当前位置:网站首页>Yyds dry goods inventory # look up at the sky | talk about the way and principle of capturing packets on the mobile terminal and how to prevent mitm
Yyds dry goods inventory # look up at the sky | talk about the way and principle of capturing packets on the mobile terminal and how to prevent mitm
2022-07-02 16:33:00 【Petterpx】
Capturing packages is for every developer , It should be said that it is one of the most basic skills , Recently, due to the needs of the company, I came into contact with some bag grabbing related , Also encountered some strange problems , So make a simple record , Hope to help you .

Commonly used packet capturing tools on mobile terminals
A good workman does his work well , You must sharpen your tools first , Grab the bag , How can there be no good tools , For ordinary bag grabbing , We have the following tools
Fiddler
stay windows The environment is very good , It provides a series of packet capturing methods and subsequent scripts , Focus on , Script , This is also the reason why many people like .
Be careful : stay mac Poor support , The new version of the software lacks core function scripts , Experience is very poor .
Charles
Experience nice, stay Mac,windows Experience is ok , Support scheduled storage , Related scripts are not supported .( That's why it's not as good as fiddler The cause of the fire , stay mac It was a good experience )

AnyProxy
Alibaba's packet capturing tool , Use... On the web , Easy to use , Support js Script . Batch packet capturing can be considered .
summary
The following experiences are personal experience .
If it is windows user , I just want to practice my hand casually ,fiddler Bad choice ,mac user choice Charles.
If you want to analyze the data after catching it , Write to database , that AnyProxy and fiddler Can meet the needs ,mac Users directly consider AnyProxy that will do , Don't ask why , Asking is fiddler stay mac It's a lump of porridge .
Related use tutorials , A handful , I won't narrate here .
reminder : Remember to install the certificate , Remember Android7.0 following ( Above use xp frame , Or something else )
Principle of common bag capturing tools
It seems that it's a bit off the subject , Next, get back on track , What is the principle of the above packet capturing software ?
MITM, It's the middleman [Gong Ji],Ps: These two words involve violations
What is? MITM?
A picture is worth a thousand words ( Small gray figure )

In short , Little red and little green need to communicate , As a result, Xiao Hei, the middleman, overheard and forwarded them respectively .
Not having https Do you ?
Many people think that , use https No, that's fine , I have a certificate for verification , But ordinary https Still equivalent to streaking , Allied The above tools can still crawl through proxy plus forged root certificates https, See the following analysis for the specific principle .
Principle analysis
We use charles give an example .charles Equivalent to an intermediary agent . When the client communicates with the server , charles Receive the certificate of the server , Then dynamically generate a certificate and send it to the client , then charles As an intermediate agent on the client and The server Communication between , So relevant communication data Can be Charles Intercept .
As described in the figure below :
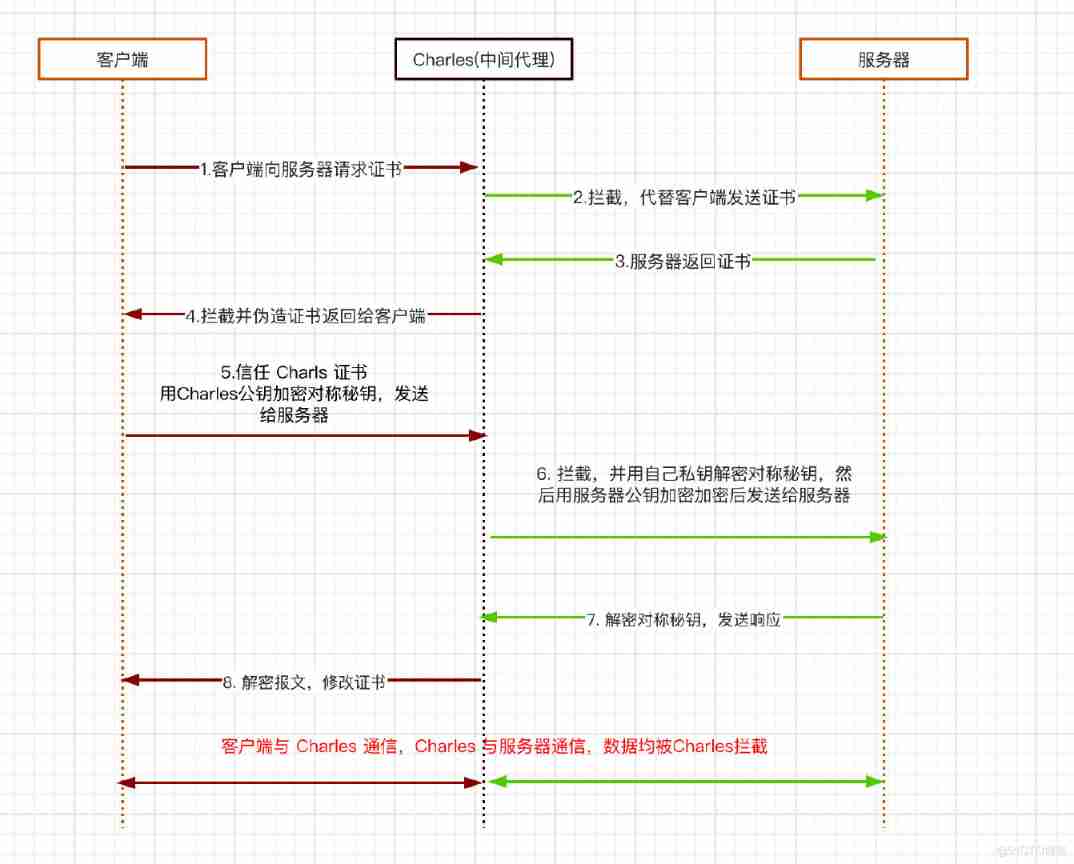
The specific steps are as follows :
- client To the server launch HTTPS request
- Charles Intercept client requests , Masquerading as a client making a request to the server
- The server towards client Back to the server CA certificate . ( In fact, it has been Charles Intercept )
- Charles Intercept the server's response , Get server certificate public key , Then make a certificate of your own , Replace the certificate of the server and send it to client .
- client Received The server ( It's actually Charles Certificate ) After the certificate , Generate a symmetric secret key , And use Charles The certificate sent back is encrypted with public key , Send to The server ( Actually sent to Charles)
- Charles Intercept the response from the client , Decrypt the symmetric secret key with your own private key ( Here we have got the symmetric key ), Then use the server certificate public key to encrypt , Send to the server .
- The server decrypts the symmetric secret key with its own private key , Client side ( the truth is that Charles) send out Respond to
- Charles Intercept server response , Replace it with your own certificate and send it to the client .
- thus , Link building , Charles Got it The public key of the server certificate and Symmetric secret key negotiated by client and server , Then you can decrypt or modify the encrypted message .
That's why we catch https You need to install the corresponding certificate , Because we have to make the client think the certificate is valid , That is, our certificate is also the root certificate , however Android7.0 in the future , Certificates manually installed by users will not be trusted , So we usually use xp Framework or other ways
How to prevent MITM?
Determine whether to set the proxy
When the network requests , Determine whether the client currently sets a proxy , If you set a proxy , It is forbidden to visit .
Client local certificate validation
The client does certificate verification locally , And setting not only verifies the public key , Set complete formal verification mode . In this case , The certificate will not only verify the domain name when verifying the request , The public key and other information in the certificate will also be verified , In this case , Certificates forged by intermediaries cannot be verified , Unable to capture packets .
Https Request and corresponding data are encrypted
Encrypt the data encrypted by the certificate again , In this way, even if the other party has replaced the certificate , Then the data we see is still a pile of data after chaos .
Last , The above are my true understanding and actual feelings , There are risks in catching bags , Just practice your hands , Don't be a black and gray industry
Reference blog
I am a Petterp , If you think my article is helpful to you , Welcome to thumb up , If you have any thoughts and questions , Feel free to discuss in the comment area .
边栏推荐
- Yyds dry inventory method of deleting expired documents in batch
- According to the atlas of data security products and services issued by the China Academy of information technology, meichuang technology has achieved full coverage of four major sectors
- unity Hub 登录框变得很窄 无法登录
- PCL point cloud image transformation
- Song of cactus - throwing stones to ask the way (2)
- JS learning notes - operators
- PCL 最小中值平方法拟合平面
- Best practices for building multi architecture images
- What is Amazon keyword index? The consequences of not indexing are serious
- Write your own CPU Chapter 11 - learning notes
猜你喜欢

Practice of traffic recording and playback in vivo

Yyds dry goods inventory has not revealed the artifact? Valentine's Day is coming. Please send her a special gift~

MySQL calculates the data within the longitude and latitude range

头条 | 亚控科技产品入选中纺联《纺织服装行业数字化转型解决方案重点推广名录》
What is the difference between self attention mechanism and fully connected graph convolution network (GCN)?

Solve * * warning * *: your ApplicationContext is unlikely to start due to a @componentscan of the defau
Add user-defined formula (time sharing t+0) to mobile app access as an example

Rock PI Development Notes (II): start with rock PI 4B plus (based on Ruixing micro rk3399) board and make system operation

mysql 计算经纬度范围内的数据

曆史上的今天:支付寶推出條碼支付;分時系統之父誕生;世界上第一支電視廣告...
随机推荐
Trigger: MySQL implements adding or deleting a piece of data in one table and adding another table at the same time
Yyds dry inventory KVM new inventory to expand space for home
ROW_ NUMBER()、RANK()、DENSE_ Rank difference
Register as a harmonios developer and install deveco studio 3.0 beta2 for harmonios
July 1st gift: Yi Jingjie's "hundred day battle" ended perfectly, and the database of Guiyang bank was sealed in advance
Song of cactus - throwing stones to ask the way (2)
[fluent] dart data type string type (string definition | string splicing | string API call)
Yyds dry goods inventory has not revealed the artifact? Valentine's Day is coming. Please send her a special gift~
Seal Library - installation and introduction
Mathematical analysis_ Notes_ Chapter 5: univariate differential calculus
How to use stustr function in Oracle view
Construction and business practice of Zhongke brain knowledge map platform
Boot connection to impala database
SQL solves the problem of continuous login deformation holiday filtering
Introduction to database system Chapter 1 short answer questions - how was the final exam?
[fluent] dart data type number type (DART file creation | num type | int type | double type | num related API)
In memory of becoming the first dayu200 tripartite demo contributor
Figure database | Nepal graph v3.1.0 performance report
Everyone Xinfu builds: a one-stop intelligent business credit service platform
Understand the key technology of AGV -- the difference between laser slam and visual slam