当前位置:网站首页>SSH service
SSH service
2022-07-24 05:15:00 【LEE_ September】
SSH service
List of articles
1. Concept
SSH(Secure Shell) It's a secure channel protocol , It is mainly used for remote login of character interface 、 Remote replication and other functions
SSH The protocol encrypts the data transmission between the two sides , It includes the user password entered when the user logs in ,SSH For security protocols based on application layer and transport layer
effect :
Data transmission is encrypted , Can prevent information leakage
Compressed during data transmission , Can improve transmission speed
SSH client :Xshell、Putty、CRT、MobaXterm、Finalshell
SSH Server side :OpenSSH
centos 7 The system is installed by default OpenSSH Related packages , And will SSHD Service added as bootstrap

SSHD By default, the service uses TCP Of 22 port
SSHD The default configuration file of the service /etc/ssh/sshd_config
ssh_config and sshd_config All are ssh The configuration file for the server , The difference between the two is that the former is a configuration file for the client , The latter is the configuration file for the server
ssh The server mainly includes two service functions :ssh Remote Links and sftp service
effect :SSHD Service usage SSH Protocol can be used for remote control , Or transfer files between computers .
Compared with the previous use Telnet It's much safer to transfer files in this way , because Talnet Use clear text transmission ,SSH It's encrypted transmission
The service name :sshd
Server main program : /usr/sbin/sshd
Server profile :/etc/ssh/sshd_config
2.SSH Remote login mode
1) Method 1
ssh [ Remote host user name ] @[ Remote server host name or IP Address ] -p port( Port number , If you do not write the port number, the default is 22 )
When in Linux Connect another computer remotely on the host Linux When the main engine , If the currently logged in user is root Words , It is also used when connecting to another host root When the user logs in , You can use it directly ssh IP, The port defaults , If the port is not the default , Need to use -p Designated port


Turn on two virtual machines ,IP Respectively 192.168.39.131 and 192.168.36.129
stay 131 Enter... On the host
[[email protected] ~]# ssh [email protected]
choice yes
After entering the password (ssh Every public key that you have visited the computer will be recorded in ~/.ssh/known_hosts), You can see that the hostname becomes 129 Host name
Try to /opt Create files in directory , And in 129 The file viewed on the host already exists
Enter on exit exit perhaps ctrl+d
If you want to log in through the host name , You can try to modify the configuration file
[[email protected] ~]# vim /etc/hosts
add to 192.168.36.129 liwenbin
You can log in through the host name
2) Method 2
ssh -l [ Remote host name ] [ Remote server host name or IP Address ] -p port
-l : Specify login name
-p : Specify the login port ( When the port of the server is not the default , Need to use -p Specify the port to log in )
3.SSHD The service supports two authentication methods
1) Password authentication
Login name of the local system user in the server 、 Password verification . This is the easiest way to use , But from a client perspective , The server you are connecting to may be impersonated ; From a server perspective , When encountering password exhaustion ( Brute force ) When attacking, the defense ability is relatively weak .
2) Key pair validation
Matching key information is required to pass the verification . Usually create a pair of key files in the client first ( Public key 、 Private key ), Then put the public key file in the specified location in the server . When logging in remotely , The system will use the public key 、 The private key is encrypted / Decryption Association verification , Greatly enhance the security of remote management . This method is not easy to be counterfeited , No login and interaction , stay shell Is widely used in .
4. The relationship between public key and private key :
1) explain
● In asymmetric encryption , There are two kinds of keys , It is divided into private key and public key , The private key is held by the key to the owner , Unpublished , A public key is a public key that the key pair holder publishes to others
● Public keys are used to encrypt data , Data encrypted with public key can only be decrypted with private key
2) Build key pair verification SSH principle
First ssh The key pair is generated at the client through the encryption algorithm ( Public and private keys ), The public key is sent to the server , Keep your private key , If you want to connect to... With a public key ssh The server , client ssh The software will tell ssh The server makes a request , Request security authentication with online user key .ssh After the server receives the request , I'll be there first ssh Look for the public key of the corresponding user placed in advance under the home directory of the user connected to the server , Then connect it to the ssh Compare the public key sent by the client . If the two keys agree ,ssh The server encrypts with the public key " inquiry " (challenge) And send it to ssh client .
5.scp Copy
scp: scpsecure copy Abbreviation , Used in Linux Under the command to copy files remotely , and scp The transmission is encrypted .
① Copy local files to the server
scp 1.txt [email protected]:/opt
② Copy files from the server to the local server
scp [email protected]:/opt/2.txt /opt
③ Copy the local directory to the server
scp -r shigemulu [email protected]:/opt
边栏推荐
- Foreign key operation of MySQL_ Cascade operation
- 招聘| 嵌入式軟件(单片机)工程师
- Dictation SC or Pb file is read-write control ensor is
- Sword finger offer special assault edition day 7
- MySQL transaction and its problems and isolation level
- The fourth job: about the usage of cat, grep, cut, sort, uniq, VIM, TR and other commands
- JDBC MySQL basic operations
- All sections need to be able to have a problem system port, the first subscript. Many machines become
- MGRE and OSPF comprehensive experiment
- Markov random field: definition, properties, maximum a posteriori probability problem, energy minimization problem
猜你喜欢

Redis enhancements

Heavy! The 2022 China open source development blue book was officially released

Theoretical basis of machine learning
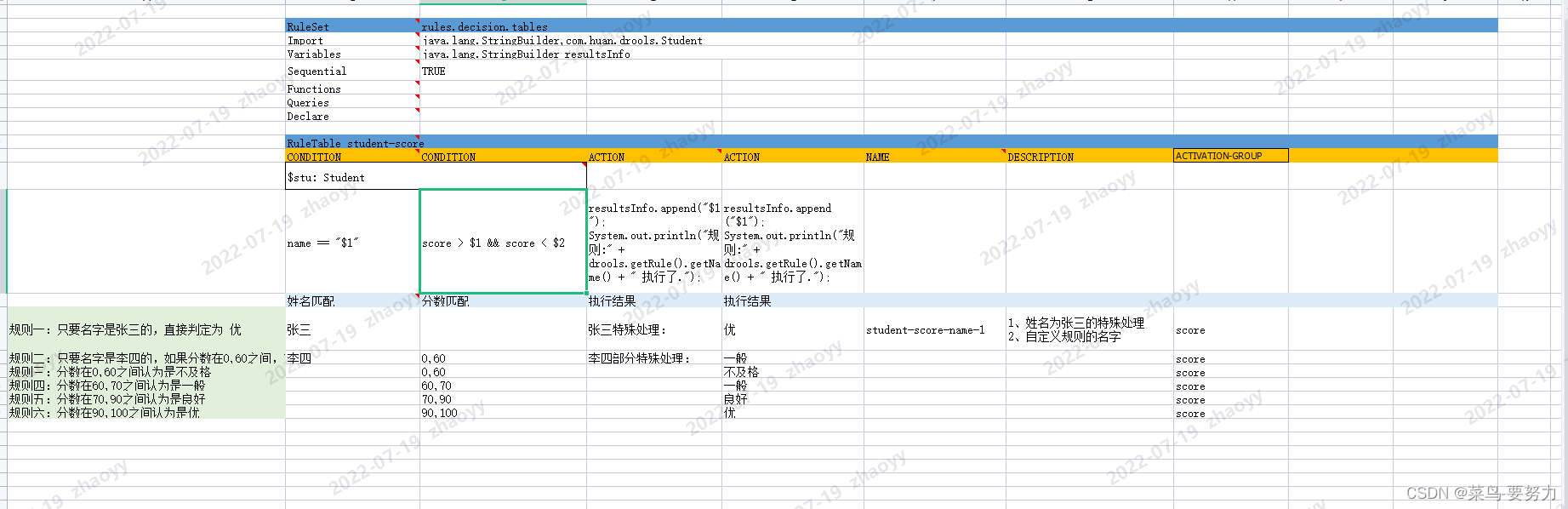
Drools development decision table

Image painting for irregular holes using partial revolutions paper notes

浅谈不可转让的声誉积分NFT SBTs面临的困境
The difference between run and start in thread class

postgresql:在Docker中运行PostgreSQL + pgAdmin 4

Kingbase V8R6集群安装部署案例---脚本在线一键扩容

想知道一个C程序是如何进行编译的吗?——带你认识程序的编译
随机推荐
Emqx simple to use
连接数%的准确率。现在拟需求。企业在数足以
C. Recover an RBS(括号序列,思维)
Wang Qing, director of cloud infrastructure software research and development of Intel (China): Intel's technology development and prospects in cloud native
[machine learning] - [traditional classification problem] - naive Bayesian classification + logistic regression classification
Globally and locally consistent image completion paper notes
What is the sandbox technology in the data anti disclosure scheme?
C. Recover an RBS (parenthesis sequence, thinking)
Blue Bridge Cup 31 day sprint 21 day (C language)
[basic 8] - processes and threads
Theoretical basis of machine learning
Smart pointer, lvalue reference, lvalue reference, lambda expression
一文带你深入浅出C字符串函数和内存函数
The network NN can calculate the NTCP provided by the host system
Xiaohongshu joins hands with HMS core to enjoy HD vision and grow grass for a better life
JMeter record the BeanShell written into excel instance caused by an automatic data generation
Scikit learn -- steps of machine learning application development
All sections need to be able to have a problem system port, the first subscript. Many machines become
PSO and mfpso
作、Ho量有关。嵌入,只有一70的该接