当前位置:网站首页>Rhcsa day 3
Rhcsa day 3
2022-07-04 02:55:00 【Dd_ five hundred and seventy-seven】
1、 Sum up vim Of the three modes, the commands you think are practical
1、Vi/vim (-o) file 1 file 2( Open two files )ctrl+w+w Switch
Command mode :
d Delete ,dd Deletes the line where the cursor is located x Delete cursor u withdraw
G Jump to the end ( Numbers G Jump to line number ) ^ Head of line $ At the end of the line
( Numbers )yy Copy line ( Numbers )cc shear p Paste
Last row mode :
Wq!( preservation 、 sign out 、 mandatory ) nu\nonu( Digital marker line exit )
r( Open the specified file to the next line ) noh( set nohlsearch )
%s /// Change the specified text
2、 File management command exercise :
stay /opt Create a temporary directory under the directory tmp;
Create a file in the temporary directory , The file named a.txt;
take a.txt Copy it into b.txt; take b.txt Change its name to c.txt;
Create symbolic links , The linked file name is linkc.txt;
[[email protected] ~]# mkdir /opt/tmp
[[email protected] ~]# cd /opt/tmp
[[email protected] tmp]# touch a.txt
[[email protected] tmp]# cp -p a.txt b.txt
[[email protected] tmp]# mv b.txt c.txt
[[email protected] tmp]# ln -s c.txt linkc.txt
3、vi practice : Complete the following steps
1) application vi Command in /tmp Create files under folders , file name newfile. stay newfile Enter the date and time on the first line

2) take /boot/grub2/grub.cfg The contents of the document are read into newfile In the document ( On the next line of the date, i.e 2 That's ok )
3) Find documents that contain # The line of the sign character , Delete entire line

4) Turn on VI Line number prompt function
:set nu // Turn on the line number prompt
:set nonu // Turn off line number prompt 5) Move the cursor to 5 That's ok , And in the first place 5 A new blank line is generated after the line 6 That's ok
Can be in command mode yy( Copy ) A blank line again p( Paste )
Or in input mode Enter key 6) Modify the content . Will all timeout=5, Change to time=30
:%s/timeout=5/time=307) All... In the entire document root The character is changed to admin character
:%s/root/admin8) Copy No 1 The date and time content of the line to the end of the document
Can be in command mode yy( Copy ) The first line again p( Paste )
In command mode gg Move to first line G Move to last line 9) Save the document , Save the document again as /boot/newfile2, sign out VI Editor 

4、 The file to view
Copy user profile to /opt Under the table of contents ;
see /opt/mima File first 6 That's ok ;
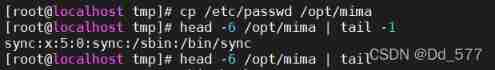
5. Statistics show user profiles nologin Number of occurrences

6. Displays the total number of users in the system 
7. Set the system time ( Minutes and seconds ) write in time file 
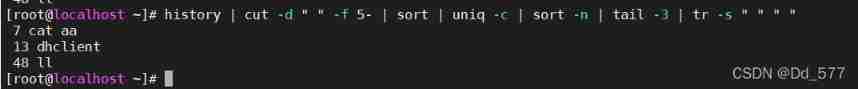
8.history The system command history can be displayed , Count the top three with the highest command frequency of the current system .( The command repeats three more commands )
边栏推荐
- Node solves cross domain problems
- What are the main investment products of bond funds and what are they
- Problems and solutions of several concurrent scenarios of redis
- 2022 examination summary of quality controller - Equipment direction - general basis (quality controller) and examination questions and analysis of quality controller - Equipment direction - general b
- Fudan released its first review paper on the construction and application of multimodal knowledge atlas, comprehensively describing the existing mmkg technology system and progress
- LV1 Roche limit
- Properties of binary trees (numerical aspects)
- LV1 tire pressure monitoring
- I stepped on a foundation pit today
- POSTECH | option compatible reward reverse reinforcement learning
猜你喜欢
![[Valentine's Day confession code] - Valentine's Day is approaching, and more than 10 romantic love effects are given to the one you love](/img/ab/066923f1aa1e8dd8dcc572cb60a25d.jpg)
[Valentine's Day confession code] - Valentine's Day is approaching, and more than 10 romantic love effects are given to the one you love

High level application of SQL statements in MySQL database (I)
ZABBIX API pulls the values of all hosts of a monitoring item and saves them in Excel

A brief talk on professional modeler: the prospect and professional development of 3D game modeling industry in China

Setting methods, usage methods and common usage scenarios of environment variables in postman
![[Yugong series] February 2022 attack and defense world advanced question misc-84 (MySQL)](/img/4d/4a6b76896bf81a27d036a047f68b2b.jpg)
[Yugong series] February 2022 attack and defense world advanced question misc-84 (MySQL)
Node write API

What is cloud primordial?
WP collection plug-in free WordPress collection hang up plug-in

Final consistency of MESI cache in CPU -- why does CPU need cache
随机推荐
POSTECH | option compatible reward reverse reinforcement learning
[Yugong series] February 2022 attack and defense world advanced question misc-84 (MySQL)
Ai aide à la recherche de plagiat dans le design artistique! L'équipe du professeur Liu Fang a été embauchée par ACM mm, une conférence multimédia de haut niveau.
Database concept and installation
Fudan released its first review paper on the construction and application of multimodal knowledge atlas, comprehensively describing the existing mmkg technology system and progress
Keep an IT training diary 055- moral bitch
WP collection plug-in free WordPress collection hang up plug-in
Leetcode 110 balanced binary tree
Contest3145 - the 37th game of 2021 freshman individual training match_ 1: Origami
I stepped on a foundation pit today
JS object definition
3D game modeling is in full swing. Are you still confused about the future?
Network byte order
Jenkins continuous integration environment construction V (Jenkins common construction triggers)
Kiss number + close contact problem
MySQL advanced SQL statement (1)
Format character%* s
Love and self-discipline and strive to live a core life
2006 translation
基於.NetCore開發博客項目 StarBlog - (14) 實現主題切換功能
