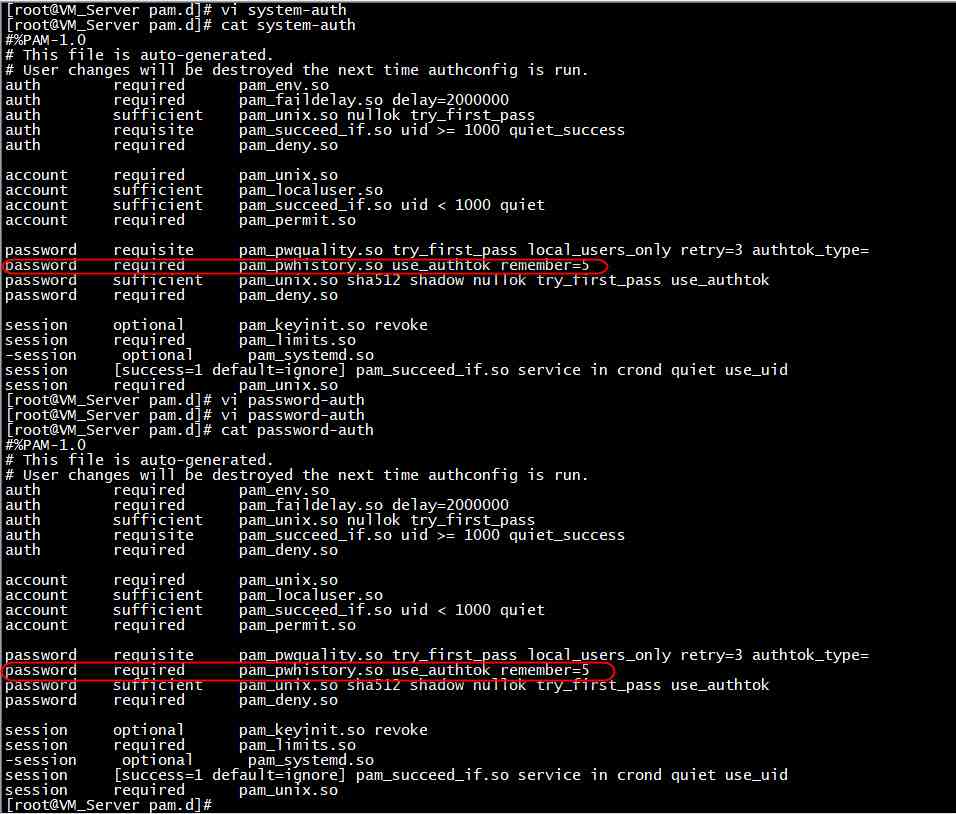
Audit description : Check the documents /etc/pam.d/system-auth And documents /etc/pam.d/password-auth Whether the following configuration exists :password sufficient pam_unix.so remember=5 or password required pam_pwhistory.so remember=5 among remember Option is greater than or equal to 5
Suggestions for modification : Edit profile /etc/pam.d/system-auth And documents /etc/pam.d/password-auth Modify or add configuration :password sufficient pam_unix.so remember=5 or password required pam_pwhistory.so remember=5 remarks : Use remember=5 The configuration covers the original module configuration
Practical solutions : Edit profile /etc/pam.d/system-auth And documents /etc/pam.d/password-auth Modify or add the following configuration
password required pam_pwhistory.so use_authtok remember=5
2、 File and directory default permission control
Rule description : This setting determines the default permissions for newly created directories and files
Audit description : Check /etc/profile, /etc/profile.d/.sh, /etc/bashrc Of umask Configure to 027( perhaps 0027)
Suggestions for modification : Set up /etc/profile /etc/profile.d/.sh、/etc/bashrc In the document umask Configure to 027( perhaps 0027)
umask Value means : When a user creates a new file or directory , The file or directory has a default permission . The default permission is set by umask Value to specify .umask Value represents permission “ Complement code ”, That is to subtract from the default maximum permission value umask It's worth the actual permission value .
The default maximum permissions for a file are readable and writable , The default maximum permissions for a directory are read, write, and executable .
That is, the actual default permissions of a file are 666 subtract umask value . The actual default permissions for the directory are 777 subtract umask value
resolvent :
sed -i 's/umask 022/umask 027/g' /etc/profile
sed -i 's/umask 022/umask 027/g' /etc/bashrc
Before the change
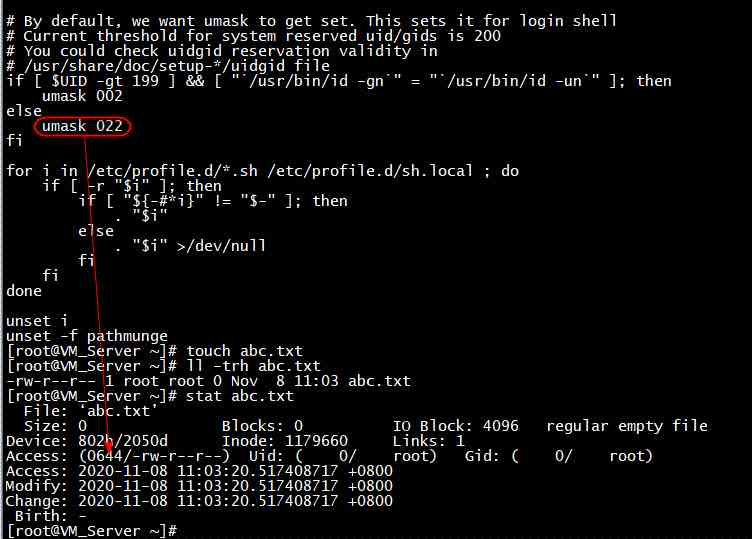
After modification
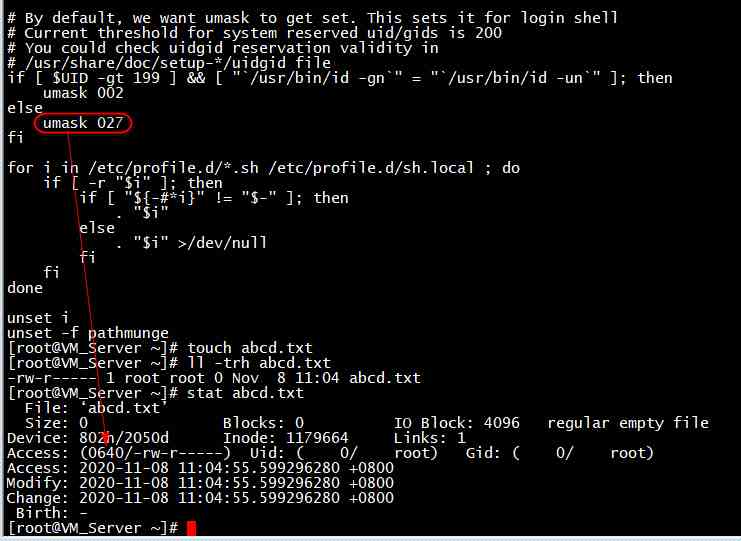
3、 Configure user minimum Authorization
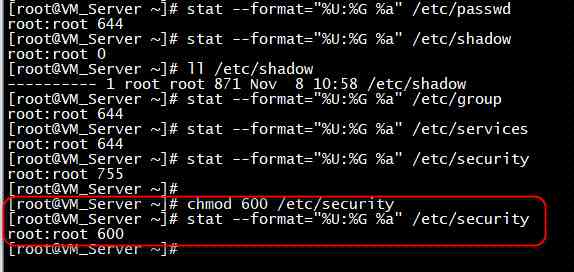
Rule description : Check the documents /etc/passwd、/etc/shadow、/etc/group、/etc/services、/etc/xinetd.conf And contents /etc/security Authority
Audit description : Check the documents /etc/passwd、/etc/group、/etc/services Whether the permission of is less than or equal to 644, Check the documents /etc/shadow Whether the permission of is less than or equal to 400, Check /etc/xinetd.conf file 、/etc/security Whether the directory permission is less than or equal to 600, Check whether the owners and groups of the above files and directories are root:root
Suggestions for modification : Settings file /etc/passwd、/etc/group、/etc/services The authority of is 0644, Settings file /etc/shadow The authority of is 0400, Settings file /etc/xinetd.conf、 Catalog /etc/security The authority of is 0600,
For example, to perform :chmod 600 /etc/passwd. Set the owner and group of the above files and directories as root:root, For example, to perform :chown root:root /etc/passwd
Test case information :{ "checkDescription": " In the catalog /etc/security In existence , Check file permissions , Nonexistence pass: stat --format="%U:%G %a" /etc/security 2>/dev/null", "current_value": "/etc/security root:root 0755", "suggest_value": " The file does not exist or /etc/security root:root 600( Or more strictly )" }
To solve the process
stat --format="%U:%G %a" /etc/passwd
stat --format="%U:%G %a" /etc/shadow
ll /etc/shadow
stat --format="%U:%G %a" /etc/group
stat --format="%U:%G %a" /etc/services
stat --format="%U:%G %a" /etc/security
chmod 600 /etc/security
stat --format="%U:%G %a" /etc/security
4、 modify SSH Of Banner Warning message
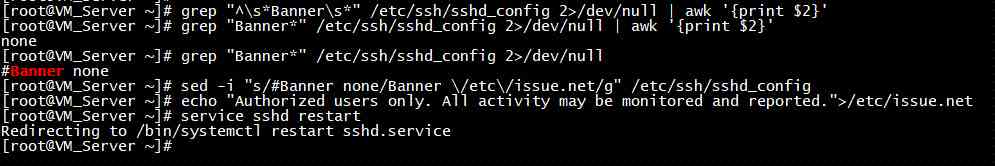
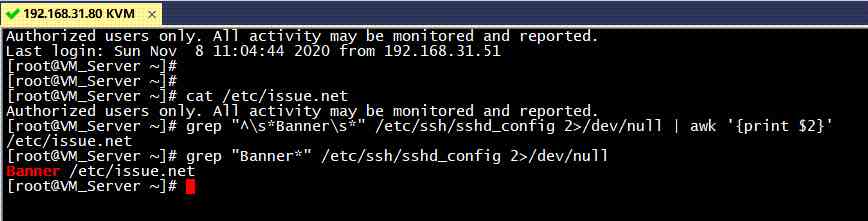
Rule description : Check ssh Service status , If it is not turned on pass, If on, check if it is set ssh Login alarm information , Setting rules pass
Audit description : Check ssh Service status , If it is not turned on pass, If open, check /etc/ssh/sshd_config file , Whether to configure Banner, Get its path file , Check that the file is not empty , If it is not empty pass
Suggestions for modification : If ssh Service doesn't need , The service needs to be shut down . if necessary ssh service , You need to configure /etc/ssh/sshd_config In file Banner
[root@VM_Server ~]# grep "^\s*Banner\s*" /etc/ssh/sshd_config 2>/dev/null | awk '{print $2}'
[root@VM_Server ~]# grep "Banner*" /etc/ssh/sshd_config 2>/dev/null | awk '{print $2}'
none
[root@VM_Server ~]# grep "Banner*" /etc/ssh/sshd_config 2>/dev/null
#Banner none
[root@VM_Server ~]# sed -i "s/#Banner none/Banner \/etc\/issue.net/g" /etc/ssh/sshd_config
[root@VM_Server ~]# echo "Authorized users only. All activity may be monitored and reported.">/etc/issue.net
[root@VM_Server ~]# service sshd restart
5、 Set key file properties
Rule description : Check /var/log/messages Does the file exist a attribute
Audit description : Check /var/log/messages Does the file exist a attribute :lsattr /var/log/messages | cut -b 6
Suggestions for modification : Use the command to change the log file properties :chattr +a /var/log/messages
lsattr /var/log/messages
lsattr /var/log/messages | cut -b 6
chattr +a /var/log/messages
lsattr /var/log/messages | cut -b 6

This article is from WeChat official account. - WalkingCloud(WalkingCloud2018).
If there is any infringement , Please contact the [email protected] Delete .
Participation of this paper “OSC Source creation plan ”, You are welcome to join us , share .
版权声明
本文为[yuanfan2012]所创,转载请带上原文链接,感谢
边栏推荐
- 当我们开发一个接口时需要注意些什么
- Application of V7 version of lvgl Library
- Can public IP address and SSL certificate improve SEO?
- Python调用飞书发送消息
- CUDA_共享内存、访存机制、访问优化
- Come and learn! Development Guide for personalized recommendation system (with internet disk link)
- Brief analysis of LinkedList source code
- CRM系统能帮助企业做哪些事?
- Do you know your server? Do you know what's inside the server
- Day84: Luffy: preferential activity strategy & User Authentication & checking / settlement of shopping cart goods
猜你喜欢

2018中国云厂商TOP5:阿里云、腾讯云、AWS、电信、联通 ...

CRM系统能帮助企业做哪些事?

SQL server attached database access denial resolution summary
![Usage of [:] and [::] in Python](/img/3b/00bc81122d330c9d59909994e61027.jpg)
Usage of [:] and [::] in Python

Hand in hand to teach you to use container service tke cluster audit troubleshooting

asp.net Using serilog in core and customizing enrich

DB-Engines 11月数据库排名:PostgreSQL坐稳同期涨幅榜冠军宝座

Performance evaluation report of YoMo codec - Y3
SSL证书和公网IP地址如何影响SEO
eleven point nine
随机推荐
C/C++编程笔记:C语言开发坦克大战!纪念我们逝去的小霸王游戏
Common concepts and points for attention of CUDA
PHP - curl copy paste access SMS verification code example
PL/SQL Developer临时用户和新手的功能指南
sql 筛选查询重复列
Fear of reconstruction? I'm too late to tell you how to refactor. Now I'm here
价值超10亿美元的直播系统架构图是什么样子的?
The problem of looting by leetcode
Aikang Guobin denounced Guoxin Securities report as untrue and sent a lawyer's letter
剑指offer之打印二叉搜索树中第k小的结点
LeetCode-378. 有序矩阵中第K小的元素
那么当下的行情投资者该怎么办呢? 现在新的投资风口来了!
手把手教你使用容器服务 TKE 集群审计排查问题
LeetCode 50 Pow(x,n)
The solution of type interface * * is not known to the mapperregistry
Leetcode 49 letter heterotopic word grouping
商品后台系统优化
SQL server attached database access denial resolution summary
CUDA_寄存器和局部存储器
获取List集合对象中某一列属性值