当前位置:网站首页>Csma/cd carrier monitoring multipoint access / collision detection protocol
Csma/cd carrier monitoring multipoint access / collision detection protocol
2022-07-07 14:09:00 【sinat_ thirty-six million seven hundred and eighty-nine thousan】
“ Multipoint access ” It means that many computers are connected to a bus by means of multi-point access .
“ carrier sense ” It means that each station should check whether there are other computers sending data on the bus before sending data , If there is , Do not send data for the time being , In case of collision . “ carrier sense ” It is to use electronic technology to detect whether there are data signals sent by other computers on the bus .
“ collision detection ” That is, when the computer sends data, it detects the signal voltage on the channel . When several stations send data on the bus at the same time , The signal voltage swing on the bus will increase ( Superimpose on each other ). When the signal voltage swing value detected by a station exceeds a certain threshold value , It is considered that at least two stations on the bus are sending data at the same time , Indicates a collision . So-called “ Collision ” It's a conflict . therefore “ collision detection ” Also known as “ Collision detection ”.
After collision detected : In the event of a collision , The signal transmitted on the bus has serious distortion , There is no way to recover useful information . Every station that is sending data , Once a collision is found on the bus , Stop sending immediately , So as not to waste network resources , Then wait for a random period of time and send again .
characteristic :
1、 Use CSMA/CD Protocol Ethernet can not carry out full duplex communication but only two-way alternate communication ( Half duplex communication ).
2、 Each station is in a short period of time after sending data , There is a possibility of collision . This uncertainty of transmission makes the average traffic of the whole Ethernet far less than the maximum data rate of Ethernet .
Contention period :
The first station to send data frames , At most time after sending data frame 2a ( Twice the end-to-end round trip delay ) We can know whether the transmitted data frame has suffered collision . After the contention period, no collision has been detected , In order to be sure that this transmission will not collide .
Ethernet end-to-end round-trip delay 2a It's called contention period , Or collision window . Usually , take 51.2 us For the length of the contention period . about 10 Mb/s Ethernet , It can be sent during the contention period 512 bit, namely 64 byte . When Ethernet sends data , If before 64 No bytes conflict , Then the subsequent data will not conflict .
If there is a conflict , It must have been before it was sent 64 In bytes . As soon as a conflict is detected, the transmission is stopped , At this time, the data already sent must be less than 64 byte . Ethernet specifies Shortest valid frame Long for 64 byte , Where the length is less than 64 Byte frames are invalid frames aborted due to conflicts .
“ Wait for a random period of time ” The explanation of —— Binary exponential type backoff algorithm :
The collision station stops sending data , To postpone ( to retreat ) A random time to send data .
Determine the basic retreat time , Generally, it is taken as the period of contention 2a.
Defining parameters k ,
k = Min[ Number of retransmissions , 10]
From the set of integers [0,1,…, (2^k - 1)] Randomly take a number , Write it down as r. The delay required for retransmission is r Times the basic escape time .
When re communicating 16 Discard the frame if it still fails , And report to the top .
边栏推荐
- 参数关键字Final,Flags,Internal,映射关键字Internal
- Laravel5 call to undefined function OpenSSL cipher IV length() error php7 failed to open OpenSSL extension
- XML文件的解析操作
- Help tenants
- How does MySQL control the number of replace?
- 带你掌握三层架构(建议收藏)
- js 获取当前时间 年月日,uniapp定位 小程序打开地图选择地点
- 118. 杨辉三角
- Details of redis core data structure & new features of redis 6
- Indoor ROS robot navigation commissioning record (experience in selecting expansion radius)
猜你喜欢

VSCode 配置使用 PyLint 语法检查器
gvim【三】【_vimrc配置】
LeetCode简单题分享(20)
Xshell connection server changes key login to password login

为租客提供帮助

Flask session forged hctf admin
通过 iValueConverter 给datagrid 的背景颜色 动态赋值
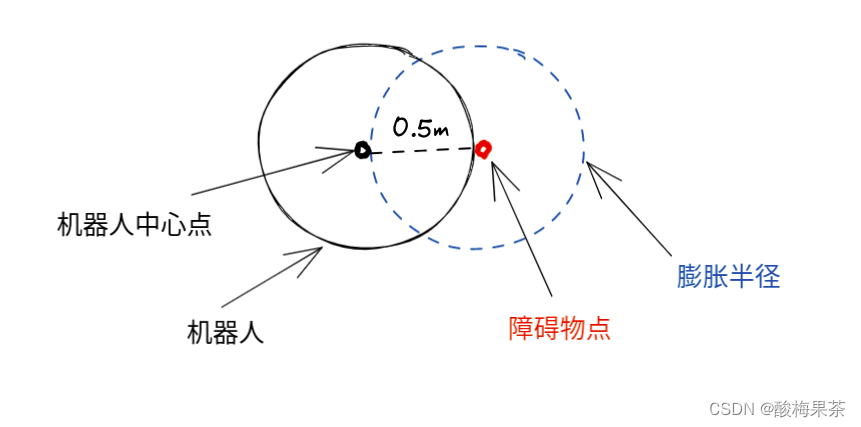
Indoor ROS robot navigation commissioning record (experience in selecting expansion radius)
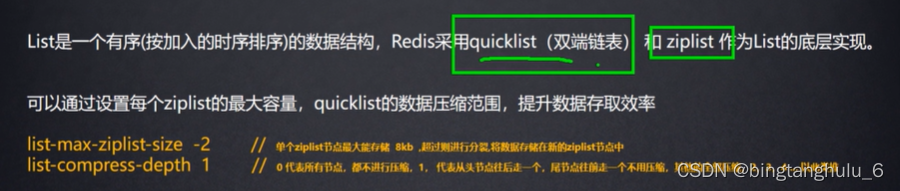
Redis 核心数据结构 & Redis 6 新特性详
XML文件的解析操作
随机推荐
Supply chain supply and demand estimation - [time series]
mysql导入文件出现Data truncated for column ‘xxx’ at row 1的原因
Details of redis core data structure & new features of redis 6
Mysql怎样控制replace替换的次数?
Mathématiques avancées - - chapitre 8 différenciation des fonctions multivariables 1
Redis 核心数据结构 & Redis 6 新特性详
带你掌握三层架构(建议收藏)
Laravel form builder uses
Laravel5 call to undefined function openssl cipher iv length() 报错 PHP7开启OpenSSL扩展失败
Best practice | using Tencent cloud AI willingness to audit as the escort of telephone compliance
最长上升子序列模型 AcWing 1012. 友好城市
2022-7-6 Leetcode 977. Square of ordered array
TPG x AIDU | AI leading talent recruitment plan in progress!
Excuse me, when using Flink SQL sink data to Kafka, the execution is successful, but there is no number in Kafka
【AI实战】应用xgboost.XGBRegressor搭建空气质量预测模型(二)
Did login metamask
【日常训练】648. 单词替换
高等数学---第八章多元函数微分学1
js 获取当前时间 年月日,uniapp定位 小程序打开地图选择地点
"Song of ice and fire" in the eleventh issue of "open source Roundtable" -- how to balance the natural contradiction between open source and security?