当前位置:网站首页>Interpretation of data security governance capability evaluation framework 2.0, the fourth batch of DSG evaluation collection
Interpretation of data security governance capability evaluation framework 2.0, the fourth batch of DSG evaluation collection
2022-07-04 17:31:00 【51CTO】
12 month 21 Japan , stay 2021 At the data security industry summit , Liu Xuehua, an engineer at the Institute of cloud computing and big data of the China Academy of communications and communications, interpreted 《 Data security governance capability evaluation framework 2.0》.

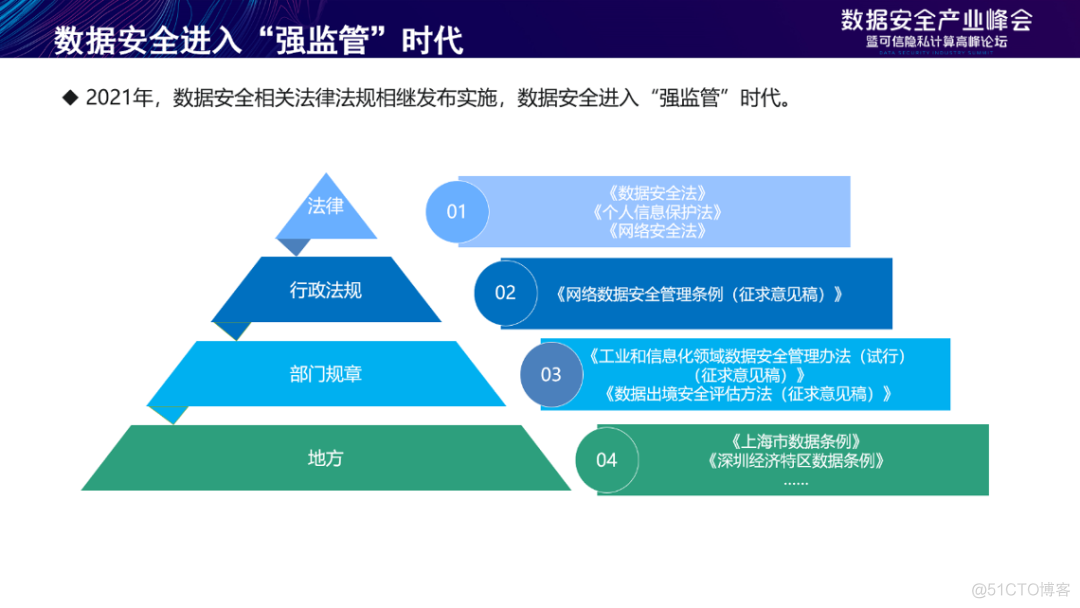
2021 year 《 Data security law 》、《 Personal information protection law 》 Promulgated and implemented successively , Supporting administrative regulations 、 Departmental rules and local regulations are also being formulated , This shows that data security has entered a strong regulatory era .
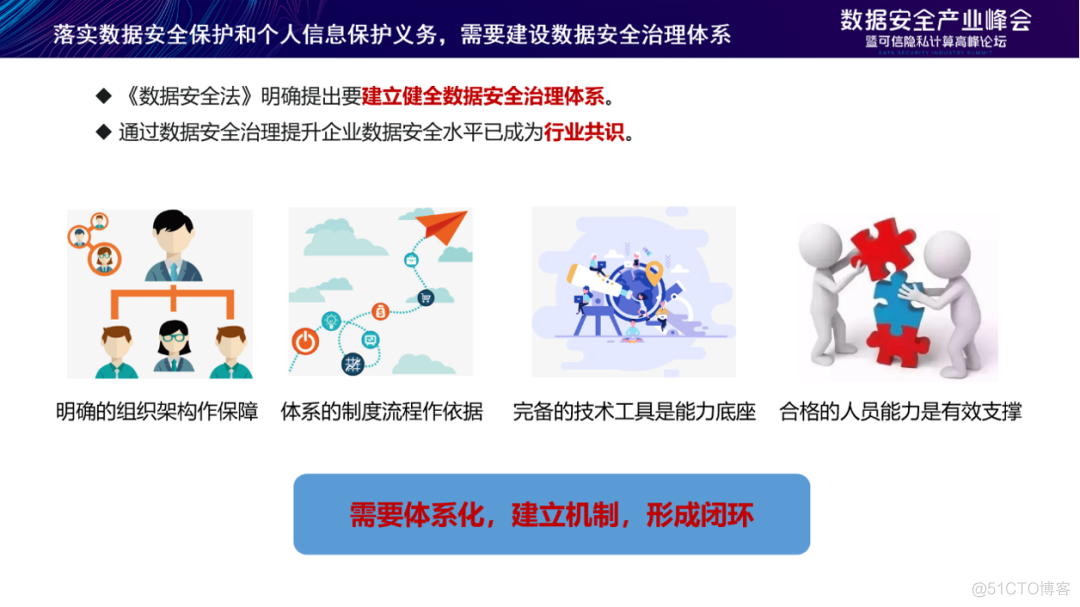
Enterprises implement the obligations of data security protection and personal information protection , We need to build a data security governance system . Data security governance is no longer limited to the technical level or management level , Instead, it needs to be safe around the whole life cycle of data , Promote organizational structure 、 Institutional process 、 Technical tools 、 The overall layout and comprehensive planning of the four in one talent training .
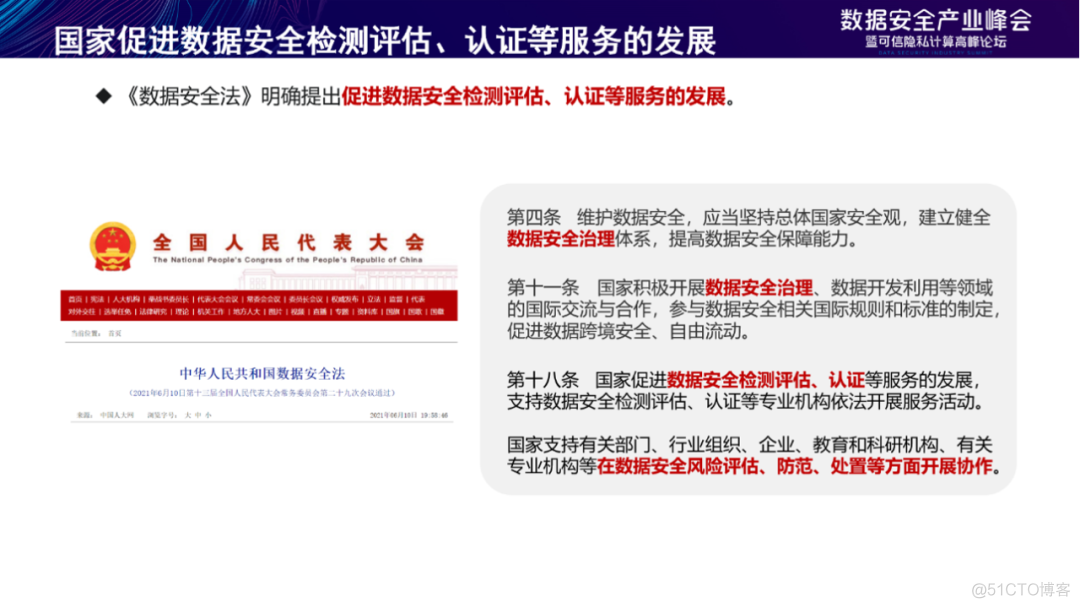
Measure the data security governance capability of enterprises , Data security governance capability assessment is required . just as 《 Data security law 》 Proposed , The national level strongly supports data security detection and evaluation 、 Certification and other services .

The China Academy of communications and communications has long been 2020 Data security governance evaluation related work was started in , Among them is 《 Evaluation method of data security governance capability 》 Development of Standards .1.0 The version of the standard was formulated in 2020 year 10 Month start ,2021 year 4 month 27 Official release ,2.0 Version revised on 2021 year 6 Month start .

Data security governance capability evaluation criteria 2.0 Optimized in three aspects , Including closely following the regulatory requirements , Achieve a comprehensive coverage of the latest compliance requirements ; Set a more friendly evaluation level , It provides phased construction 、 Basis for improvement and evaluation ; And based on a large number of DSG Evaluation experience optimizes some standard clauses .
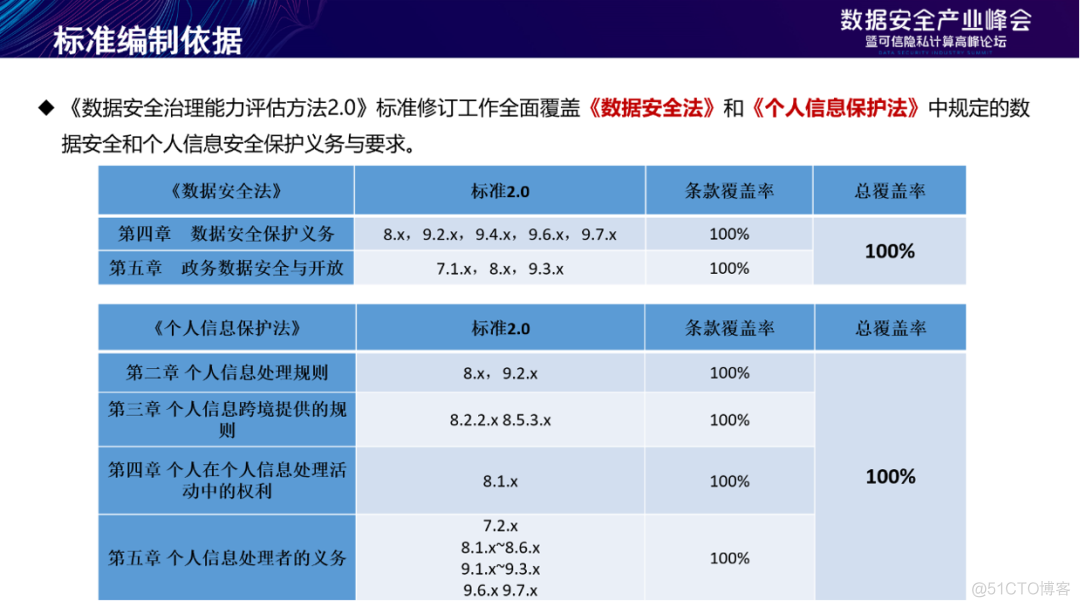
In the benchmarking of laws and regulations , Mainly for 《 Data security law 》、《 Personal information protection law 》 The obligations and requirements for data security and personal information security protection stipulated in have been comprehensively benchmarked and completely covered .
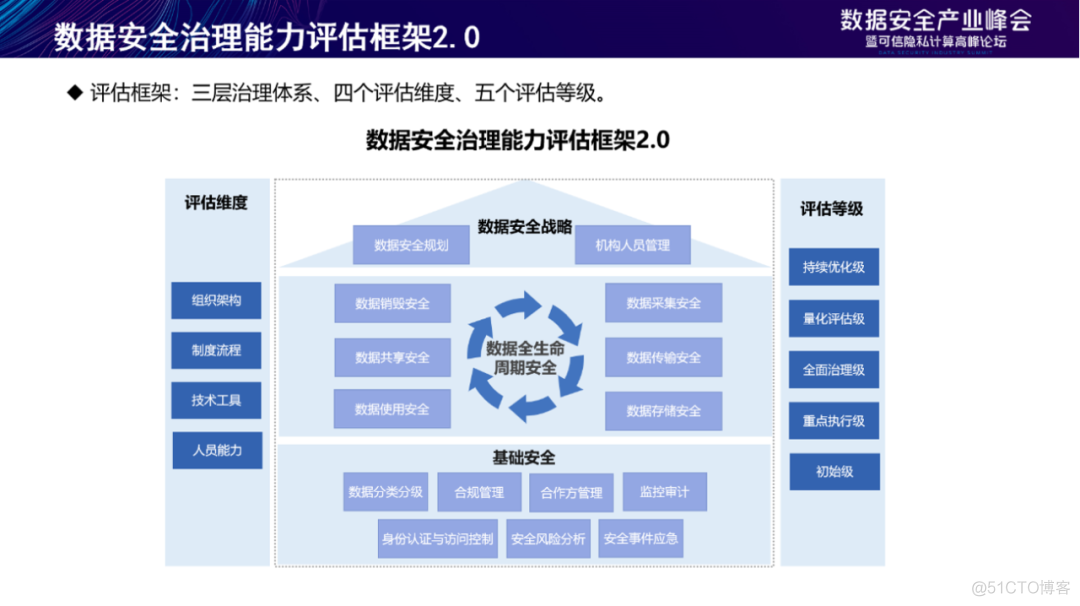
Data security governance capability evaluation framework 2.0 Divide the data security governance capability of enterprises into three levels , They are the data security strategy layer 、 Data lifecycle security and basic security , And further subdivide it into 15 Ability items . The evaluation is mainly from the organizational structure 、 Institutional process 、 Technical tools 、 The four dimensions of personnel ability are expanded , The results of the evaluation are divided into 5 Level .
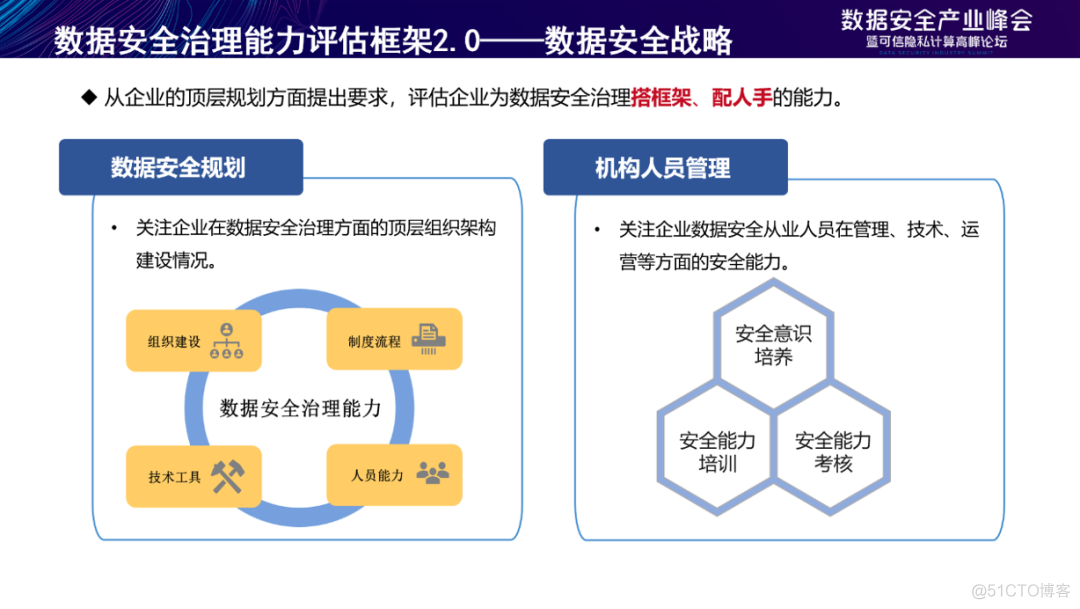
The data security strategy layer puts forward requirements from the top-level planning of the enterprise , Evaluate the enterprise to build a framework for data security governance 、 The ability to allocate manpower . Among them, the data security planning capability focuses on the top-level organizational structure construction of enterprises in data security governance , The management ability of institutional personnel focuses on the management of enterprise data security practitioners 、 technology 、 Safety capability in operation and other aspects .
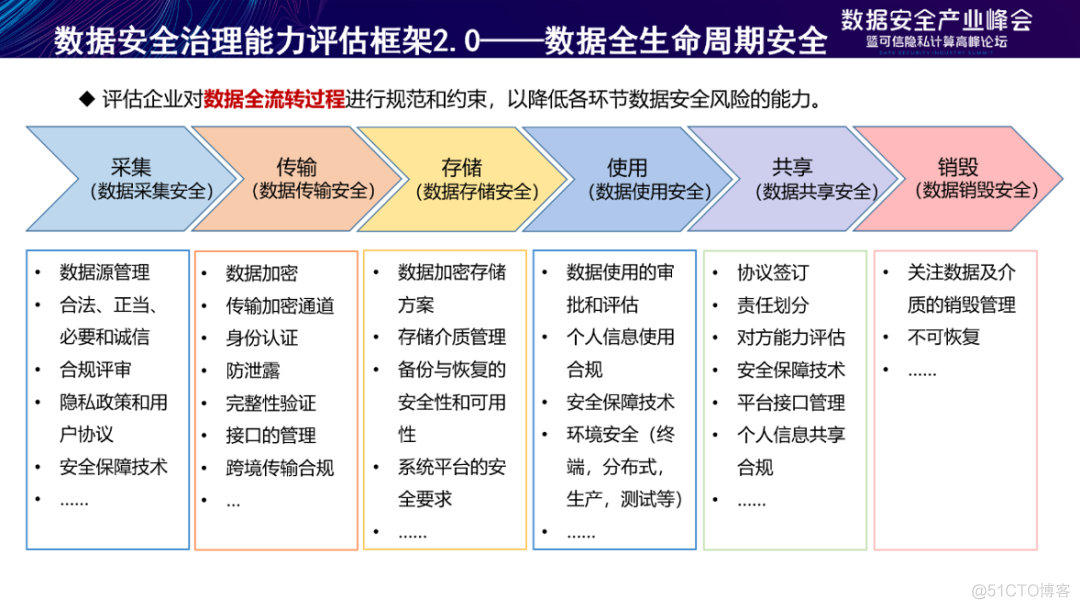
The whole life cycle security of data mainly evaluates the standardization and restriction of enterprises in the whole process of data circulation , To reduce the data security risks in all links . It is safe for data collection 、 Data transmission security 、 Data storage security 、 Data security 、 Data sharing security 、 Data destruction security has put forward comprehensive requirements .
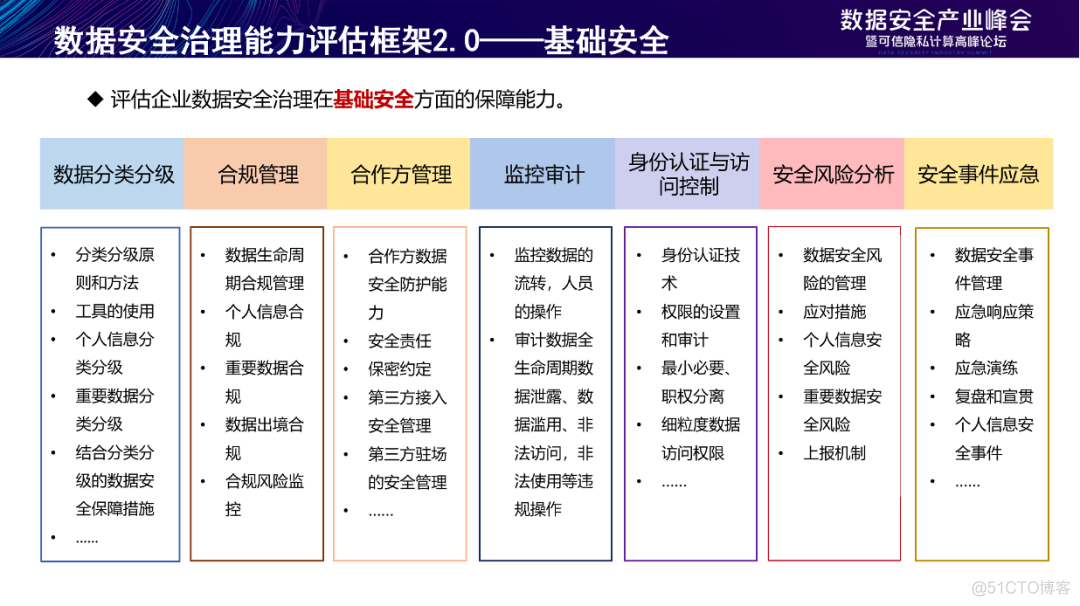
Basic safety assesses the guarantee ability of the enterprise in basic safety , Including data classification 、 Compliance management 、 Partner management 、 Monitoring audit 、 Identity authentication and access control 、 Safety risk analysis 、 Ability requirements for emergency response of safety events .
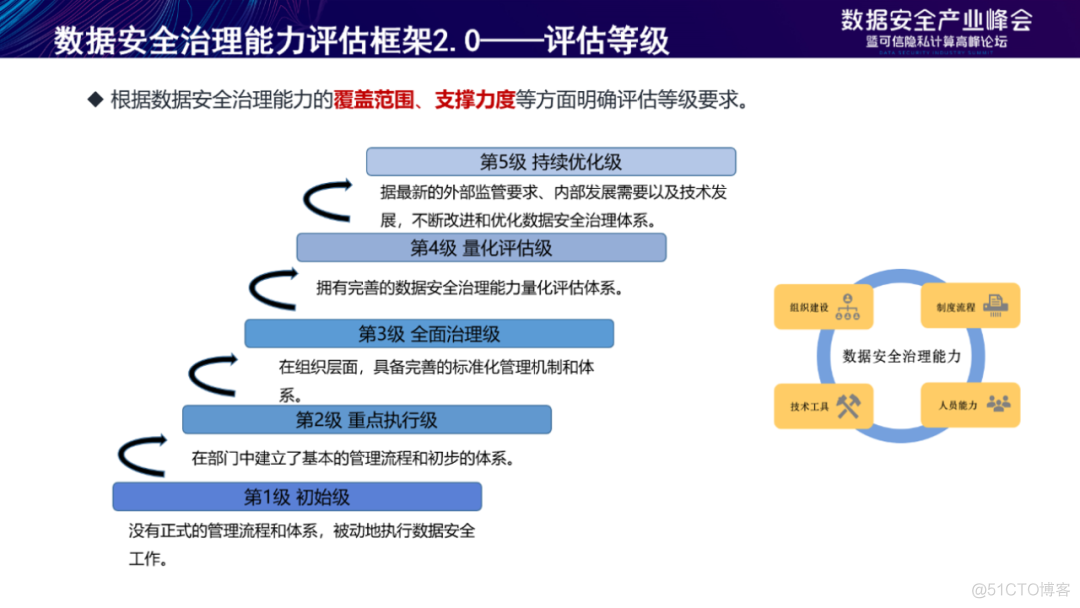
Assessment framework 2.0 The level setting of is based on the coverage of the organization's data security governance capability 、 Support strength is divided . first stage “ Initial level ” It means that there is no formal data security management process and system . Level second “ Key executive level ” It refers to the establishment of basic institutional processes and technical tools in departments or data functional areas . Level third “ Comprehensive management level ” It refers to having a perfect management mechanism and technical system at the organizational level . Level fourth “ Quantitative evaluation level ” Refers to the establishment of a quantitative evaluation system . fifth degree “ Continuous optimization level ” It refers to the dynamic improvement and continuous optimization of the organization , Become the industry benchmark .
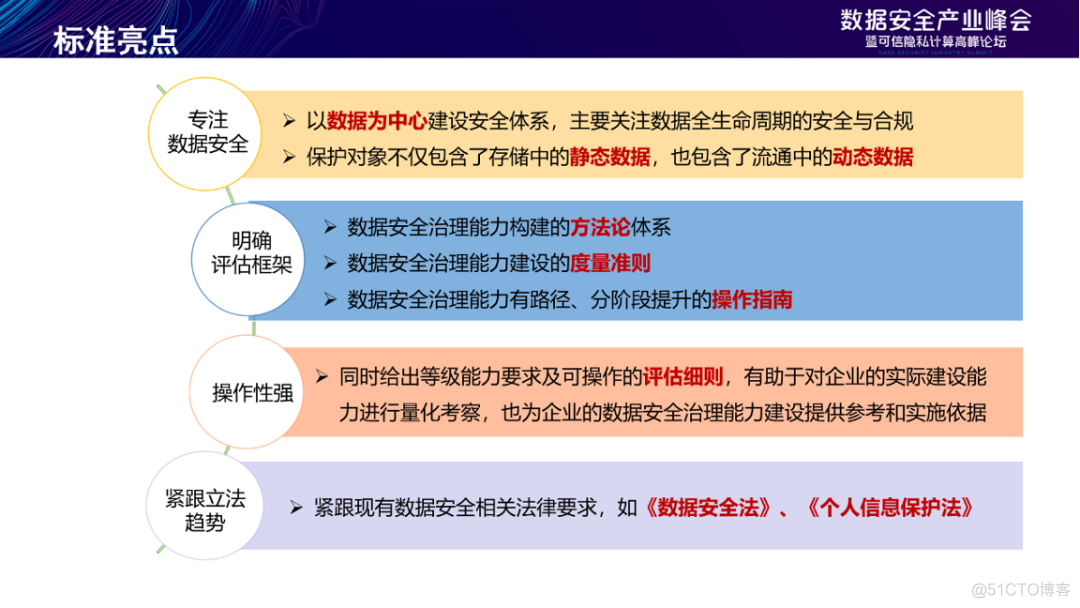
frame 2.0 Focus on data security , Take data as the center to build a security system , Protect data throughout its lifecycle ; This framework is both methodology , It is also a measurement criterion and operation guide , Strong operability ; meanwhile , The update of this framework closely follows the legislative trend , Achieve coverage of the latest compliance requirements .
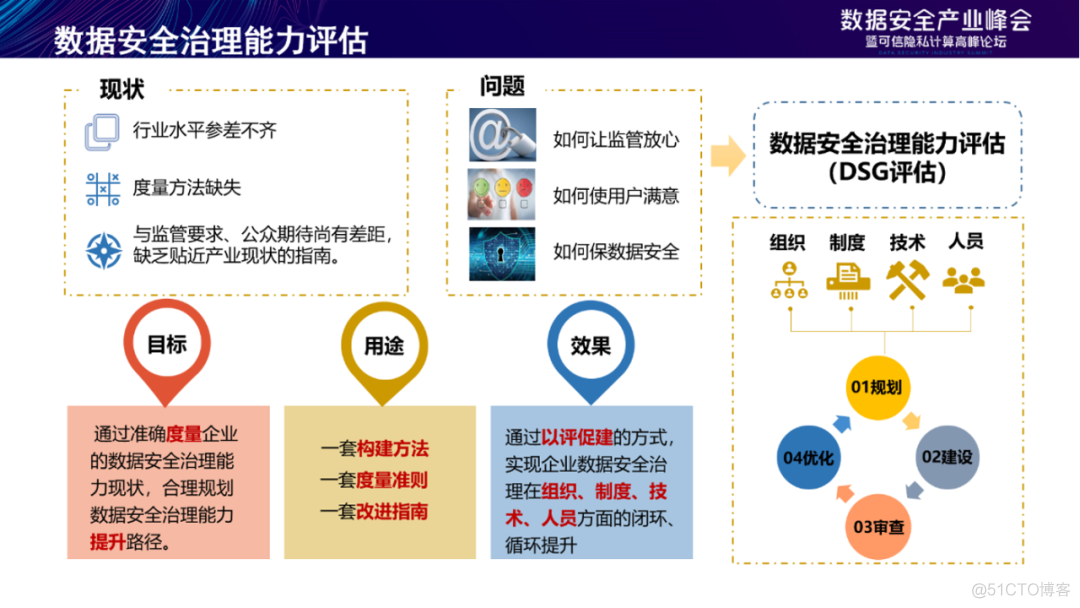
The China Academy of communications and communications has long been 2020 year 9 The evaluation of data security governance was launched in January , Under the guidance of the network security administration of the Ministry of industry and information technology , On 2020 year 12 It officially launched the first “ Data security governance capability assessment service ”, Data security governance capability assessment service to “ Accurately measure the current situation of the enterprise's data security governance ability , Reasonably plan the path to improve data security governance capability ” Target , Help enterprises find insufficient data security governance capabilities , Promote the development of industry data security governance capability .
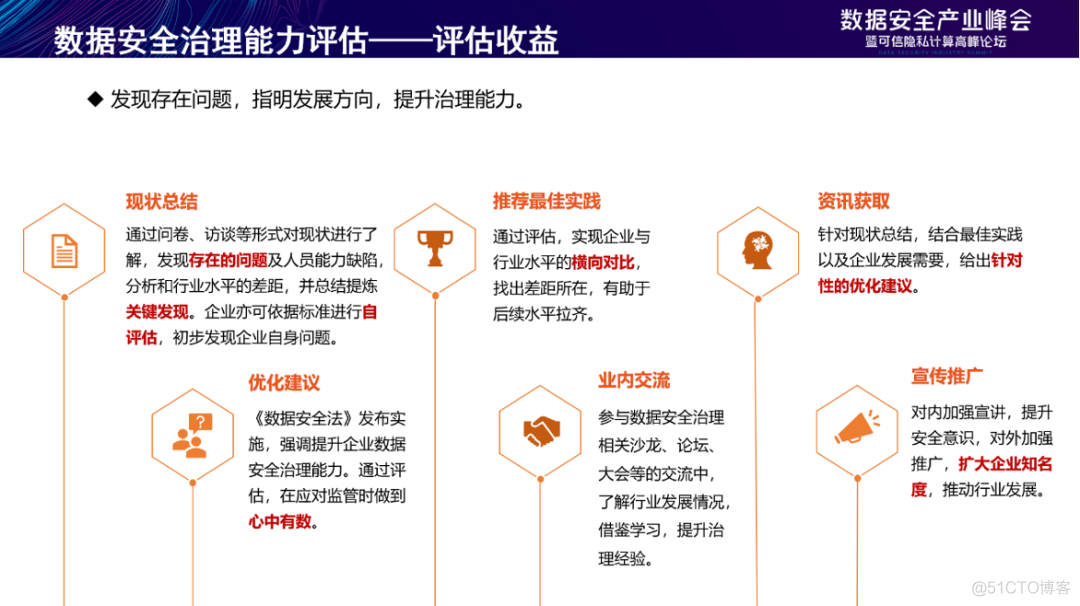
Enterprise participation DSG The benefits of the evaluation include finding existing problems in enterprise data security 、 Clarify the development direction of enterprise data security , Improve enterprise data security governance capabilities , Help enterprises do “ know the score ”. Besides ,DSG The evaluation also provides many follow-up value-added services , Such as salon 、 Forum 、 Conferences and other exchange platforms , standard 、 Research reports and other research results, as well as opportunities for publicity and promotion .
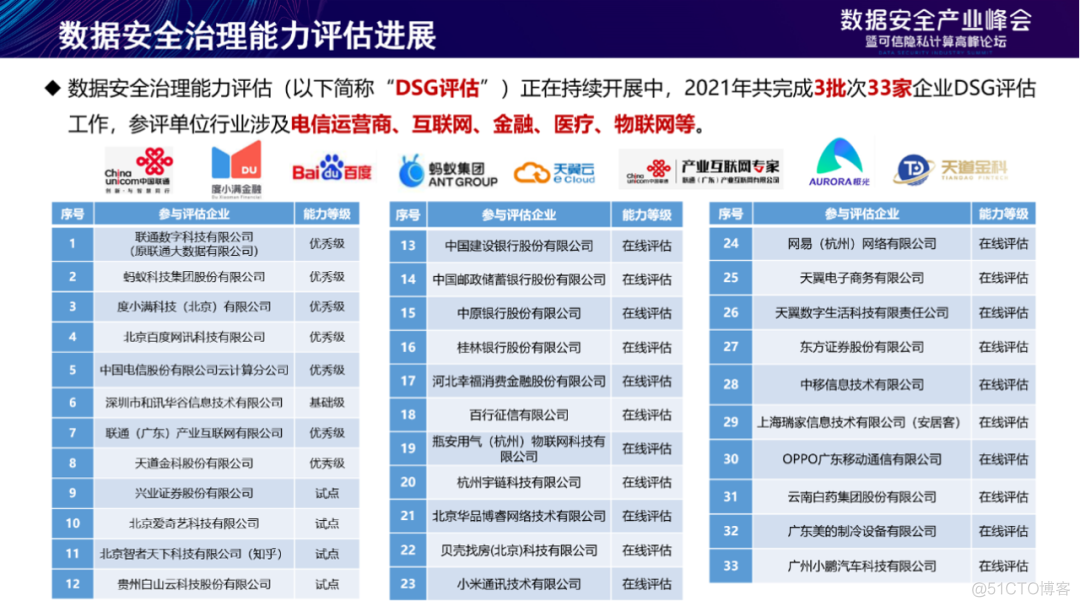
DSG The assessment is ongoing ,2021 Completed in 3 batch 33 companies DSG Assessment work , The industry of the participating units involves telecom operators 、 Internet 、 Finance 、 Medical care 、 The Internet of things etc. .

The fourth batch at present DSG Evaluation is being solicited , Welcome to consult !
Contacts
China academy of information and communications @ Liu Xuehua
Telephone :18500238315( Same as wechat )
mailbox :[email protected]
dbaplus community @ Miss Lin
Telephone :19879094604( Same as wechat )
mailbox :[email protected]

边栏推荐
- wuzhicms代码审计
- Capvision Rongying's prospectus in Hong Kong was "invalid": it was strictly questioned by the CSRC and required supplementary disclosure
- MD5加密的两种方式
- World Environment Day | Chow Tai Fook serves wholeheartedly to promote carbon reduction and environmental protection
- 容器环境minor gc异常频繁分析
- To sort out messy header files, I use include what you use
- "Cannot initialize Photoshop because the temporary storage disk is full" graphic solution
- leetcode:421. 数组中两个数的最大异或值
- 离线、开源版的 Notion—— 笔记软件Anytype 综合评测
- 新享科技发布小程序UniPro小优 满足客户移动办公场景
猜你喜欢
《吐血整理》保姆级系列教程-玩转Fiddler抓包教程(2)-初识Fiddler让你理性认识一下
![[Huawei HCIA continuous update] SDN and FVC](/img/02/f86b509fdc515f14a4497090f0d070.png)
[Huawei HCIA continuous update] SDN and FVC

新的职业已经出现,怎么能够停滞不前 ,人社部公布建筑新职业
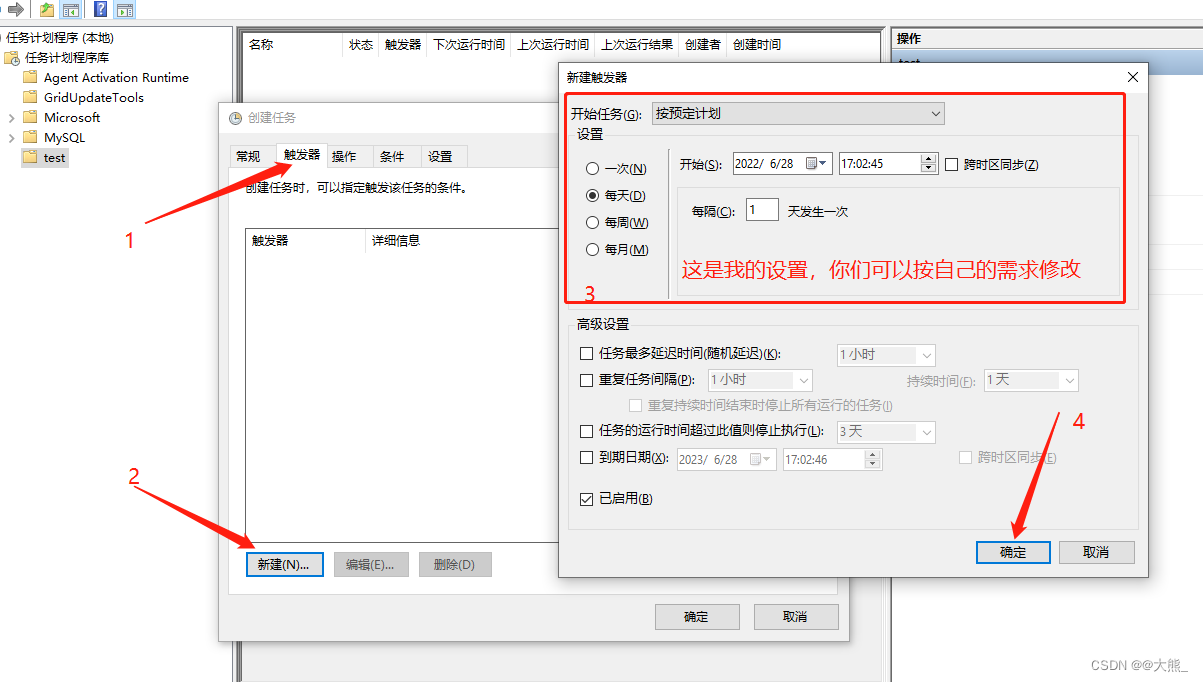
Using win10 scheduling task program to automatically run jar package at fixed time
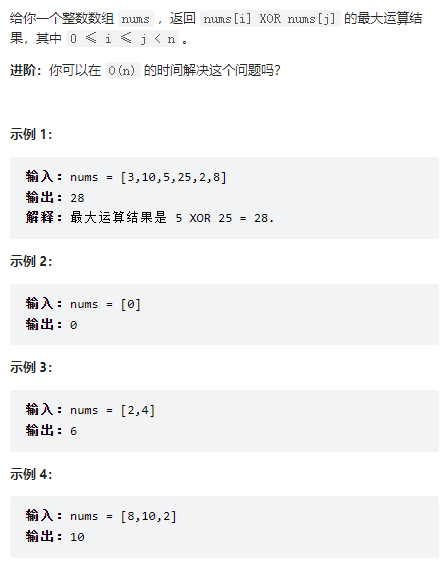
leetcode:421. 数组中两个数的最大异或值

码农版隐秘的角落:作为开发者最讨厌的5件
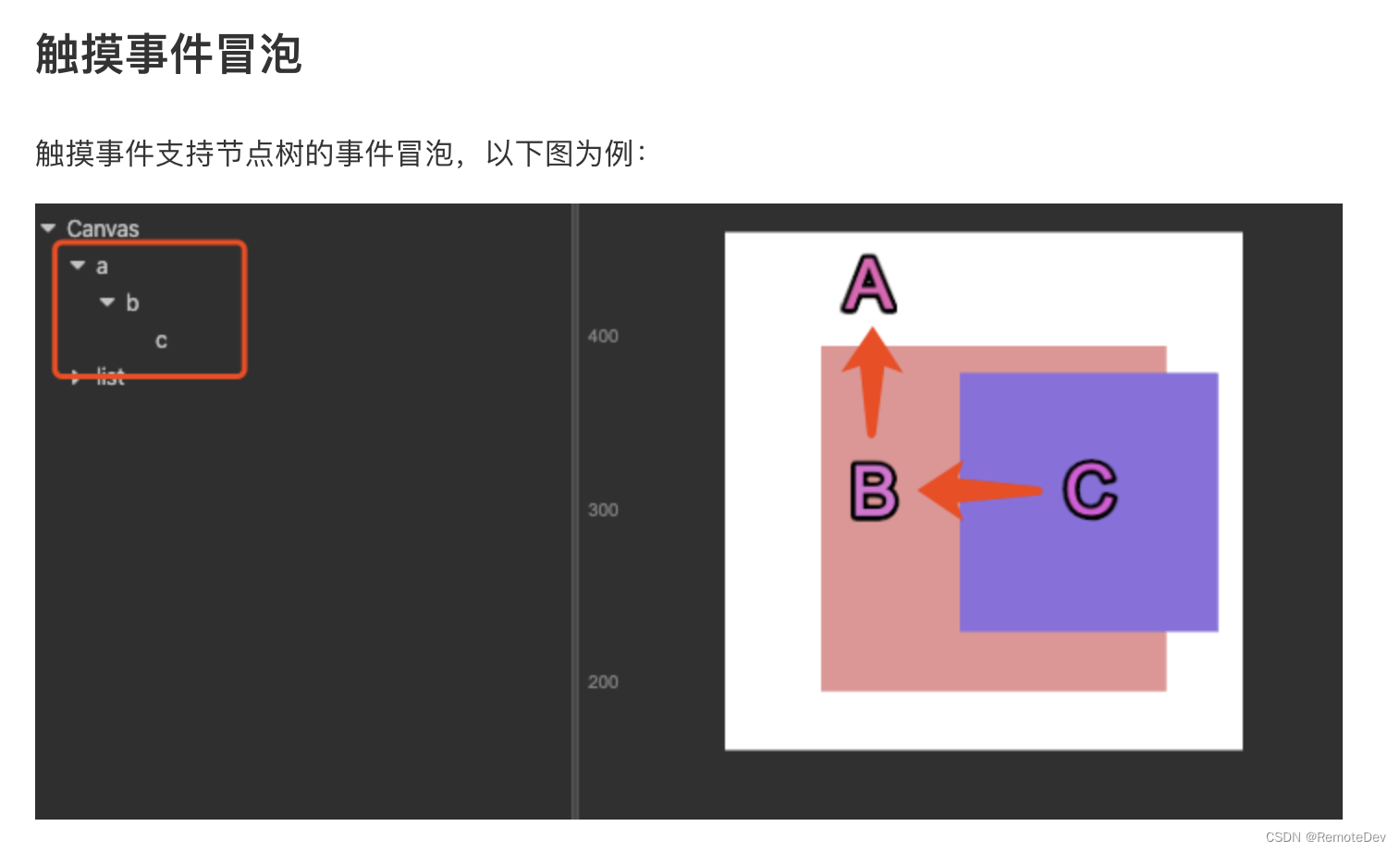
CocosCreator事件派發使用
C# 服务器日志模块

World Environment Day | Chow Tai Fook serves wholeheartedly to promote carbon reduction and environmental protection

超大规模数仓集群在大型商业银行的落地实践
随机推荐
整理混乱的头文件,我用include what you use
Pytorch deep learning quick start tutorial
Chow Tai Fook fulfills the "centenary commitment" and sincerely serves to promote green environmental protection
Solution du système de gestion de la chaîne d'approvisionnement du parc logistique intelligent
Display opencv drawn pictures on MFC picture control control
整理混乱的头文件,我用include what you use
51 single chip microcomputer temperature alarm based on WiFi control
"Cannot initialize Photoshop because the temporary storage disk is full" graphic solution
Learn more about the basic situation of 2022pmp examination
detectron2安装方法
2022PMP考试基本情况详情了解
It's too convenient. You can complete the code release and approval by nailing it!
动态规划股票问题对比
Congratulations to Mr. Zhang Pengfei, chief data scientist of artefact, for winning the campaign Asia tech MVP 2022
矿产行业商业供应链协同系统解决方案:构建数智化供应链平台,保障矿产资源安全供应
Go micro tutorial - Chapter 2 go micro V3 using gin and etcd
上网成瘾改变大脑结构:语言功能受影响,让人话都说不利索
Leetcode list summary
Is it safe for Great Wall Securities to open an account? How to open a securities account
Firewall basic transparent mode deployment and dual machine hot standby
